- CheckMates
- :
- Products
- :
- CloudMates Products
- :
- Cloud Network Security
- :
- Discussion
- :
- Re: Additional External IP (azure)
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Are you a member of CheckMates?
×- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Additional External IP (azure)
How do i add an additional external IP to the CloudGuard device in Azure. I've added the new IP in the Azure Portal and attached to the VM, but within the GUI the IP isn't being display?
If i create a new alias within the CG GUI, i can't specify the IP as it doesn't allow for /32 within the subnet mask.
Any help would be really appreciated.
Thanks
Tom
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Tom,
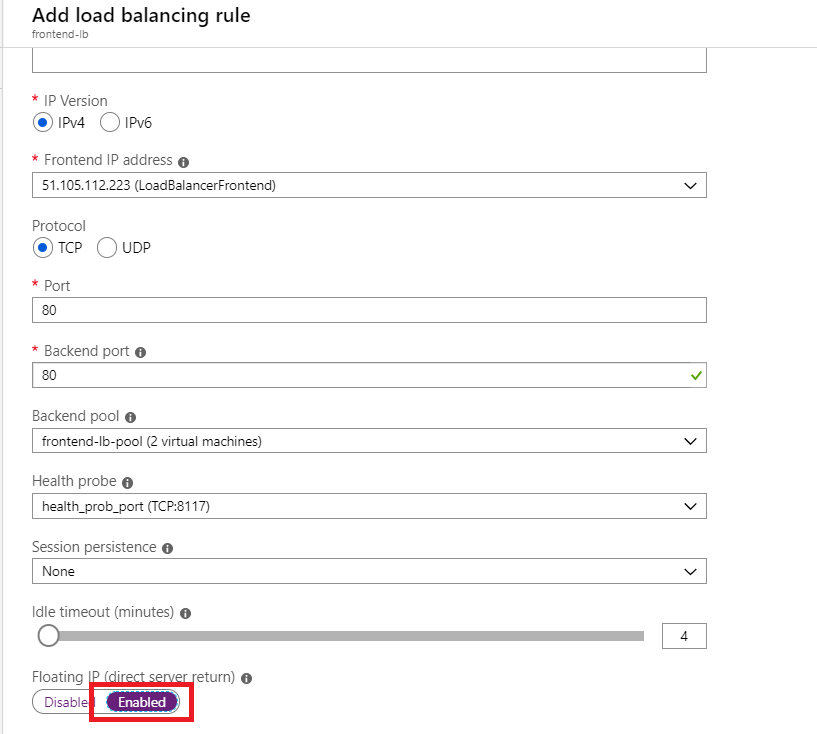
you could use a LB and use Load Balancing Rules (instead of a Inbound NAT Rule). If you enable "Floating IP (direct server return)", which is disabled per default, the LB will not NAT the Destination IP. In this case you will see the Public IP on the Firewall and you can NAT accordingly.
If using a Standard LB, please make sure to have a Network Security Group which has to allow the traffic (this is not necessary if you use a Basic LB which is sufficient and allows the traffic per default).
May be that helps ?
Matthias
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
What are you using the IP address for?
If it's just for, say, Address Translation, the IP doesn't actually need to appear in the OS config at all, there just needs to be a NAT rule for it.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks Dameon,
I just need it for NAT to forward traffic to a web server. Do i need to create an object for the external IP. How do i assign the nat to the new IP?
Thanks
Tom
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Tom,
This video from check point channel may help you >
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks Huseyin,
I've followed this before, but this is setup using the eth0 external IP. I have this working, but i need more than 1 external IP. For instance i may have more than 2 external webservers that all resolved using different DNS.
So i need to a way to send 1 external IP to one web server and the other External IP to another web server. I dont have any kinda of LB so i can't content switch i just need 1 IP to 1 server and 1 to another
Thanks
Tom
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
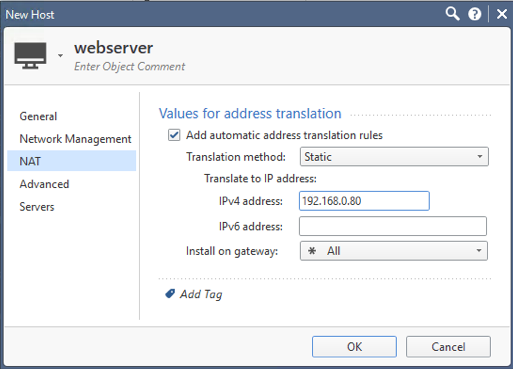
Create host objects for the new public IP address if you haven't already.
In the NAT tab for these objects, specify the internal IP address.
Repeat for each public IP address.
Ensure there is a rule allowing access to these objects for services http/https and install policy.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
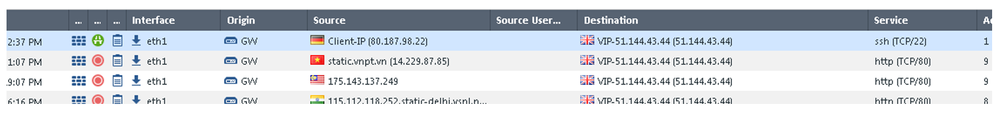
I've done that, but i can't seem to get it to work. Plus i don't see any reference to the external IP/Host Object in the logs so it doesn't look like the IP address is even hitting the CG.
If i do the same with the original ETH0 external IP it works, but just not with the additional IP.
Thanks
Tom
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Have you done a tcpdump on the relevant interface to verify the traffic to that IP address is even reaching the gateway?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@Tom,
If I understand correctly, you have setup a web server and you want to assign a Azure public IP and route the traffic from Internet to that web server
If this the case, you will have to create an
1. Azure public IP address
2. Attach the public IP address to the Azure load balancer in front of the Check Point firewalls
3. Create an Inbound NAT rule in the Azure load balancer
4. Create a NAT rule on the Check Point firewalls which will receive the traffic from Azure load balancer and NAT it back to the original port of the inside web server
This way you will be able to route traffic from Internet to the web server. Let me know if this helps.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks for the reply.
Im getting closer now, i can hit the external IP of the Azure LB and NAT through to the CG, but do i create a rule to send the traffic to the webserver only assigned to that IP.
It's hard to explain, but i have 2 Web Servers (Web1 and Web2) both have a LB in front. I have a rule that says from the internet to web1 and from the internet to web2 both for http. How do i specify that if you come in on External IP 1 you go to Web1 and if you come in on External IP2 you go to web2. at the moment i can only get it to route to the web server in the first rule? I have checked the logs and see that the source traffic is always the CG and not the external IP address?
How do i route based on source the IP's if being NAT'd from the Azure LB into the cloud guard?
Hope that makes sense?
Thanks
Tom
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I dont understand this. I have a rule that says any source to cloudguard for https accept.
I then have a NAT rule that says source address is the Azure LB Public IP > destination CloudGuard > HTTPS > Translated Source Original > Destination is WebServer but it just won't translate it through to the web server....
What am i missing ![]()
Tom
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I just am working on these scenarios with a customer of mine implementing all their web presence into Azure. This is what we have working for multiple web servers.
We had to use an external load balancer to map additional ip addresses into the scenario. Essentially the external load balancer just takes care of the NAT converting https on the external ip addresses to custom ports on the firewall 9443,9444 etc for http on the firewall.
The firewall then has NAT rules (and access rules) allowing traffic into the firewall and NATing the traffic back to http on either the web server directly or an internal load balancer to balance the traffic among multiple web servers.
we currently have 5 https servers each on their own IP address. If you hit the limit for external ip addresses, you can just spin up another external load balancer.
this has the advantage of leaving the external looking like https, and the internal web server also receives https.
however this works for any TCP protocol and now possibly UDP with the improvements to the load balancer.
it did take me a long time to figure out what works and what wouldn’t work, but this was the working scenario that works here.
a lot of the problem here is getting the external ip traffic to the firewall so that NAT can happen. I was never able to route this to the firewall, Microsoft seems to always think that you’re going to put these ip addresses directly on your hosts rather than thru a security gateway.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks Ted, so you route based on incoming port rather than source IP? Or do you route on both?
Its odd cause you’d think you can just route based on incoming IP. To me this is just basic functionality of a firewall rule, also I’m pretty sure it works on the 77.30 version.
There has had to be way to do it other than in port, otherwise the firewall is going to get really messy and hard to manage over time ![]()
thanks
Tom
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Tom,
you could use a LB and use Load Balancing Rules (instead of a Inbound NAT Rule). If you enable "Floating IP (direct server return)", which is disabled per default, the LB will not NAT the Destination IP. In this case you will see the Public IP on the Firewall and you can NAT accordingly.
If using a Standard LB, please make sure to have a Network Security Group which has to allow the traffic (this is not necessary if you use a Basic LB which is sufficient and allows the traffic per default).
May be that helps ?
Matthias
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Matthias,
Thanks for the reply.
This is exactly what I've done and works perfectly.
Cheers
Tom.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Matthias,
Can you share your configuration?
Regarsd
JSalinas
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi JSalinas,
just define a Load balancing rule on the LB:
Important: you have to enable Floating IP. If doing so tells the LB not to NAT the Destination IP.
On the FW you´ll see the Public IP:
If you are using a Standard LB, a NSG which allows this traffic is necessary. This NSG has to be attached to the Subnet in which the (External) Interface of the FW is deployed. (the Interface definded as the Backend Pool on the LB).
Matthias
P.S. the public IPs are no longer part of my environment 😉
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello Mathias,
in your solution- did you have to create a brand new Load Balancer? The reason I ask is because when we deployed Cloudgard, it spins up a front end load balancer and a back end load balancer as part of its deployment requirements. Im wondering if we could leverage those existing LBs or do we have to create new LB's.
Thank you
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello Ping_Choi,
please use the front end load balancer which was deployed by Checkpoint, you don´t need a new load balancer
Matthias
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I have followed the step of floating IP on the Load balancer and it work for the initial frontend IP on the LB. I created a new frontend IP on the loadbalancer to publish another web server and enable floating IP but the floating IP is not appearing on the checkpoint VM part by default. The first frontend IP appears on the checkpoint VM overview page but the new one is not showing.
Any assistance will be appreciated
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Danimax007,
did you add a load balancing rule for the new public IP as well?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Matthias_Haas,
I did,
It later worked after like 20 - 30 minutes maybe the public IP itself was not receiving the traffic after I newly provisioned it but I doubt it. Only the first LB frontend IP is showing on the checkpoint VM page but traffic is also arriving on the second frontend IP to the checkpoint VM. I will monitor it and maybe try out a third frontend IP with floating IP enable and see if there is a delay or it will start working immediately.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Your NAT rule is incorrect.
The original source of your traffic IS NOT the External IP.
Think about it. Your original source is me, the world, the WWW - people accessing it.
The original destination is your external IP - this is what people are accessing to get to your internal server.
Your translated destination is then the internal server.
Do not apply NAT on the Azure Load Balancer - only NAT on the CP Firewall.
Follow the load balancing rules as per above and traffic will be received by the firewall
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi there,
My object: ExternalIP represents the public IP of my LB, is this correct?
You say: Do not apply NAT on the Azure Load Balancer - only NAT on the CP Firewall.
So I just need to create:
A Load Balancer Rules? I don't need to create an Inbound NAT rules on the LB?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
No NAT at all on the load balancer.
If you follow the guide above, traffic will come to the firewall un'NAT'd - so the firewall will see the original source i.e the world.
To clarify - NO NAT on the load balancer. Just the rules.
Then, your original destination on the check point NAT is the public IP you want your users to get to.
So, if you was setting up a webserver for me, and you gave me the IP of 200.200.200.200. The original destination would be 200.200.200.200.
The public IP lives on the load balancer. The load balancer uses its load balancing rules to FORWARD not NAT to the Check Point.
The Check Point recieves the traffic in its original form and NAT's according to policy 🙂
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi there,
First of all a million thanks 🙂
Two questions!!
1-In my CheckPoint do I need to create a Policy rule? Or just a nat rule like you explained to me earlier?
2-Why when I create the BackendPool (in the LB), right away my CheckPoint, in the Azure platform shows me the IP address that I just created in the LB? (screenshot here)
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Here I show all the stages I have done, but it still doesn't work.
LoadBalancer:
1-I created a BackendPool pointing towards my VM FW (Image 1)
2-I created a Helth PRobes (image 2)
3-I created a load Balancing Rules (image3)
FW CheckPoint:
1-I created a Policy Access Rules (image 4)
2-I created a NAT Rule (image 5)
***When I try to access my Web server with the public IP of the LB I get this: Image 6
If someone else could help me find out what is not working, I would appreciate it, thank you 🙂
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
1. you don´t need that double port modification (LB 80-> 9091, FW 9091 -> 80), just keep it on Port 80 (but it should work anyway)
2. do you get any log entry on the Firewall ? If not, which type of LB are you using (Standard or Basic) ? If Standard, make sure you have a NSG attached to the subnet of the backend pool (external interface of the FW) which allows traffic from "any" Source IP (Port 80/9091) to the Public IP
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
-I made the port modification since I will have several web servers that will be accessible through that port (80). Therefore I need to use other ports and then NAT on the FW. Do you think it is well done this way?
-Currently I do not see any log in the firewall that refers to the public IP of the LB. Previously when I had created an Inbound NAT Rule on the LB (JackPrendergast told me it was not the correct solution), instead of a Load Balancing Rule. In the firewall I saw the public IP of the LB.
-I'm using Basic LB. Therefore I don't think there is anything else that I should configure in Azure, only the LB
Any other ideas please?
!!!!!!!!Just as a detail, I followed the stages of a course in UDEMY where they explain how to create the LB in azure and then the necessary rules in the FW. In the course they use the option: Inbound NAT rule and everything works correctly. I tried that way following exactly the same steps and it didn't work