- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity AI Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
CheckMates Fest 2026
Join the Celebration!
AI Security Masters
E1: How AI is Reshaping Our World
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Maestro Madness
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- General Topics
- :
- Re: First packet isn't sync
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jump to solution
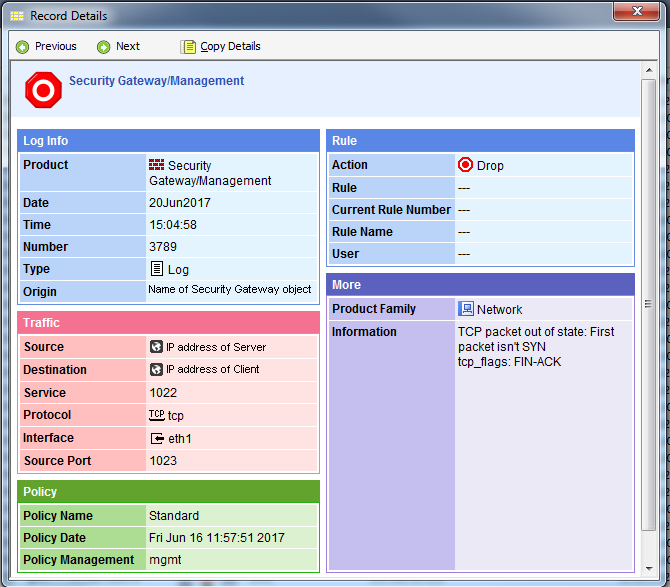
First packet isn't SYN
my gateway R80.10 and multicast cluster working. but internet is very slow and didnot drop any packet.
only one drop packet is below picture. how can i solve this issue?
- Tags:
- r80.x
1 Solution
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
If I see an "out of state" error and the TCP flags involved are FIN and/or RST, I generally ignore them as they tend to be harmless in the majority of cases. It simply indicates that the subject connection was not terminated cleanly as far as the firewall is concerned; this can be caused by many things including poorly-written applications and transient network and/or system problems. However if these "out of state" logs for RST/FIN are conclusively correlated with application performance problems, TCP state logging (sk101221) and sending a TCP RST upon connection expiration (sk19746) can be useful here. The former SK was covered in my book, while the latter SK was mentioned in the addendum to my book available for free at the URL below.
But the following combinations in an "out of state" error message will tend to get my attention:
SYN-ACK - Strong indicator of asymmetric routing on the forward path (from the connection's perspective), where the firewall is only seeing the return direction of the TCP 3-way handshake.
ACK all by itself - Probably asymmetric routing on the return path (from the connection's perspective).
ACK accompanied by PSH (or perhaps just ACK by itself) - The connection was timed out by the firewall due to inactivity.
--
My book "Max Power: Check Point Firewall Performance Optimization"
now available via http://maxpowerfirewalls.com.
Gaia 4.18 (R82) Immersion Tips, Tricks, & Best Practices Video Course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
7 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
For TCP connections, the first packet the Security Gateway expects to see is a TCP SYN.
This packet would then be evaluated by the rulebase to determine whether or not the connection is permitted.
If it sees a TCP packet that is not a SYN and it can be associated with an existing allowed connection, then the packet will pass.
In the case where the TCP packet is NOT a SYN and cannot be associated with an existing connection, you see this error.
If you search on the phrase "First packet isn't SYN" in SecureKnowledge, there are several possible reasons this might occur.
In your case, it looks like a FIN-ACK packet has been received.
These are associated with closing a TCP connection gracefully.
The Security Gateway had already aged out the connection from the connections table, which happens after the TCP End Timeout (40 seconds by default, as I recall).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
How can we resolve this ? do we increase the TCP end timeout?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
create a new service for the interested connections and increase his session timeout if it is really needed
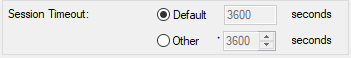
do not modify stateful inspection settings or any file on your management ![]()
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I would first check routing. Make sure, out and in packets use same route and same checkpoints inerface.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
If I see an "out of state" error and the TCP flags involved are FIN and/or RST, I generally ignore them as they tend to be harmless in the majority of cases. It simply indicates that the subject connection was not terminated cleanly as far as the firewall is concerned; this can be caused by many things including poorly-written applications and transient network and/or system problems. However if these "out of state" logs for RST/FIN are conclusively correlated with application performance problems, TCP state logging (sk101221) and sending a TCP RST upon connection expiration (sk19746) can be useful here. The former SK was covered in my book, while the latter SK was mentioned in the addendum to my book available for free at the URL below.
But the following combinations in an "out of state" error message will tend to get my attention:
SYN-ACK - Strong indicator of asymmetric routing on the forward path (from the connection's perspective), where the firewall is only seeing the return direction of the TCP 3-way handshake.
ACK all by itself - Probably asymmetric routing on the return path (from the connection's perspective).
ACK accompanied by PSH (or perhaps just ACK by itself) - The connection was timed out by the firewall due to inactivity.
--
My book "Max Power: Check Point Firewall Performance Optimization"
now available via http://maxpowerfirewalls.com.
Gaia 4.18 (R82) Immersion Tips, Tricks, & Best Practices Video Course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The issue with FIN-ACK can also arise if you have software blades (HTTPS interception,...) on that check the content.
For HTTPS see:
TCP [FIN-ACK] packets for HTTPS traffic are dropped as out-of-state after enabling HTTPS Inspection
Regards
Heiko
➜ CCSM Elite, CCME, CCTE ➜ www.checkpoint.tips
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 19 | |
| 10 | |
| 10 | |
| 10 | |
| 6 | |
| 2 | |
| 2 | |
| 2 | |
| 2 | |
| 2 |
Upcoming Events
Thu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: Exposing AI Vulnerabilities: CP<R> Latest Security FindingsThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter


