- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity AI Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
CheckMates Fest 2026
Join the Celebration!
AI Security Masters
E1: How AI is Reshaping Our World
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
R82.10 and Rationalizing Multi Vendor Security Policies
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- General Topics
- :
- Re: Remote Access and Site-to-Site VPN access rest...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Remote Access and Site-to-Site VPN access restriction
Dear Mates
I have currently migrated our VPN solution to Check Point. However, I have been experiencing some issues when it comes to restricting access to specific machines.
For example, if I set the VPN domain on the Gateway to 10.10.0.0/24 which is a network behind the gateway. And then create a firewall policy for remote users to access only 10.10.0.20/32, the remote users are also being able to access other hosts in 10.10.0.0/24 network like 10.10.0.22/32 , even if I only use a single host as a destination.
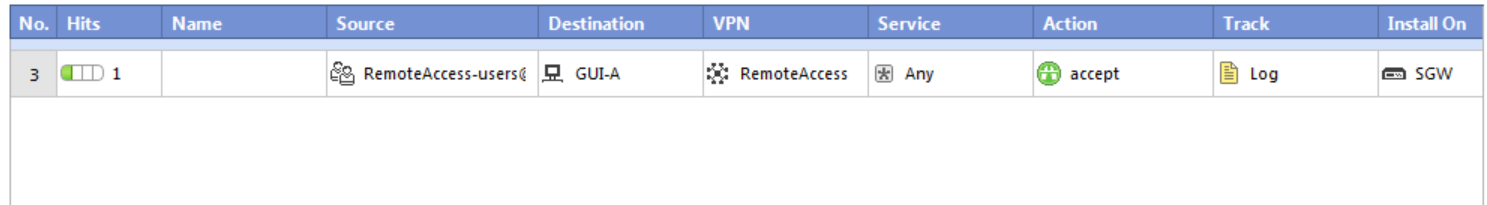
In the figure above, the RemoteAcess-users, are also being able to access other machines on the defined VPN domain apart from GUI-A.
Does this mean that remote users can access any machine in the VPN domain?
Any ideas on how this issue could be resolved, in such a way remote users only access the machines defined in the Destination field of the Firewall Policy?
Site-to-Site VPN
The same behavior is happening in site-to-site VPN, I only specified on host in the source, but other host can also access the remote machines even if they are not specified as source.
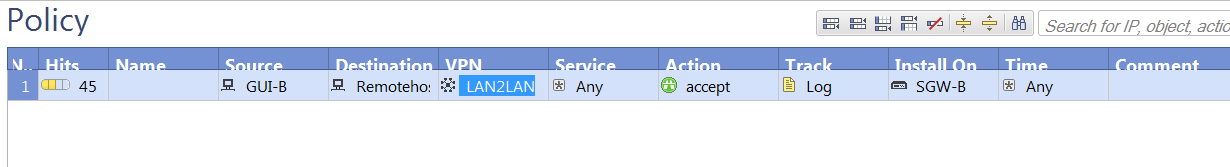
Thanks in advance
10 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
1. Please check logs and find out which firewall rule is allowing such traffic (if all rules have enabled logging).
2. Send us screenshot of "GUI-A" and "GUI-B" hosts.
3. Check NAT rules if there are any.
Kind regards,
Jozko Mrkvicka
Jozko Mrkvicka
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi there
There is only one rule. And when such communication happen, I don't see the logs in SmartView tracker. I'm starting to wondering if it's not an implicit rule.
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
In this case try to enable logging of Implied rules from Global Settings and install the database (of course firewall itself).
Stupid question, but it happened to me few times - are you checking the correct gateway ? Try to do tcpdump to confirm that you see some traffic during test, and issue "fw stat" to find which policy package is used for this cluster.
Kind regards,
Jozko Mrkvicka
Jozko Mrkvicka
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The traffic seems to be accepted by an implied rule (see the figure below). The question is, where can i find the implied rule number 0? is it the first one in the implicit rules (File->View->implied rules)?

Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Isnt IP 10.10.1.3 one of cluster members? Is this IP part of Topology ?
usually traffic going from cluster members is going via Implied Rules.
Also, try some real traffic, like ssh or https, not ping.
Kind regards,
Jozko Mrkvicka
Jozko Mrkvicka
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
its not a cluster. I am using two separated gateways.
10.10.1.3 is a host which is part of the topology of the remote peer.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10.10.1.3 must be included only in local VPN encryption domain of SGW-B (also part of Topology).
10.10.0.10 must be included only in remote VPN encryption domain of VPN-PEER.
Kind regards,
Jozko Mrkvicka
Jozko Mrkvicka
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You were right.
I enabled Web services on the 10.10.0.10, and I tried to access it using http from a remote client and access was not granted. I tried to ping it, it worked.
I guess this issue is only related to Ping.
Why is that ping is accepted by the implied rule even if the destination is not specified in the firewall policy?
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Di Junior,
Please check if you have Accept ICMP requests enabled, or not. These are the default settings for all implied rules:
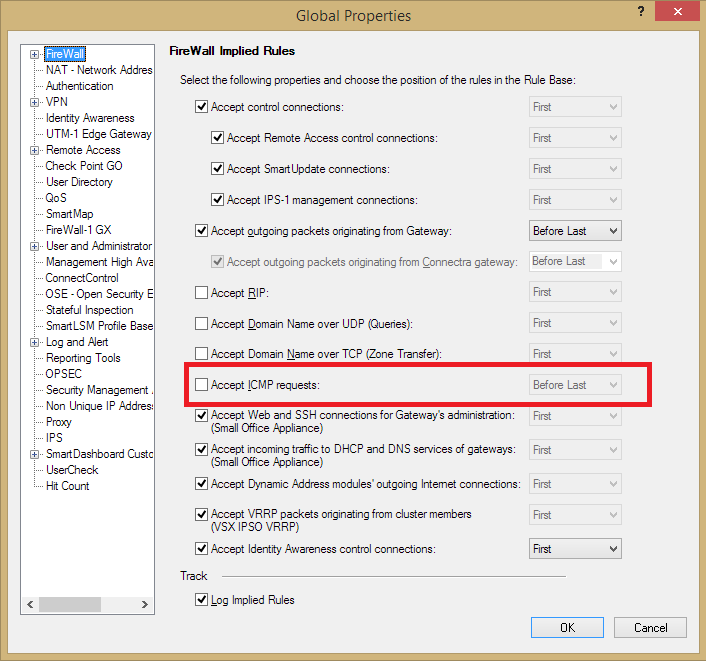
Kind regards,
Jozko Mrkvicka
Jozko Mrkvicka
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
0 - Implied rules - it represents all of implied rules, you would need to check Global properties or Implied rules themselves to understand which setting exactly allows this traffic. But usually it's not difficult to determine.
I would like to point to another possibility, which is not your case obviously, but just worth mentioning.
Accept all encrypted traffic option might be enabled in comunity properties.
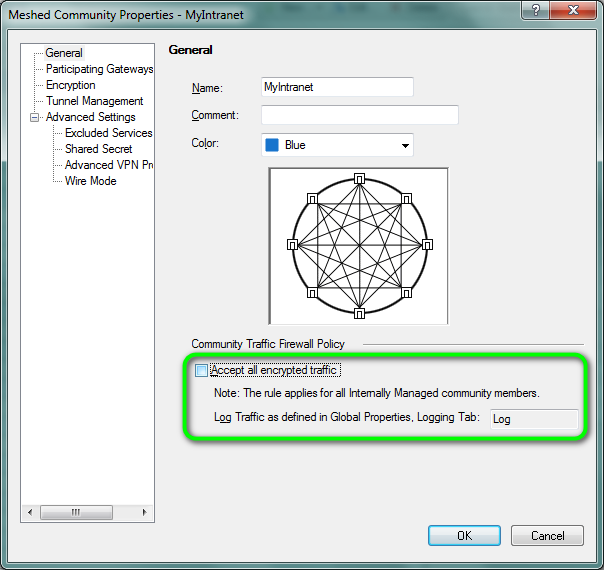
Which will result in the following rule, which is visible in policy by default (not like implied rules).

Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 15 | |
| 11 | |
| 6 | |
| 3 | |
| 3 | |
| 2 | |
| 2 | |
| 2 | |
| 2 | |
| 2 |
Upcoming Events
Thu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldFri 09 Jan 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 42: Looking back & forwardThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: Exposing AI Vulnerabilities: CP<R> Latest Security FindingsThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldFri 09 Jan 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 42: Looking back & forwardThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter


