- Products
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
Check Point
for Beginners
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Educational Resources
- :
- Check Point for Beginners
- :
- How To Deploy 1550 SMB Appliance Using Zero Touch ...
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
OPEN OTHER ARTICLES
 SMP 1500 appliance VPN setup with an Externally Managed Gateway
SMP 1500 appliance VPN setup with an Externally Managed Gateway
 Jump Start: SMB Appliance Network Security - free online course
Jump Start: SMB Appliance Network Security - free online course
 Check Point 1500 Appliances - Reviewer Guide
Check Point 1500 Appliances - Reviewer Guide
 Check Point Security Management Portal - Reviewer Guide
Check Point Security Management Portal - Reviewer Guide
 Video - Learn Zero Touch Deployment with Quantum Spark In 10 Minutes
Video - Learn Zero Touch Deployment with Quantum Spark In 10 Minutes
 Video - Getting Started with Quantum Spark 1800 Series; Unboxing + 1st Time Wizard
Video - Getting Started with Quantum Spark 1800 Series; Unboxing + 1st Time Wizard
 Video - Firmware Upgrade on Quantum Spark In Less Than 3 Minutes
Video - Firmware Upgrade on Quantum Spark In Less Than 3 Minutes
 Video - Check Point Quantum Spark 1590: Unboxing, Initial Configuration and Watch Tower App
Video - Check Point Quantum Spark 1590: Unboxing, Initial Configuration and Watch Tower App
 Video - Setting up a Check Point 1590 Quantum Spark SMB Firewall
Video - Setting up a Check Point 1590 Quantum Spark SMB Firewall
 Video - How to use Check Point Zero Touch with Quantum Spark SMB appliance
Video - How to use Check Point Zero Touch with Quantum Spark SMB appliance
 Video - Check Point Remote Access VPN Setup and Configuration for Quantum Spark 1590 SMB Firewall
Video - Check Point Remote Access VPN Setup and Configuration for Quantum Spark 1590 SMB Firewall
 Video - Check Point Quantum Spark 1590 Site to Site VPN with Ubiquiti UDM Pro
Video - Check Point Quantum Spark 1590 Site to Site VPN with Ubiquiti UDM Pro
 Video - First look at the Check Point Quantum Spark 1600 Firewall
Video - First look at the Check Point Quantum Spark 1600 Firewall
 Video - Unboxing of Check Point Quantum Spark 1800 Firewall
Video - Unboxing of Check Point Quantum Spark 1800 Firewall
 Video - Block internet access to a client on Quantum Spark 1590 SMB Firewall + URL Filtering
Video - Block internet access to a client on Quantum Spark 1590 SMB Firewall + URL Filtering
 Video - Firmware Upgrade on Check Point Quantum Spark 1590 SMB appliance in less than 3 Minutes
Video - Firmware Upgrade on Check Point Quantum Spark 1590 SMB appliance in less than 3 Minutes
 Video - Configuring high availability on Check Point Quantum Spark Next-Gen Firewalls
Video - Configuring high availability on Check Point Quantum Spark Next-Gen Firewalls
 Check Point Jump Start: Quantum Spark
Check Point Jump Start: Quantum Spark
 SMB Security
SMB Security
How To Deploy 1550 SMB Appliance Using Zero Touch Cloud Service
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
2020-07-07
03:34 AM
Author: Chris Biernacki
Introduction
The next family of our Small and Medium Business appliances are based on R80 code.
Check Point's R80.20 release for Small and Medium Business Appliances are supported only on the new 1500 Series Security Gateways. For more information about the 1500 Series, refer to sk157412: 1500 Series Security Gateways.
Introduction to Zero Touch Cloud Service
The Zero Touch cloud service is mainly deployed in Small and Medium Business (SMB) environments.
Check Point's Small and Medium Business Appliances are high performance, integrated devices offering Firewall, VPN, Anti-Virus, Application Control, URL Filtering, Email Security, and SandBlast Zero-Day Protection, all in compact form factors that are simple to configure and manage.
The 1500 Security Gateways deliver enterprise-grade security in a series of simple and affordable, all-in-one security solutions to protect small and medium business employees, networks, and data from cyber theft.
1500 Security Gateways offer integrated, multi-layered security in a compact desktop form factor. Setup can be done in minutes using pre-defined security policies and our step-by-step configuration wizard.
1500 Security Gateways are conveniently manageable locally via a Web interface, centrally by the Check Point Security Management Portal (vSMP), or centrally by Check Point's central management systems: SmartConsole, MDM, LSM (Future), Maas (Future) and can be deployed using Zero Touch cloud service as initial deployment.
When booted for the first time (or after a factory default reset), every SMB gateway tries to fetch settings from the Zero Touch server.
The gateway uses the WAN connection to access the Internet, so make sure that you plug in the Ethernet cable to the WAN socket and that the Internet is accessible.
The settings from the Zero Touch server substitute the First Time Configuration Wizard of the gateway. After the gateway downloads and successfully applies the settings, it does not contact the Zero Touch server again.
If the gateway is reset to factory defaults, it initiates the process again and fetches settings from the Zero Touch server. If you want to configure the gateway after the settings were downloaded successfully, you must log into the gateways webui.
Deployment Steps
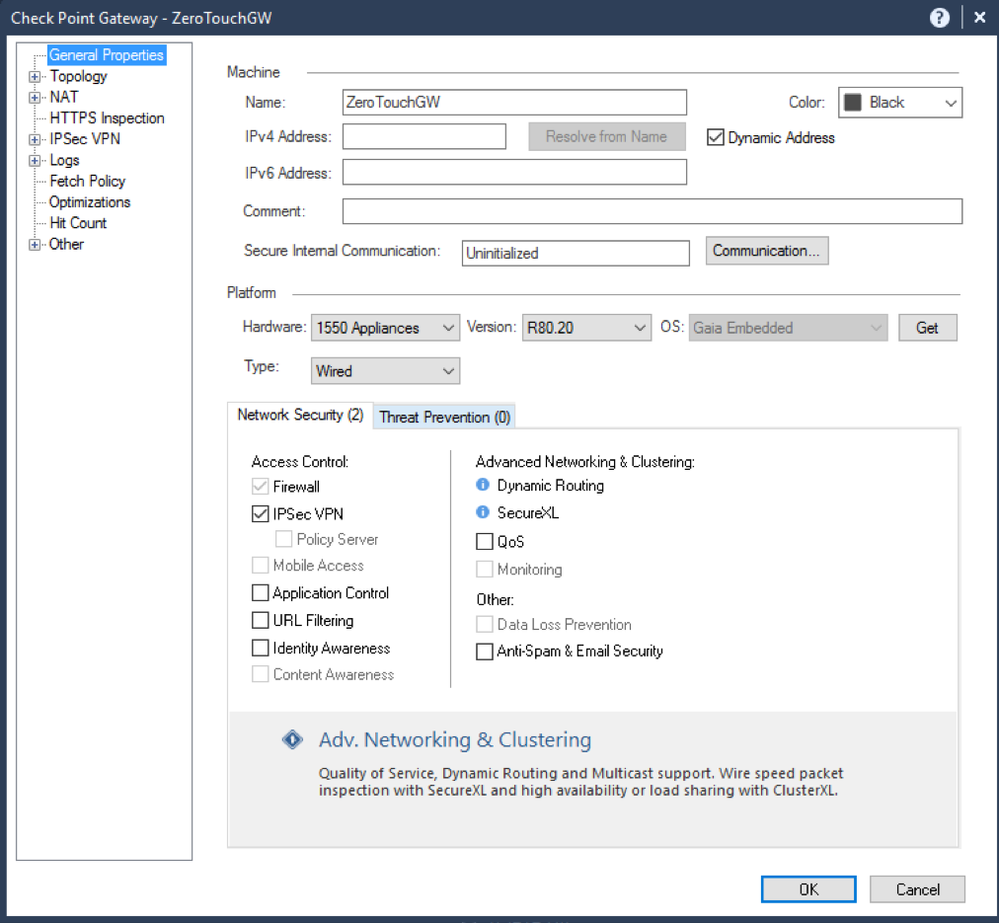
1. Create a Gateway object in Smart Console, and configure the hostname (do not use underscore), IP address (in most cases, it will be a dynamically assigned IP address, in this case the Dynamic Address box will be checked, otherwise, the specific IPv4 address will be specified), hardware and OS version (make sure the version is R80.20 Gaia Embedded)
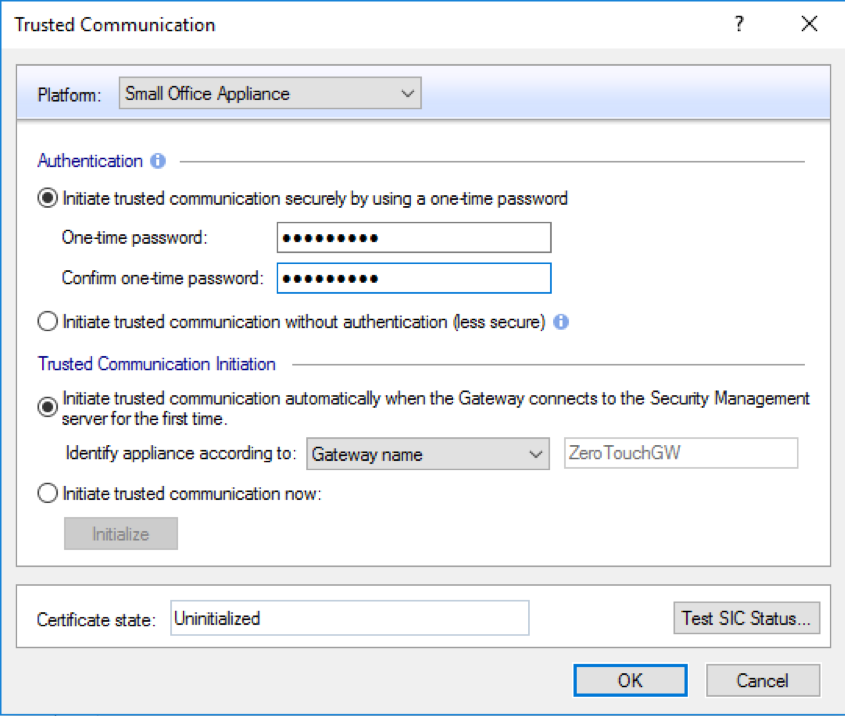
2. Prepare the SIC password so that the gateway can connect to the manager for the first time. Click on Communication option. Enter the SIC password and check the option to Initiate trusted communication automatically when the Gateway connects to the Security Management Server for the first time, as shown in the following image.
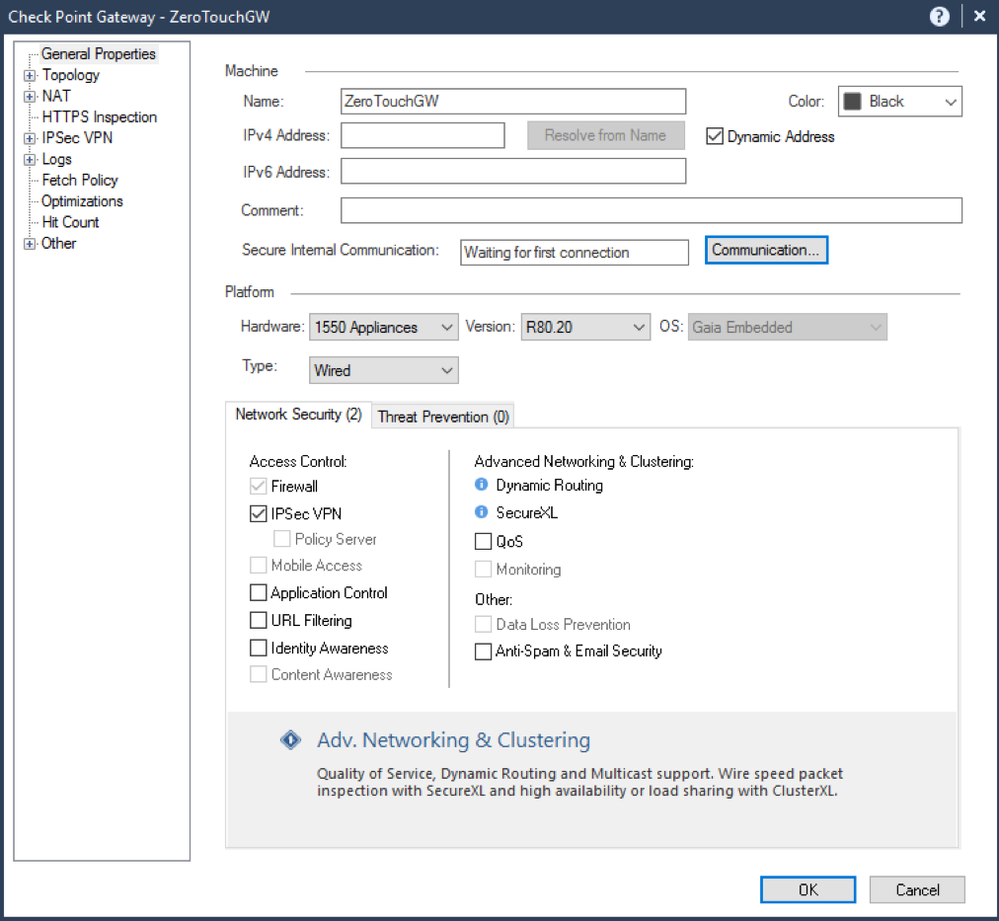
3. Once completed, the status of the SIC in the Gateway object will be as follows: Waiting for first connection:
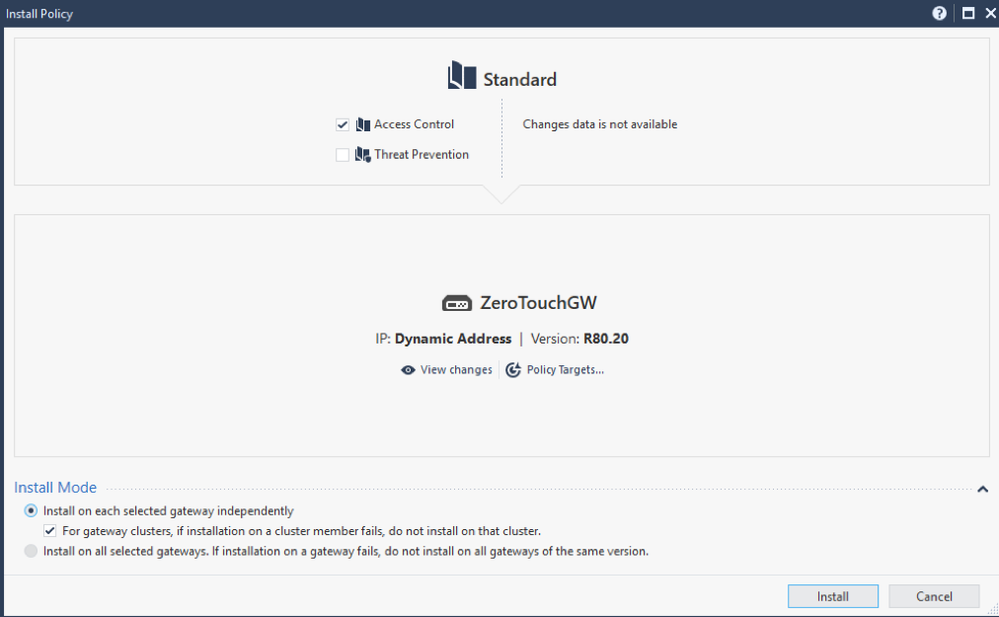
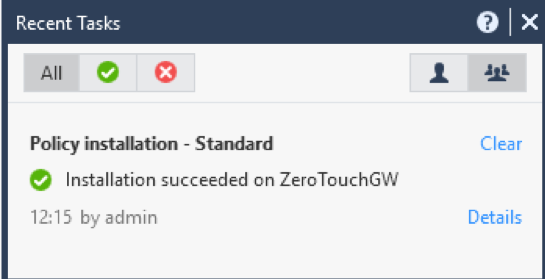
4. Publish changes and Install policy on the new 1550 appliance. This action does not actually install policy, but leaves it ready for when requested by the 1550 appliance. The 1550 appliance can also be configured as the ‘Installation target’ of the Policy Package.
5. Once complete, then you may continue to the Zero Touch portal.
Zero Touch Cloud login page:
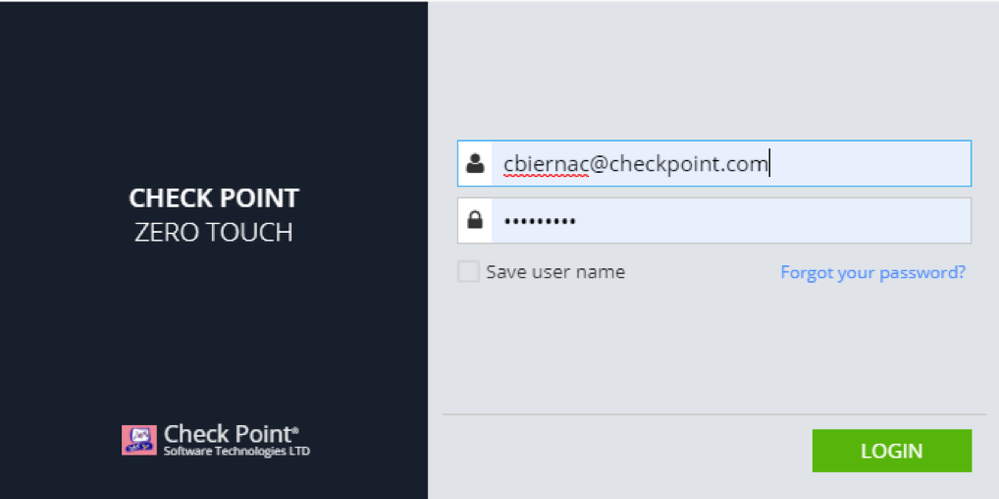
https://zerotouch.checkpoint.com/ZeroTouch/login.jsp#app.Templates
*** Please enter your Usercenter.checkpoint.com credentials as anyone with an active User Center Account has access to Zero Touch portal. ***
Zero Touch Templates
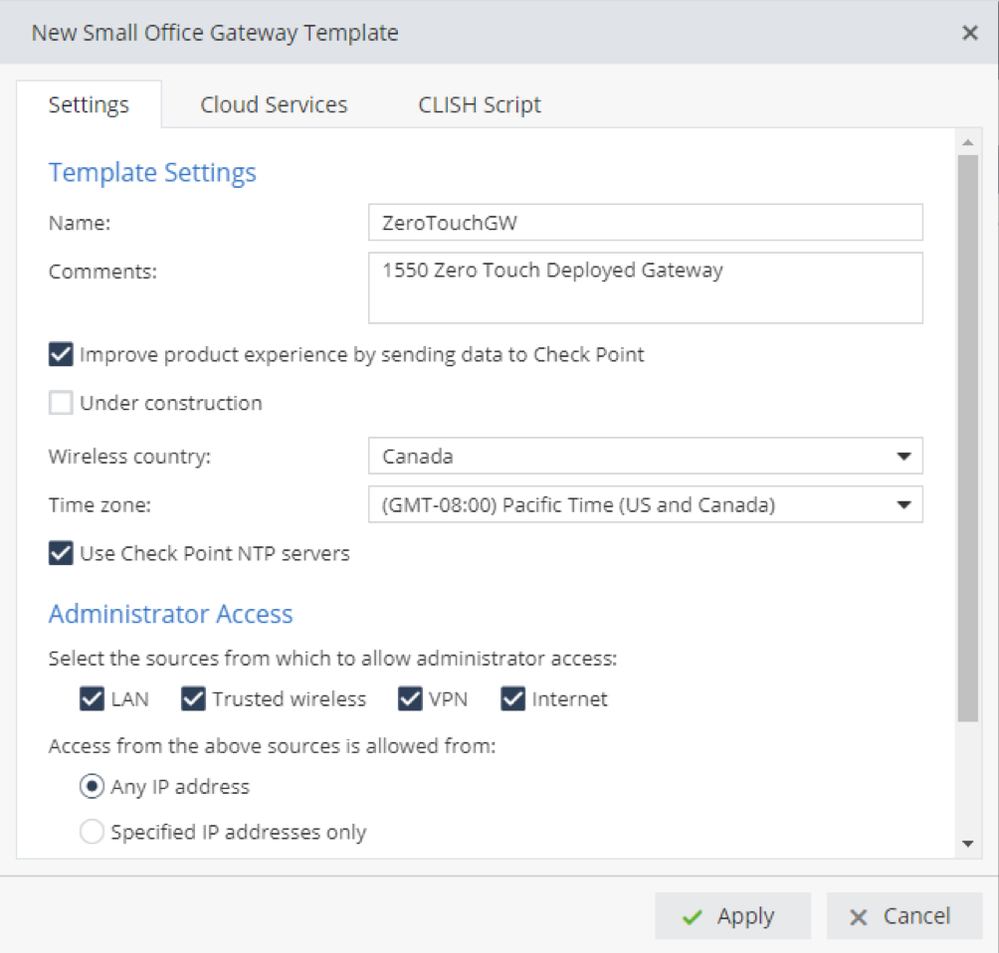
The next step is creating a Zero Touch Template, which are forms for Small Office and Gaia Gateways to add settings to the gateways' profiles on Zero Touch during gateway claim operations. The forms' settings load information for gateways into Zero Touch during the Gateways’ claim process.
There are two methods to create templates:
- You can create a template with the common parameters that apply to all devices (for example NTP servers, DNS servers, etc.)
- You can also modify the 'CLI script' for each deployment and upload the complete configuration to the SMB.
To configure a gateway in centrally managed mode and connect it to the Security Management Server, enter these CLI commands in the CLI script field (example):
set security-management mode centrally-managed
set sic_init password xxxx
set security-management mgmt-addr xx.xx.xx.xx use-one-time-password true localoverride-
mgmt-addr true send-logs-to by-policy
fetch policy mgmt-ipv4-address xx.xx.xx.xx
Notes:
- The hostname must be the same as the one created for the SMB object in SmartConsole. SIC will only be established successfully to that specific hostname.
- The Security Management Server must be accessible from the Internet through a Static NAT.
- The Security Management Servers IP is the public IP.
- As part of the CLI script, the 1550 appliance connects to the Security Management Server’s public IP, establishes SIC, and downloads the policy.
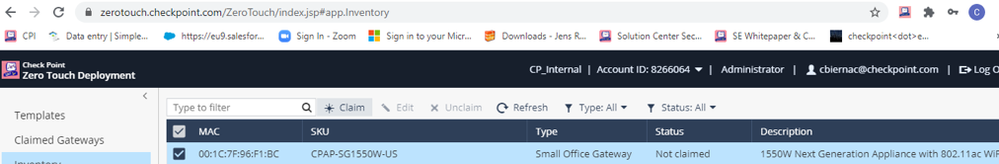
Next, you will need to claim the Gateway, by going to the Inventory Section:
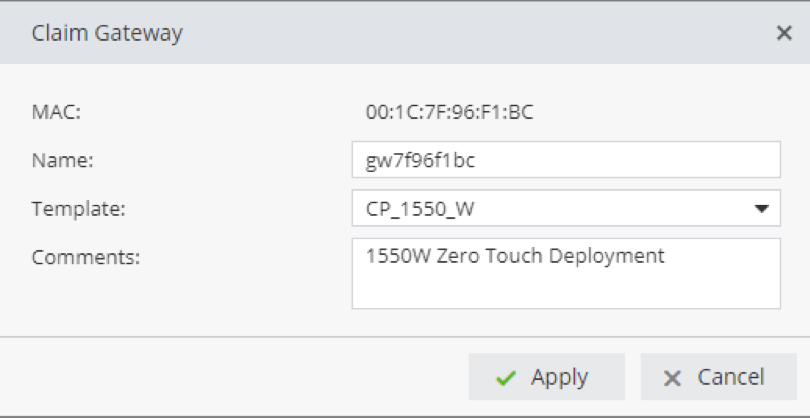
In the Inventory table, find the 1550 Appliance by its MAC and select Claim.
Configure the hostname accordingly (Strongly advise you to use the same name you used to create the object on the Management Server), then select the template that you would like applied to it.
Please note that the hostname of the 1550 Appliance must not contain the symbol ‘_’, because the Zero Touch process will fail and not able to make the claim.
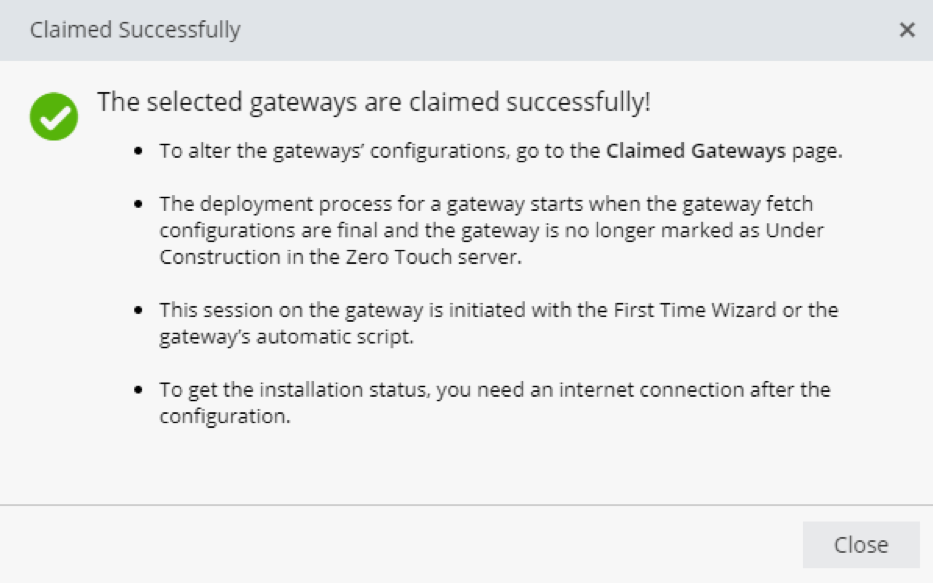
The 1550 Appliance will now appear in the 'Claimed Gateways' table. By accessing its properties, you can override any configuration inherited from the template. This allows you for example, to adjust the IP configurations of the interfaces.
Once you have made the ‘Claim’, connect the WAN interface of the 1550 Appliance to a network that is configured via DHCP and has Internet access.
If the 1550 Appliance was previously deployed, restore it to default factory settings before you continue.
During the initial boot, the 1550 Appliance automatically executes the Zero Touch script. In case it fails to connect to the Internet, the script runs every 5 minutes until you can download the Zero Touch configuration or do the First Time Wizard manually.
When the Zero Touch process finishes, confirm on the 1550 Appliance that the correct policy was installed via ssh by issuing the following command (‘fw stat’).
In Smart Console, select the 1550 Appliance and you will see that the status of the SIC is now ‘Trust Established’.
Labels
Author: Chris Biernacki
Introduction
The next family of our Small and Medium Business appliances are based on R80 code.
Check Point's R80.20 release for Small and Medium Business Appliances are supported only on the new 1500 Series Security Gateways. For more information about the 1500 Series, refer to sk157412: 1500 Series Security Gateways.
Introduction to Zero Touch Cloud Service
The Zero Touch cloud service is mainly deployed in Small and Medium Business (SMB) environments.
Check Point's Small and Medium Business Appliances are high performance, integrated devices offering Firewall, VPN, Anti-Virus, Application Control, URL Filtering, Email Security, and SandBlast Zero-Day Protection, all in compact form factors that are simple to configure and manage.
The 1500 Security Gateways deliver enterprise-grade security in a series of simple and affordable, all-in-one security solutions to protect small and medium business employees, networks, and data from cybe
...
4 Comments
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
About CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter