- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity AI Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
CheckMates Fest 2026
Join the Celebration!
AI Security Masters
E1: How AI is Reshaping Our World
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
R82.10 and Rationalizing Multi Vendor Security Policies
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- General Topics
- :
- About Global properties
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
About Global properties
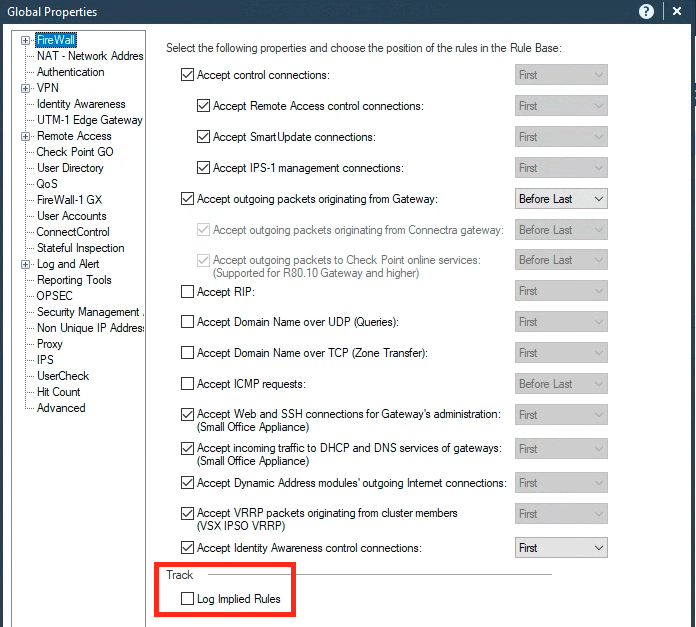
Can you please help us the working of Accept Domain name over UDP (queries) and Accept Domain Name over TCP (Zone transfer) in the global properties.
If we enable what it exactly does.
Regards,
Vengatesh SR
8 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Vengatesh SR,
This option will enabled DNS queries on UDP/53 and DNS zone transfer over TCP/53 using a implicit rule. In other words, it not necessary create a rule on rulebase to accept dns traffic if this option is enabled.
Alisson Lima
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
yes we can see the implicit rule created if we enable the Accept Domain name over UDP (queries) and Accept Domain Name over TCP (Zone transfer). We have already enabled it in our production device. We need to know if we can disable it now we will get any impact or not.
And also wanted to know what it exactly does if we kept enabled.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
If you disable these global properties, then DNS lookups and zone transfers through the firewall will be blocked unless it is permitted by a different rule.
If you don't know if these things are happening through the he Security Gateway, then I recommend logging Implied Rules for a time before deciding to disable these properties.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
What is best practice , shold we enable accept ICMP request in implied rules?
if firewall interface is gateway for vlan and server in that vlan required to ping gateway interface what other solution? should we allow before stealth rule?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Don't believe enabling via implied rules is strictly necessary.
ICMP would need to be allowed prior to your stealth rule, yes.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Dameon brings up a good point here, and this is a topic I cover in the CCSA classes that I teach. The stealth rule should always be one of the first rules in your Network/Firewall policy layer, but what kind of rules need to appear prior to the stealth rule? The main ones are:
- Administrative Access Rules - Allowing SSH/HTTPS/4434 from trusted internal hosts/networks to the firewall itself for purposes of management via the Gaia Web interface and clish/expert mode.
- Ping/Traceroute - If you want the firewall to answer pings sent directly to one of its interfaces and/or show up as a visible hop in a traceroute, you'll need a rule allowing it. Generally I don't have a problem with the firewall responding to pings/traceroutes sent from an internal reasonably-trusted network, but definitely not for the Internet. Note that including the traceroute service in a rule used to halt SecureXL Accept Templating from that point (i.e. "acceleration disabled from rule #X"), but this limitation was lifted in gateway code version R80.10.
- SNMP/NMS Polling - If you have a Network Management Station (NMS) initiating SNMP polls to the firewall, you'll need an explicit rule allowing it. Notice that it is possible to only allow the NMS to perform SNMP reads by utilizing the special service snmp-read, which would be considered best practices unless the NMS is performing SNMP set operations which is not too likely. Netflow and external authentication connections such as RADIUS/TACACS initiated by the firewall itself will be allowed by default (implied rule "Accept outgoing packets from gateway") unless you explicitly block it.
- DHCP Server/Relay - If the firewall is performing DHCP Relay or acting as a DHCP server, the rules permitting this traffic must appear prior to the stealth rule.
There are a few other corner-case rules that have to appear prior to the Stealth Rule (VRRP multicast advertisements, legacy Client Authentication, SecureRemote Topology Downloads, etc.) but these are the big ones.
Gaia 4.18 (R82) Immersion Tips, Tricks, & Best Practices Video Course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi! Could you help me please, i need to watch Global Properties in cli, how can i get this?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@Alisson_Lima is 100% correct. In simple words, anything you enable in that section would allow connection on implied rule, so you dont have to create specific policy based rules for it.
From R80 smart console guide, you can also click on help section and read it there as well. Hope that helps.
- First - Applied first, before all other rules in the Rule Base - explicit or implied
- Last - Applied last, after all other rules in the Rule Base - explicit or implied, but before the Implicit Cleanup Rule
- Before Last - Applied before the last explicit rule in the Rule Base
Best,
Andy
Andy
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 18 | |
| 11 | |
| 6 | |
| 4 | |
| 3 | |
| 3 | |
| 2 | |
| 2 | |
| 2 | |
| 2 |
Upcoming Events
Thu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldFri 09 Jan 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 42: Looking back & forwardThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: Exposing AI Vulnerabilities: CP<R> Latest Security FindingsThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldFri 09 Jan 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 42: Looking back & forwardThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter


