- Products
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- Learn
- Local User Groups
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
- Partners
- More
- ABOUT CHECKMATES & FAQ
- Sign In
- Leaderboard
- Events
Access Control and Threat Prevention Best Practices
5 November @ 5pm CET / 11am ET
Firewall Uptime, Reimagined
How AIOps Simplifies Operations and Prevents Outages
Overlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Spark Management Portal and More!
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- General Topics
- :
- Hostname disclosure
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hostname disclosure
Hello All,
I'm looking for some piece of advice on the following. We ran Shodan scan against our domain and the report is coming with some detailed information about the firewalls as for instance hostname,smartCenter host and public IP address:
193.120.x.x
IrelandIreland, Dublin
Details CheckPoint
Firewall Host: B-ECOM-xxx.xx
SmartCenter Host: b-chk-mgmt-ecom-xxx.xxx.ie
Port 264
Any ideas on how to avoid this type of information to be disclosed?
We have seen through our SIEM, that China for instance are running this type of scans to our firewalls.
Many thanks,
Reinaldo
18 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
See the following thread:
https://community.checkpoint.com/thread/8321-hostname-disclosure-on-port-264
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I understand and I saw the article from checkpoint. Problem is that the scan is disclosing firewall host name and up address and that could lead to a possible attack. Our external siem team are advising us to mitigate this problem and we don't know how to proceed.
I know that the information is public but I believe that i is not good practice to have the host name and ip address disclosed for the big bad world.
Any thoughts?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Do you have stealth-rule in place?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yes we do have a stealth rule in place. But I don't think that will mitigate the problem as the port tcp 264 is used for vpn topology downloader.
Currently there are no rules allowing this type of traffic in the rule set, but if you run a scan against your domain you can get all the details as mentioned before, hostname, ip address, etc.
Try to run a shodan scan you will see the results...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Currently there are no rules allowing this type of traffic in the rule set, but if you run a scan against your domain you can get all the details as mentioned before, hostname, ip address, etc.
Have you checked Implied Rules? This rule is activated as part of Accept Control connections option in Global Properties.
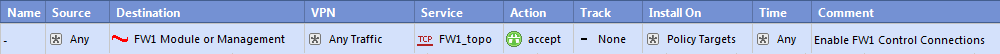
So you would like to not show hostnames on this port, right? This is the main issue you see? I believe public IP address cannot be cosidered as internal information.
The SmartCenter and Security Gateway names are part of the gateway certificate that is presented for authentication in many scenarios. The gateway name is in the Subject field of the certificate and the SmartCenter name is in the Issuer field, since Internal CA runs on the SmartCenter. Certificate owner name and CA names are considered public information.
I will not run Shodan...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Aleksei,
Indeed the rule is in place.
What we are trying to accomplish, it is to not share the full hostname of the firewalls. The scan results report provide a full hostname:
Firewall Host: B-ECOM-xxx.xx
SmartCenter Host: b-chk-mgmt-ecom-xxx.xxx.ie
I understand what you are saying, but our third part siem team and manager don't. I have provided to them the official documentation from Checkpoint but it seems not to be enough.
What I'm trying here is maybe do not display the full hostname , but not sure if this is possible.
many thanks.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Isnt tcp_264 used only for very old VPN client ? https should be the only port for topology download for new VPN client.
Kind regards,
Jozko Mrkvicka
Jozko Mrkvicka
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jozko, read please the checkpoint documentation about port tcp 264 and run a shodan scan against your domain...
Https is just for ssl vpns.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
set hostname PLEASE_DONT_SCAN_US_THANKS
save config
Kind regards,
Jozko Mrkvicka
Jozko Mrkvicka
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Not really helpful but thank you for your suggestion.
I'm talking about a financial institution with several production devices.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
If you know IP range where this scan is from, just create SAM rule and you are safe.
Kind regards,
Jozko Mrkvicka
Jozko Mrkvicka
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you for recommendation Jozko.
We already thought about that possibility but the scan is all over the place (several sources /countries) and also there is a possibility about IP masquerading (VPN,proxy, etc), so I don't think this will mitigate the problem.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
If you know IP ranges which can use tcp_264 for VPN topo download (RA users) then you can specify it in rulebase, and disable implied rule for this (not sure if possible only for 1 implied rule). All other attemps besides ranges in "white list" will be blocked.
Kind regards,
Jozko Mrkvicka
Jozko Mrkvicka
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
As was stated in our official SK on the topic, we consider the disclosed information to be public: Check Point response to SecuRemote Topology Service Hostname Disclosure
Short of blocking the relevant traffic, there is not currently a way to prevent the disclosure of this information.
Adding this capability would most likely require an RFE (Request for Enhancement), which should be brought through your local Check Point office.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
A simple solution is to configure SmartEvent to blacklist external scanners.
By the time Shodan or other port scanners will go through the lower ports, they will be labeled as scanners, dropped and blocked:

- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you for your input I think this should be useful. Could you please recommend the no of connections to be configured?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I believe that there are default values populated already. I would suggest leaving those intact.
I have lowered mine in the lab and have run into situation where it has locked me out.
Had to remove the SAM rule created by SmartEvent to regain the access.
If you do have vulnerability scans going through the firewall, do not forget to add those to exceptions.
Regards,
Vladimir
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
How to configure Security Gateway to detect and prevent port scan
Kind regards,
Jozko Mrkvicka
Jozko Mrkvicka
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 29 | |
| 15 | |
| 14 | |
| 13 | |
| 7 | |
| 7 | |
| 5 | |
| 5 | |
| 4 | |
| 4 |
Upcoming Events
Wed 05 Nov 2025 @ 11:00 AM (EST)
TechTalk: Access Control and Threat Prevention Best PracticesThu 06 Nov 2025 @ 10:00 AM (CET)
CheckMates Live BeLux: Get to Know Veriti – What It Is, What It Does, and Why It MattersTue 11 Nov 2025 @ 05:00 PM (CET)
Hacking LLM Applications: latest research and insights from our LLM pen testing projects - AMERTue 11 Nov 2025 @ 10:00 AM (CST)
Hacking LLM Applications: latest research and insights from our LLM pen testing projects - EMEAAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter


