- Products
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- Learn
- Local User Groups
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
- Partners
- More
- ABOUT CHECKMATES & FAQ
- Sign In
- Leaderboard
- Events
The Great Exposure Reset
24 February 2026 @ 5pm CET / 11am EST
CheckMates Fest 2026
Watch Now!AI Security Masters
Hacking with AI: The Dark Side of Innovation
CheckMates Go:
CheckMates Fest
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- General Topics
- :
- Re: Package processing
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Package processing
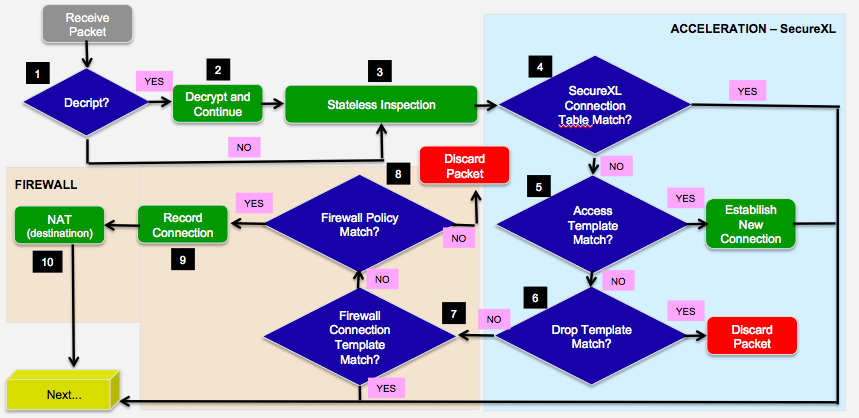
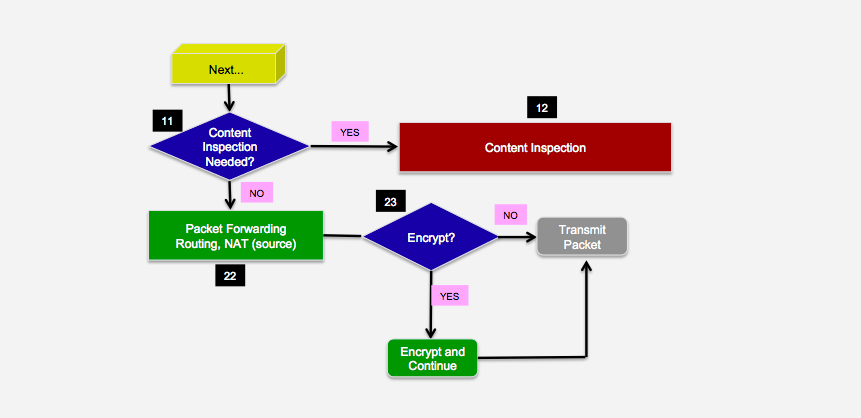
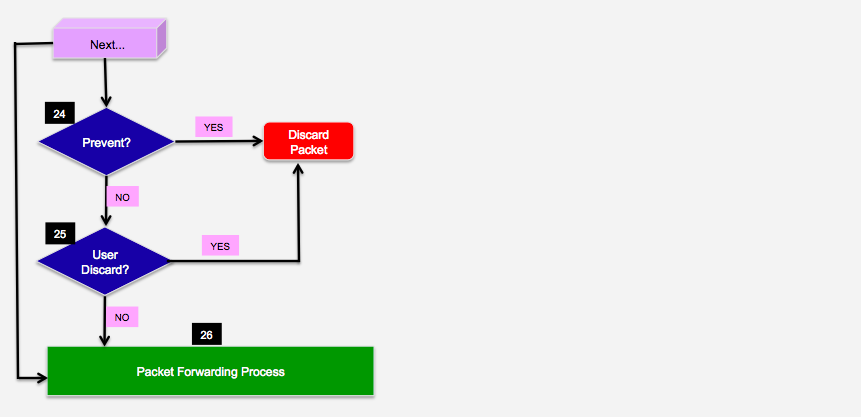
Hello friends, can anyone help me understand the flow of packets in the gateway?I'm studying on the subject.
Objectively, what happens at each stage?I inserted numbers to facilitate.
Thank You.
11 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Most everything is explained here:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Carlos,
Your drawing must have been hard work. Thanks for that! But I think we should not confuse the users with too many different flowcharts.
I've been trying for a long time to create a reasonable overview R80.x Security Gateway Architecture (Logical Packet Flow) . Here Valeri Loukine from Check Point supported me very well in backround and we tried to find an error-free flow. That was hard work and thanks again to Valeri Loukine, Dameon and Moti.
History:
09-27-2017 - Moti. published the original article for R77.x:
Checkmates: Check Point Threat Prevention Packet Flow and Architecture
07-29-2018 - I tried to write a new article for R80.x and Valeri Loukine supported me.
R80.x Security Gateway Architecture (Logical Packet Flow)
08-06-2018 - Valeri Loukine has reworked the original article for R80.x by Moti.:
Security Gateway Packet Flow and Acceleration - with Diagrams
And here are the references to the other sources for the flowchart:
SecureKnowledge: Best Practices - Security Gateway Performance
Download Center: R80.10 Next Generation Threat Prevention Platforms
Download Center: R77 Security Gateway Packet Flow
Download Center: R77 Security Gateway Architecture
Support Center: Check Point Security Gateway Architecture and Packet Flow
Checkmates: Check Point Threat Prevention Packet Flow and Architecture
Checkmates: fw monitor inspection point e or E
Checkmates: Infinity NGTP architecture
Checkmates: R80.x Security Gateway Architecture (Content Inspection)
Regards
➜ CCSM Elite, CCME, CCTE ➜ www.checkpoint.tips
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank You Helko.
