- Products
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
Check Point
for Beginners
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Educational Resources
- :
- Check Point for Beginners
- :
- Check Point 1500 Appliances - Reviewer Guide
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
OPEN OTHER ARTICLES
 How To Deploy 1550 SMB Appliance Using Zero Touch Cloud Service
How To Deploy 1550 SMB Appliance Using Zero Touch Cloud Service
 SMP 1500 appliance VPN setup with an Externally Managed Gateway
SMP 1500 appliance VPN setup with an Externally Managed Gateway
 Jump Start: SMB Appliance Network Security - free online course
Jump Start: SMB Appliance Network Security - free online course
 Check Point Security Management Portal - Reviewer Guide
Check Point Security Management Portal - Reviewer Guide
 Video - Learn Zero Touch Deployment with Quantum Spark In 10 Minutes
Video - Learn Zero Touch Deployment with Quantum Spark In 10 Minutes
 Video - Getting Started with Quantum Spark 1800 Series; Unboxing + 1st Time Wizard
Video - Getting Started with Quantum Spark 1800 Series; Unboxing + 1st Time Wizard
 Video - Firmware Upgrade on Quantum Spark In Less Than 3 Minutes
Video - Firmware Upgrade on Quantum Spark In Less Than 3 Minutes
 Video - Check Point Quantum Spark 1590: Unboxing, Initial Configuration and Watch Tower App
Video - Check Point Quantum Spark 1590: Unboxing, Initial Configuration and Watch Tower App
 Video - Setting up a Check Point 1590 Quantum Spark SMB Firewall
Video - Setting up a Check Point 1590 Quantum Spark SMB Firewall
 Video - How to use Check Point Zero Touch with Quantum Spark SMB appliance
Video - How to use Check Point Zero Touch with Quantum Spark SMB appliance
 Video - Check Point Remote Access VPN Setup and Configuration for Quantum Spark 1590 SMB Firewall
Video - Check Point Remote Access VPN Setup and Configuration for Quantum Spark 1590 SMB Firewall
 Video - Check Point Quantum Spark 1590 Site to Site VPN with Ubiquiti UDM Pro
Video - Check Point Quantum Spark 1590 Site to Site VPN with Ubiquiti UDM Pro
 Video - First look at the Check Point Quantum Spark 1600 Firewall
Video - First look at the Check Point Quantum Spark 1600 Firewall
 Video - Unboxing of Check Point Quantum Spark 1800 Firewall
Video - Unboxing of Check Point Quantum Spark 1800 Firewall
 Video - Block internet access to a client on Quantum Spark 1590 SMB Firewall + URL Filtering
Video - Block internet access to a client on Quantum Spark 1590 SMB Firewall + URL Filtering
 Video - Firmware Upgrade on Check Point Quantum Spark 1590 SMB appliance in less than 3 Minutes
Video - Firmware Upgrade on Check Point Quantum Spark 1590 SMB appliance in less than 3 Minutes
 Video - Configuring high availability on Check Point Quantum Spark Next-Gen Firewalls
Video - Configuring high availability on Check Point Quantum Spark Next-Gen Firewalls
 Check Point Jump Start: Quantum Spark
Check Point Jump Start: Quantum Spark
 SMB Security
SMB Security
PREVIOUS ARTICLE
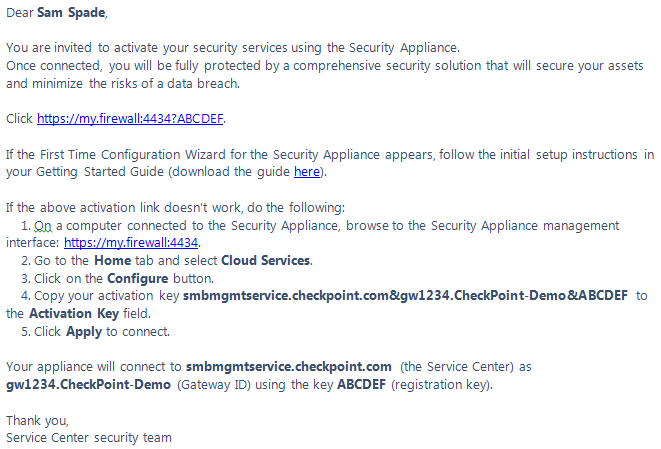
Complete the First Time Configuration Wizard as shown in the Quick Start Guide
TO READ THE FULL POST
it's simple and free
NEXT ARTICLE
Check Point 1500 Appliances - Reviewer Guide
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
2021-08-11
05:21 AM
About this guide
The 1500 Appliance includes the same enterprise-grade Software Blade security that is deployed on Check Point security appliances. Unique to the 1500 Appliance is the simplified web-based management and pre-defined security policies providing out-of-the-box security. This guide describes the Check Point 1500 Appliance management, focusing on the Next Generation security policy pre-defined on the 1500 Appliance. The policies are explained, followed by a general explanation of how to modify the default policies.
Authors and contributors
This document is
- created by Antoinette Hodes a.k.a. @AntoinetteHodes
- edited by @Aviv_Abramovich
- adapted for CP4B by @_Val_
Documentation
The 1500 Appliance includes a Quick Start Guide and Getting Started Guide. Context sensitive on-line help is available in the Web User Interface.
The platform
Check Point 1500 Appliances
Check Point 1500 Appliances leverage enterprise-grade protection for small to medium businesses starting at $600.
- Enterprise-Strength Security – Secure with 100% block rate, recommended by NSS for prevention, powered by R80. These boxes offer 2x more performance up to 4 Gbps firewall and 660 Mbps of full Threat Prevention.
- Simple, Intuitive Management for Small Businesses – Setup security within minutes with the First-Time Wizard and predefined security policies. Or with Out-of-the-box Zero Touch Provisioning, mobile app for security on the go and a unified management portal.
- Wired, Wi-Fi and Wi-Fi with Embedded 3G/4G/LTE - Offer wireless access to guests. Connect to the Internet with Ethernet or 3G/4G/LTE wireless. LTE is an essential component of any enterprise wireless WAN, either as a primary or failover link connecting fixed remote sites or a mobile fleet of vehicles. The 1500 embedded 3/4G/LTE modem supports: CAT6, Dual SIM: nano and micro, LTE antennas: 1x main, 1x diversity and Global coverage
- Great Value – Available in one bundle including Next-Generation Threat Prevention.
These Software Blades are included in the Check Point 1500 Appliance:
- Firewall - World’s most proven firewall solution that can examine hundreds of applications, protocols and services out-of-the box. The firewall also performs Network Address Translation and intelligent VoIP security.
- IPsec VPN - Sophisticated (but simple to manage) Site-to-Site VPN and flexible Remote Access working seamlessly with a variety of VPN agents.
- Application Control - Signature-based granular control of thousands of Internet applications and Web 2.0 widgets. Check Point has over 6,000 applications already defined, the most signatures in the industry.
- IoT Device Recognition – Find all connected devices in your network.
- URL Filtering - Best of breed URL filtering engine, based on a central database, located in the Check Point data center. This ensures excellent coverage of URLs, while maintaining minimal footprints on devices. The Check Point 1500 Appliance provides cut-through performance, as URL categorization queries are done asynchronously.
- Identity Awareness - Gives user and machine visibility across network blades. Enables the creation of identity-based access policies for application and resource control.
- IPS (More than 2000 protections) - Best in class integrated IPS with leading performance and unlimited scaling. IPS protections are updated with IPS updates.
- Anti-spam & Email Security (based on IP Reputation and content) - Comprehensive and multidimensional protection for organizations’ email infrastructure. This includes updates.
- Anti-Virus engine runs in stream (network) mode, supporting high performance and concurrency.
- Anti-Bot - Detects bot-infected machines, prevents bot damages by blocking bot cyber-criminal’s Command and Control center communications, and is continually updated from ThreatCloud
- Advanced Networking and Clustering – A dynamic routing suite and ClusterXL high availability.
- QoS - Quality of Service optimizes network performance by prioritizing business-critical traffic.
- SandBlast Threat Emulation (sandboxing)
More information is available at www.checkpoint.com/products/1500-security-appliances.
Configuring the appliance
1500 Appliances are running the Check Point GAiA secure operating system. This diagram shows the default IP address of the appliance.
Complete the steps in the Quick Start Guide (summarized below)
- Connect power. The Information LED marked with the
character on the front of the appliance turns steady blue when the appliance is ready.
- Connect the 1500 Appliance to the Internet.
- Connect your PC to the LAN1 port at IP address 192.168.1.1 for initial setup. On your PC enable DHCP or set a static IP address in the 192.168.1.0/24 network other than 192.168.1.1.
- Configure your 1500 Appliance using a browser.
Complete the First Time Configuration Wizard as shown in the Quick Start Guide
(summarized below)
- Open a web browser and connect to http://192.168.1.1 or http://my.firewall. The appliance will automatically redirect to a secure https://192.168.1.1:4434 connection to the appliance.
- Login with username “admin” and password “admin” (both without single quotes). Change your login credentials immediately after your first login.
- Accept the browser security warnings and log in to the appliance.
- The Web UI shows the First Time Configuration Wizard. Click Next.
- Change the default password and set the country. The latter matches the wireless country code. Click Next.
- Confirm the date and time. Click Next.
- Optionally set the appliance host name and the domain name. Click Next.
- Configure the Internet connection. Click Next.
- Optionally configure the Local Network. By default the 6 LAN ports are configured as a switch. Click Next.
- Optionally configure the Wireless Network. The default the authentication method is WPA/WPA2 PSK. Click Next.
- Optionally configure Administrative Access to limit which IP Addresses and ports are allowed access. Click Next.
- The appliance connects to the Internet to activate the license. Configure the Software Blades or security features as desired. Click Next.
- Click Finish and the product configuration is complete.
Local Security Management
After you completed the First Time Configuration Wizard the default security policy is automatically enforced. Via the Web UI you can fine tune the security policy.
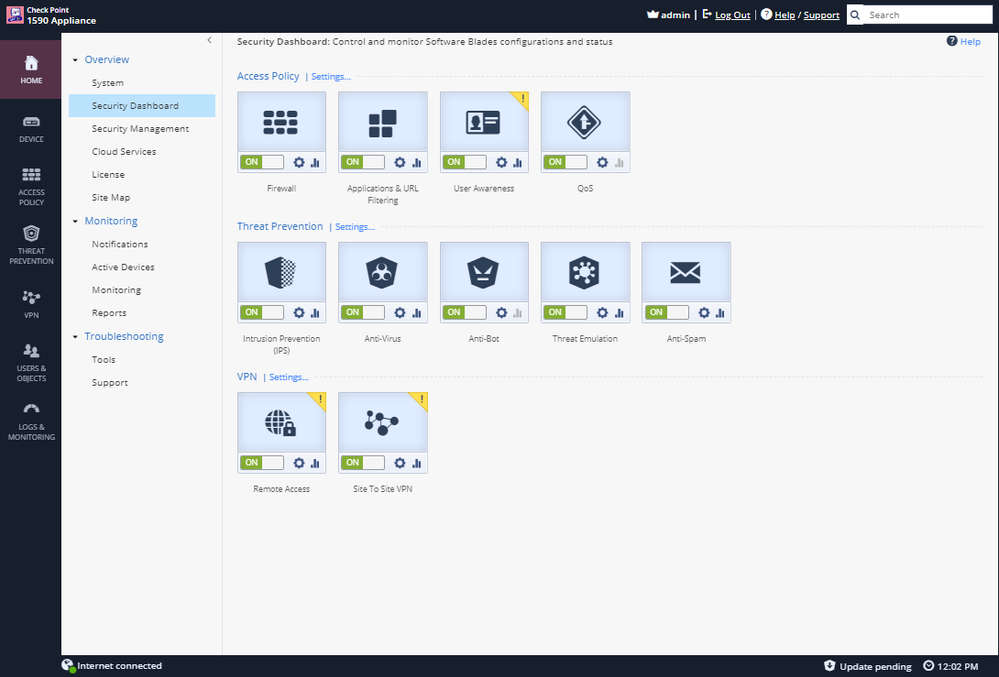
1500 Appliance Security Dashboard
Web User Interface (WebUI)
The WebUI is a simplified, intuitive web-based interface for configuring the 1500 Appliance. Virtually all system configuration tasks can be done through this Web-based interface.
- Easy Access - Simply browse to https://<Device IP Address>:4434.
- Browser Support - Internet Explorer, Firefox, Chrome, Edge and Safari.
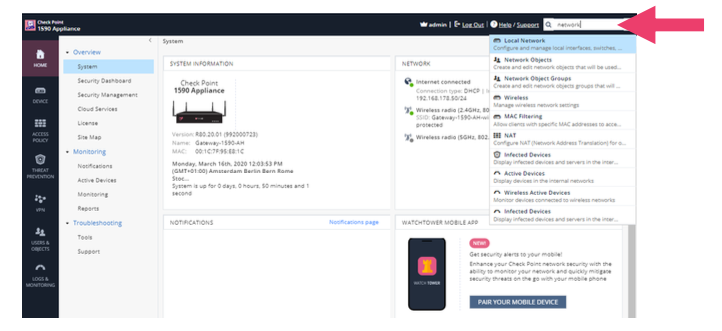
- Powerful Search Engine - makes it easy to find the configuration. For instance type in Firewall in the search bar and click on the top result to go to the Firewall Policy page.
- Simple Powerful Monitoring and Diagnostics - Contains high level graphs of each security function. Monitor system CPU, memory and disk usage. Google-like search through security and system logs. View Active devices and VPN tunnels. Easily capture a diagnostics file or packet captures.
Navigating the Web User Interface
- To become familiar with the Web UI follow this quick walk through.
- The search bar takes you quickly to a configuration page. For example type these words into the search field; firewall, log, user, network and application. Notice the pages available and select needed one by clicking it.
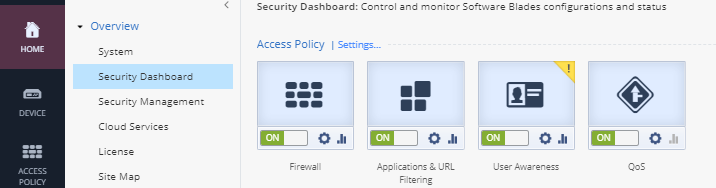
- Type Dash in the search field and press enter. The Security Dashboard is displayed. From this page you can see which security features are enabled, status messages, jump to a configuration window and view the overall activity status.
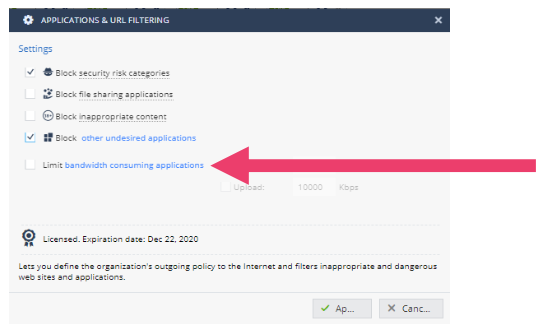
- To disable a security feature drag the slider bar from ON to OFF. Locate Applications & URL Filtering and drag the slider from ON to OFF and then back to ON again.
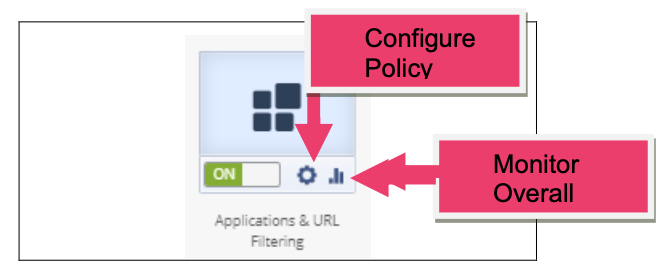
- In the Security Dashboard it is also easy to modify the security policy and view an overall status. Locate the Gear and Graph icons. Click on the Gear icon in Applications & URL Filtering.
