- CheckMates
- :
- Products
- :
- CloudMates Products
- :
- CloudGuard - WAF
- :
- UPDATE | CloudGuard AppSec Updates Regarding OpenS...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
UPDATE | CloudGuard AppSec Updates Regarding OpenSSL Nov-2022 Critical Vulnerability
In an official statement, the OpenSSL project team announced the forthcoming release of their next version which was released on Tuesday November 1st 2022. This release includes a fix for a security vulnerability, originally marked as critical but lowered to HIGH.
CloudGuard AppSec Gateway and AppSec deployments for docker and Kubernetes
If all traffic to your application is routed through CloudGuard AppSec, your application is secure even when your protected web server uses a vulnerable OpenSSL library, without any updates.
You do need to follow the instructions below to ensure that communication between CloudGuard AppSec and Check Point cloud is using a patched OpenSSL version.
CloudGuard AppSec for Linux (Embedded Agent)
Make sure that OpenSSL version used by a Server to which you added an Embedded Agent is using a non-vulnerable version of OpenSSL.
Updates to CloudGuard AppSec
CloudGuard AppSec Gateways (VMWare, AWS, Azure) and CloudGuard AppSec for Linux (Embedded Agent)
We released a new agent version with the patched OpenSSL version. The new agent version is 432762 (v1.2244.432762-hotfix-01-11-22).
Important to note - The vulnerable openSSL version is used by the AppSec agent as an SSL client, whereas the vulnerability mainly impacts server-side SSL.
-
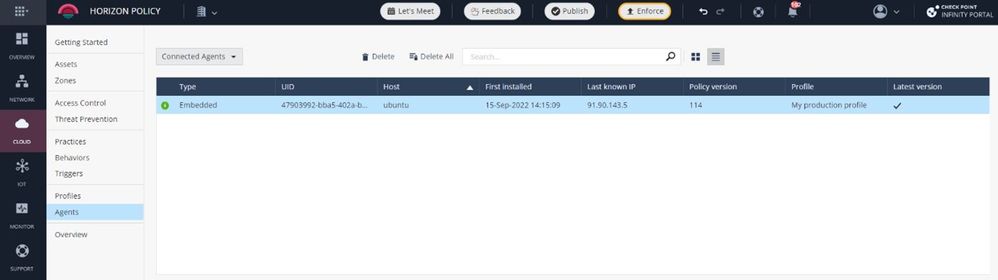
If your agent upgrade Mode is set to Automatic, you will get the fix automatically. To validate, once released, that your agents are upgraded, browse to Cloud->Agents and verify the “Latest Version” Column is checked - see example below.
-
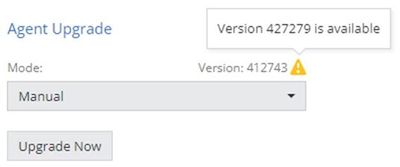
If your agent upgrade Mode is set to Manual, you will need to browse to Cloud->Profiles, edit your profile objects and click on “Upgrade Now” (there is no expected downtime when doing this upgrade). It will appear like this:
CloudGuard AppSec Gateway's pre-packaged NGINX is using an OpenSSL version which is not vulnerable.
CloudGuard AppSec Docker
CloudGuard AppSec Docker and pre-packaged NGINX with Attachment are using an OpenSSL version which is not vulnerable.
CloudGuard AppSec for Kubernetes Ingress
CloudGuard AppSec deployment package does not bring OpenSSL, but rather installs one during setup. Unless manual changes were done, the default OpenSSL library installed during deployment will be 1.1.1, which is not vulnerable.
CloudGuard AppSec / Infinity Next Cloud
Check Point is working with our public cloud providers to make sure that all cloud components are properly patched as well as our own software running in the cloud.
Labels
- Labels:
-
Critical Update
-
OpenSSL
0 Replies