- Products
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- Learn
- Local User Groups
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
- Partners
- More
- ABOUT CHECKMATES & FAQ
- Sign In
- Leaderboard
- Events
Call For Papers
Your Expertise, Our Stage
The Great Exposure Reset
AI Security Masters E4:
Introducing Cyata - Securing the Agenic AI Era
AI Security Masters E3:
AI-Generated Malware
CheckMates Go:
CheckMates Fest
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- General Topics
- :
- Check Point R80.20 Production and Public EA
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Check Point R80.20 Production and Public EA
If you can't wait for R80.20 to be released, you can now participate in the Early Availability program.
We offer both Production and Public EA versions.
Production EA
Who Qualifies for the Production EA program?
- We are looking for customers willing to deploy in a production environment and willing to work directly with R&D
- Existing working environments in R80.10 / R77.30
- Production EA covers both Gateway and Management
- Complete the online questionnaire: https://www.checkpoint.com/surveys/R80_20_EA_Questionnaire
- For any question, contact us at : EA_SUPPORT@checkpoint.com
Public EA
IMPORTANT – Check Point Public EA is only for lab and sandbox deployments
Public EA (as of 23 May 20th 2018) covers Gateway and Management!
To gain access to the public EA:
- UserCenter:
- Register to the Public EA release via - usercenter.checkpoint.com -> TRY OUR PRODUCTS -> Early Availability Programs -> CPEA-EVAL-R80.20
- PartnerMAP:
- Register to the Public EA release via - usercenter.checkpoint.com -> LEARN -> Early Availability Programs -> CPEA-EVAL-R80.20
What's new in R80.20
Acceleration
- HTTPS Inspection performance improvements
- Session rate improvements on high-end appliances (including 2012 appliances and 13000 and above appliances)
- Acceleration is enabled during policy installation
Threat Prevention
- Threat Prevention Indicators (IoC) API
- Management API support for Threat Prevention Indicators (IoC)
- Add, delete, and view indicators through the management API
- Threat Prevention Layers
- Support layer sharing within Threat Prevention policy
- Support setting different administrator permissions per Threat Prevention layer
- MTA (Mail Transfer Agent)
- MTA monitoring:
- E-mails history views and statistics, current e-mails queue status and actions performed on e-mails in queue
- MTA configuration enhancements:
- Setting a next-hop server by domain name
- Stripping or neutralizing malicious links from e-mails
- Adding a customized text to a malicious e-mail's body or subject
- Malicious e-mail tagging using an X-header
- Sending a copy of the malicious e-mail
- MTA monitoring:
- ICAP
- ICAP server support on a Security Gateway to consult with Threat Emulation and Anti-Virus Deep Scan whether a file is malicious
- Threat Emulation
- SmartConsole support for multiple Threat Emulation Private Cloud Appliances
- SmartConsole support for Blocking files types in archives
Identity Awareness
- Identity Tags support the use of tags defined by an external source to enforce users, groups or machines in Access Roles matching
- Identity Collector support for Syslog Messages - ability to extract identities from syslog notifications
- Identity Collector support for NetIQ eDirectory LDAP Servers
- Improved Transparent Kerberos SSO Authentication for Identity Agent
- Two Factor Authentication for Browser-Based Authentication (support for RADIUS challenge/response in Captive Portal and RSA SecurID next Token/Next PIN mode)
- New configuration container for Terminal Servers Identity Agents
- Ability to use an Identity Awareness Security Gateway as a proxy to connect to the Active Directory environment, if SmartConsole has no connectivity to the Active Directory environment and the gateway does
- Active Directory cross-forest trust support for Identity Agent
- Identity Agent automatic reconnection to prioritized PDP gateways
- Additional filter options for identity collector - "Filter perSecurity Gateway" and "Filter by domain"
- Improvements and stability fixes related to Identity Collector and Web-API
Mirror and Decrypt
- Decryption and clone of HTTP and HTTPS traffic
- Forwarding traffic to a designated interface for mirroring purposes
Hardware Security Module (HSM)
- Enhancement of outbound HTTPS Inspection with a Gemalto SafeNet HSM Appliance
- SSL keys are stored when using HTTPS Inspection
Clustering
- Sync redundancy support (over bond interface)
- Automatic CCP mode (either Unicast, Multicast or Broadcast mode)
- Unicast CCP mode
- Enhanced state and failover monitoring capabilities
- OSPFv3 (IPv6) clustering support
- New cluster commands in Gaia Clish
Advanced Routing
- Allow AS-in-count
- IPv6 MD5 for BGP
- IPv6 Dynamic Routing in ClusterXL
- IPv4 and IPv6 OSPF multiple instances
- Bidirectional Forwarding Detection (BFD) for gateways and VSX, including IP Reachability detection and BFD Multihop
Access Policy
- New Wildcard Network object supported in Access Control policy
- Simplified management of Network objects in a security policy
- HTTPS Inspection now works in conjunction with HTTPS web sites categorization. HTTPS traffic that is bypassed will be categorized.
- Rule Base performance improvements, for enhanced rule base navigation and scrolling
- Global VPN Communities. Previously supported in R77.30.
Compliance Blade
- Add customized best practices for gateways based on your personal scripts
- Support for 35 regulations including GDPR
Security Management
- Upgraded Linux kernel (3.10)
- Additional support for Open Servers hardware
- New file system (xfs)
- More than 2TB support per a single storage device
- Enlarged systems storage (up to 48T tested)
- I/O related performance improvements
- Support of new system tools for debugging, monitoring and configuring the system
- iotop (provides I/O runtime stats
- lsusb (provides information about all devices connected to USB)
- lshw (provides detailed information about all HW)
- lsscsi (provides information about storage)
- ps (new version, more counters)
- top (new version, more counters)
- iostat (new version, more counters)
- Multiple simultaneous sessions in SmartConsole - One administrator can publish or discard several SmartConsole private sessions, independently of the other sessions.
- Integration with a Syslog server (previously supported in R77.30) - A Syslog server object can be configured in SmartConsole to send logs to a Syslog server.
SmartProvisioning
- Integration with SmartProvisioning (previously supported in R77.30)
- Support for the 1400 series appliances
- Administrators can now use SmartProvisioning in parallel with SmartConsole
vSEC Controller Enhancements
- Integration with Google Cloud Platform
- Integration with Cisco ISE
- Automatic license management with the vSEC Central Licensing utility
- Monitoring capabilities integrated into SmartView
- vSEC Controller support for 41000, 44000, 61000, and 64000 Scalable Platforms
Endpoint Security Server
Managing features that are included in R77.30.03:
- Management of new blades:
- SandBlast Agent Anti-Bot
- SandBlast Agent Threat Emulation and Anti-Exploit
- SandBlast Agent Forensics and Anti-Ransomware
- Capsule Docs
- New features in existing blades:
- Full Disk Encryption
- Offline Mode
- Self Help Portal
- XTS-AES Encryption
- New options for the Trusted Platform Module (TPM)
- New options for managing Pre-Boot Users
- Media Encryption and Port Protection
- New options to configure encrypted container
- Optical Media Scan
- Anti-Malware
- Web Protection
- Advanced Disinfection
- Full Disk Encryption
Additional Enhancements
- HTTPS Inspection support for IPv6 traffic
- Additional cipher suites support for HTTPS inspection
- Improvements in policy installation performance on R80.10 and higher gateways with IPS
- Network defined by routes - gateway's topology is automatically configured based on routing
- IPS Domain Purge on Security Management Server - IPS update packages are saved for 30 days, older packages are purged.
- SmartConsole Extensions – an open API platform for extending Smart Console with third-party and in-house tools and features.
- Compressed snapshots - reduced system snapshot size.
26 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Great! I’ve registered for the Public EA.
My blog: https://checkpoint.engineer
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you https://community.checkpoint.com/people/dwelccfe6e688-522c-305c-adaa-194bd7a7becc
But we still waiting a solution for DPD full support. Check Point proprietary protocol cannot provide multiple link vpn with 3rd party VPN Routers ![]()
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
For those wondering, we've also added the relevant migration tools to the EA downloads.
This will allow you to take an export from an existing management running R77.x or R80.x and import it to R80.20 EA Management.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
An R80.20EA tip here (thanks Tomer Sole for sharing this one and correcting me):
For those interested in the API documentation in it's EA form, it's available on https://mgmt-ip/api_docs (after you enable the API to IPs other than localhost).
This feature does NOT exist in R80.10 or R80, sadly.
Hope we can keep this feature in the GA release as it is VERY handy to have local documentation.
This also works in R80/R80.10 as well, FYI.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
So far it doesn't work for me on R80.10
<< We make miracles happen while you wait. The impossible jobs take just a wee bit longer. >>
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I checked it on my R80.10 install and it worked.
For this specific issue, we should discuss on the following thread: Tip of the Day: Local R80.x API Documentation
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I've just heard and registered straight away. Thanks you guys please keep improving CP...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Finally, more than 2TB storage supported : )
I'm also curious as to the new Clustering CLISH commands. new functionality or just moving some smartconsole tasks to CLI?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
As the public EA is for management only, I assume the clish commands for clusters aren't relevant yet ![]()
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Support for < 2TB of storage when I built our new MGMT server bit me. Had to redo RAID configurations and burn HD space, but got it running eventually.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Any ETA for the GA?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The dates depend on results from the EA, particularly Production EA.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you Dameon Welch Abernathy
At the top of this page you stated: "
Public EA
IMPORTANT – Check Point Public EA is only for lab and sandbox deployments
Also Public EA only covers Management at this time (not gateway) "
So if I understand correctly, under the current Public EA Program is not possible to run / test any type of Security Gateways with the SW Image R80.20 - testing is limited to Security Management Servers only.
When would it be possible to test the new R80.20 Security Gateway features ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
That's correct, the current public EA is only for Security Management.
The timeline for Public EA for R80.20 Security Gateway has not been finalized.
Private EAs for R80.20 include Security Gateway, and you should apply if you're interested and meet the criteria.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Note that we released a new version of the public EA for R80.20 that now includes Security Gateway support.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
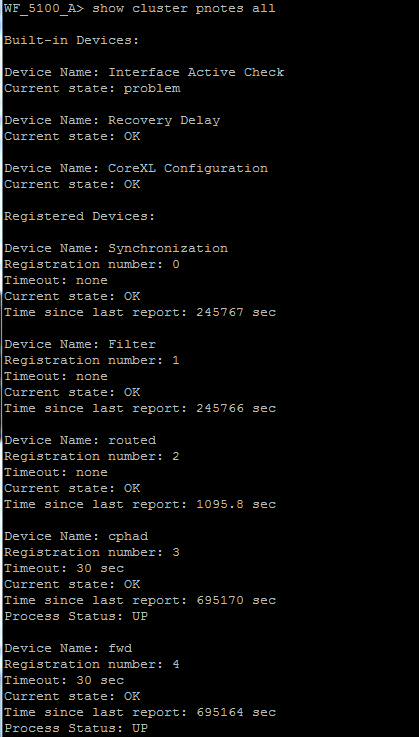
Some details on a few of the features here:
- Auto CCP - The feature aims to automate CCP mode configuration, and make it adaptive to changes in the network, preventing unnecessary failovers and interface state changes due to CCP packet not being received as a result of networking issues.
- Automatically choose between Unicast/Multicast/Broadcast
- Default is Unicast CCP
- Less noise (Multicast CCP – 8116)
- New CCP Unicast mode - A new Default mode allowing cluster members to send CCP to the unicast address of the peer member.
- Cluster Clish commands (not only in expert mode anymore)
- Control (Pnote/ccp/debug…)

- Monitor(list/interfaces…)
- Control (Pnote/ccp/debug…)

- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Nice new features, when we'ill can testy GW R80.20?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The new public EA build includes Security Gateway functionality.
You can test immediately ![]()
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You're right, Thanks! ![]()
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Is full database revision restore supported in r80.20? similar to what was possible in r77.30?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Not as far as I know.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
R80.10 1-click policy restore is still the norm for R80.20. We plan to add more capabilities to the Automatic Revisions that compose the Security Management Server in our next releases, not in R80.20. Discussion for this is here: How do you rollback an old policy?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
Thanks for this. So basically, policy restore is the same as it was in r80.10, full database restore is still not available?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Capabilities should be similar to R80.10 in this regard, yes.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The Public EA builds were updated today on User Center.
The Public EA also includes Security Gateway in addition to Security Management.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Looks like a new public EA was made available 1 August.
Also, we are not currently planning to support the Accelerator Cards with the GA release of R80.20, so I have removed it from the above notes about what features are supported.
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 28 | |
| 16 | |
| 10 | |
| 9 | |
| 7 | |
| 7 | |
| 6 | |
| 5 | |
| 5 | |
| 3 |
Upcoming Events
Tue 03 Mar 2026 @ 04:00 PM (CET)
Maestro Masters EMEA: Introduction to Maestro Hyperscale FirewallsTue 03 Mar 2026 @ 03:00 PM (EST)
Maestro Masters Americas: Introduction to Maestro Hyperscale FirewallsTue 03 Mar 2026 @ 04:00 PM (CET)
Maestro Masters EMEA: Introduction to Maestro Hyperscale FirewallsTue 03 Mar 2026 @ 03:00 PM (EST)
Maestro Masters Americas: Introduction to Maestro Hyperscale FirewallsFri 06 Mar 2026 @ 08:00 AM (COT)
Check Point R82 Hands‑On Bootcamp – Comunidad DOJO PanamáAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter


