- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
The Great Exposure Reset
24 February 2026 @ 5pm CET / 11am EST
CheckMates Fest 2026
Watch Now!AI Security Masters
Hacking with AI: The Dark Side of Innovation
CheckMates Go:
CheckMates Fest
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- General Topics
- :
- Re: How to configure Check Point Security Gateway ...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jump to solution
How to configure Check Point Security Gateway as HTTP/HTTPS Proxy
Can Anybody PLease help me on this How to configure Check Point Security Gateway as HTTP/HTTPS Proxy
Thanks In advance
- Tags:
- httphttps proxy
60 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Apologies, but I have to paste the entire SK here to get to the bottom of it.
Please scroll down to the highlighted sections and please help me understand the implications of these perls of wisdom:
----
R80.10 Configuration
- In order to make the Proxy Server to work on R80.10, an explicit rule should be created allowing traffic to the gateway itself on the proxy defined port.
- When using URL Filtering, an explicit rule should be created to match the URL categorization.
-----
(3) Limitations
HTTP/HTTPS proxy support is limited for the following features/configurations:
HTTPS traffic | Not supported in Transparent Proxy configuration when the HTTPS traffic ports are configured in the 'ports' section of the proxy configuration. | No active plans |
----
The following features/configuration are supported, but might require some adjustments:
HTTPS traffic | Supported in Non-Transparent Proxy configuration. | - |
-----
For what its worth, this seem to do the trick:
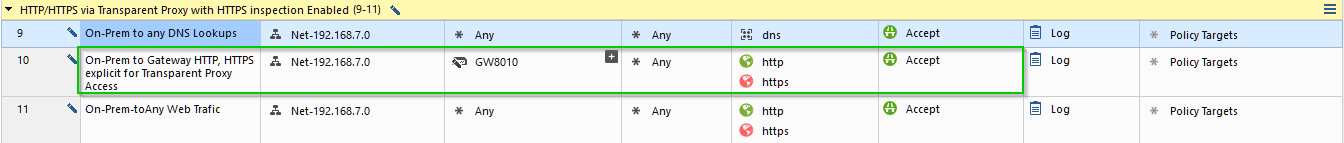
With Proxy configured thus:
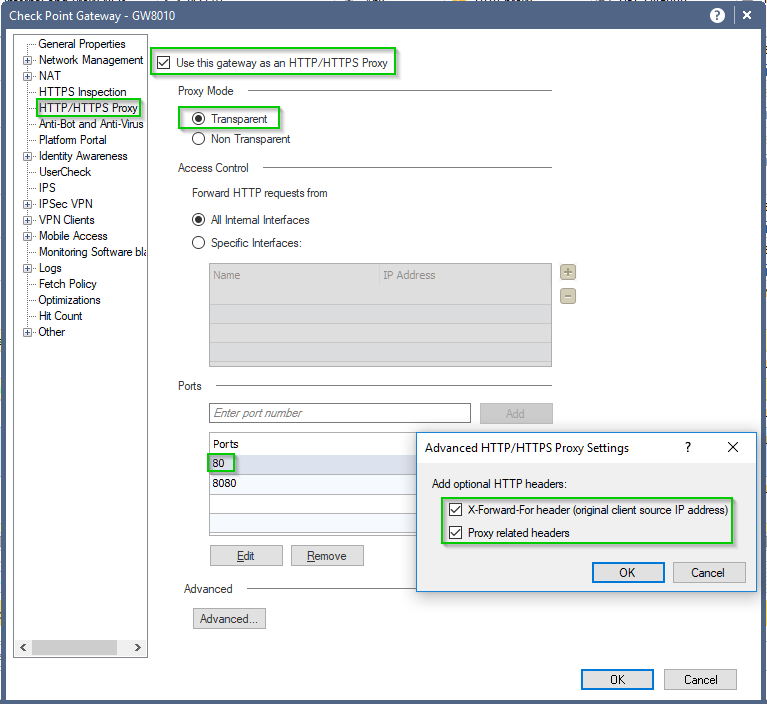
And the proxy checker actually returns:
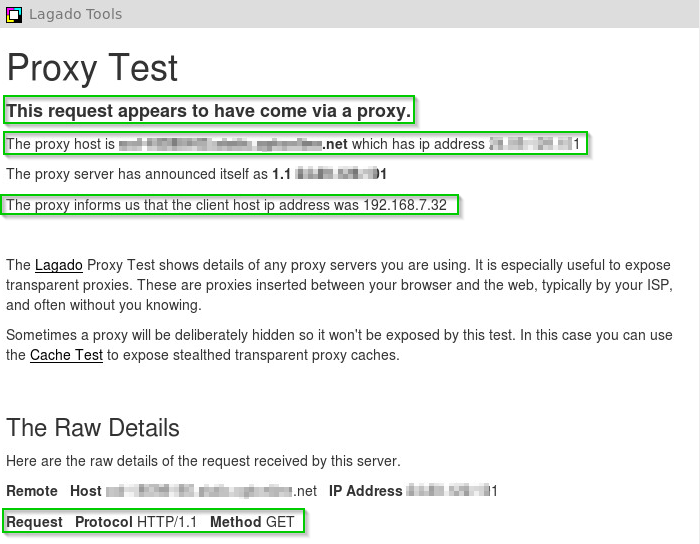
But since I have HTTPS inspection enabled, I have no means to discern if that traffic is being proxied or inspected inline which, in case of HTTPS may not be different anyhow, as the session is broken-down in two and the certificates will be substituted in both cases:
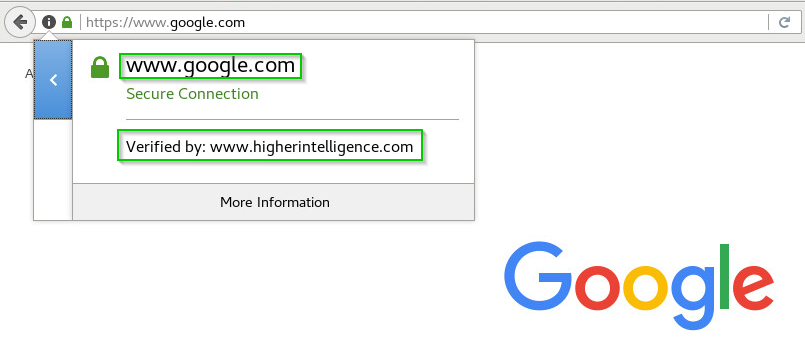
How to configure Check Point Security Gateway as HTTP/HTTPS Proxy
Top of Form
Rate This |
Bottom of Form
Solution ID | sk110013 |
Product | Security Gateway |
Version | R75.40, R75.40VS, R75.45, R75.46, R75.47, R76, R76SP, R76SP.10, R76SP.10_VSLS, R76SP.20, R76SP.30, R76SP.40, R77, R77.10, R77.20, R77.30, R80.10 |
OS | Gaia, SecurePlatform 2.6 |
Platform / Model | All |
Date Created | 14-Feb-2016 |
Last Modified | 22-Jan-2018 |
Solution
Table of Contents:
- Configuration in SmartDashboard
- Important notes
- Limitations
- Proxy errors
- Related documentation
- Related solutions
(1) Configuration in SmartDashboard
- Open the Security Gateway object you would like to configure as a Proxy.
- Go to HTTP/HTTPS Proxy pane:
- Check the box Use this gateway as an HTTP/HTTPS Proxy.
- Configure the Proxy settings:
- Proxy Modes
Two proxy modes are supported:
- Transparent - All HTTP traffic on specified ports and interfaces is intercepted and processed by the Proxy code in the Security Gateway. No configuration is required on the clients.
- Non Transparent - All HTTP/HTTPS traffic on specified ports and interfaces is intercepted and processed by the Proxy code in the Security Gateway. Configuration of the proxy address and port is required on client machines.
- Access Control
You can configure one of these options for forwarding HTTP requests:
- All Internal Interfaces - HTTP/HTTPS traffic from all internal interfaces is processed by the Proxy code in the Security Gateway.
- Specific Interfaces - HTTP/HTTPS traffic from interfaces specified in the list is processed by the Proxy code in the Security Gateway.
- Ports
By default, traffic is intercepted only on port 8080. You can add or edit ports as required.
- Advanced
You can configure proxy headers by clicking on Advanced... button.
- Proxy related headers - By default, the HTTP header contains the "Via" proxy related header. Clear this checkbox if you do not want to include it.
- X-Forward-For header (original client source IP address) - check this box to include the actual source IP address in the HTTP.
This header must be configured, if traffic will be forwarded to Identity Awareness Security Gateways that require this information for user identification. - Logging
The Security Gateway opens two connections (one connection with the client and one connection with the actual destination server), but only the Firewall blade can log both connections.
Other blades show only the connection between the client and the Security Gateway.
The "Destination" field of the log only shows the Security Gateway and not the actual destination server.
The "Resource" field shows the actual destination.
- Example:
- Install policy on the Security Gateway.
R80.10 Configuration
- In order to make the Proxy Server to work on R80.10, an explicit rule should be created allowing traffic to the gateway itself on the proxy defined port.
- When using URL Filtering, an explicit rule should be created to match the URL categorization.
(2) Important notes
- In order to maintain highest security, it is recommended to avoid selecting external interfaces as the relevant proxy interfaces.
- Check Point HTTP/HTTPS proxy is not a caching proxy (it does not cache commonly visited web pages to provide faster local access to hosts on the LAN).
(3) Limitations
HTTP/HTTPS proxy support is limited for the following features/configurations:
Feature / | Comments | Plans |
IPv6 | Proxy can be used, but not for IPv6 connections. In addition, refer to sk112816 - Check Point support for IPv4 / IPv6 Proxy. | Planned to be resolved in a future version. |
Span Port / | Proxy is not supported when this feature is enabled. Refer to sk98389. | No active plans |
VPN Site-to-Site | Proxy can be used, but not over VPN connections. Refer to sk93929. | Planned to be resolved in a future version. |
Mobile Access blade | Proxy can be used, but not over Mobile Access connections. | No active plans |
Anti-Spam & E-mail Security blade | Proxy is not supported when this feature is enabled. *The Content-based Anti-Spam is not supported with proxy (only the IP Reputation is supported) | No active plans |
Application Accounting | Not supported in Transparent Proxy configuration. | No active plans |
HTTPS traffic | Not supported in Transparent Proxy configuration when the HTTPS traffic ports are configured in the 'ports' section of the proxy configuration. | No active plans |
UserCheck | Users do not receive a UserCheck page for blocked HTTPS connections that pass through Proxy, but instead receive a message that the page could not be reached. | Planned to be resolved in a future version. |
NTLM authentication | Not supported in Proxy configuration. Refer to sk100214. | No active plans |
The following features/configuration are supported, but might require some adjustments:
Feature / | Comments | Integrated in |
VPN Remote Access with client E75.30 | The following configuration is required - add both internal and external interfaces to 'Specific Interfaces' setting in HTTP/HTTPS Proxy properties. | - |
UserCheck | UserCheck block page message is not shown when Security Gateway is configured as HTTP Proxy. To resolve the issue, add the portal IP address to the proxy exceptions list in your web browser, or use a proxy PAC file to exclude the portal from the connections that require a proxy. This allows the client to connect directly to the portal, without going through the proxy feature. Refer to sk72100. | - |
Bridge mode | The following configuration is required - you must configure an IP address on the bridge interface. | - |
Cluster with Cluster Virtual IP address on a different subnet than the member's physical IP addresses | In case you encounter connectivity issues, contact Check Point Support to get a Hotfix for this issue (Issue ID 01223637). | R76 and above |
Application & URL Filtering with a single interface | When Security Gateway is configured as HTTP/HTTPS Proxy with a single interface, define the relevant rules in 'Application & URL Filtering' policy as follows: Source - 'Any'; Destination - 'Any'. Refer to sk80340. | - |
"Page not found" error | Error is shown when Security Gateway is configured as Non-transparent Proxy, if the same site is accessed on more than one destination port. Contact Check Point Support to get a Hotfix for this issue (Issue ID 01134342). | R75.47, |
Ports Leak in ClusterXL HA | If ClusterXL in High Availability mode is used as Proxy in Non Transparent mode, then NAT kernel table 'fwx_alloc' on the Standby cluster member has significantly more entries than on the Active cluster member. "NAT hide failure - no available port for hide NAT" logs in SmartView Tracker will appear. | R77 and above |
HTTPS traffic | Supported in Non-Transparent Proxy configuration. | - |
Additional notes:
- By default, Check Point Security Gateway does not support Reverse Proxy Functionality.
For Capsule Docs Reverse Proxy, refer to:- sk102973 - Check Point Capsule Docs - 3rd-party Reverse Proxy Server
- sk103706 - Capsule Docs On-Premises vs. Capsule Docs managed in the Cloud
- sk105123 - Check Point Capsule Docs, Endpoint Security and Remote Access VPN E80.61 / R77.20.01
- sk108375 - Check Point Capsule Docs, Endpoint Security and Remote Access VPN E80.62 / R77.30.01
- On 41000 / 61000 Security System - Proxy connections will be dropped during failovers (due to the fact that such connections are handled as a Local Connection, which has no backup) (Issue 02331051).
(4) Proxy errors
Below is a summary of proxy errors as it is seen in browser and in logs.
Error | Browser | Log |
DNS failure, no connectivity to DNS server | Gateway Timeout The requested URL couldn't be resolved | Reject Proxy: DNS timeout/error; Connection was rejected due to DNS timeout or error |
DNS server is available but no record for the URL request | Gateway Timeout The requested URL couldn't be resolved | Reject Proxy: Internal error; Connection was rejected due to internal error |
DNS server is available, record for URL also available but no Internet connection | This web page is not available ERR_TUNNEL_CONNECTION_FAILED | Reject Can't connect to server |
HTTP server failure, no connectivity to HTTP server | Gateway Timeout The requested URL couldn't be resolved | Reject Can't connect to server |
HTTPS server error "500/404" - usually it indicates on a problem with the HTML code or page not found | Server error 500 | Accept |
Server Reset: Server is up and running but not listens to HTTP/S ports. Can happen after reboot or internal server errors | Server error 502 | Accept |
Authentication failure: wrong credential in a password authentication | Unauthorized The server could not verify that you are authorized to access the document requested. | Accept |
(5) Related documentation
- R77 versions IPS Administration Guide - chapter "Monitoring Traffic" - section "HTTPS Inspection" - sub-section "HTTP/HTTPS Proxy"
- R77 versions Threat Prevention Administration Guide - chapter "Using Threat Prevention with HTTPS Traffic" - section "HTTPS Inspection" - sub-section "HTTP/HTTPS Proxy"
- R77 versions Application Control and URL Filtering Administration Guide - chapter "Managing Application Control and URL Filtering" - section "HTTPS Inspection" - sub-section "HTTP/HTTPS Proxy"
(6) Related solutions
- sk112816 - Check Point support for IPv4 / IPv6 Proxy
- sk92482 - Performance impact from enabling HTTP/HTTPS Proxy functionality
- sk101395 - How to configure Proxy Chain on a Check Point Security Gateway defined as Proxy
- sk104639 - Connection from a Client to a Server does not work when both Client and Server are NATed ...
- sk104639 - Mobile Access R77.30 Reverse Proxy
- sk111171 - Security Gateway in HTTP/HTTPS Proxy mode sends TCP RST packet in response to TCP SYN pac...
- sk112939 - Application Control and URL Filtering blades do not work when Security Gateway is configu...
Applies To:
- This SK replaces sk98559
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Not supported in Transparent Proxy configuration when the HTTPS traffic ports are configured in the 'ports' section of the proxy configuration.
That just means we can't transparently proxy HTTPS. Which makes sense because you would need to to HTTPS Inspection to do it properly.
HTTPS traffic
Supported in Non-Transparent Proxy configuration.
This is because in an explicit proxy mode, the actual connect message is in cleartext (e.g. CONNECT https://www.google.com HTTP/1.1).
We can allow/block traffic based on the actual destination in this case.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I've configured WPAD via DHCP and serve a central PAC file which excludes the security gateway. Workstations subsequently use an explicit proxy configuration but UserCheck redirection is not working in Google Chrome, Edge and Internet Explorer. Is this an issue I should open with TAC or do I need to do something to get the browser to honor the redirect?
The following is a packet capture from the office router sitting in between the workstation and the security gateway:

The browser appear to simply ignored the response. I'm able to see the User Check message if I manually type it in to the browser and it's not sent to the security gateway via the proxy protocol.
PS: Running R80.10 management and security gateway.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
It might be worth a TAC case, but we are sending a redirect-type message as we should.
Never seen a 303 error before but it kind of makes sense since it's neither a "temporary" or "permanent" redirect.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
What gateway are you expecting the user check from? If remote, its’ user check URL should also be made accessible, else your workstation may be attempting to reach it via the local one.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Directly from the security gateway at the moment:
internet --- firewall --- PC
We would like to present User Check notifications for secure sites, without enabling HTTPS inspection and understood R80.10 to be able to do this when configuring an explicit proxy.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
David,
please provide a topology information describing PC, both gateways, any routers between them, etc..
Your traffic may be going from PC to secure site via remote gateway (proxy), but when redirected, points to the local gateway for the access to the UserCheck URL.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Vladimir,
The test case is extremely simple, we have a security gateway at the perimeter of our network (100.127.254.1/30), which interfaces with a router (100.127.254.2/30), which is the gateway for the LAN (192.168.5.254/23). A workstation (192.168.5.12/23) attempting to navigate to a site who's category is blocked and configured to display a User Check notice only redirects to the notification page when using plain HTTP connections.
I understood R80.10 to be able to redirect secure browsing (HTTPS) requests when workstations are configured with an explicit proxy. We subsequently configured the security gateway as a non-transparent proxy, set the proxy port as 3128 and configured a workstation to use the explicit proxy (100.127.254.1:3128).
Using Internet Explorer 11, Edge or Google Chrome and navigating to a non-secure site results in the browser displaying the User Check page but browsing to blocked HTTPS sites results in a connection error being displayed, instead of the User Check page.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
P.S. This is not a vSEC implementation, though. I've just piggybacked on the thread as this distinction seem immaterial in my case.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
P.S.S. Is there a reason you are asking about App Control functionality with proxy in the mix?
Will proxy somehow impede the App Control ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Dear Team,
Tell me, please, are there any nuances in synchronizing proxy connections?
We tested the non-transparent proxy: we started downloading a large file and changed the active member of the cluster. Download interrupted and did not recover. With other proxy (such as SQUID) we hadn't similar problems.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
As far as I know, explicit proxy connections are not synchronized.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks for reply.
But is there any documentary evidence of this?
In proxy limitations I see that only on 41000 / 61000 Security System proxy connections will be dropped during failovers (due to the fact that such connections are handled as a Local Connection, which has no backup).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I see what you mean, as it's explictly listed as "not supported" for Scalable Platforms (but not regular ones) here: How to configure Check Point Security Gateway as HTTP/HTTPS Proxy
In which case, if you're having issues with this, it's worth a TAC case to investigate further.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello Guys for additional information, I have 3 proxies and we will coming soon remove these feature of our gateways because in tacker log we don't see all track of users access. For all others connections without proxy are tracked full in smartview.
Could please verify in your environment its occurred?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Are you running them in a transparent or non-transparent mode?
Do you have HTTPS inspection enabled?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yes, I have HTTPS Inspection enable and non-transparent mode. The web browsers with pacfile script.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Are you missing some of the information or is there nothing at all logged for users accessing sites via proxies?
Is IA enabled on both, the gateways as well as on management?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yes the IA is enabled on both, and some access not show the user from IA only the gateway in source field... I think its related two connections was established one client to firewall and other firewall to destination site.
We have another problem too when use the proxy, some access not showing the url destination in "Resource field", I think to use the proxy feature is not better idea.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I do recall encountering similar issues in the past, some of them may even be listed in this thread.
Did you try it with these settings enabled in the HTTP/HTTPS Proxy / Advanced properties?
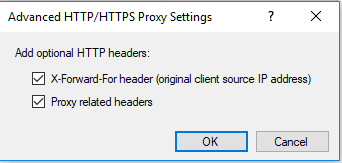
You may not want to leave those permanently turned-on, but may be it will help the gateways track the decoupled log events better.
I really would like for someone from Check Point to comment on the issue of tracking web access via proxies with clearly identified resources.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
To log all URLs, the rule that matches must be set to track with extended log.
If this is not happening, please open a TAC case so the issue can be investigated.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I can confirm that the proxy connections are not being logged properly.
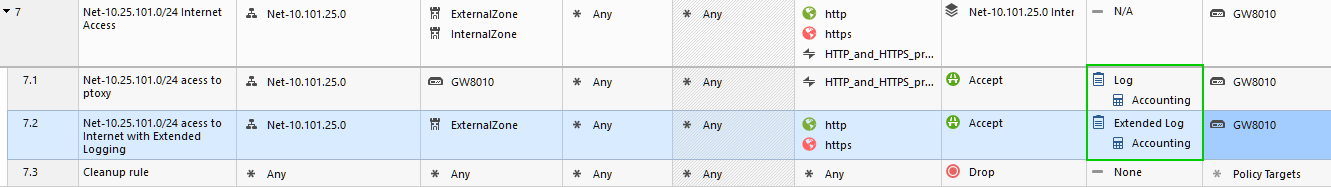
with the layer's blades being:
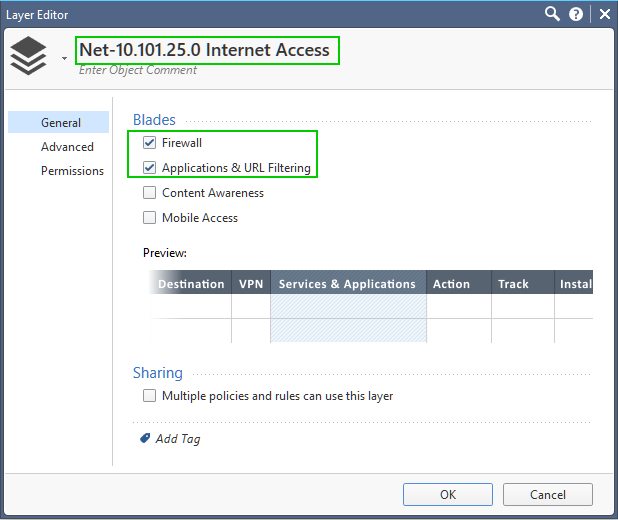
And the gateway configured:
