- CheckMates
- :
- Products
- :
- CloudMates Products
- :
- Cloud Network Security
- :
- Discussion
- :
- CloudGuard VMSS instance and logging (on premise S...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Are you a member of CheckMates?
×- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
CloudGuard VMSS instance and logging (on premise SMS)
I have a question about logging for CloudGuard VMSS instances and logging.
My management server is on a on premise network and all check point ports are forwarded via static NAT from the internet gateway to the SMS. Unfortunately, I do not receive any log information from the Cloudguard VMSS instance on port 257. There is no traffic on the VMSS gateway or on the on premise internet gateway visible.
tcpdump -i eth0 -nn port --> does not display any packet
I had also tried to implement the following sk102712:
$FWDIR/conf/masters file on Security Gateway is overwritten during each policy installation - proced...
Therefore my question:
Does CloudGuard VMSS instances also use port 257?
Or Azure CME mechanissmen are used here to upload loggging informations?
Design:
[Azure VMSS instance] --> [Internet] --> [on premise FW gateway with static NAT rule] --> [SMS]
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @Nir_Shamir
I had done all that and thanks for the tips.
But I have found the issue!
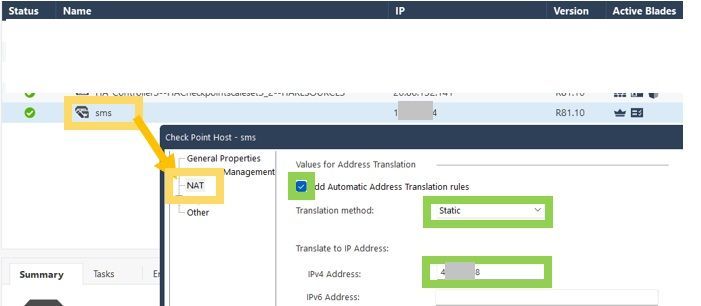
If I create a static NAT rule for the management object, everything works fine.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You may have to implement the following sk171055.
Then you can roll out the parameter via the routing script when activating the VMSS instance.
# vi $MDS_FWDIR/conf/static_route_config_<CONFIGURATION-TEMPLATE-NAME>.sh
# chmod u+x $MDS_FWDIR/conf/static_route_config_<CONFIGURATION-TEMPLATE-NAME>.sh
# autoprov_cfg set template –tn <CONFIGURATION-TEMPLATE-NAME> –cg $MDS_FWDIR/conf/static_route_config_<CONFIGURATION-TEMPLATE-NAME>.sh
Here is the content of the script. The area marked with the dots is the original routing script.
$MDS_FWDIR/conf/static_route_config_<CONFIGURATION-TEMPLATE-NAME>.sh
------------------------------------------------------------------------
#! /bin/bash
ckp_regedit -a SOFTWARE\\CheckPoint\\FW1 FORCE_NATTED_IP -n 1
.......
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
All Check Point Gateways use port 257 for logging , this of course includes CloudGuard Gateways.
which Log Server is configured in the GWs ? is it configured with its public IP or its private IP ?
You should see traffic with port 257 on the GWs , no matter what is configured.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @Nir_Shamir,
Is it configured with a public IP.
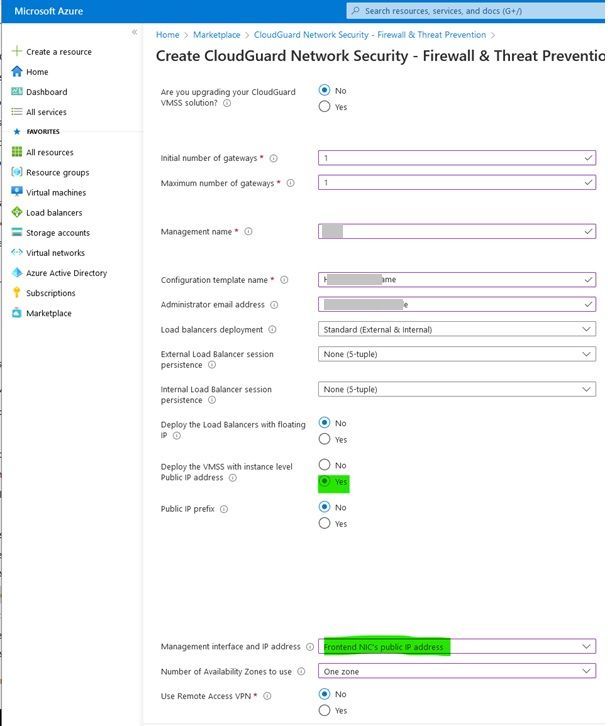
Here I do not have the option of specifying a management IP if I roll this out via marketplace.
I am missing the IP address of the management server here:
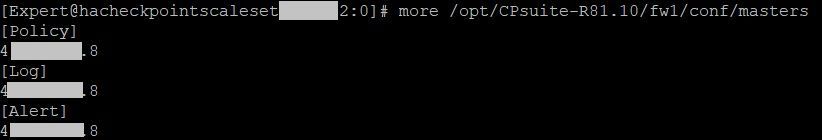
So I had tried implement sk102712 and configure the "$FWDIR/conf/masters" file. That didn't work either.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
the IP Address of the management server in the template is isn't part of the GWs configuration. its just for NSG configuration.
I am guessing you followed sk100583 Scenario 2 to configure the Public IP address of the Management server as the log server ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @Nir_Shamir,
That's exactly what I did and it doesn't work either.
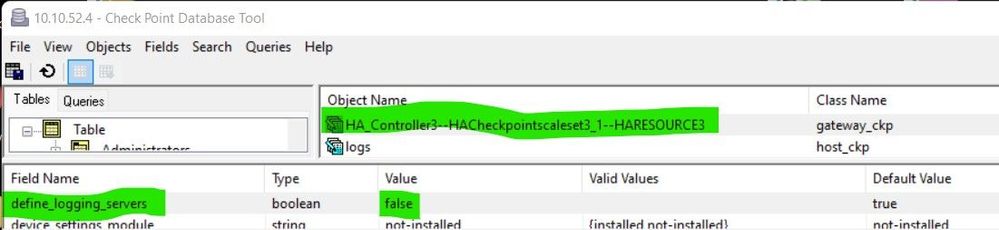
On the VMSS gateway:
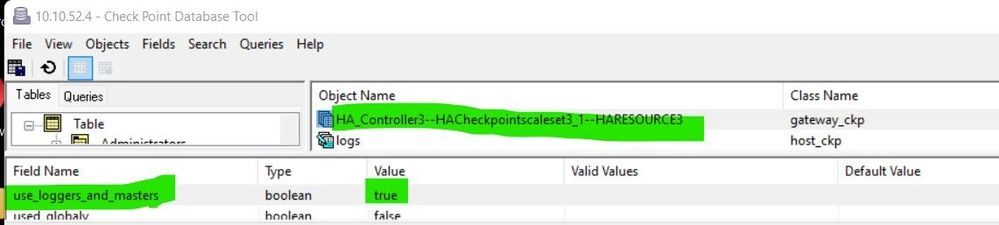
Gguidbedit on SMS :
use_loggers_and_masters = true:
and
define_logging_servers = false:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
and you don't see any tcp port 257 traffic on the GWs ?
have you tried installing DB , rebooting GWs .
of there is no logging traffic then something is off
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @Nir_Shamir
I had done all that and thanks for the tips.
But I have found the issue!
If I create a static NAT rule for the management object, everything works fine.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Of course, the suboptimal thing is that I have to change the masters for each VMSS instance.
Furthermore, I have to change the GuiDBEdit entries for each VMSS instance.
This is a problem with autoscaling!
Is there a better approach here for a on premise management server connection?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
well , basically the NAT configuration on the management server should be enough.
I would change everything back as it was (GUIDBEDIT etc.) and only leave the NAT on the management server.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Both solutions do not work!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You may have to implement the following sk171055.
Then you can roll out the parameter via the routing script when activating the VMSS instance.
# vi $MDS_FWDIR/conf/static_route_config_<CONFIGURATION-TEMPLATE-NAME>.sh
# chmod u+x $MDS_FWDIR/conf/static_route_config_<CONFIGURATION-TEMPLATE-NAME>.sh
# autoprov_cfg set template –tn <CONFIGURATION-TEMPLATE-NAME> –cg $MDS_FWDIR/conf/static_route_config_<CONFIGURATION-TEMPLATE-NAME>.sh
Here is the content of the script. The area marked with the dots is the original routing script.
$MDS_FWDIR/conf/static_route_config_<CONFIGURATION-TEMPLATE-NAME>.sh
------------------------------------------------------------------------
#! /bin/bash
ckp_regedit -a SOFTWARE\\CheckPoint\\FW1 FORCE_NATTED_IP -n 1
.......