- Products
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Maestro Madness
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- General Topics
- :
- Propose your Idea of the Year!
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Propose your Idea of the Year!
Yes, this is this time of year, again.
Same as one year ago, we turn to the community and ask you, good folks, to propose the idea of the year. Or, better:
The Idea Of The Year!
The rules are the same as before, it is about ideas that you wish Check Point would develop into a product/service offering, or improvements to existing ones.
Do you think we miss something important or we should consider to expand our product portfolio, feature set, functionalities, get to a completely new playground, change the rules of the game?
Tell us NOW!
A few disclaimers/notes:
- There are no guarantees that any idea suggested will be developed, even the "Idea Of The Year",
- From the suggestions below, we will choose 3-5 ideas which will be put up for voting later on,
- Preference will be given to ideas that come from customers and partners, though employees are welcome to participate as well.
- "Likes" and "discussion" around specific ideas will influence (but not wholly determine) the final list, so if you like something someone has suggested, let it be known!
@Dorit_Dor and R&D leaders will choose the best ideas, and if you win, you will get a prize! What prize? We will tell you later.
Get creative, use your imagination and PROPOSE!
75 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@HeikoAnkenbrand- I fussed to the powers that be at CPX360 in Vegas this year about how bad it is to troubleshoot what can end up being tiny issues. Troubleshooting VPNs is a royal pain in the ethernet interface.
I wouldn't get my hopes up that changes will be coming soon. But they did note that they were working on a new interface for the VPN side of things.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
VPN runs in SecureXL and CoreXL (more see here in my article R80.x Security Gateway Architecture (Logical Packet Flow))
From my point of view it is relatively easy to enable VPN debugging from the management server on a gateway. I have also written a script for this on the CLI (more see here: GAIA - Easy execute CLI commands on all gateways simultaneously).
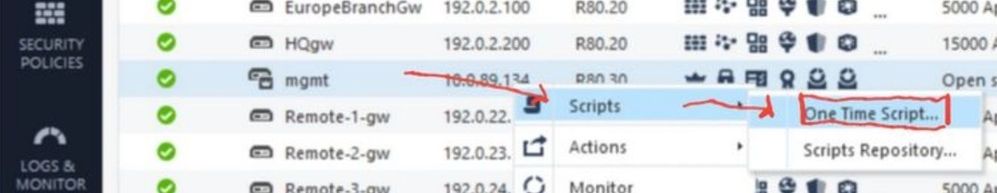
Furthermore, you can already execute scripts via the SmartConsole on the gateway. This could be used to enable VPN debugging. Therefore a part is already present (see picture). Now you only have to transfer the log data of the files ike.elg and ikev2.xml to the SmartConsole. Now you have to analyze the log data like with IKEVIEW in the SmartConsole.
From my point of view, Check Point should be able to integrate this into the SmartConsole.
Regards
Heiko
➜ CCSM Elite, CCME, CCTE ➜ www.checkpoint.tips
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@HeikoAnkenbrand- no disagreement from me.
At the end of the day there are far too many steps necessary to "enable" advanced troubleshooting in Gaia.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
We're supposed to be wishes and ideas.
With version R85 or R90 😀 this is already possible.
➜ CCSM Elite, CCME, CCTE ➜ www.checkpoint.tips
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@HeikoAnkenbrand- I've been posting wishes and ideas.
Sorry they're so advanced that we will have to wait 20 years to see them! 🙂
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I see this topic coming very out of bounds - people started with 1 - 3 ideas per posting, but meanwhile, people write long lists reminding me of the letters with wishes for Xmas... This makes it nearly impossible just to give a Kudo to a brilliant idea as the post contains more than twenty, so you also have to post und clutter all up.
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
SDWAN
VXLAN
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@Ruta_Thornber Something is coming soon, stay tuned
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
1. Have all the modifications to the kernel parameters, configuration files, scripts, affinity configurations, etc.. that are done in addition to the actions available via SmartConsole or WebUI to be compiled in the exportable archive for each device and presented in a readable form from the right click menu of the Check Point objects in SmartConsole.
2. Have SAM rules to be present on demand (if manually toggled) in the rulebase in the expandable section. Have dynamic indicator icon on the GW objects show up when SAM rules are triggered.
3. Enable DNS proxy functionality to improve function and logging of DNS trap protections when DNS servers are on the same network as the clients.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Change the red "X" on the gateways that fail to download latest signature updates to something less threatening.
It throws off the focus of admins as well as TAC (had my fare share of this first hand), when troubleshooting TP issues.
It will also be beneficial to improve the situation with the TP and the entitlements updates. Their availability, to put it mildly, could be better.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I can save you one request for next year 🙂
We are in advanced stages of a new elastic update server so i expect no failures in the future
The new server is expected to be ready in a month or so and the change should be transparent to customers (they will get the new update server automatically once its ready).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Allow recovery/viewing of IKE pre-shared secrets, this is a major pain during firewall replacement projects and typically forces coordination with external partners/vendors which is a bottleneck to the whole process. There is no reason to secure this information from an authorized GUI administrator; making it visible in the SmartConsole or via some kind of CLI tool would be great. I realize this will entail a rework of how the pre-shared keys are stored since they appear to be kept as some kind of one-way hash.
- When a monitored interface is declared as DOWN by ClusterXL, provide more information about *why* in commands like cphaprob -a if. Physical link failure/flap? Cluster members can't seem to see each other at all? High CCP loss due to mulitcast mode causing switch forwarding issues? No other responding hosts detected on that interface at all? Bond problem? It is a guessing game right now.
- When ClusterXL Cluster Under Load (CUL) is active, display a notification or color change on the Gateways & Servers tab of SmartConsole or make this an alertable event.
- Want to echo Danny's request for a packet tracer type functionality that integrates all the disparate tools like the following, if the packet is dropped by any Check Point code show why similar to fw ctl zdebug drop:
- Packet receipt and its attributes (use pinj and include connection UUID too)
- What processing path is it assigned to and why (SXL/PXL/F2F/CPASXL/PSLXL/etc.)
- Antispoofing check result
- Geo Policy check result
- Connections state table lookup result
- If new connection, initial Firewall/Network policy matched rule (fw up_execute or Packet Mode search)
- NAT rule matched or cached hit from fwx_cache
- Subject to decryption by IPSec/HTTPS Inspection?
- What blades are assigned to inspect this connection's traffic at iI (or inbound side of SecureXL) and result from each
- Routing lookup result (ip route get) or PBR result if present
- What blades are assigned to inspect this connection's traffic at oO (or outbound side of SecureXL) and result from each
- Subject to encryption by IPSec/HTTPS Inspection?
- Packet leaves and its attributes & UUID
- Big honking warnings ("Wide Impact" Icon?) or extra confirmation on the Global Properties NAT screen prior to turning off "translate destination on client side" or "Automatic ARP Configuration" which will cause instant death for all NATs on most firewalls upon policy install, or a slow painful death of all NATs over the period of 4 hours, respectively.
- Provide the built-in ability to easily perform a "clusterXL_admin down/up" command from the R80+ SmartConsole (yes you could run a one-time script to do this). When a cluster member is stopped/started from the old SmartView Monitor it performs a cphastop/cphastart which is NOT the same thing.
-In a firewall traffic log entry, always update it with the egress interface even if Accounting is not enabled. This will allow immediate verification that the firewall itself routed the traffic correctly by looking at logs.
- Provide a SmartConsole alarm/status alert if overall packet loss at the network level on a firewall's interface (RX-DRP/RX-ERR/RX-OVR) exceeds some ridiculously high configurable threshold like 5% for an extended period.
Gaia 4.18 (R82) Immersion Tips, Tricks, & Best Practices Video Course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
A very simple idea.
Please add pipe and grep to clish. It would be very useful in restricted environments without bash access.
Maybe a specialiced one like other cli vendors do:
clish>show configuration | include "this\|or this"
clish>show configuration | exclude "this\|or this"
clish>show configuration | include "this" | include "then this"Or fully grep
clish>show configuration | grep "this\|or this"
clish>show configuration | grep -v "this\|or this"
Best regards
Alois
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I've posted a couple other times about how the OS being different for the SMB appliances and the bigger gateways is annoying. Here's another one I'd like to see added - Dynamic objects.
You can't do a domain dynamic object. Which is painful because with systems like Azure and AWS being so dynamic you are really hamstrung at writing effective rules when IP's are changing all the time.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
1) A "Do nothing" / "No Action" action for the SSL Inspection Policy so we have a proper way to bypass traffic without doubts.
2) A SOAR (Security Orchestration Automation and Response) product would be amazing, DevSecOps is becoming hot, I think that would be a really nice addition to the Check Point portfolio.
____________
https://www.linkedin.com/in/federicomeiners/
https://www.linkedin.com/in/federicomeiners/
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
A dark mode / soft tones for Smart Console would be awesome.
- « Previous
- Next »
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 14 | |
| 10 | |
| 9 | |
| 7 | |
| 6 | |
| 3 | |
| 2 | |
| 2 | |
| 2 | |
| 2 |
Upcoming Events
Fri 12 Dec 2025 @ 10:00 AM (CET)
Check Mates Live Netherlands: #41 AI & Multi Context ProtocolTue 16 Dec 2025 @ 05:00 PM (CET)
Under the Hood: CloudGuard Network Security for Oracle Cloud - Config and Autoscaling!Fri 12 Dec 2025 @ 10:00 AM (CET)
Check Mates Live Netherlands: #41 AI & Multi Context ProtocolTue 16 Dec 2025 @ 05:00 PM (CET)
Under the Hood: CloudGuard Network Security for Oracle Cloud - Config and Autoscaling!Thu 18 Dec 2025 @ 10:00 AM (CET)
Cloud Architect Series - Building a Hybrid Mesh Security Strategy across cloudsAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter