- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
Quantum SD-WAN Monitoring
Register HereCheckMates Fest 2026
Watch Now!AI Security Masters
Hacking with AI: The Dark Side of Innovation
MVP 2026: Submissions
Are Now Open!
Overlap in Security Validation
Help us to understand your needs better
CheckMates Go:
R82.10 and Rationalizing Multi Vendor Security Policies
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- General Topics
- :
- Re: R80.x - Performance Tuning Tip - Control Secur...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
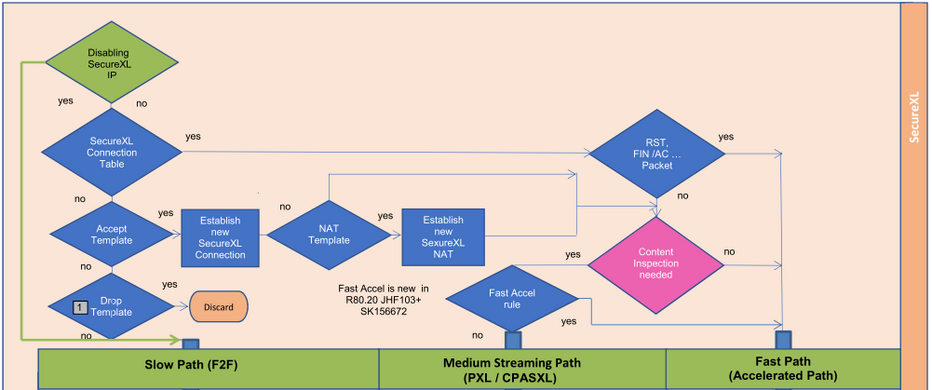
R80.x - Performance Tuning Tip - Control SecureXL / CoreXL Paths
|
Disabling SecureXL for traffic sent from/to specific IP |
|---|
Disabling SecureXL for traffic sent from/to specific IP addresses might be needed when it is not possible to disable SecureXL completely due to high traffic load on Security Gateway. This will route all packets through the F2F path (picture 1 green).
Tip 1
How to disable SecureXL for specific IP addresses? Edit the relevant table.def file, define the IP addresses, whose traffic should not be accelerated. More read here sk104468.
Picture 1
|
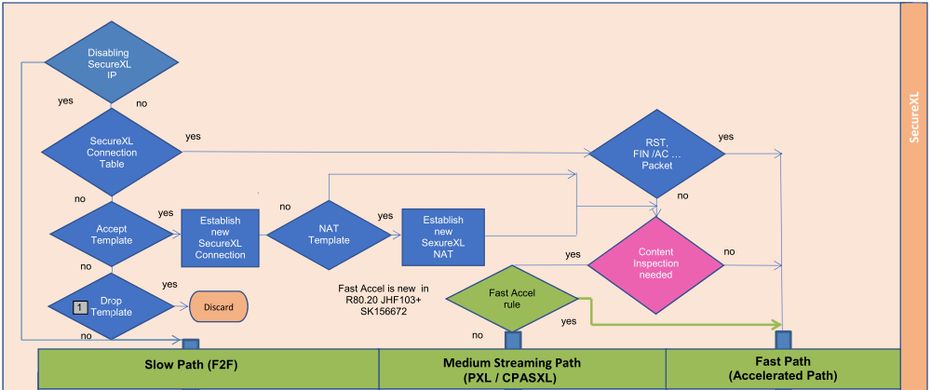
Fast Acceleration |
|---|
The Fast Acceleration (picture 2 green) feature lets you define trusted connections to allow bypassing deep packet inspection on R80.20 Take 103/ R80.30 Take 107 and above gateways. This feature significantly improves throughput for these trusted high volume connections and reduces CPU consumption.
The CLI of the gateway can be used to create rules that allow you to bypass the SecureXL PSLXL path to route all connections through the fast path.
Tip 2
Use this function to exclude IP's or networks from deep inspection.
Picture 2
Feature Attributes:
- Configured from the gateway's CLI.
- Can be turned On / Off, Off is the default.
- Rules can be added / deleted by demand.
- Configuration (State / rules) survive reboot.
- Maintain rule hit count (does not survive reboot).
- Every configuration change done by the user is logged in $FWDIR/log/fw_fast_accel.log file.
Read more here to create fast_accel rules: sk156672 - SecureXL Fast Accelerator.
Tip 3
Here you can see the complete packet flow in detail: R80.x - Security Gateway Architecture (Logical Packet Flow)
➜ CCSM Elite, CCME, CCTE ➜ www.checkpoint.tips
8 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Is there also a hotfix for r80.10 to use fast accel?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yes this feature exists in R80.10 but the command is sim fastaccel, you will need R80.10 Jumbo HFA 177+ installed to use it. More info: sk139772: SecureXL Fast Accelerator (sim fastaccel) for Non Scalable Platforms R77.30/R80.10
Gaia 4.18 (R82) Immersion Tips, Tricks, & Best Practices Video Course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This is super cool!
Would be neat if we could add groups of stuff to table.def. Like "Skype Traffic".
Then maybe we wouldn't kill all Skype call traffic each time we push policy!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Maybe, even with traffic matching fast_accel SecureXL still has to be restarted every time policy is pushed in R80.10 and earlier. Due to the new F2V path in R80.20+, SecureXL is not restarted every time policy is pushed on R80.20+.
Gaia 4.18 (R82) Immersion Tips, Tricks, & Best Practices Video Course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
SecureXL has been significantly revised in R80.20.
Yes, it's great that SecureXL is not restarted anymore in R80.20+.
In R80.40 there will be some new interesting features 🙂
➜ CCSM Elite, CCME, CCTE ➜ www.checkpoint.tips
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello,
How can we notice the secure Xl was restarted or not ?
Thank you so much .
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I looked into this and at least in R80.20+ there does not seem to be any log events kept about SecureXL being enabled/disabled via fwaccel off/on. SecureXL can't really be completely and permanently disabled in R80.20+ anyway. In R80.10 and earlier I vaguely remember seeing some kind of message in /var/log/messages any time SecureXL state was toggled, but I may just be remembering the message issued when the SIM driver initializes on bootup.
Gaia 4.18 (R82) Immersion Tips, Tricks, & Best Practices Video Course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
👍
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 12 | |
| 8 | |
| 7 | |
| 6 | |
| 5 | |
| 5 | |
| 4 | |
| 3 | |
| 3 | |
| 3 |
Upcoming Events
Thu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationTue 27 Jan 2026 @ 11:00 AM (EST)
CloudGuard Network Security for Red Hat OpenShift VirtualizationThu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: Exposing AI Vulnerabilities: CP<R> Latest Security FindingsThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationTue 27 Jan 2026 @ 11:00 AM (EST)
CloudGuard Network Security for Red Hat OpenShift VirtualizationThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter