- CheckMates
- :
- Products
- :
- CloudMates Products
- :
- Cloud Network Security
- :
- Discussion
- :
- Re: Ideas needed in CheckPointCG-VMSS
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Are you a member of CheckMates?
×- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Ideas needed in CheckPointCG-VMSS
Dear CheckMates,
I need some idea on attached Topology to achieve. Anyone can help me on this please.
1) Had spinned CheckPoint-CG VMSS in Azure.
2) Placed WebServer in Backend and Outgoing Internet traffic thru VMSS works fine.
3) Inbound traffic to Webserver thru VMSS also works fine with FrontendLB configured.
4) Since VMSS cannot support Site-to-Site VPN, we used Azure VirtualNetworkGW placed in VMSS VNet (New GatewaySubnet for AzureVPN)
5) Site Connection between Azure NativeVPNGW & 3rd Party got created fine & Connected Status
6) Used VPN Route based in Azure (not BGP) in "Connections" in Azure Portal
7) Requirement is:
a) Traffic from Peer-side to reach AzureVPNGW thru S2S-Tunnel.
b) Then AzureVPNGW should forward this traffic to VMSS for Inspection.
c) After Inspection, VMSS should in-turn route the traffic to Internal WebServer.
d) Inbound is (Traffic from PeerSide =>>> S2S =>>> AzureVPNGW =>>> VMSS =>>> WebServer)
e) Outbound is (Traffic From WebServer =>>> VMSS =>>> AzureVPNGW =>>> S2S =>>> PeerSide)
f) When packet from PeerServer leaves their localGW, it got encrypted
g) But don't see this packet in VMSS (Unable to check in AzureVPNGW)
h) But Webserver sends reply packets towards VMSS for this Inbounded traffic.
i) Looks like AzureVPNGW routes the Inbound traffic directly to WebServer and not to VMSS for inspection.
I unable to configure any separate routes in AzureVPNGW towards VMSS as both are part of same VNet
Either way traffic not reaching each other.
Any ideas on how can I achieve this.
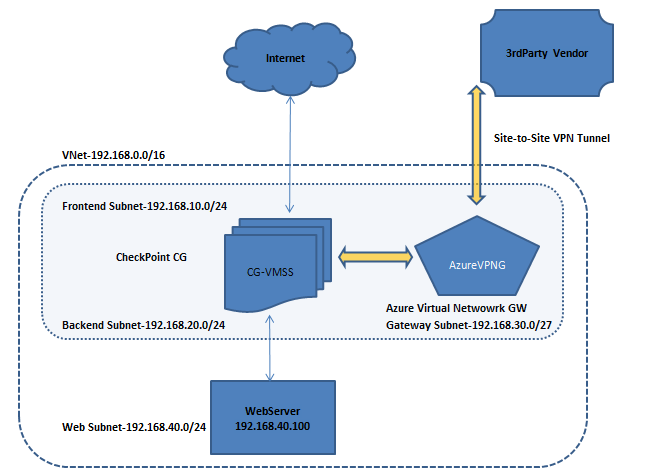
Regards, Prabu
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Prabu,
did you try to define a UDR (User Defined Route) attached to your Azure VPN Gateway subnet, to route traffic for your WebServer to your VMSS ?
something like name=To_WebServer_via_VMSS, address prefix = 192.168.40.100/32, next hop = CG-VMSS
Regards,
Raphael
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Prabu,
We can use UDR apply to the Azure Gateway subnet to route traffic to the VMSS for inspection, but pay attention, you should have:
To_WebServer, address prefix = 192.168.40.100/32, next hop: ILB of the VMSS as mentioned by Raphael
Hope help you
Kiet


