- CheckMates
- :
- Products
- :
- CloudMates Products
- :
- Cloud Network Security
- :
- Discussion
- :
- Re: Outbound NAT Azure HA Cluster
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Are you a member of CheckMates?
×- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Outbound NAT Azure HA Cluster
Hi All,
I’ve got a Check Point R80.30 HA cluster deployed in Azure following the latest sk.
As a next step I am looking to leverage the Check Point cluster to be the Internet gateway for outbound Internet traffic and perform outbound NAT to the subnets behind it.
I'm not looking to do automatic NAT. So for my NAT rules...just for a sanity check - I’m NATing my traffic so that it changes the translated source to the private Cluster VIP address?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The final NAT to a public address happens within Azure.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi
I have the same question to NAT outbound Internet traffic behind checkpoint cloudguard cluster, don't find any clear documentation. Can someone please help
I want to NAT all internal client behind cluster IP for outbound internet access.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Salman2020
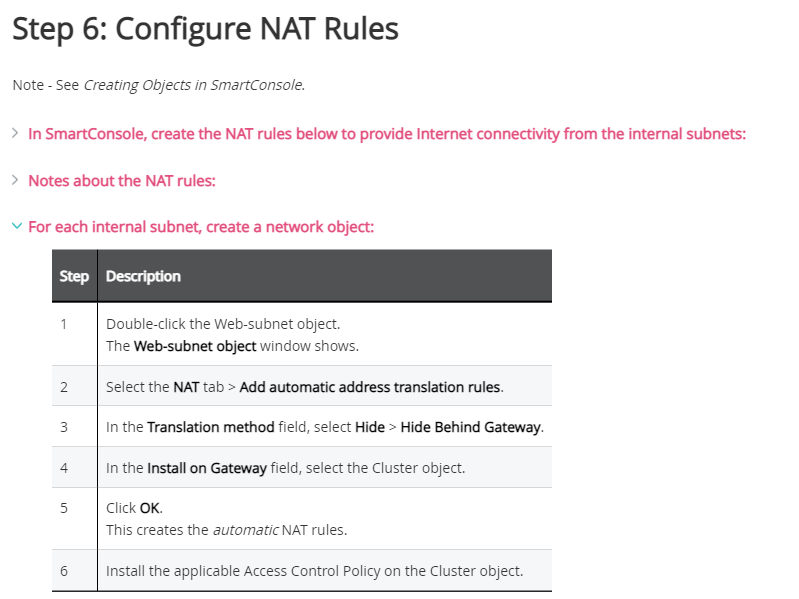
You can use the "hide behind gateway" feature on any host or network you choose.
Keep in mind, it will not use the VIP but the public address of the active gateway itself.
You can find this in the admin guide as well:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks for the response Edan,
just on this" comment Keep in mind, it will not use the VIP but the public address of the active gateway itself." if my gateways failover then NAT IP will change is that correct.
Is there any NAT option to hide for example all " source 10.0.0.0/8" behind VIP of the clusters, so egress IP will not change.
Also I want to create Manual NAT as below not automatic.
Original Source: 10.0.0.0/8 Original Destination: internet Org srv:any Translated Source : ????
what will be the translated source, VIP public, VIP private Gateway IP
many thanks in advance
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
If you want a no NAT rule, then the "translated source/destination/service" will be "Original" and should be listed at the top of the NAT rulebase.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I want to create Manual NAT rule.
Example: Original Source: 10.0.0.0/8 Original Destination: internet Translated Source : ????
what should be the translated source ? VIP public of cluster , VIP private Gateway IP or public IP of active Gateway.
Our Cloudguard HA pair running as Active/Standby.
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
For Azure to do the final NAT to a public address, you would need to use a private IP.
On this case, not sure if you use the private VIP or just the IP of the gateway.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Salman,
Technically you can use the hide behind gateway feature to hide behind the private IP of the VIP and it will work.
Do note, as this configuration is not mentioned in the admin guide, this is not a supported configuration by support.
Additionally, I'm not sure what is your goal with this, but if it's do avoid downtime, I would like to remind you that due to Azure limitations failover in Azure involves up to 15 seconds of downtime, and up to 2 minutes if VPN is used.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks Edan,
From your comment : Do note, as this configuration is not mentioned in the admin guide, this is not a supported configuration by support.
what is the supported config ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Salman,
The supported config is what was mentioned earlier from the admin guide with "hide behind gateway"