Hello Jeffrey,
the problem is that once the attacker was able to trick the user into installing the fake Certificate Authority certificate, the attacker can use this to create fake certificates for whatever URl/website that they wish. After the installation, the browser will completely trust this CA.
The original purpose of the CA plays no role here. The browser does not know about this purpose nor does it check it. It simply checks whether it trusts the CA if it sees a certificate which was issued by it. Since the user installed the CA manually, this will be the case, enabling the attacker to fake certificates.
While you are probably right that only Check Point software needs this cert. But the browser doesn't care. Once the CA is installed, it trusts it blindly.
Of course you are right that there needs to be a Check Point infrastructure available to abuse this vulnerability. However, the attacker wouldn't need to set it up themselves. They only need to be on the same network as the victim and act as a man-in-the-middle between the victim and the cert installation portal.
Also, yeah, the user would probably notice that they can't access the Check Point products after installing this fake CA (I guess, I don't have detailed knowledge of the products). But even if this would be the case, a normal user without a security/technological background will probably not think twice about it, try again and download the correct CA certificate, without removing the malicious one. And even if they do remove the malicious CA, the damage might have already been done.
Furthermore, the installation of a malicious CA cert is just one type of attack that is possible here. The attacker could also use this vulnerability to spread whatever malware they want, as I've also explained in pervious posts.


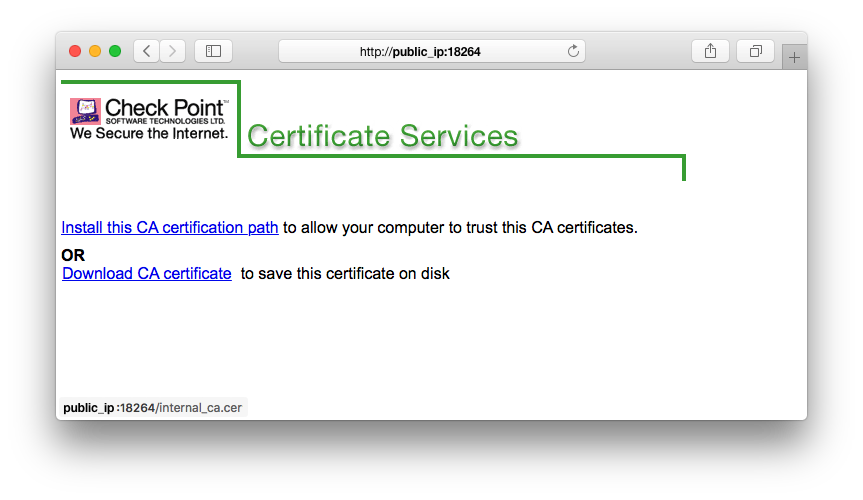 Don't be fooled, this is
Don't be fooled, this is