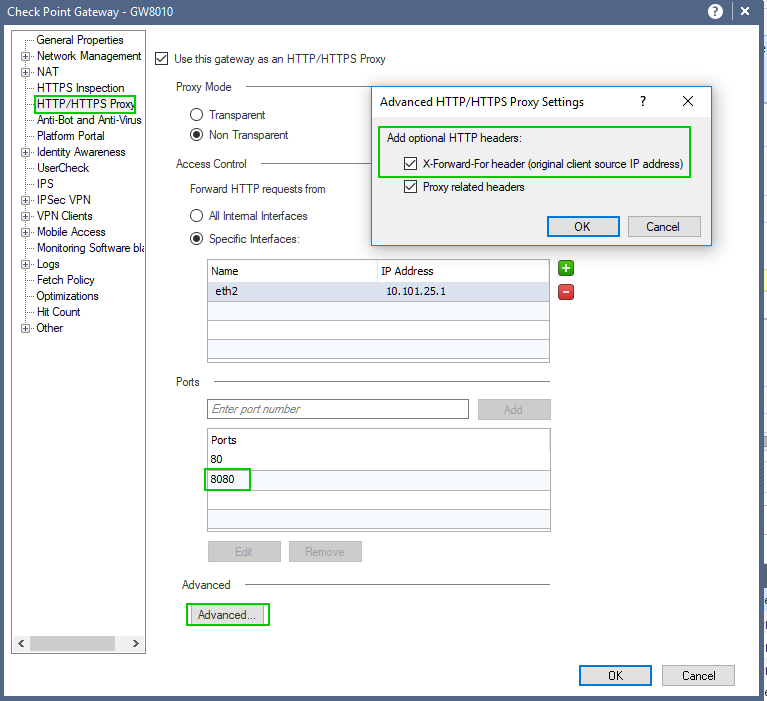
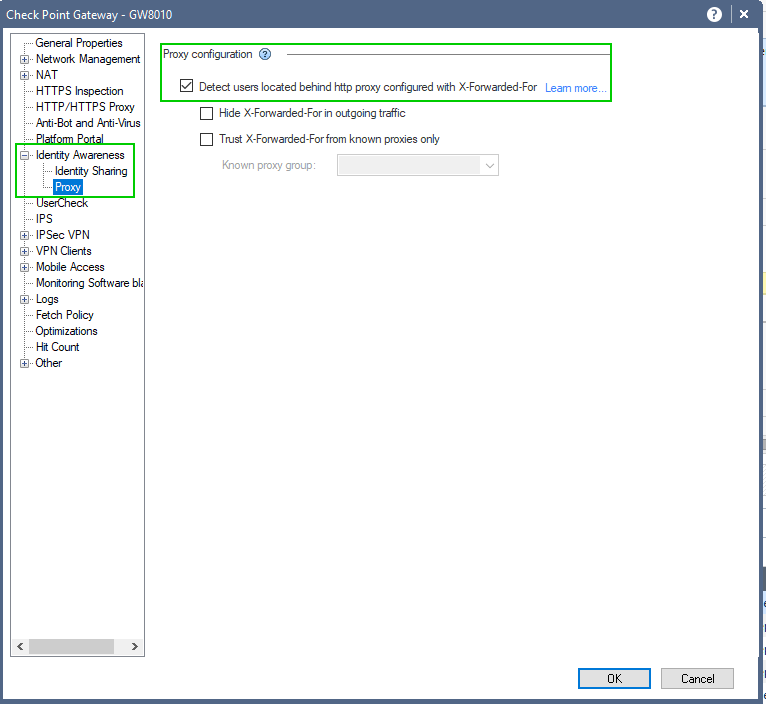
Proxy functionality verified:
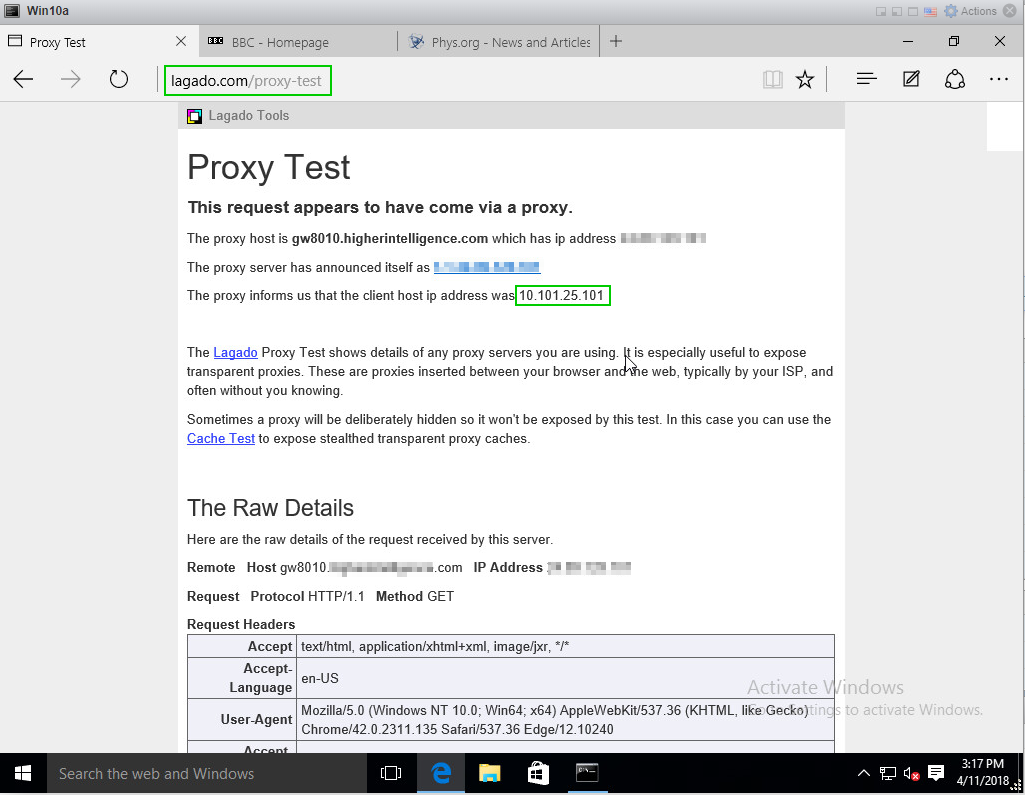
Log's Resource and the URL columns remain empty:
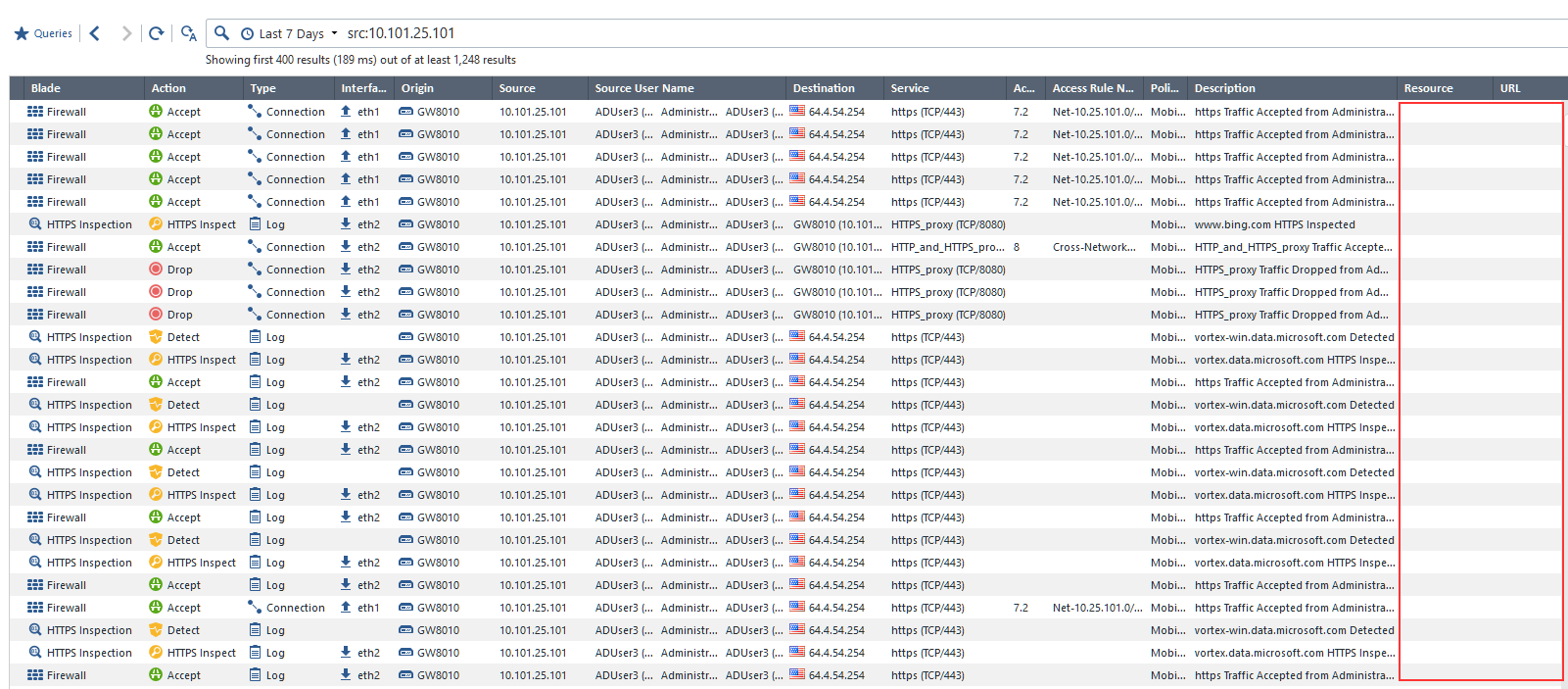
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
That's it , now how can we solve this ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Please open SR with TAC and include in it reference to this thread (you can include the link to my post with details directly, so that they will not be searching for it). Chose severity of the case to reflect how badly it affects your production environment.
Reply here with the SR # to enable forum curators collaborate with TAC and R&D and keep all of us updated on the progress.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
cross-referencing this thread:
HTTPS inspection real life examples and caveats in R77.30 and R80.10
As I showed in the screenshots below I believe using the CP as a proxy works perfectly fine for me.
