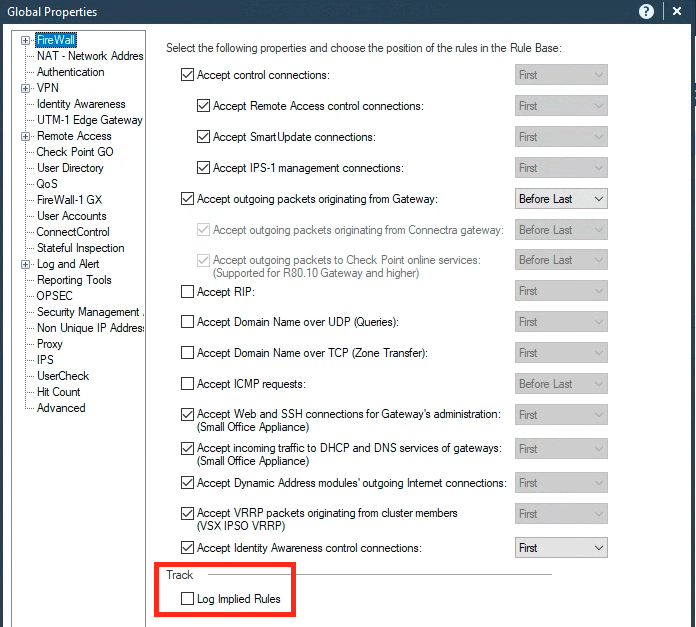
Dameon brings up a good point here, and this is a topic I cover in the CCSA classes that I teach. The stealth rule should always be one of the first rules in your Network/Firewall policy layer, but what kind of rules need to appear prior to the stealth rule? The main ones are:
- Administrative Access Rules - Allowing SSH/HTTPS/4434 from trusted internal hosts/networks to the firewall itself for purposes of management via the Gaia Web interface and clish/expert mode.
- Ping/Traceroute - If you want the firewall to answer pings sent directly to one of its interfaces and/or show up as a visible hop in a traceroute, you'll need a rule allowing it. Generally I don't have a problem with the firewall responding to pings/traceroutes sent from an internal reasonably-trusted network, but definitely not for the Internet. Note that including the traceroute service in a rule used to halt SecureXL Accept Templating from that point (i.e. "acceleration disabled from rule #X"), but this limitation was lifted in gateway code version R80.10.
- SNMP/NMS Polling - If you have a Network Management Station (NMS) initiating SNMP polls to the firewall, you'll need an explicit rule allowing it. Notice that it is possible to only allow the NMS to perform SNMP reads by utilizing the special service snmp-read, which would be considered best practices unless the NMS is performing SNMP set operations which is not too likely. Netflow and external authentication connections such as RADIUS/TACACS initiated by the firewall itself will be allowed by default (implied rule "Accept outgoing packets from gateway") unless you explicitly block it.
- DHCP Server/Relay - If the firewall is performing DHCP Relay or acting as a DHCP server, the rules permitting this traffic must appear prior to the stealth rule.
There are a few other corner-case rules that have to appear prior to the Stealth Rule (VRRP multicast advertisements, legacy Client Authentication, SecureRemote Topology Downloads, etc.) but these are the big ones.
Gaia 4.18 (R82) Immersion Tips, Tricks, & Best Practices Video Course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course