- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity AI Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
CheckMates Fest 2026
Join the Celebration!
AI Security Masters
E1: How AI is Reshaping Our World
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Maestro Madness
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- General Topics
- :
- ClusterXL with two public IP ranges
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
ClusterXL with two public IP ranges
I can use your advise on this subject.
Scenario:
Client getting a /30 and /24 IP ranges from ISP.
ISP expects connectivity between themselves and a client over /30 network.
ISP will be forwarding /24 traffic to the single IP in the /30 network.
ISP does not provide routing equipment.
Client does not have an L3 device between cluster and ISP.
What is the appropriate configuration for the cluster and its members to accommodate this scenario?
I am trying to avoid the use of the manual Proxy ARP and rely on Static NAT for the hosts in DMZs.
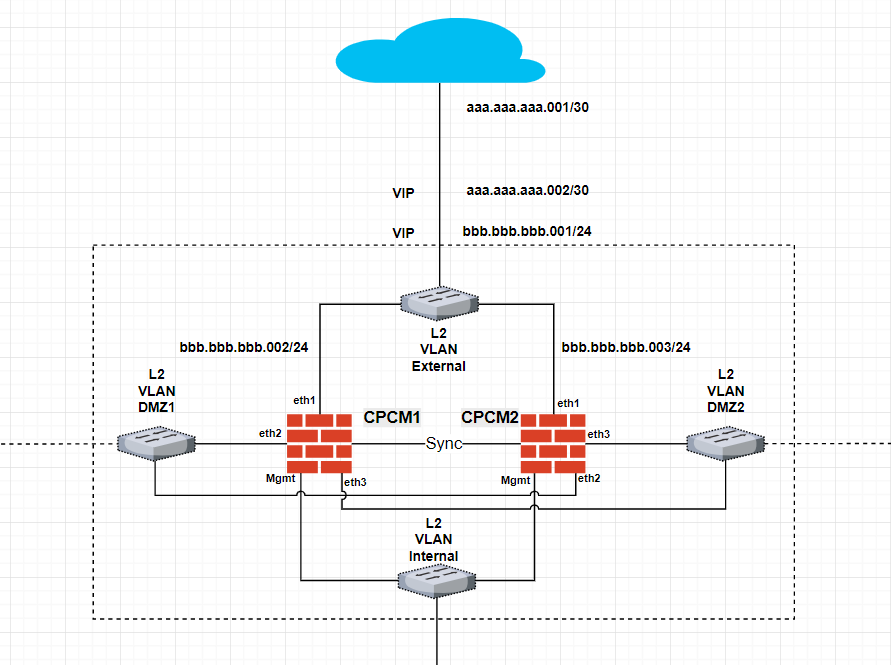
Thank you,
Vladimir
11 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Since ClusterXL does not support one interface being in two different subnets, you might have to connect two physical interfaces to that network segment (one for the /24, the other on /30).
You might need to use private IPs for the interfaces in the /30 segment and make the ClusterXL IP on that interface something in the /30.
You might need to use private IPs for the interfaces in the /30 segment and make the ClusterXL IP on that interface something in the /30.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
"Since ClusterXL does not support one interface being in two different subnets, you might have to connect two physical interfaces to that network segment (one for the /24, the other on /30)."
It there a reason for the physical interfaces of the cluster members on these two network to reside on the same L2 segment?
It seems that if they are on a different L2 segment or the same one, the cluster will have to undertake some roundabout internal routing to forward packets between these two networks.
"You might need to use private IPs for the interfaces in the /30 segment and make the ClusterXL IP on that interface something in the /30."
What about using public IPs from /24 for physical interfaces while using single IP from /30 for external VIP?
Would this permit the inbound and outbound routing for both public ranges? Is so, what additional configuration parameters may be required to differentiate it from common single public VIP when used with RFC 1918 addresses on physical interfaces?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Vladimir,
as Dameon wrote, I think the best way is to use two IPs for the physical interfaces outside on it‘s own private network. One of the IPs from your /30 network should be the cluster VIP.
If you need the addresses from the /24 - pool for real hosts you can deploy a new cluster interface for this subnet and attache it to an switch.
If doing only NAT with this pool you can use it in your rulebase. As you wrote, the ISP is routing this network from external to one of the addresses from /30 pool. You don‘t need any proxy ARP for NAT like this.
your question...
<<<< What about using public IPs from /24 for physical interfaces while using single IP from /30 for external VIP? <>>>>
I think it‘s better to have the /24 subnet separate from the other IPs, the routing and NAT is clearly.
Wolfgang
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you @Wolfgang.
I was not sure, for some reason, that the cluster will source the outbound traffic from otherwise arbitrary IP addresses from its external interfaces.
I have just tested it on a single gateway and it does seem to work as you and @PhoneBoy have described:
Host on internal private network statically NAed to the public IP from the range NOT assigned to any of the interfaces or defined in topology is being routed out with the XLATE of the defined public IP out of its external interface.
So long as ISP will be forwarding the traffic to /24 in question, this should work for Static NAT purposes.
The only deviation from norm is that the cluster's portals will be accessible by the IP from /30 range, but the hosts behind it by IPs from /24.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Vladimir,
you ˋre right.
we had a similar configuration at one of our customer sites. They are using a smaller subnet /29 for internet access and two other /26 subnets for a lot of published webservices and . The /26 are all statically NATed and the IP for remote access ( MobileAccessPortal and VPN) is from /29 subnet.
regards
Wolfgang
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi!
I'm not 100% sure if I fully understood your question, but there is a way to configure cluster members with different IP ranges:
See sk32073 for configuration instructions.
I configured this last fall for a client who got had only one public IP-address from the ISP.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you @Lari_Luoma , the question was really in regards to the gateway NATing to the IPs that do not belong to the ranges the interfaces are in.
I am routinely using it in cases of overlapping VPN domains, but was not sure if it'll work for the normal traffic.
Looks like it does.
Regards,
Vladimir
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Lari,
hope you doing well, I have a question same as you mentioned for customer with 1 Public IP, in my case I have 2 Public IP avaliable and other 4 IP's being used 1 for Default Gateway and other 3 for Public Facing services.
I have tried configure Cluster with RFC 1918 FW-1 10.10.10.1/24 and FW-2 10.10.10.2/24 and VIP as Public IP 80.90.239.147/24 (this is dummy Publci IP)
deafult route on both members
set static-route 80.90.239.144/29 nexthop gateway logical eth8 on
set static-route default nexthop gateway address 80.90.239.145 on
did set the arp for both private IPs as
FW-1
add arp static ipv4-address 10.10.10.2 macaddress 00:1C:E2:D1:1A:A5
FW-2
add arp static ipv4-address 10.10.10.1 macaddress 00:1C:E1:D2:19:C1
can not route the traffic and internet didnt work good thing was I didnt get any warrning when policy installed.
any sugesstion...
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
All steps you should need are documented in ClusterXL Admin Guide.
If you still won't get it working, I recommend you open a TAC case for further troubleshooting and debugging.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@kamaladmire1 following the given information you have configured different IP subnet for your public IP
80.90.239.147/24 your public IP
80.90.239.144/29 your default route
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
sorry that was a typo when writing to you it is on 80.90.239.147/29
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 16 | |
| 10 | |
| 10 | |
| 8 | |
| 7 | |
| 3 | |
| 2 | |
| 2 | |
| 2 | |
| 2 |
Upcoming Events
Thu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: Exposing AI Vulnerabilities: CP<R> Latest Security FindingsThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter


