I need to set up multiple vpn star communities peered to an Azure Cloudguard R80.40 cluster. These tunnels are being migrated from an existing Cisco ASA that is performing twice-nat to separate the local network from the remote public ranges. The remote peers will be various third party appliances, and some private networks may overlap my organization's private networks and each other's. Therefor we have a public range of IP addresses that we are using for NAT. The peer organizations have the same on their side.
In this example assume the local source is coming from a 192.168.0.0/16 subnet and all others are /24.
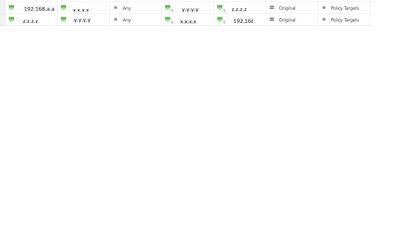
Src (local private) | Destination (local private) | Translated source (local public) | Translated dst (remote public) | Partner private |
192.168.a.a | x.x.x.x | y.y.y.y | z.z.z.z | 192.168.b.b |
So the return traffic should look something like this.
Src (remote public) | Destination (local public) | Translated src (local private) | Destination (actual IP) |
z.z.z.z | y.y.y.y | x.x.x.x | 192.168.a.a |
I am unsure how the encryption domain works with the twice-nat going both directions. Is this setup possible with Check Point?
- What is the best way to define the VPN domain for the cluster object VPN domain? The VPN domain is set to a user defined Network Group. Some of the other communities may not need the twice nat and will target local IP addresses without translation, so it seems that the local subnets would need to be included in the group. If NAT translation happens before link selection, does the y.y.y.0/24 network need to be included in the VPN domain, or does that interfere with return traffic?
- What is the best way to define the VPN domain for the individual community? Only include z.z.z.0/24? Or include the translated x.x.x.0/24?
- Will NAT rules like this work?