These three oneliners allow you to reset the passwords of all users in the SmartConsole or to restrict access of all users.
Important!
If you run this onliner on the Smart Center Server, all users settings will be changed accordingly.
You should therefore back up the management server first. More read here:
- sk108902: Best Practices - Backup on Gaia OS (I would recommend a snapshot or a migrate server export of the SMS.)
Set all users to ‘undefined’
|
This onliner sets all users defined in the SmartConsole under ‘User’ to ‘undefined’ as bulk operation.
This means that users can no longer log in using their username and password.
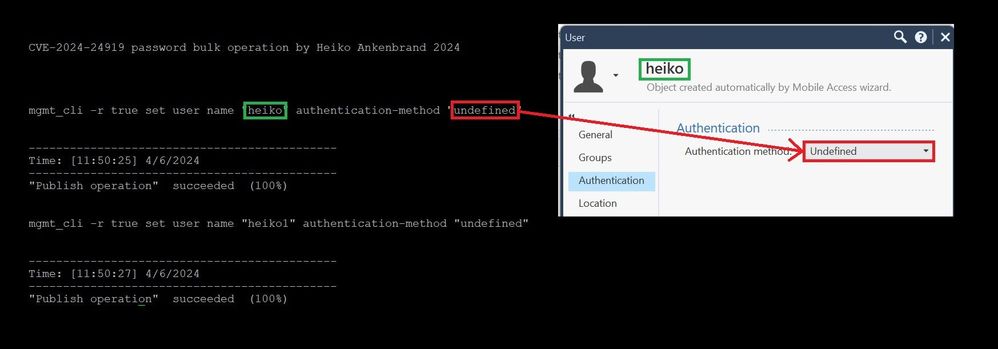
1) Execute this oneliner on SMS
clear; echo -e "CVE-2024-24919 password bulk operation by Heiko Ankenbrand 2024\n\n";mgmt_cli -r true show users details-level "full" limit 500 offset 0 | grep name | grep -v SMC | awk '{split($0,a," "); print a[2]}' |sed 's/\"//g' |sed 's/\n//' | tr -d '\r' |awk '$test=$0;{system("echo -n $test")}' >user.txt ; for i in $(cat user.txt); do test1=" ende"; test="mgmt_cli -r true set user name \""${i}"\" authentication-method \"undefined\""; echo -e "\n\n${test}";$test; done;
2) Install the policy in the SmartConsole after you have run this onliner
Set all user to the same password
|
This onliner sets all users defined in the SmartConsole under ‘User’ to default password as bulk operation.
This means that all users then have the password they have set.
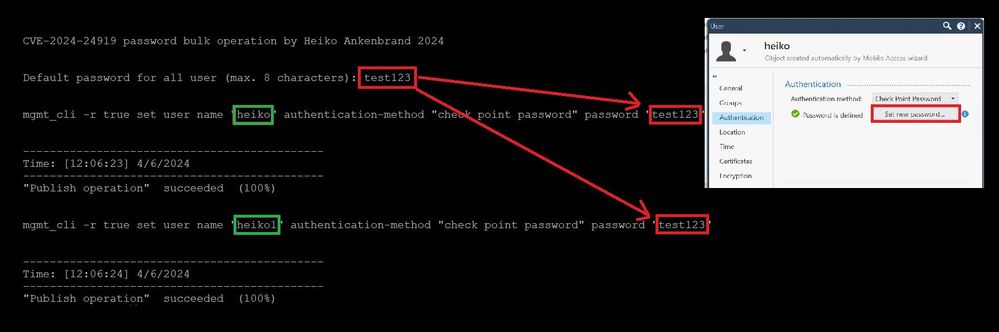
1) Execute this oneliner on SMS
clear; echo -e "CVE-2024-24919 password bulk operation by Heiko Ankenbrand 2024\n\n";read -p "Default password for all user (max. 8 characters): " pass;mgmt_cli -r true show users details-level "full" limit 500 offset 0 | grep name | grep -v SMC | awk '{split($0,a," "); print a[2]}' |sed 's/\"//g' |sed 's/\n//' | tr -d '\r' |awk '$test=$0;{system("echo -n $test")}' >user.txt ; for i in $(cat user.txt); do test1=" ende"; test="'mgmt_cli -r true set user name \""${i}"\" authentication-method \"check point password\" password \""${pass}"\"'"; test=${test//\'}; echo -e "\n\n${test}"; echo $test |awk '{system($0)}'; done;
2) Install the policy in the SmartConsole after you have run this onliner
Set all users to random passwords
|
This onliner sets all users defined in the SmartConsole under ‘User’ to random password as bulk operation.
This means that all users are set to a ‘random’ password. An overview of the set passwords is shown in the file pass.txt.
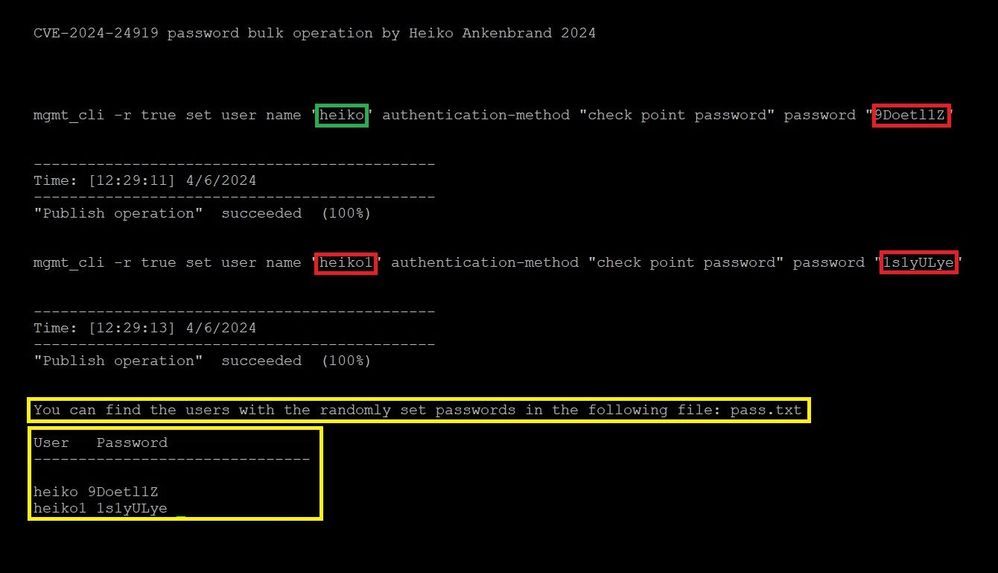
1) Execute this oneliner on SMS
clear; echo "" > pass.txt; echo -e "CVE-2024-24919 password bulk operation by Heiko Ankenbrand 2024\n\n";mgmt_cli -r true show users details-level "full" limit 500 offset 0| grep name | grep -v SMC | awk '{split($0,a," "); print a[2]}' |sed 's/\"//g' |sed 's/\n//' | tr -d '\r' |awk '$test=$0;{system("echo -n $test")}' >user.txt ; for i in $(cat user.txt); do pass=$(tr -dc A-Za-z0-9 </dev/urandom | head -c 8;); test="'mgmt_cli -r true set user name \""${i}"\" authentication-method \"check point password\" password \""${pass}"\"'"; test=${test//\'}; echo -e "\n\n${test}"; echo $test |awk '{system($0)}'; echo "${i} ${pass}" >> pass.txt; done; echo -e "\n\nYou can find the users with the randomly set passwords in the following file: pass.txt \n\nUser Password\n-------------------------------"; more pass.txt;
2) Install the policy in the SmartConsole after you have run this onliner
➜ CCSM Elite, CCME, CCTE ➜ www.checkpoint.tips





