- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity AI Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
CheckMates Fest 2026
Join the Celebration!
AI Security Masters
E1: How AI is Reshaping Our World
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Maestro Madness
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- General Topics
- :
- Re: Issues with Identity Awareness - some users ar...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Issues with Identity Awareness - some users are not seen and some traffic is incorrectly marked
Hello,
I need to deploy IA across few firewalls in order to replace statically assigned IPs with IA-based rules.
For the record I'm running 80.30 Take 50 across all of our firewalls.
I have 4 collectors and they seems to be talking fine to my Gateways.
I have done some investigation on the PDP/PEP and connectivity to the AD - or, actually, Collectors. Long story short I think we can summarise our issue in 2 separate points:
- Some users are not being recognised as a AD users by PDP. Or they are "lost"
- Some traffic is marked as initiated by the users but that’s not the case at all as user just logged on to the server. Traffic is not generated by them. I will explain below exactly what I mean by that.
In terms of problem number 1:
- My user (one of many!) is not to be seen by PDP/PEP daemons.
- I have 2 devices (laptop/PC) and I have logged on to both of them today. I have also done full reboot of my PC and I had confirmation that my trust with the AD was established, all of the log on scripts were run correctly.
- My user was recognised before – I have logs to prove this
- Some other users were recognised before but they are not now (for example my colleague who sits right next to me – I could see his username yesterday but not today. He has definitely logged on to this PC multiple times today)
- Sometimes I can see user but NOT IP associated with that user
- Looking at the "Logs & Monitor" tab in SMS Console I can see events related to the "Log in/log out" however looking at "pdp monitor user" I can see user within PDP/PEP
Problem 2 manifests itself by marking traffic between servers as USER TRAFFIC.
Here is a specific scenario of what happens:
- Server is sending syslog messages to another server (and this traffic is seen correctly)
- User A logs in to the server and performs some operations NOT RELATED to the syslog (for example looking at the DHCP configuration)
- From that point on server marks traffic as sent by the user and goes against user’s ACLs.
- Only Syslog traffic (514) seems to be marked as the user's traffic.
Needless to say that both issues would be a showstoppers to implement this into PROD environment.
Please see some details about our setup – I have created a quick script to give us one-page summary about most important features of PDP:
Now, users and machines numbers are taken from this grep:
pdp monitor summary all | grep -c "[u]"
Thank you in advance for your help. I'm not sure what I could be looking into. I do have case open with our 1st line support (before we hit TAC) but that's slow to progress so I'm hoping I can get some help from "the experts in the field"
Cheers
Chris
8 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The first issue most likely requires investigation with the TAC.
The second issue, I’m afraid, is normal, as once the user logs into the server with an AD user, their username will be associated with the IP of the server.
It may be possible to filter that somehow.
The second issue, I’m afraid, is normal, as once the user logs into the server with an AD user, their username will be associated with the IP of the server.
It may be possible to filter that somehow.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Ok
for issue #1 I suspect that there is another user that logs onto your machine after you had logged onto it. Could be some AD service account for example. The best you can do is check for all IA associated logs with that specific IP, for example use filter
x.x.x.x and blade:"Identity Awareness"
Go through logs and see what's going on. Can be quite tricky to see the issue but usually you can see it there. For us it was "two" user problem per IP, i.e if you log in with a regular account "user1" and get your IP association and later run something on your machine with admin account "admin1" then IA will swiftly move IP association from user1 to admin1
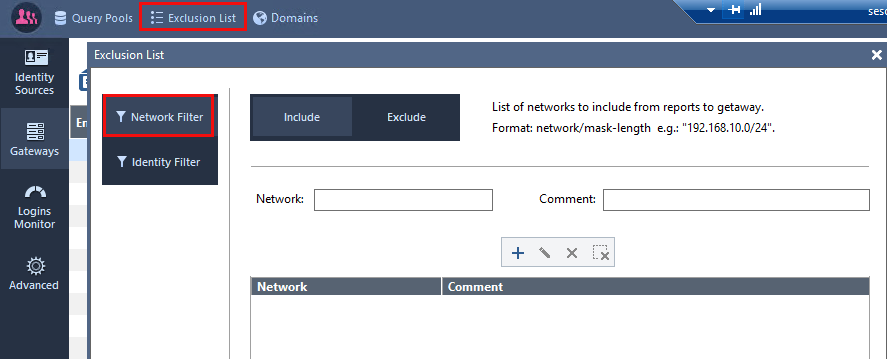
for the issue #2, you may exclude your server networks from IA completely in IDC. Give it a go!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
As above excluding networks or service accounts may help, some scenarios can only be overcome using the Identity Awareness Agent/s however.
CCSM R77/R80/ELITE
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Just another note about #1, when using the Identity Agents in conjunction with Identity Sharing I've seen some issues where user mappings get "lost" or don't get propagated correctly between different gateways. What seemed to help was disabling Identity Sharing completely, then having the Identity Agents directly send the identities to all the involved gateways instead of having them share with each other.
As for #2 I'd agree with the other posters, you are probably going to have to deploy the Identity Agent to the involved systems to make that work the way you want.
Gaia 4.18 (R82) Immersion Tips, Tricks, & Best Practices Video Course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello,
First of all many thanks to you all for your input. Much appreciated! Since posting this question I had my call with TAC and we are one step closer to get this working.
In regards to issue #1 it looks like we are missing events 4624, 4768, 4769. SK99006 says how the policy should be configured (and it is!) but we are still not getting them 😞 Obviously we need to look closer what else could be an issue here. Any help with this would be more than appreciated.
Thank you all for tips around issue #2 - I will set up some filters and see how it goes.
Thanks all!
Cheers
Chris
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello Chris,
Unfortunately there is no better way for Identity Based Access Rules than to go with Identity Agents.
Even when you sort your two issues you will hit another one in case you have wire/wireless users in your organization.
Imagine wired user correctly mapped already on PEP level with IP address.
Identity Based Access Rule is correctly reinforced and life is good.
Then what happens when our wired user goes to the meeting room with laptop and connects to Wi-Fi.
User gets different IP address from local DHCP server.
This information is however not propagated over to Domain Controller instantly as no communication with DC takes place.
Consequently this info doesn't get through to your Identity Collector
And finally this info doesn't get through to your PDP and ultimately PEP firewall will drop the traffic as new IP address is not mapped with allowed user yet.
New IP to user mapping happens at the end of the day but user needs to sit in the meeting room waiting for his laptop to talk to DC. Or lock the screen. Or reboot the laptop. Then all propagates down the stream over to PEP very quickly. Imagine asking every user to do this.
I wish Identity Collector way for IA blade would be enough but is not in my experience. Unless Im missing something here.
Please correct me anyone if I m wrong here.
Thanks,
Juraj
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
As @Juraj_Skalny said, roaming users can be a problem and the Identity Agent can help solve it. Roamers can also sometimes get remapped automatically with Transparent Kerberos Authentication via the captive portal, but this can be tricky to get working consistently in most customer environments.
Gaia 4.18 (R82) Immersion Tips, Tricks, & Best Practices Video Course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
It works for us actually as normally you lock/unlock laptop and that triggers AD event that's passed onto IDC and new wifi address gets reflected. For sure it's not the fastest and more reliable ways but it seems to cover some non-critical services quite OK
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 18 | |
| 10 | |
| 10 | |
| 10 | |
| 6 | |
| 3 | |
| 2 | |
| 2 | |
| 2 | |
| 1 |
Upcoming Events
Thu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: Exposing AI Vulnerabilities: CP<R> Latest Security FindingsThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter