- CheckMates
- :
- Products
- :
- CloudMates Products
- :
- CloudGuard - WAF
- :
- AppSec provides preemptive protection against "Tex...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Are you a member of CheckMates?
×- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
AppSec provides preemptive protection against "Text4Shell" vulnerability (CVE-2022-42889)
CVE-2022-42889 affects Apache Commons Text versions 1.5 through 1.9. It has been patched as of Commons Text version 1.10. You are advised to patch your servers as recommended by Apache.
Check Point CloudGuard AppSec machine-learning-based WAF provides preemptive protection (no software update needed) against the latest “Apache Commons Text” vulnerability (CVE-2022-42889) – a critical zero-day attack, with CVSS Score 9.8/10.
CloudGuard AppSec’s contextual machine learning engine provides preemptive protection against “text4shell” attacks (as also for e.g. Log4shell, Spring4shell) by not relying on a classical signature-based approach, as all traditional WAF solutions do, but instead by using a modern machine learning-based approach, which does not rely on signatures at all. It provides modern, effective protection for Web Applications and APIs against known and unknown attacks and can be deployed in the most common scenarios ranging from e.g. K8s ingress controllers-based protection to virtual machine-based reverse proxies (e.g. by integrating into NGINX). It’s available as a free & open-source community edition.
CloudGuard AppSec uses contextual analysis to learn how users normally interact with your web application. It then uses this information to automatically detect requests that fall outside of normal operations, and sends those requests for further analysis to decide whether the request is malicious or not.
CloudGuard AppSec’s Contextual Machine Learning Engine is powered by two different machine learning models:
- A supervised model that was trained offline and fed with millions of requests, both malicious and benign.
- An unsupervised model that is being built in real time in the protected environment. This model uses traffic patterns specific to this environment.
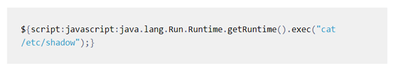
Below you can find a screenshot of an CloudGuard AppSec log created for a preemptively prevented text4shell example exploit (based on the “script” lookup prefix explained earlier above), shown as the “Matched Sample” (open-appsec would block any command (not just the one in the example):
Attached is the HTTP request then got automatically classified based on the found indicators to potential types “Remote Code Execution” and others (see “AppSec Incident Type”).
For more information please visit Check Point's Blog here.