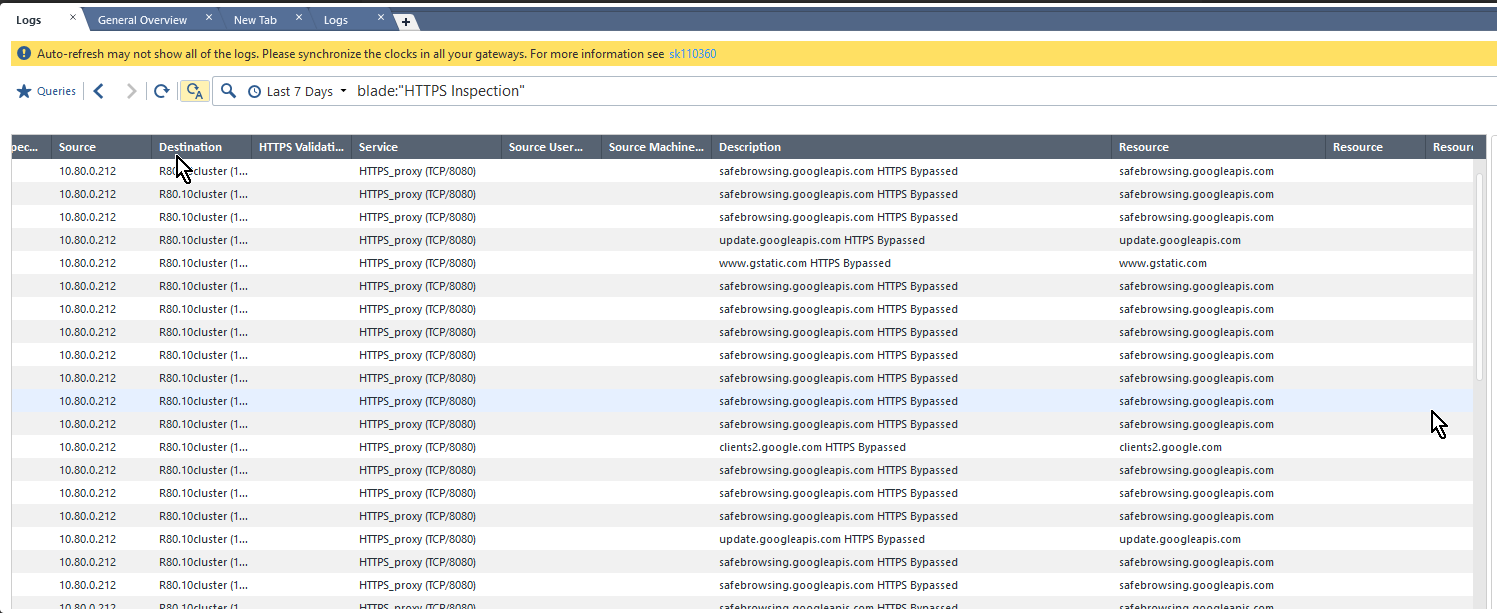
Possibly the findings from this chat that Resource tracking doesn't work is because of a bug (?) that there are two "Resource" columns (see screenshot above) and the one that is displayed in the previous screenshots was the wrong one?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Advanced
You can configure proxy headers by clicking on Advanced... button.
- Proxy related headers - By default, the HTTP header contains the "Via" proxy related header. Clear this checkbox if you do not want to include it.
- X-Forward-For header (original client source IP address) - check this box to include the actual source IP address in the HTTP.
This header must be configured, if traffic will be forwarded to Identity Awareness Security Gateways that require this information for user identification.
Logging
The Security Gateway opens two connections (one connection with the client and one connection with the actual destination server), but only the Firewall blade can log both connections.
Other blades show only the connection between the client and the Security Gateway.
The "Destination" field of the log only shows the Security Gateway and not the actual destination server.
The "Resource" field shows the actual destination.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
That's it ... The X-forward and Log full are configured too...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hmm.. does it work now or are you simply saying that those settings are enabled already, but you are still having problems with logging?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Vladimir
It was already set up and it does not work. Because this I will deactivate this feature.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks.
I'll try to replicate it in mu lab at some point and post the discoveries here.
Have you opened the SR with TAC?
If yes, please reply with the case #, so that CP guys can follow up on it.
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 21 | |
| 20 | |
| 15 | |
| 10 | |
| 8 | |
| 8 | |
| 6 | |
| 6 | |
| 6 | |
| 6 |
Trending Discussions
Upcoming Events
Tue 10 Feb 2026 @ 03:00 PM (CET)
NIS2 Compliance in 2026: Tactical Tools to Assess, Secure, and ComplyTue 10 Feb 2026 @ 02:00 PM (EST)
Defending Hyperconnected AI-Driven Networks with Hybrid Mesh SecurityThu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: AI-Generated Malware - From Experimentation to Operational RealityFri 13 Feb 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 43: Terugblik op de Check Point Sales Kick Off 2026Tue 10 Feb 2026 @ 03:00 PM (CET)
NIS2 Compliance in 2026: Tactical Tools to Assess, Secure, and ComplyTue 10 Feb 2026 @ 02:00 PM (EST)
Defending Hyperconnected AI-Driven Networks with Hybrid Mesh SecurityFri 13 Feb 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 43: Terugblik op de Check Point Sales Kick Off 2026Thu 19 Feb 2026 @ 03:00 PM (EST)
Americas Deep Dive: Check Point Management API Best PracticesAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter


