- CheckMates
- :
- Products
- :
- CloudMates Products
- :
- Cloud Network Security
- :
- Discussion
- :
- Re: Deploy AWS Cross-AZ Cluster without Public Add...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Are you a member of CheckMates?
×- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Deploy AWS Cross-AZ Cluster without Public Addresses/EIPs
Hi CheckMates,
Can I deploy a cross az cluster without the public addresses. The template from CheckPoint deploys with public connectivity and this isn't necessarily a requirement for my use case as it would only be serving east/west/south traffic. I am thinking the EIP used for cluster address could be configured as any ENI and that SmartConsole does not require it for any critical functionality? Appreciate i might be corrected there 😅
Ideally the template I create would include 2 public and 2 private subnets for ingress/egress and sync. The ENIs in public subnet wont have associated public addresses (or could use 4 private subnets). Outbound connectivity can be routed via a NAT gateway in the same VPC or via transit gateway to my outbound VPC and NATed
Any help/advice will be greatly appreciated.
C
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
1. Cross az cluster will not work without public VIP.
2. With singe az cluster you have the option to use public or private.
3. If a VPN is unnecessary, I recommend using VMSS GWLB.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Could there be future developments to negate this requirement? Would be nice to not have to provision public endpoints when they're not required.
I have deployed a GWLB cluster to manage egress traffic - these are currently deployed with public addresses as its deployed from template but again in the process of creating my own. Assuming these can be deployed without the public addresses?
Thanks for confirming.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @cdav
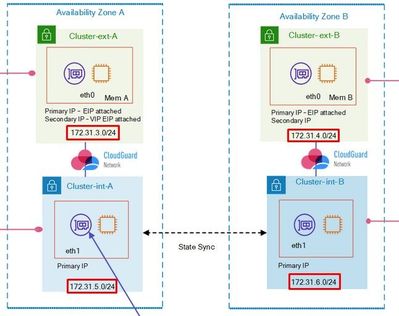
Cross AZ Cluster members located in different Availability Zones, hence in different subnets.
Using private IPs only means the Cluster IP (VIP) has to be part of the subnets range belongs to both cluster members. Since subnets ranges of cluster members are completely different , there is no way to define Cluster IP.
They way it can be achieved is to associate Elastic IP with private IP of active cluster member and move it to another member in case of failover.
The GWLB solution can be deployed without elastic IPs, this option is available in our CFT and Terraform templates.
The GWLB solution supports East-West and North-South traffic flows
For more details refer to:
CloudGuard Network for AWS Gateway Load Balancer Auto Scale Group Deployment Guide
GWLB Workshop - https://unrivaled-melba-1a81a6.netlify.app/
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @Roman_Kats thank you for the above!
Yes i understand the point regarding gateways being in different azs/subnets. Are you saying there is a way to achieve to private clustering? My understanding would be:
- deploy cluster members with interfaces in "public" subnet but no associated public address.
- create addtional eni and map to active members public eni
- in the event of failover construct a method for moving the eni to new active members eni
- still leave the "private/internal" interfaces for SYNC.
Regards,
C
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
completely misunderstood your response. Can see this isnt achievable.
Many thanks