These images removed from some slides that I am preparing for a presentation. So it is "broken" into several.
I'll take a look at the message history. My intention is to use the numbers to remove some doubts. I've been looking at some documents but I had some doubts.
For example:Is the first packet "arriving" in the Firewall accelerated? Or should the first packet go through the Firewall that will perform the filters?What happens in step 5?
Thank You!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Just a clarification on the following:
>>>08-06-2018 - Valeri has reworked the original article for R80.x by Moti:
Security Gateway Packet Flow and Acceleration - with Diagrams
Actually, my post is based on SK articles Moti mentioned in his post. Re-work usually means something else.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks for the answer. I've been looking at this document and I had some doubts. For example: Is the first packet "arriving" in the Firewall accelerated? Or should the first packet go through the Firewall that will perform the filters? But once, thank you.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Rather than us trying to look through your diagram and explain, it would be better if you just plainly state the questions you have.
This way, we're answering the right questions ![]()
However, I do recommend reading through the referenced documents, which does answer many of the questions you are likely to have.
But to answer your specific question here:
In Step 5-6 in your diagram, this is happening in SecureXL.
If the initial packet matches an accept/drop template, then the initial packet (and subsequent ones) will be accelerated.
If the packet does not match an accept or drop template, then the initial connection packet is sent F2F (not accelerated).
It's possible that later we determine the connection is eligible for acceleration, in which case future packets on that connection will be accelerated.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks for the answer. I've been looking at this document and I had some doubts. For example: Is the first packet "arriving" in the Firewall accelerated? Or should the first packet go through the Firewall that will perform the filters? But once, thank you.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Please do not use pre-formatted in the comments, it is impossible to read it. I have edited your fond out above.
The answers to your question are already in the documentation. Please look here: ATRG: SecureXL
Part 4 with diagrams addresses this particular question.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Carlos,
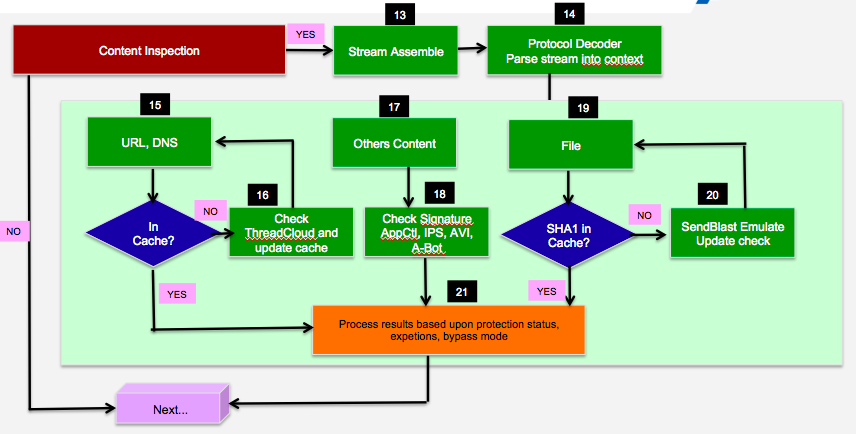
I don't think you can draw a reasonable flowchart in the area of content inspection. That's why I left it out of my Flowcharts. The problem is that a strong difference has to be made between Passive Streaming Library (PSL for F2F Path ,PXL for medium path) and Active Streaming (CPAS) . You describe PSL and PXL here? Real one must stand with SecureXL strongly differentiate whether it goes the F2F path, PXL path or the Acceleration path (without content inspection).
In the firewall chain you can see the PSL (PXL) and CPAS modules:
# fw ctl chain
...
in chain:
...
14: 7f730000 (ee3485a0) (00000001) passive streaming (in) (pass_str)
15: 7f750000 (ee55b7d0) (00000001) TCP streaming (in) (cpas)
...
out chain:
...
3: - 1fffff0 (ee55ba00) (00000001) TCP streaming (out) (cpas)
13: 7f700000 (ee55bbf0) (00000001) TCP streaming post VM (cpas)
...
There is another problem at the waypoint "Protocol Decoder". This is where Context Management Infrastructure (CMI) comes in. The "Protocol Decoder" does not assemble files, URL's and DNS requests. It only recognizes the protocols. The RAD daemon (DNS and URL) or the DLPU daemon (files) assemble the informations for evaluation of further blades RAD for (AntiBot, AntiVirus, URLF,...) and DLPU for (TED). There are other daemons in play here, too.
I once tried to summarize that in an overview. But I don't think you can reproduce this 100% in a drawing either. Here is the link to the article: R80.x Security Gateway Architecture (Content Inspection)
Personally, I would not try to map the content inspection path as a flowchart.
You have a lot of work in the flowchart, so once again a lot of respect from my side.
Regards,
➜ CCSM Elite, CCME, CCTE ➜ www.checkpoint.tips
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello Heiko Ankenbrand, thank you for your help and response. Big hug.
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 22 | |
| 21 | |
| 13 | |
| 9 | |
| 8 | |
| 8 | |
| 8 | |
| 8 | |
| 7 | |
| 7 |
Trending Discussions
Upcoming Events
Thu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: AI-Generated Malware - From Experimentation to Operational RealityFri 13 Feb 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 43: Terugblik op de Check Point Sales Kick Off 2026Thu 19 Feb 2026 @ 03:00 PM (EST)
Americas Deep Dive: Check Point Management API Best PracticesThu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: AI-Generated Malware - From Experimentation to Operational RealityFri 13 Feb 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 43: Terugblik op de Check Point Sales Kick Off 2026Thu 19 Feb 2026 @ 03:00 PM (EST)
Americas Deep Dive: Check Point Management API Best PracticesAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter