- Products
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- Learn
- Local User Groups
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
- Partners
- More
- ABOUT CHECKMATES & FAQ
- Sign In
- Leaderboard
- Events
Quantum Spark Management Unleashed!
Check Point Named Leader
2025 Gartner® Magic Quadrant™ for Hybrid Mesh Firewall
HTTPS Inspection
Help us to understand your needs better
CheckMates Go:
SharePoint CVEs and More!
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- General Topics
- :
- Re: Report show spam category with "accept" action...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
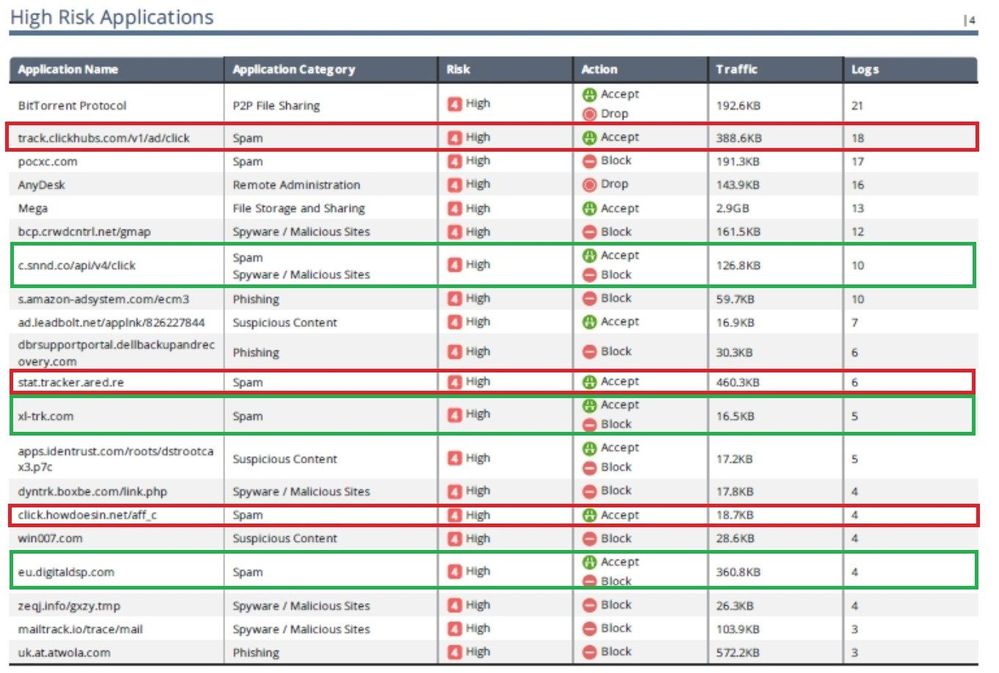
Report show spam category with "accept" actions but not blocking
Hi Everyone,
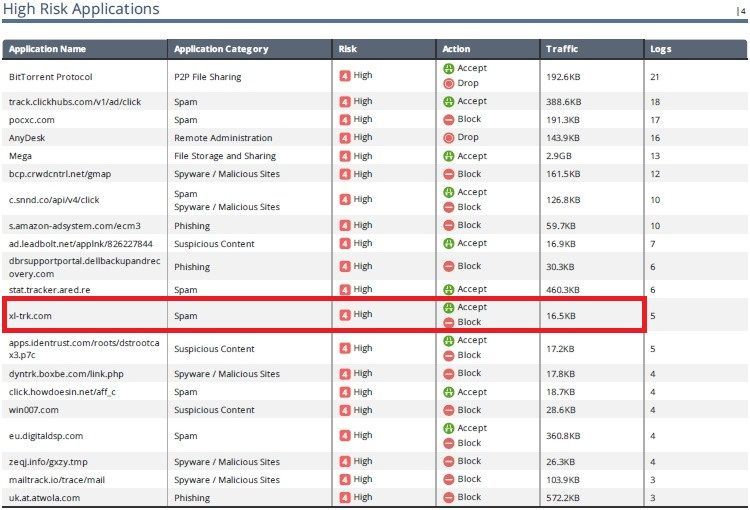
I'm doubting about the High-Risk Applications report was showing different action, although the application name was showing as the same category
I have 2 highlights, one is the red margin and another one is the green margin. Look at the red margin is shown to accept but not blocking. but the green margin is to show status alternately ( accept then block ) but some only show block
Does anyone describe above to me?
Really appreciate every comment
Regards,
Sarm
23 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You have different rules in your policy which allow the same URL/category for some user/source-ip and deny it for others. That's why it is reported that way.
Drill-Down to see the logs related to the entries and look on the matched rules!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Norbert
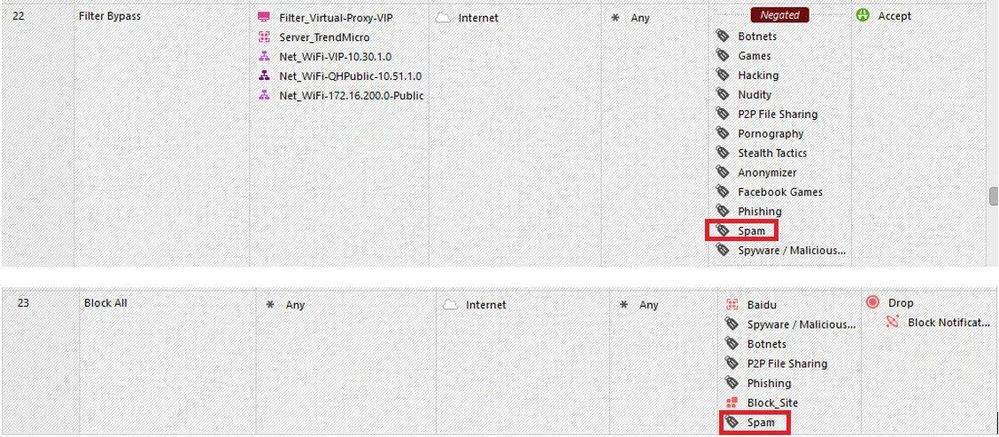
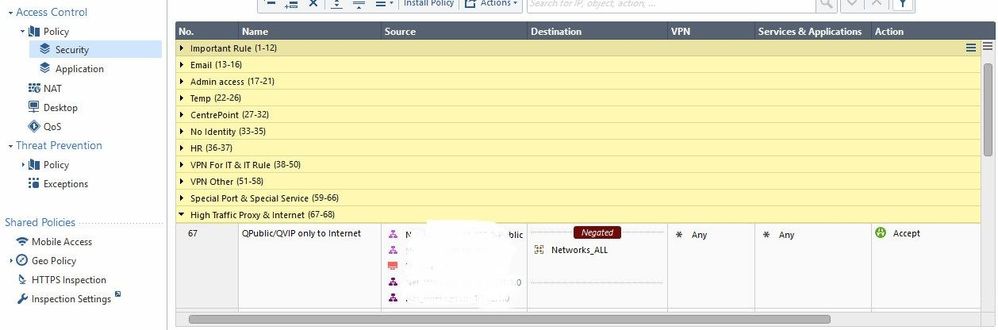
Look at rule no.22 and 23 these should be blocked spam, right?
Regards,
Sarm
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Rule 22 is negated in application column, so this is not relevant for spam.
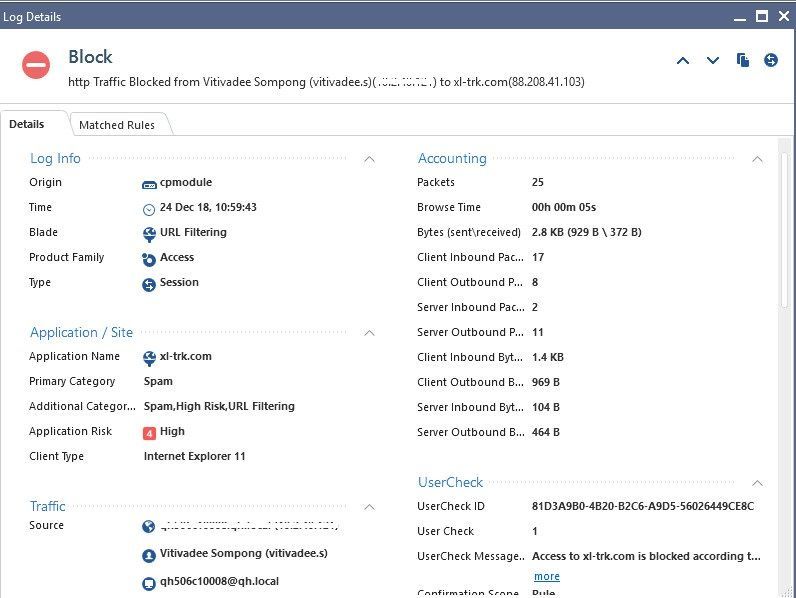
Please show details of the logs allowing or blocking the same destination traffic. Then I might be able to tell you why the action is different.
e.g. double-click this line in the view:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Norbert
Okay, let me check if I can see the log entries that relevant spam in the reports due to that report was correct since Nov 2018 - Jan 2019
I will update two of you again.
By the way, Is there any way to filter out with application name in the log entries view?
Thank you.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Like Norbert said, we need to see the log entries to find out which rule it is accepting on.
Some sites/URLs have multiple categories and the traffic may be getting matched on a different (earlier) rule.
Some sites/URLs have multiple categories and the traffic may be getting matched on a different (earlier) rule.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Admin,
I will provide you the log entries here once I find them.
Thank you
I will provide you the log entries here once I find them.
Thank you
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi All,
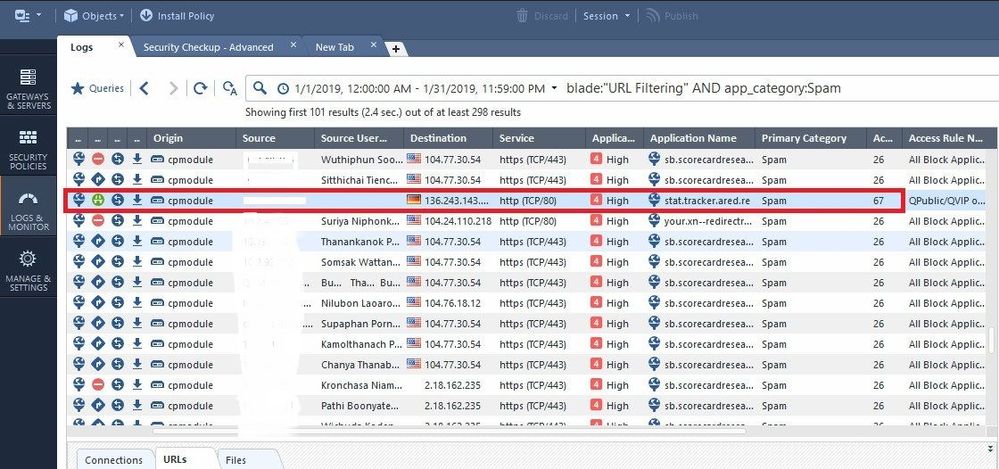
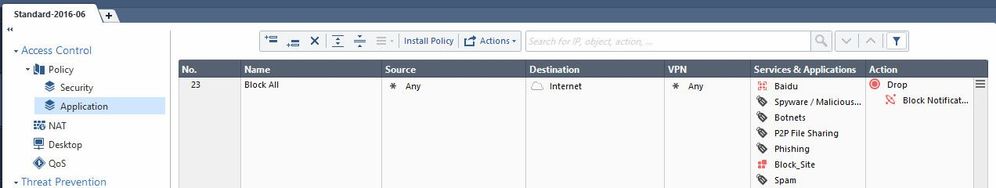
Please see the log entries that I was able to find some of them below.
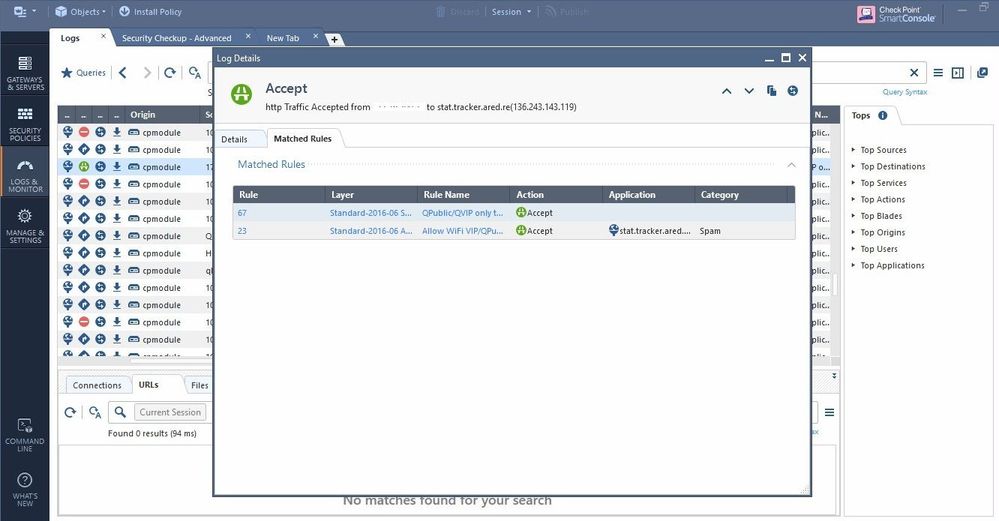
For example, "stat.tracker.ared.re
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
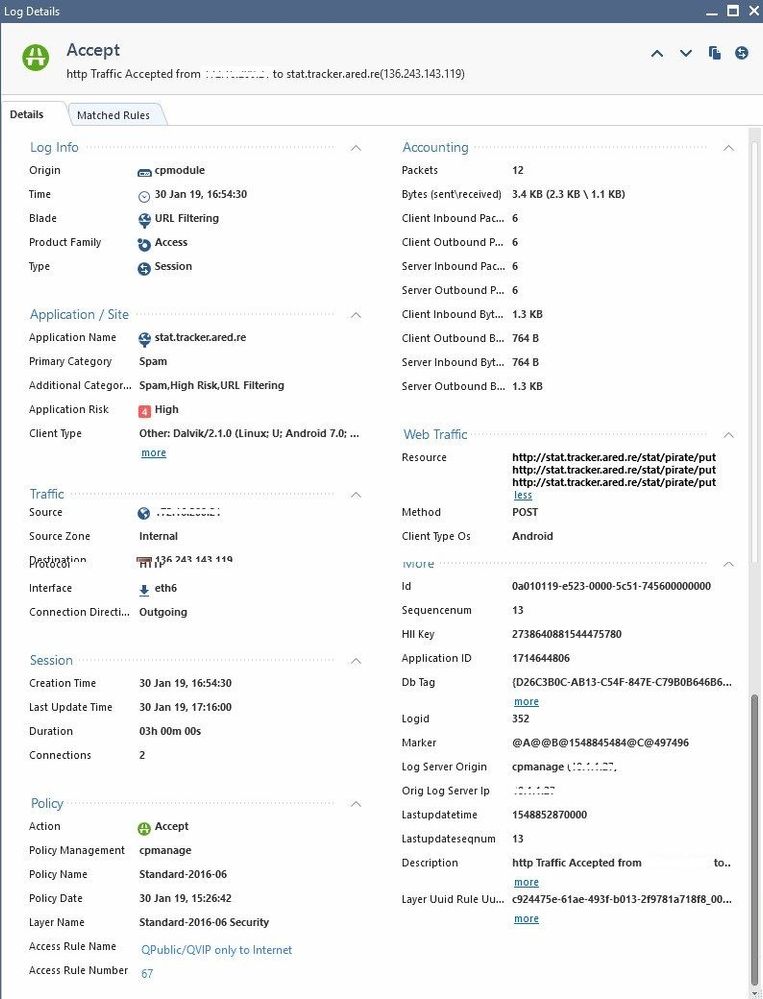
The rule matched on application layer was rule number 23, but it looks like it was a different then the one you showed with block. The rule name is different, it is „Allow WiFi VIP.....“.
Click the rule name in the log and you will get to the matching rule.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The logs you are showing are from 30 Jan 2019. The installed policy is from some hours earlier.
Today we had March 25. Maybee you changed something in the rulebase and as a result the shown rulenumbers doesn‘t match.
As the other checkmates members wrote, clicking the rule entry in the logs brings up the matching rules.
The rule UIDs are not changing over time, but the rule numbers at the beginning of a rule line.
Wolfgang
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
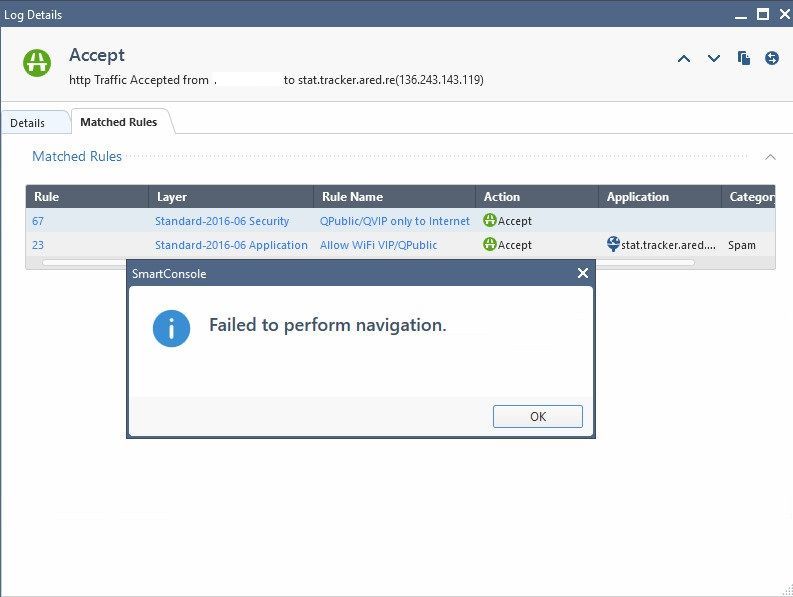
Hi All
I tried to click the rule entry that problematic, found an error "failed to perform navigation" when clicking both rule number and a rule name column. They might be changed something but not sure this would be related to my report showing since 1Nove2018 - 31Jan 2019. As a result, we saw a spam site allowing in the report.
Please kindly advise me if I'm wrong.
Thank you.
Sarm
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Looks like the rule doesn't exist anymore.
You could try to find the rule by opening a revision from the history looking at the timeframe of the log entries.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Norbert
Thank you for your recommendation, I will try to and update you again.
Thank you for your recommendation, I will try to and update you again.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
How come you think it should match rule 22.
The category in your log entry is "Spam" which is not covered by rule 22.
The category in your log entry is "Spam" which is not covered by rule 22.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Nortbert
Sorry, it was my fault I did not notice that there was no spam category in by rule 22.
But anyway, Can you clarify me regarding some application name that displayed in the reports shown action with accept then block in the same column?
Thank you
Sarm
Sorry, it was my fault I did not notice that there was no spam category in by rule 22.
But anyway, Can you clarify me regarding some application name that displayed in the reports shown action with accept then block in the same column?
Thank you
Sarm
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Now we know why we have the Accept. Now focus on Block.
Which rule is matching for Block? again look at the relevant log entry!
Which rule is matching for Block? again look at the relevant log entry!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
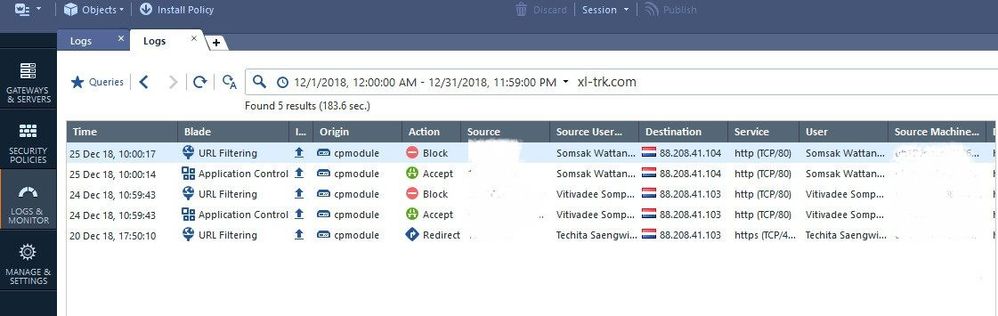
How can we filter the application with xl-trk.com? Because I need to retrieve the historical data that relevant to this log entry. It will help me faster to query.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Easiest way is double-clicking the view on the relevant row.
But you can try free text search...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
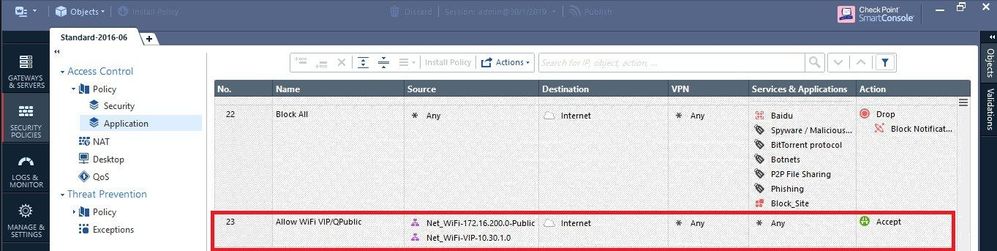
Hi Norbert
Please see screenshots as below
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
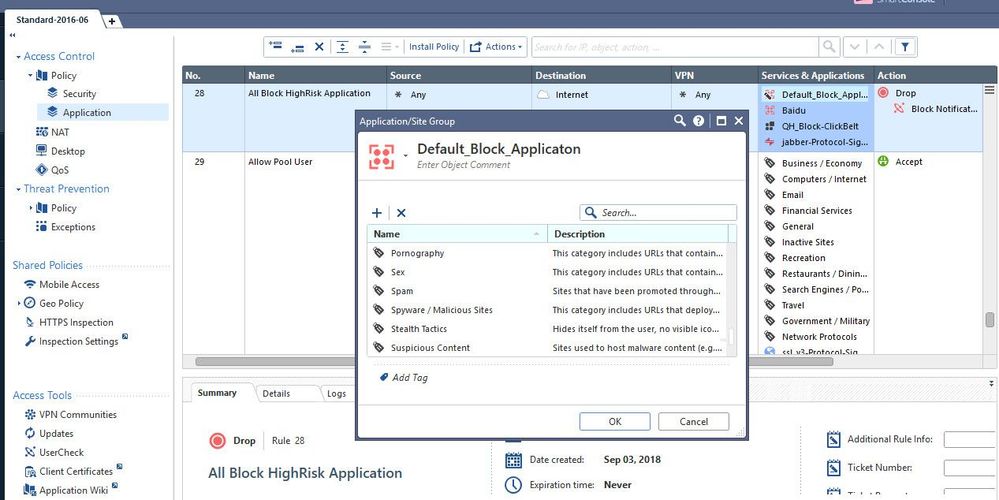
So as we see now, the Allow came from a rule matching only for 2 of your WiFi networks with Any Application and other sources are blocked from a rule further down, which Blocks the Spam category (besides others).
So that's why you see both actions in your view/report, because some were Allowed and others Blocked. So everything correct!
So that's why you see both actions in your view/report, because some were Allowed and others Blocked. So everything correct!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Maybe you're right. I will give you an example to check if my understanding is correct.
If I create the application rules one for source A to dest Z with action allow and one for source B to dest Z with action drop, where Z is spam site or else this means I will see application name (Z), category "Spam" with both action in my report, right?
If I create the application rules one for source A to dest Z with action allow and one for source B to dest Z with action drop, where Z is spam site or else this means I will see application name (Z), category "Spam" with both action in my report, right?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
correct
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Norbert
Thank you for your great help and clarifying
Thank you for your great help and clarifying
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 8 | |
| 7 | |
| 5 | |
| 5 | |
| 5 | |
| 5 | |
| 5 | |
| 4 | |
| 4 | |
| 4 |
Upcoming Events
Tue 16 Sep 2025 @ 02:00 PM (EDT)
Securing Applications with Check Point and AWS: A Unified WAF-as-a-Service Approach - AmericasWed 17 Sep 2025 @ 04:00 PM (AEST)
Securing Applications with Check Point and AWS: A Unified WAF-as-a-Service Approach - APACWed 17 Sep 2025 @ 03:00 PM (CEST)
Securing Applications with Check Point and AWS: A Unified WAF-as-a-Service Approach - EMEAThu 18 Sep 2025 @ 03:00 PM (CEST)
Bridge the Unmanaged Device Gap with Enterprise Browser - EMEAThu 18 Sep 2025 @ 02:00 PM (EDT)
Bridge the Unmanaged Device Gap with Enterprise Browser - AmericasTue 16 Sep 2025 @ 02:00 PM (EDT)
Securing Applications with Check Point and AWS: A Unified WAF-as-a-Service Approach - AmericasWed 17 Sep 2025 @ 04:00 PM (AEST)
Securing Applications with Check Point and AWS: A Unified WAF-as-a-Service Approach - APACWed 17 Sep 2025 @ 03:00 PM (CEST)
Securing Applications with Check Point and AWS: A Unified WAF-as-a-Service Approach - EMEAThu 18 Sep 2025 @ 03:00 PM (CEST)
Bridge the Unmanaged Device Gap with Enterprise Browser - EMEAThu 18 Sep 2025 @ 02:00 PM (EDT)
Bridge the Unmanaged Device Gap with Enterprise Browser - AmericasAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter