- Products
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Maestro Madness
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- General Topics
- :
- Re: Remote Access to Server in Other Office
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Remote Access to Server in Other Office
Hi all. We have a monitoring server I need to give my colleagues in the US access to. I thought it would be a simple thing to allow but it seems not (or I'm completely missing something).
My colleagues are connecting from home to the VPN of our US office, so of course they're getting an IP from the US VPN pool.
The server is in our UK office.
My firewall rule for the US gateway:
US VPN Pool > UK Monitoring server > Office VPNs > HTTP/HTTPS > Accept > Log
My firewall rule for the UK gateway:
US VPN Pool > UK Monitoring server > Office VPNs > HTTP/HTTPS > Accept > Log
Traffic is getting dropped however. I must be missing something I just don't know what. Looking at the logs it says 'Encryption Failure: According to the policy the packet should not have been decrypted'
Any help would be hugely appreciated,
10 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I'm actually looking into doing the same but inclined to say that this is not possible with the Checkpoint domain based VPN setup. As we would have to route traffic through two VPN communities (RemoteAccess & OfficeVPN).
With regular S2S VPNs you can accomplish this by using a Star VPN community and allowing the satellite GWs to route through the center GW to the other satellites. I'm struggling to see how we could achieve something similar with the Remote Access VPN.
With regular S2S VPNs you can accomplish this by using a Star VPN community and allowing the satellite GWs to route through the center GW to the other satellites. I'm struggling to see how we could achieve something similar with the Remote Access VPN.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Many years ago I accomplished this by configuring the VPN domain for the Europe site so it was working and installed the policy to the Europe gateway, then modified the VPN domain for the US site and installed the policy there.
Whenever I wanted to install a security policy to the other VPN site I had to change the VPN domain before installing it. This wasn't much work to do before each policy installation but most importantly the final result was that it worked. This was back in the R65.x days. Now in the R80.x days I would prepare this within two scripts (one of the Europe and one for the US site), put them into the script repository of SmartConsole and run these when I want to install a policy. The script would then modify the VPN domain to my required configuration and initiate the policy installation.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
When both the US and the UK Firewall are part of the same management domain, just make both gateways part of the remote access VPN community. This way you will use secondary connect, this means when the client needs to connect to a server in the UK, the client will build it's own tunnel to the UK FW, same for the US.
You do need to make sure that on each gateway you setup the Remote Access VPN Domain topology, this should only contain those networks/hosts that should be accessible for that site.
You do need to make sure that on each gateway you setup the Remote Access VPN Domain topology, this should only contain those networks/hosts that should be accessible for that site.
Regards, Maarten
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Remote Access VPN is an additional license correct? The customer is my scenario is using Endpoint Security and Remote Access VPN is only setup in the US, not UK. If purchasing additionally licenses for the UK is required for this to work as required, I don't have a problem with that. Sucks that with a route based VPN you could simply route this traffic no problem. In my experience, Checkpoint's routed based VPN functionality has not been the best.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
When you have the remote access VPN license, that is applied to the Management server and is counted per client. the license is also measured that way, a user can be connected twice, once to the US and once to the UK. The newer license is measured per gateway on concurrent connections and requires a license per connection.
Regards, Maarten
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks Maarteen. Just to clarify, this would the mobile access license, correct? Looking in SmartUpdate, I see mobile access licenses for 200 users in the license description for the UK firewall. In that case, I should have no problem adding the UK firewall to the remote access VPN community?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
That would indeed be my understanding as well.
Regards, Maarten
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Sweet! Thank you very much for your assistance!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Well you could also access through the SMTP and the other's 3rd party accessible software. It depends on your need that what you have to do by the accessing server in other office. You have to decide and give the permission to access it well.
Hope it would be helpful you too.
Regrads
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
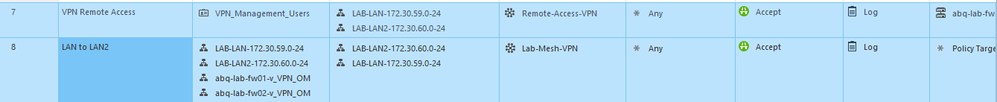
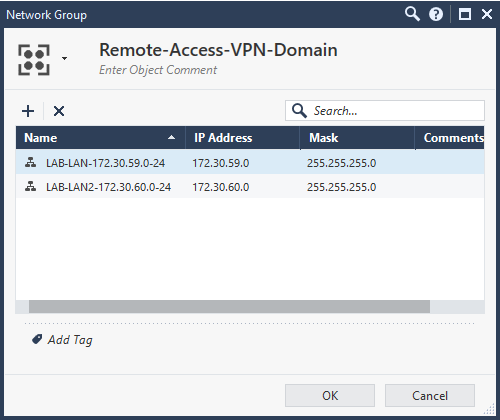
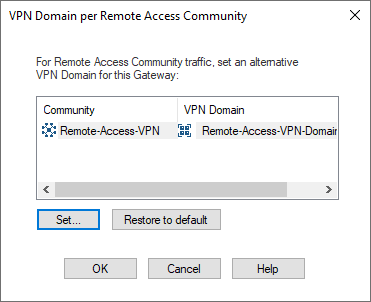
I labbed this up and did some additional research. Turns out, the key here is in the Gateway Cluster Properties under Network Management > VPN Domain > Set domain for Remote Access Community. You can then click on the Remote Access community, click set and specify the VPN domain. What I did was create a new network group with the networks in the US and the networks in the UK that remote users needed to access as this setting dictates what routes are installed in the remote users routing table. From here, you need to ensure the remote users IP pool is included in the local encryption domain on the US gateway and if the UK firewall is a third party device, you'll need to ensure the remote users IP pool is included in their remote encryption domain.
Then you'll need to rules, one allowing remote access and one allowing access over the S2S VPN to the UK. The first rule is installed on the US GW and the second rule is installed on on both GWs. You may be able to get away with one rules but this setup worked for me.
In my screenshots, "LAN-LAN-172.30.59.0-24" is the US LAN, "LAB-LAN2-172.30.60.0-24" is the UK LAN. "VPN_Management_Users" is an access role with the remote VPN users.
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 11 | |
| 9 | |
| 9 | |
| 8 | |
| 6 | |
| 3 | |
| 2 | |
| 2 | |
| 2 | |
| 1 |
Upcoming Events
Tue 16 Dec 2025 @ 05:00 PM (CET)
Under the Hood: CloudGuard Network Security for Oracle Cloud - Config and Autoscaling!Thu 18 Dec 2025 @ 10:00 AM (CET)
Cloud Architect Series - Building a Hybrid Mesh Security Strategy across cloudsTue 16 Dec 2025 @ 05:00 PM (CET)
Under the Hood: CloudGuard Network Security for Oracle Cloud - Config and Autoscaling!Thu 18 Dec 2025 @ 10:00 AM (CET)
Cloud Architect Series - Building a Hybrid Mesh Security Strategy across cloudsThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter