- Products
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Maestro Madness
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- General Topics
- :
- Connection limit for particular access rule
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Connection limit for particular access rule
One of our Major Account customer (Stock Exchange) would like to configure the connection limit for specific source, Destination and Service. (the same way where Cisco ASA can set the connection limit for particular access-list)
Can we achieve this if yes, who can we do that?
12 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Use Check Point Qos and define your required limit.
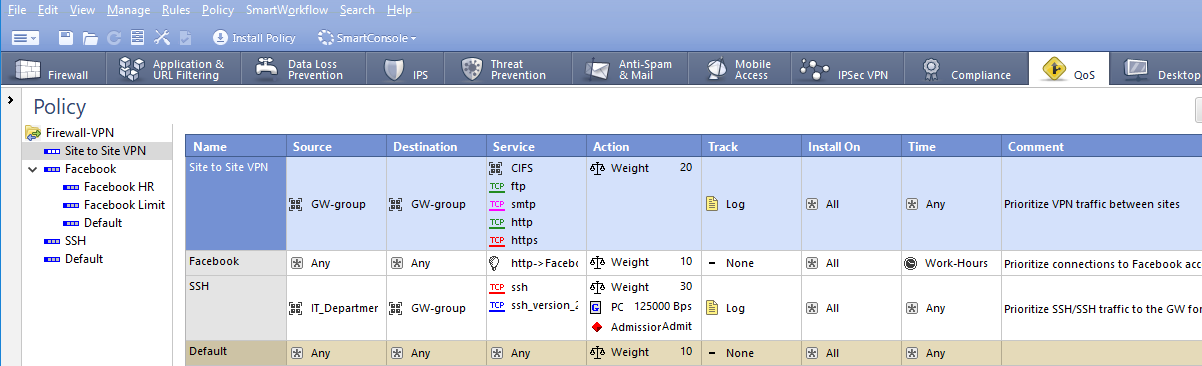
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
There is so many limitation if we use the QOS blade. Do was have any other way where we can set this or use any way to configure embryonic connection limit.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Customer was using Cisco ASA and refreshed it with 5800-NGTP and now they want to the same function as per below below cisco link
Without QOS who can we handle this. Also who we handle the embryonic connections and can we set the limit and timeout for those.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Session Timeouts can be configured within service objects:

- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks Danny, but this will not helpful in this scenario,
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
...and Danny Jung's suggestion for regular session timeouts.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Maybe a rate limiting rule with fw samp?
sk112454
| LIMIT1-NAME LIMIT1-VALUE LIMIT2-NAME LIMIT2-VALUE ... | Specifies quota limits and their values:
|
[Expert@HostName:0]# fw [-d] samp add [-S <SAM_Server>] [-t <Timeout>] {-a <d|r|n|b|q|i>} [-l <r|a>] [-n <name>] [-c <comment>] [-o <originator>] {ip <IP filter arguments>|quota <Quota filter arguments>}
untested
fw samp add -n 10_conns ip -s 192.168.0.0 -m 255.255.0.0 -d 10.1.1.1 -m 255.255.255.255 quota concurrent-conns 10
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Well, SAMP will create whole new set of rules that have to be correlated to the security policy.
It would be nice if in addition to the bandwidth limits already available for any rule, the limits for concurrent connections are introduced.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Is there any roadmap to provide this configuration via smart Console in near future?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I don't think so. The nearest roadmap is the one for R80.20 which doesn't list SAM policies.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The options for doing this today are pretty well detailed in this thread.
If you're looking for a different way to do it, then it would have to be handled as an RFE through Solution Center.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello Mahipal Singh,
You can use samp rule as below for this your requirement.
example;
fw samp add -a d -l r quota service 17/123 source any destination any concurrent-conns 100000 flush true
Example of Rate Limiting HTTP Connections:
This rule limits connections on TCP port 80 to the server at 192.168.3.4. The limit is 20 new connections per
second, per client, and the rule times out after 1 hour (3600 seconds):
fw samp add -a d -l r -t 3600 quota service 6/80 destination cidr:192.168.3.4/32 new-conn-rate 20 track source flush true
If a majority of the DoS traffic is coming from a specific region, add the source option to the rule. For
example, this rule applies only to hosts from Botland, with country code QQ (an imaginary country):
fw samp add -a d -l r -t 3600 quota service 6/80 source cc:QQ destination cidr:192.168.3.4/32 new-conn-rate 20 track source flush true
Example of a rule with ASN:
This rule drops all packets (-a d) with the source IP address in the IPv4 address block
(cidr:192.0.2.0/24), from the autonomous system number 64500 (asn:AS64500😞
fw samp -a d quota source asn:AS64500,cidr:192.0.2.0/24 service any pkt-rate 0
flush true
Good Luck,
Ali
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 12 | |
| 10 | |
| 9 | |
| 8 | |
| 6 | |
| 3 | |
| 2 | |
| 2 | |
| 2 | |
| 1 |
Upcoming Events
Tue 16 Dec 2025 @ 05:00 PM (CET)
Under the Hood: CloudGuard Network Security for Oracle Cloud - Config and Autoscaling!Thu 18 Dec 2025 @ 10:00 AM (CET)
Cloud Architect Series - Building a Hybrid Mesh Security Strategy across cloudsTue 16 Dec 2025 @ 05:00 PM (CET)
Under the Hood: CloudGuard Network Security for Oracle Cloud - Config and Autoscaling!Thu 18 Dec 2025 @ 10:00 AM (CET)
Cloud Architect Series - Building a Hybrid Mesh Security Strategy across cloudsAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter


