- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity AI Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
AI Security Masters
E1: How AI is Reshaping Our World
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Maestro Madness
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- General Topics
- :
- No authentication for port 18231 Policy Server Log...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
No authentication for port 18231 Policy Server Login (old)
Hello fellow community members!
Our security vulnerability scan has flagged that there is no authentication algorithm / ciphers for connections to port 18231 on our gateways (which according to the awesome diagram from Heiko Ankenbrand is "Policy Server Login (old)").
As we're using E80.xx Endpoint protect against a separate Policy server, I'm guessing we don't use this port any more (perhaps it was for the older R75 VPN client??).
Does anyone know of a way to secure this port, either by blocking it, or by making it offer secure SSL ciphers??
Regards,
Jason
12 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yes, with a SYN scan you see the port as open.
If you check the TLS certificates, you see an TLS handshake.
Afterwards the Check Point communication follow.
Regards
Heiko
➜ CCSM Elite, CCME, CCTE ➜ www.checkpoint.tips
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks Dameon Welch-Abernathy.
Do you know if the E80.xx client will have any issues with setting this to TLS1.2?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Possible some older VPN clients might.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Interesting. I applied the first two options in SK132712 to my R77.30 gateways, and the nmap scan has not shown any improvement.
PORT STATE SERVICE VERSION
18231/tcp open ssl/fw1-pslogon Check Point FireWall-1 Policy Server logon
| ssl-enum-ciphers:
| TLSv1.0:
| ciphers:
| TLS_DH_anon_WITH_3DES_EDE_CBC_SHA - F
| TLS_DH_anon_WITH_AES_128_CBC_SHA - F
| TLS_DH_anon_WITH_AES_256_CBC_SHA - F
| compressors:
| NULL
| cipher preference: client
|_ least strength: F
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
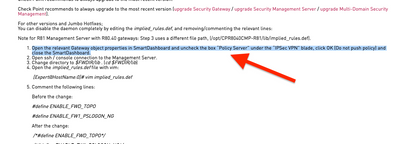
Any update here? We also performed the actions mentioned here:
for port 18231, but the port still shows as listening.
The following line was already commented out as follows:
/*#define ENABLE_FW1_PSLOGON_NG*/
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Just tried the same on 80.40 but without any apparent success either. Despite /*#define ENABLE_FWD_TOPO*/ and /*#define ENABLE_FW1_PSLOGON_NG*/ - validated on the MGR and on the two cluster members - the FW still listens on 18231 and fails basic PCI scan using Qualys.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Did you reboot or ran cpstop;cpstart after the modifying the files?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
We found that the port was disabled only after unticking Policy Server box and leaving it unticked. We didn't actually need Policy Server enabled. Otherwise the port would show as listening in netstat.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Strangely enough, that too is mentioned in the sk132712 you referenced above yourself.
Anyway, I am glad you have found the solution.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Also, read by the SK, you need to run additional modifications through SmartConsole
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Already did that obviously - multiple times.
But we found the issue: we had a old EXPLICIT policy rule active that allowed 18231 to connect to the FW. So the implicit rules were disabled but an explicit rule still existed.
In addition to that, the statemet in the SK "You can disable the daemon completely by editing the implied_rules.def, and removing/commenting the relevant lines:" is incorrect - all you remove is the _access_ to the daemon but the daemon is still started which you can easily ceck by running the netsat on the GW which still shows the daemon listening.
But at least the PCI scan now is ok with the FW
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 16 | |
| 10 | |
| 10 | |
| 8 | |
| 7 | |
| 3 | |
| 2 | |
| 2 | |
| 2 | |
| 1 |
Upcoming Events
Thu 18 Dec 2025 @ 10:00 AM (CET)
Cloud Architect Series - Building a Hybrid Mesh Security Strategy across cloudsThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldThu 18 Dec 2025 @ 10:00 AM (CET)
Cloud Architect Series - Building a Hybrid Mesh Security Strategy across cloudsThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter