- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity AI Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
CheckMates Fest 2026
Join the Celebration!
AI Security Masters
E1: How AI is Reshaping Our World
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
R82.10 and Rationalizing Multi Vendor Security Policies
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- General Topics
- :
- Re: Reverting back to self-signed certificate for ...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jump to solution
Reverting back to self-signed certificate for HTTPS Inspection
Hello all,
Thank you for taking time to read this. I performed the following on an R80.40 install:
- Enabled the HTTPS Inspection blade
- Generated a CSR, had a third-party sign the CSR,
- Installed the signed certificate
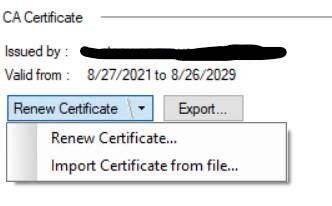
However, HTTPS Inspection failed because I used a server certificate, instead of a CA certificate. So now, I want to revert back to using the self-signed certificate which does generate a CA certificate, but this option is no longer available. From the SmartConsole -> Gateways & Servers -> Gateway Object -> HTTPS Inspection window, I can only view or export the existing certificate:
From Security Policies ->HTTPS Inspection -> HTTPS Tools -> Additional Settings (SmartDashboard) -> HTTPS Inspection -> Gateways , the only option is to Renew or Import:
I've tried disabling HTTPS Inspection, but that did not help either. I've also opened a ticket with CheckPoint and they recommended restoring from backup which unfortunately I do not have or performing a fresh install. They also recommended engaging Professional services.
Before I go this route has anybody encountered this issue or have a recommendation on how to generate the self-signed CA certificate?
1 Solution
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
TAC has not responded whether the above solution is appropriate or not, but I found the "easier" solution. The renew certificate button in the SmartDashboard is meant for the self-signed certificate that was initially created when HTTPS Inspection was activated.
Once you renew the certificate, you can immediately export this certificate from the SmartDashboard, even without pushing a policy.
After you push the policy, do not export the certificate from the SmartConsole. The SmartConsole will export the old certificate. What you have to do is close the SmartConsole and relaunch it. After relaunch, the export from the SmartConsole is the correct, current certificate.
This may be a bug or maybe it's by design -- I'm not sure, but that's how you revert back to the self-signed certificate from a third party certificate.
7 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I’d have to check this one out in my lab to see if there is a way to clear out the external certificate.
Do you have a private CA in your environment? The self-signed cert doesn’t have to be the one you generated on the gateway.
I’ve seen a number of deployments where customers who use ADCS will use the same root CA that was used for 802.1x etc. since it is already deployed to their endpoints.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi mcatanzaro,
Thanks for responding.
No, we don't have a private CA in our environment. If I understand correctly
- I can generate the self-sign on say, a linux box
- Create a private CA, sign the CSR
- Convert signed-certificate to .p12
- Import the .p12 file
That sounds doable and I actually tried something similar on the gateway, but I am not sure how to set up the CA:
cpopenssl ca -startdate 2109100000000 -enddate 2909090000000 -in fw_cert.csr -out fw_cert.crt -config $CPDIR/conf/openssl.cnf
Using configuration from /opt/CPshrd-R80.30/conf/openssl.cnf
Error opening CA private key ./demoCA/private/cakey.pem
4158678668:error:02001002:system library:fopen:No such file or directory:bss_file.c:413:fopen('./demoCA/private/cakey.pem','r')
4158678668:error:20074002:BIO routines:FILE_CTRL:system lib:bss_file.c:415:
unable to load CA private key
I'm actually reading up on how to set up the CA. Would it be okay to do this on the gateway?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Sounds like you have done your research.
Regarding the question of using cpopenssl to accomplish this, in my mind I don’t see why it wouldn’t work since it is a port of openssl.
However, I would pose this solution in your TAC case so we can verify the proper syntax and level of support from the appropriate internal resources.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi mcatanzaro,
This is what worked for me:
- Configure the active gateway to be a CA
- Sign the CSR
- Deploy signed certificate to end host
- Export signed certificate in .p12 format
Import .p12 certificate in SmartDashboard -> HTTPS Inspection -> CA Certificate
More detailed:
# Create CA directories and files. With Trail and Error and looking at the openssl.cnf file, these are the directories/files needed
mkdir ca_certificate
cd ca_certificate
mkdir demoCA
cd demoCA
mkdir {certs,crl,newcerts,private,crl,conf}
touch {index.txt,serial}
# Serial numbers are in hex and here we are starting with 1
echo "01" > serial
# Create private key for CA
cpopenssl genrsa -aes256 -out private/cakey.pem 4096
# Copy CheckPoint openssl configuration file to local configuration directory
cp $CPDIR/conf/openssl.cnf conf/
# Modify openssl.cnf
- In the [ req_distinguished_name ] section, change the default values to your appropriate environment
- In the [ usr_cert ] section, change the value for basicConstraint from FALSE to TRUE
# Create a certificate for this local CA
cpopenssl req -new -x509 -days 3650 -key private/cakey.pem -out cacert.pem -config config/openssl.cnf
# Generate a CSR on active gateway
cpopenssl req -new -newkey rsa:4096 -sha256 -out gw.csr -keyout gw.key -config <user generated config file including CN name and other data>
# Sign the CSR
cpopenssl ca -startdate 210910000000Z -enddate 290909000000Z -in gw.csr -out gw.crt -config conf/openssl.cnf
# Deploy certificate to end host
# Export the signed certificate in .p12 format
cpopenssl pkcs12 -export -out gw.p12 -in gw.crt -inkey gw.key
# Import the .p12 certificate from the SmartDashboard -> HTTPS Inspection -> CA certificate
# Push the policy
I submitted the above steps to the TAC. I probably won't here back until Monday, but it seems to work so far. Still testing...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Great to hear and good job.
Report back TAC’s findings from the case here or message me with them.
Would be nice to have this process documented if the product owners say it is supported.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
TAC has not responded whether the above solution is appropriate or not, but I found the "easier" solution. The renew certificate button in the SmartDashboard is meant for the self-signed certificate that was initially created when HTTPS Inspection was activated.
Once you renew the certificate, you can immediately export this certificate from the SmartDashboard, even without pushing a policy.
After you push the policy, do not export the certificate from the SmartConsole. The SmartConsole will export the old certificate. What you have to do is close the SmartConsole and relaunch it. After relaunch, the export from the SmartConsole is the correct, current certificate.
This may be a bug or maybe it's by design -- I'm not sure, but that's how you revert back to the self-signed certificate from a third party certificate.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Most probably SmartConsole cache issue.
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 15 | |
| 11 | |
| 6 | |
| 3 | |
| 3 | |
| 2 | |
| 2 | |
| 2 | |
| 2 | |
| 2 |
Upcoming Events
Thu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldFri 09 Jan 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 42: Looking back & forwardThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: Exposing AI Vulnerabilities: CP<R> Latest Security FindingsThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldFri 09 Jan 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 42: Looking back & forwardThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter