- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity AI Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
CheckMates Fest 2026
Join the Celebration!
AI Security Masters
E1: How AI is Reshaping Our World
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Maestro Madness
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- General Topics
- :
- Re: TLS 1.1 Protocol Detection
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
TLS 1.1 Protocol Detection
I have an R80.40 VSX Cluster where Vulnerability TLS 1.1 Protocol Detection has been reported on port 443. I went through a community post on how to disable 1.1 by editing the "vi /web/templates/httpd-ssl.conf.templ" .
My query is that does disabling TLS 1.1 in anyway affect the traffic passing through the gateways ? if i understand this correctly this is only related to GAIA Portal access ? and disabling TLS will not cause any kind of traffic interruption.
These GWs have antibot, antivi , URL Filtering blades enabled.
9 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Do not do any manual change. Follow sk126613 and use cipher_util.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I went through this sk but i dont get how TLS is being disabled there.
Moreover..i tried running cipher_util but i get the following :
Make sure the selected blade is active.
'/opt/CPshrd-R80.40/conf/ssl_inspection.cipher' file is corrupted or doesn't exist.
Aborting...
also..these TLS settings are only limited to GAIA portal access and not the passing traffic ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Editing the httpd-ssl.conf.templ file doesn't impact the web portal when multi-portal functions are used. If you know which specific ciphers you plan to use, then cipher_util is an option.
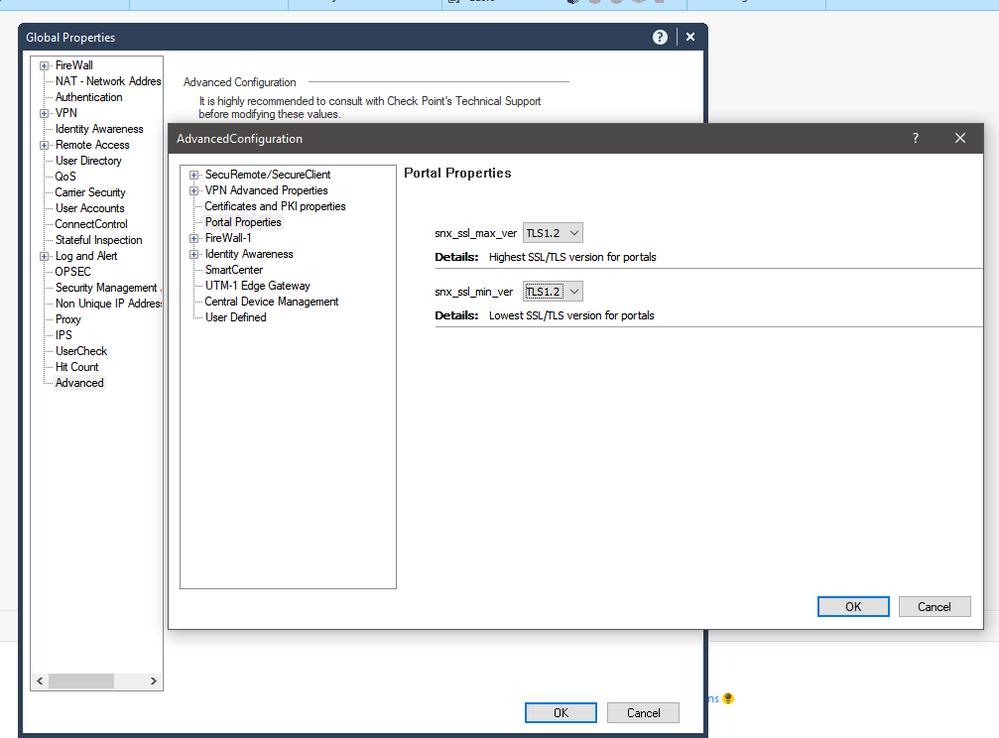
Another option would be to use Global Properties in SmartConsole. There is an advanced setting that allows you to configure the minimum TLS setting. This is simply applied when policy is pushed to the gateway.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
For Gateways this approach is alright..but i am looking to disable TLS1.0 & TLS 1.1 in Management Server as well
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Don't disabled TLSv1.1 on the Manager, I believe this is needed. I may have put in the SK related to this in a previous post related to lockdown.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Can you share the sk please
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Did try to find it, I seem to remember typing in the error I got and then finding an SK which hinted at the requirement for TLSv1.1 so I ensured this was added. Here are my entries on a R81 SMS.
#cat /web/templates/httpd-ssl.conf.templ | grep SSLCipher
SSLCipherSuite HIGH:!ADH:!RC4:!DHE:!LOW:!EXP:!RSA:!eNULL:!aNULL:!SSLv2:!MD5
#cat /web/templates/httpd-ssl.conf.templ | grep SSLProtocol
SSLProtocol -ALL {ifcmp = $httpd:ssl3_enabled 1}+{else}-{endif}TLSv1.1 +TLSv1.2 +TLSv1.3
If can, try to exclude TLSv1.1 as well and see if you get a problem. If I find the SK will update this thread.
Only odd thing I noted when attempting to scan via each TLS version TLSv1.1 came back with nothing:
Here are the results of the scan:
* TLS 1.1 Cipher Suites:
Attempted to connect using 80 cipher suites; the server rejected all cipher suites.
------------------------
* TLS 1.2 Cipher Suites:
Attempted to connect using 156 cipher suites.
The server accepted the following 11 cipher suites:
TLS_ECDHE_RSA_WITH_CHACHA20_POLY1305_SHA256 256 ECDH: X25519 (253 bits)
TLS_ECDHE_RSA_WITH_CAMELLIA_256_CBC_SHA384 256 ECDH: X25519 (253 bits)
TLS_ECDHE_RSA_WITH_CAMELLIA_128_CBC_SHA256 128 ECDH: X25519 (253 bits)
TLS_ECDHE_RSA_WITH_ARIA_256_GCM_SHA384 256 ECDH: X25519 (253 bits)
TLS_ECDHE_RSA_WITH_ARIA_128_GCM_SHA256 128 ECDH: X25519 (253 bits)
TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384 256 ECDH: prime256v1 (256 bits)
TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384 256 ECDH: prime256v1 (256 bits)
TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA 256 ECDH: prime256v1 (256 bits)
TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256 128 ECDH: prime256v1 (256 bits)
TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256 128 ECDH: prime256v1 (256 bits)
TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA 128 ECDH: prime256v1 (256 bits)
The group of cipher suites supported by the server has the following properties:
Forward Secrecy OK - Supported
Legacy RC4 Algorithm OK - Not Supported
------------------------
* TLS 1.3 Cipher Suites:
Attempted to connect using 5 cipher suites.
The server accepted the following 3 cipher suites:
TLS_CHACHA20_POLY1305_SHA256 256 ECDH: X25519 (253 bits)
TLS_AES_256_GCM_SHA384 256 ECDH: X25519 (253 bits)
TLS_AES_128_GCM_SHA256 128 ECDH: X25519 (253 bits)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I mite do that..disable TLS1.1 and then observe.
one thing i noticed in your output for SSL CIPHERS
SSLCipherSuite HIGH:!ADH:!RC4:!DHE:!LOW:!EXP:!RSA:!eNULL:!aNULL:!SSLv2:!MD5
there is no 3DES at the end ..have you disabled medium ciphers using cipher_util ? how do you determine which are the medium strength SSL Ciphers and should be disabled ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I could not get the cipher_util command to work. In my case I'm only interested in HIGH strength ciphers.
Found the SK I looked at!
sk171707
Symptom:
"SslVersionOrCipherMismatch" error when disabling AES128 and opening a new Logging & Monitor tab in SmartConsole
When we disable TLS1.0, TLS 1.1 and SHA1, the option of disabling AES128 is not supported because this creates a situation where the connection is no longer considered secure.
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 19 | |
| 10 | |
| 10 | |
| 9 | |
| 6 | |
| 3 | |
| 2 | |
| 2 | |
| 2 | |
| 1 |
Upcoming Events
Thu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: Exposing AI Vulnerabilities: CP<R> Latest Security FindingsThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter