- Products
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
What's New in R82.10?
10 December @ 5pm CET / 11am ET
Improve Your Security Posture with
Threat Prevention and Policy Insights
Overlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Maestro Madness
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- General Topics
- :
- Re: R80.x - Performance Tuning Tip - SecureXL Fast...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jump to solution
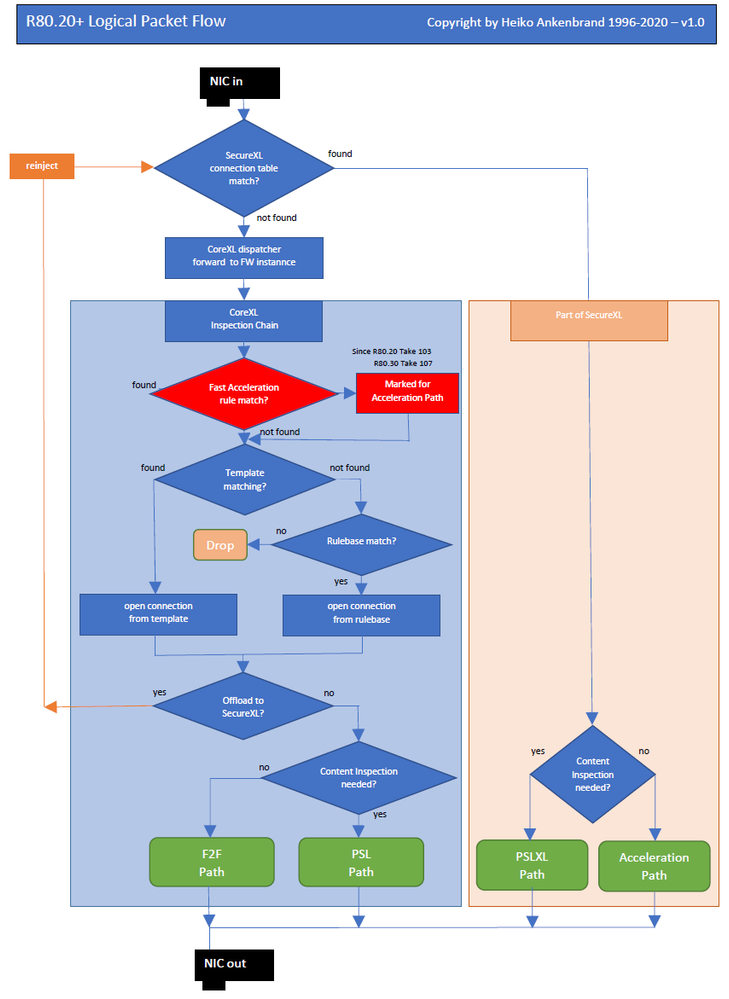
R80.x - Performance Tuning Tip - SecureXL Fast Accelerator (fw ctl fast_accel)
The Fast Acceleration (picture 1 green) feature lets you define trusted connections to allow bypassing deep packet inspection on R80.20 JHF103 and above gateways. This feature significantly improves throughput for these trusted high volume connections and reduces CPU consumption.
The CLI of the gateway can be used to create rules that allow you to bypass the SecureXL PSLXL path to route all connections through the fast path.
Tip 1
Use this function to exclude IP's or networks from deep inspection.
Picture 1
Here you can see the complete packet flow in detail : R80.x - Security Gateway Architecture (Logical Packet Flow)
I will update the document to this new function in the next few days.
Feature Attributes:
- Configured from the gateway's CLI.
- Can be turned On / Off, Off is the default.
- Rules can be added / deleted by demand.
- Configuration (State / rules) survive reboot.
- Maintain rule hit count (does not survive reboot).
- Every configuration change done by the user is logged in $FWDIR/log/fw_fast_accel.log file.
Feature Usage:
fw ctl fast_accel <option>
| Option | Explanation |
| add | Add a connection |
| delete | Delete a connection |
| enable | Set feature state to on |
| disable | Set feature state to off |
| show_table | Display the rules configured by the user |
| show_state | Display the current feature state |
| reset_stats | Reset the statistics collected by the feature |
| --help/-h | Display help message |
To create fast_accel rules, read more in this sk156672 - SecureXL Fast Accelerator (fw fast_accel) for R80.20 and above.
➜ CCSM Elite, CCME, CCTE ➜ www.checkpoint.tips
- Tags:
- performance
47 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I just wondered if it would be possible to arrange a webbinar regarding fast acceleration feature 🙂 by someone who understands it inside out 🙂
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Got it. Let me see what we can do here
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
That would be a really good idea.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi community,
Does the command take destination port range or "any" as parameter?
Thanks in advance.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
"any" is possible and a list of ports like "443,4434,445". I'm not sure if a range like "400-450", never tried
SecureXL Fast Accelerator (fw fast_accel) for R80.20 and above
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
As far as I know, no range is possible.
➜ CCSM Elite, CCME, CCTE ➜ www.checkpoint.tips
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Just checked this on R81.10 Jumbo HFA Take 30, and ranges are not possible with any parameter including port number. You also can't specify more than one destination port or IP address in a single add operation with a comma or any other character from what I can see.
Gaia 4.18 (R82) Immersion Tips, Tricks, & Best Practices Video Course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
For logs see:
sk173324 - Drop log for connection that is accelerated by fast_accel
➜ CCSM Elite, CCME, CCTE ➜ www.checkpoint.tips
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
How do you understand these statements from the Introduction section of sk156672 - SecureXL Fast Accelerator (fw fast_accel) for R80.20 and above?
- Fast Accel enforces only rule base that does not require deep packet inspection (For example: Application Control, URL Filtering and content-awareness are not included).
For the other cases: Fast accel rules are prioritized over the access rule base.
Do you think that the writers of the SK meant that fast_accel makes the firewall to skip deep packet inspection listed (For example: Application Control, URL Filtering and content-awareness)?
What could they mean by "the other cases"?
I guess "Fast accel rules are prioritized over the access rule base." could mean that fast_accel overrides the deep packet inspection by skipping it.
Unfortunately I do not have a good experience with the "Give us feedback" function in the SK.
* Sometimes they give some additional information by email but they do not modify the SK.
* Once they even asked me what they should put into the article when I needed Check Point's opinion.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You said: "I guess "Fast accel rules are prioritized over the access rule base." could mean that fast_accel overrides the deep packet inspection by skipping it."
This guess is correct, fast_accell allows bypassing medium path, accelerating specific traffic through SecureXL only even if the policy requires any kind of deeper inspection.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Traffic that would otherwise be processed in the Medium Path (both passive & active streaming) can be forced into the accelerated path with fast_accel. Traffic that would normally go F2F cannot be forcibly accelerated in this way.
Gaia 4.18 (R82) Immersion Tips, Tricks, & Best Practices Video Course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
Since the fast_accel traffic is bypassing the deep packet inspection. Does it mean, that when its policy is using for example Application Control, URL filtering or Anti-Virus. It will not filter by the following blades that requires deep packet inspection?
How do you determine the rule base which does not need deep packet inspection.
Thank you.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Correct, even if the policy is calling for some form of deep inspection via APCL/URLF/AV if that traffic is fast_accel'd it won't occur. As such fast_accel should only be used between somewhat trusted systems, and should most definitely NOT be used for traffic communicating with untrusted areas such as the Internet.
Gaia 4.18 (R82) Immersion Tips, Tricks, & Best Practices Video Course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I thought it was the other way around, that the connection had to already be excluded from IPS, HTTPS and other types of inspection or fast_accel would not work on it. At least, that seems to match my recollection for setting it up on R80.40 a couple of years ago: We had to write exception rules for IPS and HTTPS inspection to exclude the connections, along with the fast_accel rules, or they would not be accelerated.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
What you are remembering is that F2F/slowpath traffic cannot be forced fathpath with fast_accel. You can configure it but it simply will not work. Traffic that would otherwise go Medium Path Active Streaming (HTTPS Inspection mainly) and Medium Path Passive Streaming (most blades) can most definitely be forced to the fastpath with fast_accel.
Gaia 4.18 (R82) Immersion Tips, Tricks, & Best Practices Video Course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Can anyone confirm support for fastxl in CloudGuard gateways?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yes, it should work in CloudGuard gateways as well.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @Don_Paterson,
"fast_accel" always works on all gateways (CloudGuard, Open Server, Appliance, VMWare,...) where SecureXL is enabled.
➜ CCSM Elite, CCME, CCTE ➜ www.checkpoint.tips
- « Previous
-
- 1
- 2
- Next »
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 37 | |
| 21 | |
| 9 | |
| 7 | |
| 7 | |
| 5 | |
| 5 | |
| 4 | |
| 4 | |
| 4 |
Upcoming Events
Wed 26 Nov 2025 @ 12:00 PM (COT)
Panama City: Risk Management a la Parrilla: ERM, TEM & Meat LunchWed 03 Dec 2025 @ 10:00 AM (COT)
Última Sesión del Año – CheckMates LATAM: ERM & TEM con ExpertosThu 04 Dec 2025 @ 12:30 PM (SGT)
End-of-Year Event: Securing AI Transformation in a Hyperconnected World - APACThu 04 Dec 2025 @ 03:00 PM (CET)
End-of-Year Event: Securing AI Transformation in a Hyperconnected World - EMEAThu 04 Dec 2025 @ 02:00 PM (EST)
End-of-Year Event: Securing AI Transformation in a Hyperconnected World - AmericasWed 03 Dec 2025 @ 10:00 AM (COT)
Última Sesión del Año – CheckMates LATAM: ERM & TEM con ExpertosThu 04 Dec 2025 @ 12:30 PM (SGT)
End-of-Year Event: Securing AI Transformation in a Hyperconnected World - APACThu 04 Dec 2025 @ 03:00 PM (CET)
End-of-Year Event: Securing AI Transformation in a Hyperconnected World - EMEAThu 04 Dec 2025 @ 02:00 PM (EST)
End-of-Year Event: Securing AI Transformation in a Hyperconnected World - AmericasWed 26 Nov 2025 @ 12:00 PM (COT)
Panama City: Risk Management a la Parrilla: ERM, TEM & Meat LunchAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter