- Products
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- Learn
- Local User Groups
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
- Partners
- More
- ABOUT CHECKMATES & FAQ
- Sign In
- Leaderboard
- Events
The Great Exposure Reset
AI Security Masters E4:
Introducing Cyata - Securing the Agenic AI Era
AI Security Masters E3:
AI-Generated Malware
CheckMates Go:
CheckMates Fest
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- General Topics
- :
- Re: MFA with Google Authenticator
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
MFA with Google Authenticator
This may come in handy for small scale implementations where RSA SecurID is too expensive of an option to consider.
33 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This is a good thing ; thanks.
Cybersecurity Evangelist, CISSP, CCSP, CCSM Elite
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You are welcome:)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Excellent contribution. Thank you very much Vladimir!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
It's very interesting. Is there any way to integrate it with Active directory / LDAP?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This is a very good and helpful documentation.
I will try it in a quiet minute in the LAB.
THX,
Heiko
➜ CCSM Elite, CCME, CCTE ➜ www.checkpoint.tips
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You are quite welcome.
I was kind-of hopeful that CP would provide native integration with 3rd party MFAs by now besides that of SecurID and/or not relying on sms.
Alas, we'll have to keep it on the wish list:)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Agreed on the 3rd party MFA option being out of the box for Checkpoint. Integrity of authentication systems is critical. Checkpoint is positioned in the best place on networks for MFA system security.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Vladimir,
this is very cool document. Looks like you tested solution with Endpoint Client, will this work with SNX?
I have same question as Claudio: can it be integrated with LDAP/AD instead of creating local account on Radius server?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Alex,
Off the top of my head, no reason it shouldn't, likely requiring you to append the generated pin code to the password.
As to integration with LDAP/AD, I am afraid it'll not work. The whole solution hinges on manipulating accounts local to RADIUS. If you are looking at something better integrated, I believe you are venturing into RSA SECURID category.
I've just checked and they seem to discounted their offerings to a much more reasonable rates:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Excellent article.
schalhoub
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks for an excellent guide.
Since FreeRADIUS 3.0 you need to add /3.0/ to the path of radius and PAM related commands.
Example from guide: "sudo nano /etc/freeradius/radiusd.conf"
should now be sudo nano /etc/freeradius/3.0/radiusd.conf
Same with PAM.
----------------
Related question.
I want to use Google Authenticator to add 2FA for remote access users when they connect with Check Point Mobile for Windows VPN client. Currently they log on with AD credentials only.
Could someone point me in the right direction to get there?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I just noticed my question was already asked in previous comments. That's unfortunate if it doesn't work. The customer had a Cisco ASA using AnyConnect together with Microsoft MFA before they changed to CheckPoint and I was certain it should not be a biggie to make it work on CheckPoint since it was so simple on the ASA.. But Microsoft MFA doesn't run with CheckPoint without client certificates from what I understood so this is why I turned to the FreeRADIUS solution.. It's a small client so I don't think paying for RSA is an option. I have some explaining to do 🙂
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@Ilmo_Anttonen , you can most definitely make it work with Azure MFA using NPS and NPS Extension for Azure MFA.
Please see the excellent article here for the non-vendor specific implementation: http://techgenix.com/azure-mfa-existing-vpn/
I probably was referring to the Google MFA in particular and even that has probably changed with time allowing for the integration with MS NPS (which is the MS free Radius service).
Regards,
Vladimir
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Ok! Many thanks I will check it.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
When you say "Same with PAM". I can't find anywhere in the PDF that mentions /etc/freeradius/pam and I don't see pam under 3.0 folder either.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
That is so wonderful.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This is a great guide and here is an important update for those who wish to use it.
If you use the latest LTS release of Ubuntu server (18.0.4) , you will have FreeRadius 3.0, and there is an issue in the PAM implementation, namely it's missing a symbolic link. After a bit of troubleshooting and Googling, I stumbled upon this:
https://enterpriseadmins.org/blog/virtualization/build-your-own-two-factor-authentication-server/
The solution described to manually add the symbolic link via the mentioned command and restart the FreeRadius service solved the issue and I have now RADIUS working on my new Ubuntu Server.
sudo ln -sf /etc/freeradius/3.0/mods-available/pam /etc/freeradius/3.0/mods-enabled/pam
This doesn't survive reboot, so depending of your implementation you will need to re-enter that command after each restart or find a way to automate it.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello @Vladimir ,
What do you mean by "small scale implementations" ? How many users?
I have a customer with ~900 vpn users and I want to understand this solution will handle this.
Thanks in advance.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Typically, organizations of that size invest in a better integrated platforms for MFA.
That being said, there is no reason why it would not work for 900 users (please do read the comments of users pointing out changes in the paths I have described that reflect new version of Free RADIUS).
-Vladimir
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
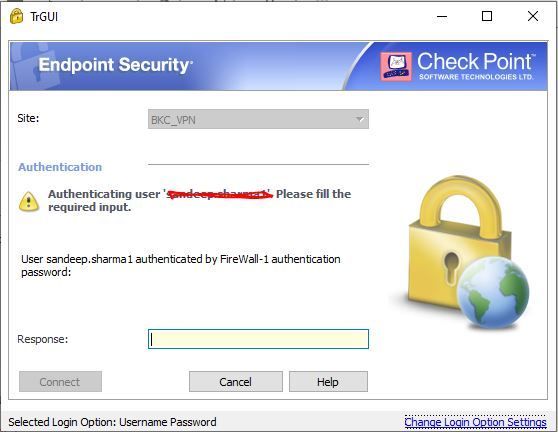
i have implemented MFA with Google Authenticator 1200 domain users & it's working perfectly.
SNX and endpoint security vpn both working perfectly!
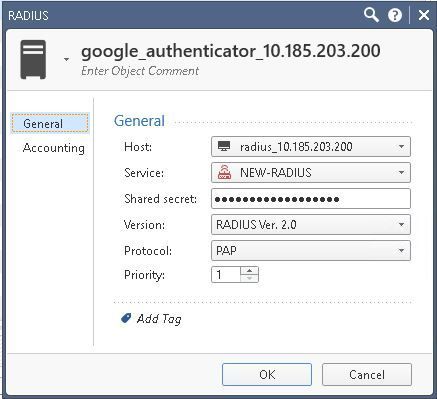
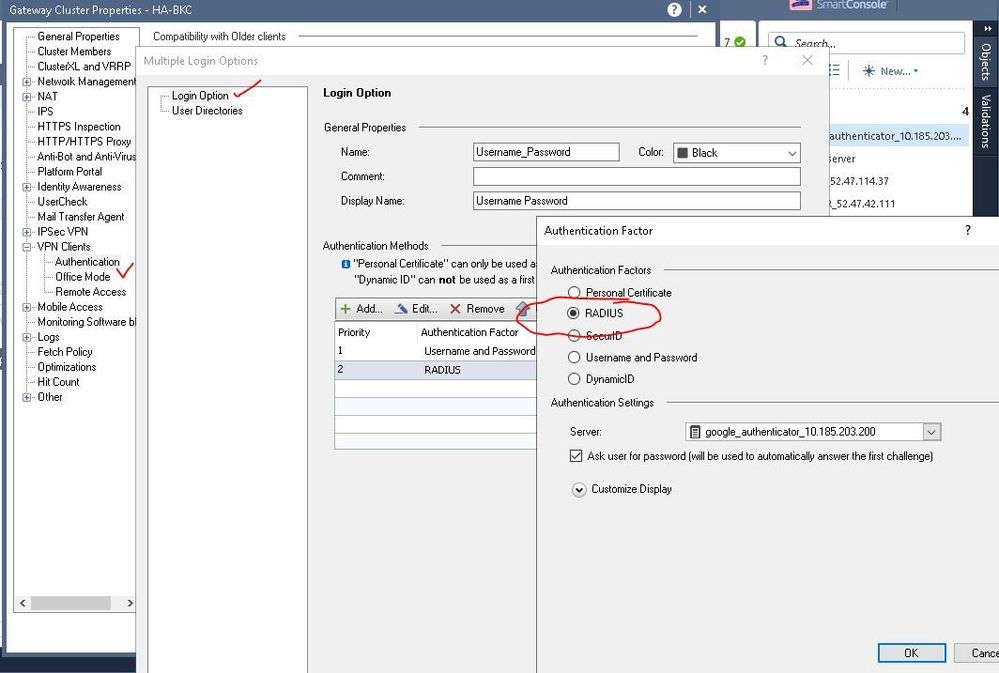
Radius server setting in checkpoint
MFA setting

Setup is FREERADIUS installed with Google authenticator following below link
https://www.petenetlive.com/KB/Article/0001256
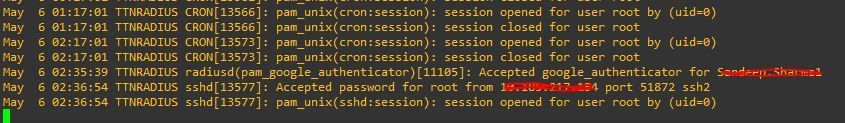
Radius server auth logs
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Sandeep,
We also trying to integrate the G-Auth with Checkpoint but not successful after many attempts. Can you please help me with checkpoint configuration related to G-Auth and FreeRadius server configuration. In my case we are using RHEL OS for Free Radius.
Thanks.
Saurabh
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Is that possible to implement the same solution using ubuntu 22.04/23.04 version. I tried the same steps but getting error.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello Praveena:
I believe I have the same problem. Do you solve the problem?
Regards,
Fabian
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Great Work Vladimir,
Just checking whether this document is still relevant in 2024 on R81.20?
Has Checkpoint finally made native support for Google Authenticator?
If not, does the document still work for the latest version of Ubuntu and it's RADIUS server?
Also, I can't seem to understand how this syncs with LDAP to AD.
Can I use this without creating local IDs?, as I purely want to use it for MFA for VPN users using Checkpoint Mobile.
Thanks!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
No "Native" support for Google Authenticator and this document should still apply.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks PhoneBoy,
How about linking with AD LDAP and using purely for 2FA for Remote Access VPN?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
According to the post above by @Sandeep_sharma, it should work in with AD LDAP as well. Please see his note about using updated FreeRADIUS installation instructions and note his configuration for Check Point RADIUS in screenshots.
This said, enough people asking about it for me to update my document for newer versions of Ubuntu and FreeRADIUS. You should see it in about a months. I will try to do that and, perhaps, include integration with Windows NPM server.
Vladimir
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Kudos to you! Champion by name Champion by nature!
Thank you for that. I'll hold off on this project until your document is updated 😅
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
going over this again and again for the last few months.
Finally got the freeradius working with the help of some forums pointing to the "freeradius -X" to get it into debug mode.
It showed me that the user and group on page 12 should be kept as freerad, rather than change to root.
This allowed me to run the "service freeradius restart" command successfully on page 18.
However, radtest is failing with the below warnings I see (from the freeradius -X window)
IN YELLOW FONT:
(0) sql: WARNING: User not found in radcheck table.
IN RED FONT:
(0) pam: ERROR: pam_authenticate failed: Authentication failure
IN WHITE FONT:
(0) Login incorrect (pam: pam_authenticate failed: Authentication failure): [fu833513] (from client localhost port 18120)
Any ideas on this one?
I can successfully log into RADIUS server directly using the ID created on page 16 just using the password (without the OTP).
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 28 | |
| 16 | |
| 10 | |
| 9 | |
| 7 | |
| 7 | |
| 6 | |
| 5 | |
| 5 | |
| 3 |
Upcoming Events
Thu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Introducing Cyata, Securing the Agentic AI EraTue 03 Mar 2026 @ 04:00 PM (CET)
Maestro Masters EMEA: Introduction to Maestro Hyperscale FirewallsTue 03 Mar 2026 @ 03:00 PM (EST)
Maestro Masters Americas: Introduction to Maestro Hyperscale FirewallsThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Introducing Cyata, Securing the Agentic AI EraTue 03 Mar 2026 @ 04:00 PM (CET)
Maestro Masters EMEA: Introduction to Maestro Hyperscale FirewallsTue 03 Mar 2026 @ 03:00 PM (EST)
Maestro Masters Americas: Introduction to Maestro Hyperscale FirewallsFri 06 Mar 2026 @ 08:00 AM (COT)
Check Point R82 Hands‑On Bootcamp – Comunidad DOJO PanamáAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter