- Products
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
10 December @ 5pm CET / 11am ET
Announcing Quantum R82.10!
Learn MoreOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Maestro Madness
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- General Topics
- :
- Re: R80.20 - IP blacklist in SecureXL
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
R80.20 - IP blacklist in SecureXL
Controls the IP blacklist in SecureXL. The blacklist blocks all traffic to and from the specified IP addresses.
The blacklist drops occur in SecureXL, which is more efficient than an Access Control Policy to drop the packets.
This can be very helpful e.g. with DoS attacks to block an IP on SecureXL level.
For example, the traffic from and to IP 1.2.3.4 should be blocked at SecureXL level.
On gateway set the IP 1.2.3.4 to Secure XL blacklist:
# fwaccel dos blacklist -a 1.2.3.4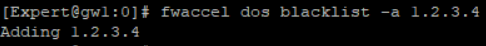
On gateway displays all IP's on the SecureXL blacklist:
# fwaccel dos blacklist -s

On gateway delete the IP 1.2.3.4 from Secure XL blacklist:
# fwaccel dos blacklist -d 1.2.3.4

Very nice new function in R80.20!
Furthermore there are also the Penalty Box whitelist in SecureXL.
The SecureXL Penalty Box is a mechanism that performs an early drop of packets that arrive from suspected sources. The purpose of this feature is to allow the Security Gateway to cope better under high traffic load, possibly caused by a DoS/DDoS attack. The SecureXL Penalty Box detects clients that sends packets, which the Access Control Policy drops, and clients that violate the IPS protections. If the SecureXL Penalty Box detect a specific client frequently, it puts that client in a penalty box. From that point, SecureXL drops all packets that arrive from the blocked source IP address. The Penalty Box whitelist in SecureXL lets you configure the source IP addresses, which the SecureXL Penalty Box never blocks.
More under this link:
Command Line Interface R80.20 Reference Guide
Regards,
➜ CCSM Elite, CCME, CCTE ➜ www.checkpoint.tips
23 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You need to use this function with LOTS of care, as it is even less visible that SAM rules...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@_Val_ , speaking of SAM rules, they are visible in SmartView Monitor, as I am pretty sure you know, and I think it would be a grand idea of including the blacklist and whitelist entries in there as well, possibly in the form of the rules.
Would logging the events associated with whitelisted and blacklisted IPs with, perhaps, heavily suppressed logs be possible?
Are there OS syslog events associated with these actions?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@Vladimir Are you referring to SmartViewMonitor legacy GUI client? If so, I would be very surprised if any inclusions are event possible with R80 family
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@_Val_ , whyever not? This is still the UI for the Monitoring blade in R80.30.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Once again, I am asking which specific UI you are referring to, one of SmartConsole tabs or to SmartViewMonitor. When you answer, I can explain 🙂
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
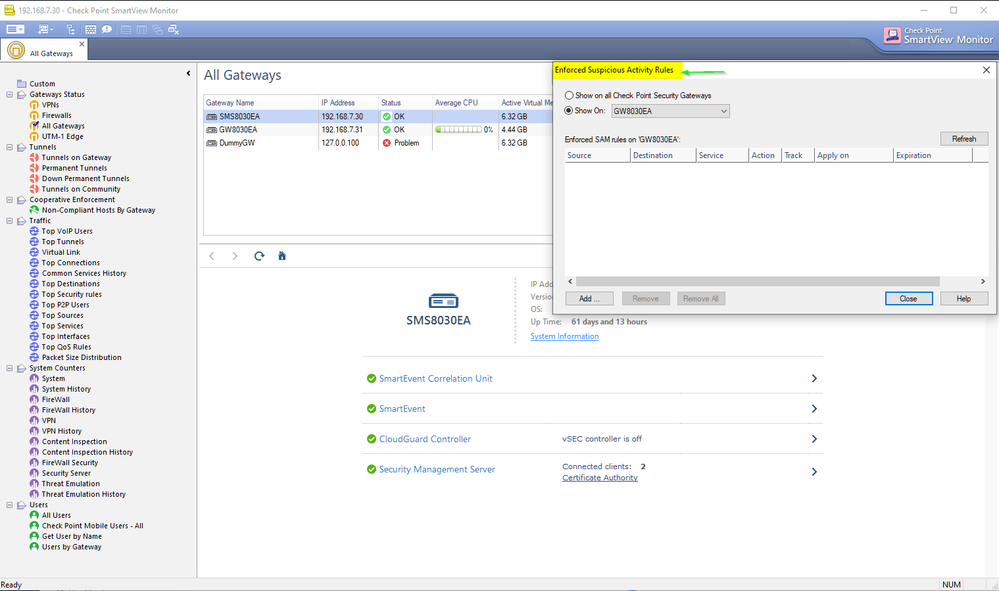
I am talking about SAR portion of the SmartViewMonitor:
I do not see the SAR in the Device and License Information of the SmartConsole:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Good, this is what I thought you did, @Vladimir 🙂
This is a legacy client which will be let go at some point. You already have some of its functionality ported to SmartConsole. Personally, I cannot expect anything new being added there.
How about adding SAM rules and blacklists visibility as a SmartConsole Extension? All you need is some API magic
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@_Val_ , nothing against using API for added capabilities, but not as the replacement of the core capabilities of the earlier version.
Consider: the SAM rules creation, visibility and alerting were built-in R77. Every client had an out of the box ability to take advantage of those. Now, unless you are willing to built something for each client, they are lacking features.
Additionally, (and I may be wrong here), aren't SmartConsole extensions not inherited during upgrade to a new versions?
I have similar take on everything that is not embedded in the product: blacklists, custom scripts, GUIDBedits, kernel parameter tuning, etc.. Haven't you ever came into the environment with the systems modified up-to wazoo and poorly documented?
If we are to rely on these means and methods, all of the changes should somehow, (and ideally) , be noted by the system, auto-documented and exportable.
With the average lifespan of CP equipment of 5 to 7 years before upgrade and average duration of the security admins employment of 2 years these days, things will fall through the cracks.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Bug or feature?
It is also possible to enter networks. In the handbook there is unfortunately only the IP Address in it and not the network.
It is also suggested that the network is be created. But it will unfortunately not be displayed afterwards![]() .
.
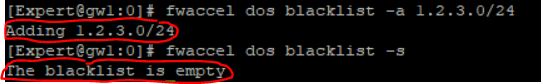
Regards,
➜ CCSM Elite, CCME, CCTE ➜ www.checkpoint.tips
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content

Kind regards,
Jozko Mrkvicka
Jozko Mrkvicka
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
How is this different to SAM?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The blacklist/whitelist is only IP level (either SecureXL drop this IP always or never subject this IP to the Penalty Box).
fw sam and fw samp allow configuring more granular rules.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I agree with Dameon here. Here is a link to sam penalty box sk that has been around for quite a while:
What is the SecureXL penalty box mechanism for offending IP addresses?
I think the new command is very good for effectively blocking individual IP addresses. For example a DoS attack from a few IP addresses or similar opportunities.
And I also agree with Valeri, the function is to be used with care. Many users will not know it yet and it is also not very transparent visible.
➜ CCSM Elite, CCME, CCTE ➜ www.checkpoint.tips
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I also find it interesting that it still works when I disable SecureXL in R80.20. I wouldn't have expected that at this point![]() .
.

➜ CCSM Elite, CCME, CCTE ➜ www.checkpoint.tips
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Heiko, blacklists continue to work after SecureXL is disabled in R80.20+ because of the same behavior in the SK below with drop templates, basically all packets associated with a new connection (no connections table match) are always sent to the firewall workers first for handing.
sk150812: High CPU when traffic is dropped by fw_workers
Gaia 4.18 (R82) Immersion Tips, Tricks, & Best Practices Video Course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
In real life, if you are facing DDoS attack (or broadcast storm), you are not able to log into system anyway (lagging, freezing, not able to execute any single command). Happened to me 2 times. The only solution was to find a root cause and cut that machine. So from logical point of view the better solution would be to move this feature into SmartConsole (some hidden place ![]() ) and push the command via SIC with triple confirmation alerts.
) and push the command via SIC with triple confirmation alerts.
Kind regards,
Jozko Mrkvicka
Jozko Mrkvicka
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I think that's gonna be a fundamental discussion. From my point of view, DDoS attacks should be blocked at the provider. You can discuss it for a long time.
If I can't get login to the system during an attack, of course I can't do much.
Everything should be configured on the firewall first. Then I don't have the problems later.
I like the option to block IP's on SecureXL level. It is simple and effective.
I think the following function "Accelerated SYN Defender" is the better choice for DoS attacks (SYN Flood attack) on Check Point gateways with enabled SecureXL.
A TCP SYN Flood attack occurs when a host, typically with a forged IP address, sends a flood of TCP [SYN] packets. Each of these TCP [SYN] packets is handled as a connection request, which causes the server to create a half-open (unestablished) TCP connection. This occurs because the server sends a TCP [SYN+ACK] packet, and waits for a response TCP packet that does not arrive. These half-open TCP connections eventually exceed the maximum available TCP connections that causes a denial of service condition. The Check Point Accelerated SYN Defender protects the Security Gateway by preventing excessive TCP connections from being created. The Accelerated SYN Defender uses TCP [SYN] Cookies (particular choices of initial TCP sequence numbers) when under a suspected TCP SYN Flood attack. Using TCP [SYN] Cookies can reduce the load on Security Gateway and on computers behind the Security Gateway. The Accelerated SYN Defender acts as proxy for TCP connections and adjusts TCP {SEQ} and TCP {ACK} values in TCP packets.
You can find more in the manual under:
"fwaccel synatk"
Regards,
➜ CCSM Elite, CCME, CCTE ➜ www.checkpoint.tips
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
HI Guys,
I always use the following commands to drop ips, subnets, ports and a list of known IPs. See sk67861.
| Command | Description |
sim dropcfg | Configures drop parameters (run 'sim dropcfg') |
sim dropcfg -h | Prints the help message with available options for 'dropcfg' parameter |
sim dropcfg -l | Prints current drop configuration |
sim dropcfg -f </path_to/file_name> | Sets drop configuration file |
sim dropcfg -e | Enforces drop configuration on the external interface only |
sim dropcfg -y | Avoids confirmation |
sim dropcfg -r | Resets drop rules |
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
1) The sim dropcfg command is not available in R80.20
2) Refer to the R80.20 Performance Tuning Administration Guide to see all relevant commands.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
just wanted to note that the blacklist with IPs added to the blacklist with
fwaccel dos blacklist -a 1.2.3.4
do not survive a reboot
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hey Sergey
I see accelerated drops were remove from SecureXL in R80.20
Are there any plans to bring it back?
Regards, Manuel
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This is fantastic feature and thanks for sharing.
BTW is there any limitation for number of IP addresses inr fwaccel dos blacklist chain?
BTW is there any limitation for number of IP addresses inr fwaccel dos blacklist chain?
Thanks and Regards,
Blason R
CCSA,CCSE,CCCS
Blason R
CCSA,CCSE,CCCS
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello,
I actually find a limit of 16384 IPs, when my script try to insert the next IP, the response is:
ERROR: IOCTL command CPHWD_IOCTL_DOS_BLACKLIST_ADD to firewall instance 0 was not successful (data->rc = CPHWD_IOCTL_RC_ERROR)
Regards.
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 17 | |
| 17 | |
| 8 | |
| 7 | |
| 7 | |
| 4 | |
| 3 | |
| 3 | |
| 2 | |
| 2 |
Upcoming Events
Fri 12 Dec 2025 @ 10:00 AM (CET)
Check Mates Live Netherlands: #41 AI & Multi Context ProtocolTue 16 Dec 2025 @ 05:00 PM (CET)
Under the Hood: CloudGuard Network Security for Oracle Cloud - Config and Autoscaling!Fri 12 Dec 2025 @ 10:00 AM (CET)
Check Mates Live Netherlands: #41 AI & Multi Context ProtocolTue 16 Dec 2025 @ 05:00 PM (CET)
Under the Hood: CloudGuard Network Security for Oracle Cloud - Config and Autoscaling!Thu 18 Dec 2025 @ 10:00 AM (CET)
Cloud Architect Series - Building a Hybrid Mesh Security Strategy across cloudsAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter