- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity AI Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
CheckMates Fest 2026
Join the Celebration!
AI Security Masters
E1: How AI is Reshaping Our World
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Maestro Madness
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- General Topics
- :
- IPS Package numbers - when is my gateway really ge...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jump to solution
IPS Package numbers - when is my gateway really getting updated?
Hello,
I am running R80.40 in both my production and lab environments. This issue / question is true for both. I have noticed that the IPS package numbers that my gateways show as having installed don't seem to be correct at times or my gateways really aren't getting updated with new protections in staging mode like I think they should be.
The way I do IPS protections is I manually download the latest updates in SmartConsole and then install threat prevention policy to the gateways. New protections are set to go into staging mode.
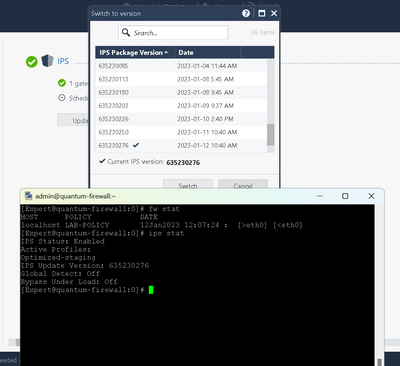
I have noticed that if I download the latest IPS update in SmartConsole, look over the new protections in staging, not make any changes, and then install threat prevention policy the IPS package number will not change to the new version per the output from the "ips stat" command.
I was under the impression that when I install threat prevention policy in this scenario the IPS package number should be updated and the new protections should be installed on the gateways in detect only mode.
The only way I can get "ips stat" to report as having the new package version is if I actually clear staging on the protections and then install threat policy.
In the past, possibly when I was running 80.30, I remember after downloading a new IPS package and installing TP policy, on the install policy screen there would be a message indicating that the IPS version was going to be updated to xxx.
How can I be sure my new protections set to detect in staging mode are actually getting applied to my gateways?
Thank you.
1 Solution
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I tested again today both in my 80.40 prod and 80.40 lab environments. After downloading the latest IPS package(s) and installing the threat prevention policy I kept executing "ips stat" and after a good minute the "IPS Update Version:" number did indeed update like it should. I guess I wasn't waiting long enough. Thanks again for your help on this.
13 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hey Mike,
I checked and definitely dont see this issue in R81.20 lab. Few questions:
1) What is the IPS profiule in use?
2) Is IPS blade set to upate automatically?
3) Has this issue been happening just recently or since while ago?
Andy
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
1. I am using the "Optimized" profile
2. No, the IPS blade is not set to update automatically. I do it manually every time.
3. I think this issue has been happening for a long time but just noticed it a couple week ago.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I dont have R80.40 to test, but will check in R81.10. By the way, Im pretty sure that manually updating IPS and having new protections in staging is NOT reason why you have this problem. As a matter of fact, give me some time, will test this in R81.20 lab in a bit and see what happens. Will let you know.
Andy
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Ok, so I changed my ips profile to optimized, set to update manually and set protections to staging. Pushed the policy, so let me observe and maybe I can check again tomorrow.
Andy
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Sorry, dont mean to "bombard" you with updates, but here is what I currently get, same set up as what you have, but as I said, will check again tomorrow. Mind you, this is R81.20 lab, but I dont think it should make any difference.
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Don't worry about bombarding me with updates. Thank you for your help!
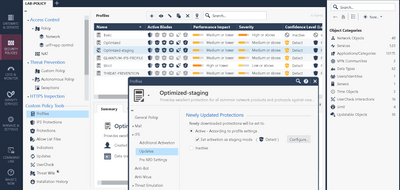
I noticed your profile reads "Optimized - staging". Is that the actual name of the profile you made or is the "staging" part something that Check Point adds when you have protections in staging mode?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Exactly Mike. So what happens is, as soon as you make ANY modifications to default IPS profile(s), it will ask you to save it with another name, usually clone, but I just called it optimized-staging. I simply added staging option as per below:
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hey man,
Dont worry, I did not forget aboyt ya : - ). Anyway, I tested again today with R81.10 AND R81.20 and all is fine, IPS shows updates, version is correct, I dont see any issues. Again, apologies, I sadly dont have R80.40 to test and probably wont have time to set up a lab today. Will see if anyone has existing lab I can tap into and try this.
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello,
Thank you for testing and providing me the results of your testing for 81.10 and 81.20. The fact that this happens in my 80.40 production and 80.40 lab makes me think this may affect all 80.40 instances.
I am considering changing my settings so IPS protections are updated automatically on the gateways and see if that makes a difference.
I am positive in the past, probably when I was on 80.30, on the install policy screen I would receive a message stating that the threat prevention policy would update the IPS package to version xxx. I don't have my 80.30 environment to go back to to verify.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
No worries, again, Im really sorry I dont have same version to test :(. Personally, as I always like to think logically about any issue, regardless what it is, I mean, IPS had not changed drastically from R80.40 to R81.20, so in my mind, its highly unlikely this would have been a bug in R80.40. Just wondering, have you ever tried disabling/re-enabling IPS blade tso see what ahppens? Disable ips, push policy, re-enable, push policy and then configure same settings again?
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Since this was really bugging me, I quickly created R80.40 lab on esxi server with SSD drives, so I could try this on R80.40. Mike, I dont have same problem, it behaves exactly how it does on R81.10 and R81.20
At this point, I can only assume its something on your end, so you may wish to involve TAC and see why its not working as expected, sorry mate.
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I tested again today both in my 80.40 prod and 80.40 lab environments. After downloading the latest IPS package(s) and installing the threat prevention policy I kept executing "ips stat" and after a good minute the "IPS Update Version:" number did indeed update like it should. I guess I wasn't waiting long enough. Thanks again for your help on this.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Its all good mate...patience and IT are usually not a "known combo" lol
Cheers.
Andy
Best,
Andy
Andy
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 19 | |
| 10 | |
| 10 | |
| 9 | |
| 6 | |
| 3 | |
| 2 | |
| 2 | |
| 2 | |
| 1 |
Upcoming Events
Thu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: Exposing AI Vulnerabilities: CP<R> Latest Security FindingsThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter