Recent Check Point articles:
Review and raise your gateway baseline security level
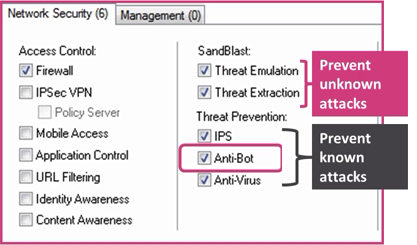
Activate Zero-Day Protection
- To protect against unknown attacks, activate Check Points Zero-Day protection solution (SandBlast, emulation) for your Gateway and Endpoint security needs
Raise the security awareness of your employees
- Train your staff to raise the awareness of phishing mails, fake domains, mailicious attachments etc.
Protect against DDoS attacks
SmartEvent
Infinity SoC
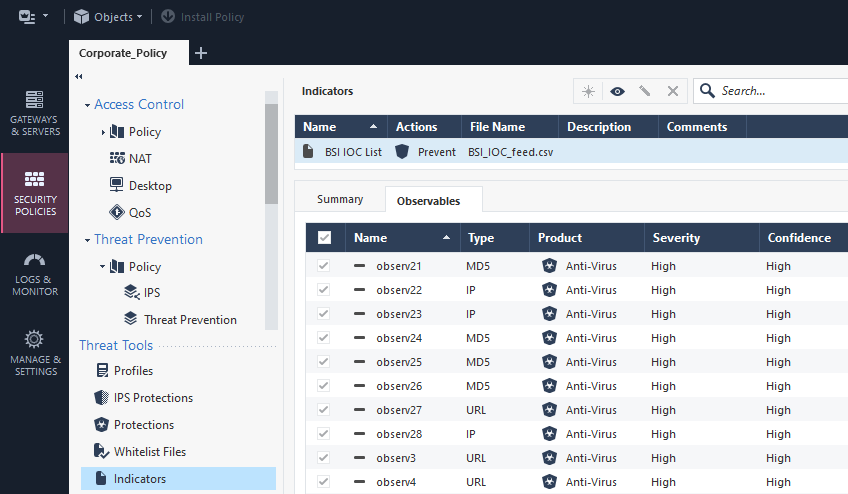
Configure Threat Indicators
Use Custom Intelligence Feeds (IOC Feeds) to block IP- & URL Blacklists
- Prerequisite: Anti-Virus & Anti-Bot
- Check Point SKs
- sk132193 - What is the "Custom Intelligence Feeds" feature?
- Check Point IOC Feeds
- Externally available IOC feeds:
- Subscribe to your local security.gov IOC feed provider
- Known .gov providers to provide IOC feeds:
Use Check Points SNORT signature support
Endpoint Security
DLP, Content Awareness
- Activate and use Check Points Data-Loss Prevention solution to avoid loosing data.
- Content Awareness is part of Check Points DLP suite and can be activated separately and without a DLP license. Check Points SmartConsole Demo mode shows a good use case.
Check your backup & restore procedures
- Check the cycle and integrity of all your backup files and test them for integrity
- Check your restore procedures
- Check for addtional backup types, such as export, snapshot etc.
- Check the security level of your backup locations
Prepare and update your disaster recovery plan
Re-evaluate your SLAs with your IT security service provider
- Is next-business-day still enough for your cyber security demand?
Subscribe to Check Point Advisories and Alerts