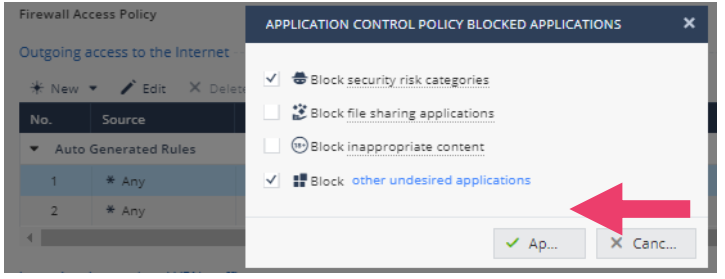
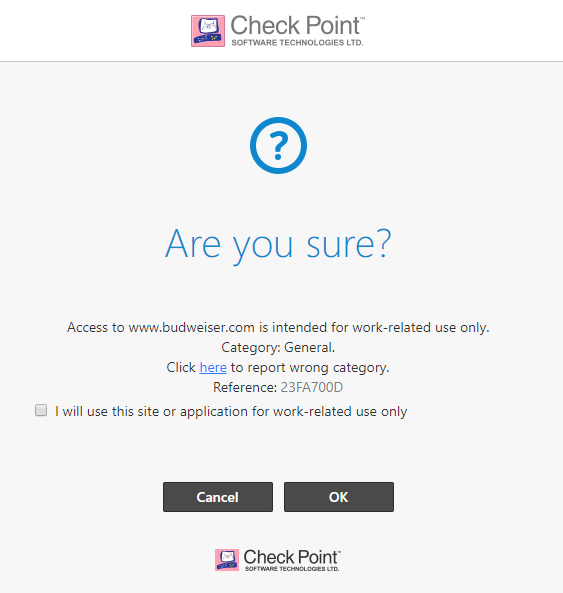
- Notice that the default Applications & URL Filtering policy Blocks the security risk categories. Click on security risk categories, inappropriate content and torrents and P2P applications to review each. Notice that these three are all predefined and not editable. Finally enable Block other undesired applications by checking the checkbox. Select Alcohol to block access to Alcohol related sites. Press Apply. Press Apply again and the security policy is changed. To test the configuration, try browsing from an internal host to www.budweiser.com.
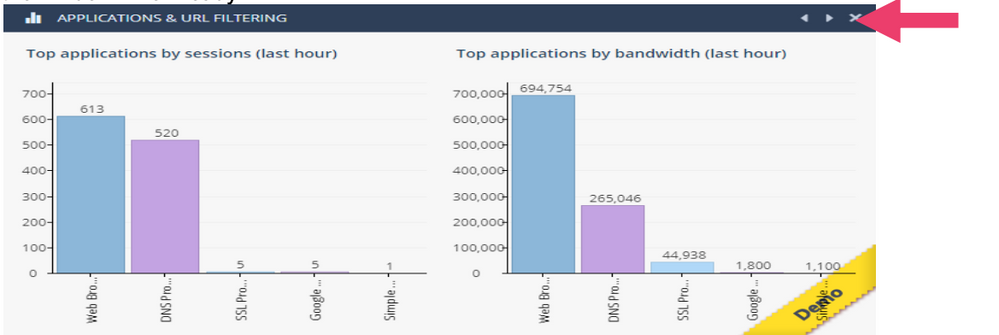
- In the Security Dashboard locate the Graph icon in Applications & URL Filtering. Click on it to see the overall activity. Click on the Arrow pointing to the left to see the Firewall Blade Activity. Or click view demo. Press X to close the window when ready.
- In the bottom of the Web UI is a Status Bar. Hover over the Internet to see the status of the Internet Connection. Hover over Status to see if the Service Blades are up to date with the latest updates.
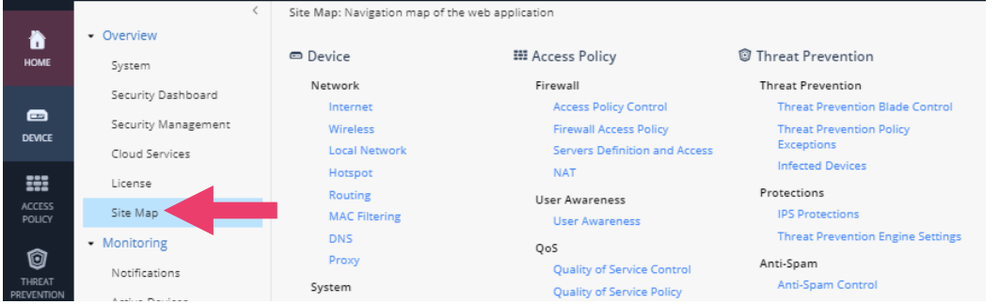
- Before leaving the Home tab, click on Site Map. Notice that there are 6 categories which correlate with the remaining 6 tabs; Device, Access Policy, Threat Prevention, VPN, Users and Objects and Monitoring. In each category are the pages available to the user. This is another way to navigate to the page you want.
- In the Home -> Site Map page click on Blade Control under Access Policy. Or if you like click on the Access Policy tab.
Modifying Access Control Policy
The 1500 Appliance is a Next Generation Firewall. In the Access Policy tab you will find stateful firewall settings including QoS and Network Address Translation, NAT. By default NAT is enabled and the Internal Networks are hidden behind the gateway’s external IP address. The default firewall policy is the Standard one:
- Allow traffic to the Internet on all services
- Allow traffic between internal networks an trusted wireless networks
- Block incoming traffic
For users who want complete policy control, there is a Strict Policy option. The Access Policy is configured through the firewall rule base.
Other components of a Next-Gen firewall like User Awareness and Application Control are configured in the Access Policy tab as well. We have seen the default Application and URL Filtering policy. URL Filtering is combined with Application Control to simplify policy management.
Two types of User Awareness are available; an Active Directory integration and a Captive Portal. The default Captive Portal setting is to capture Internet bound traffic.
The combined Next-Gen firewall policy is visible in Access Policy -> Blade Control -> Firewall Policy.
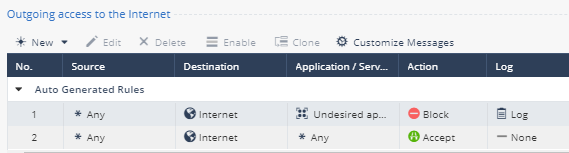
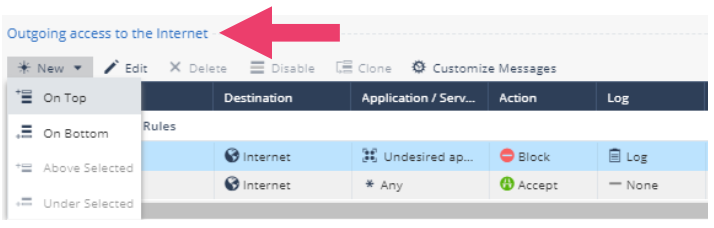
- In the search field enter firewall and select Firewall Access Policy. Notice that the policy is predefined and separated into two sets of security rules; Outgoing Access to the Internet and Incoming, Internal and VPN traffic.
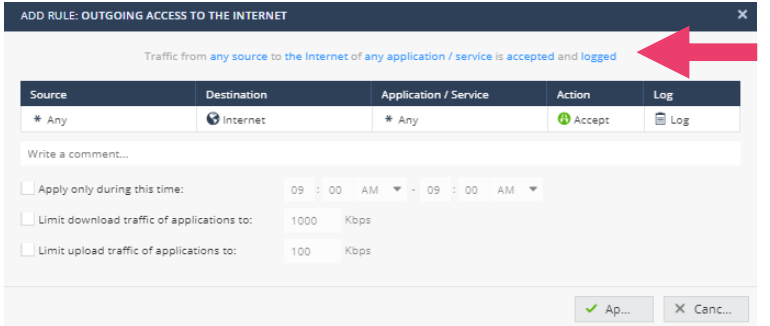
- Double click on the second outgoing security rule. Notice that the only field that can be edited is Logging. Also notice that the rule accepts all outbound connections.
- Click Cancel to return to the policy. When a packet is inspected, the inspection is done from the top down starting with the first rule in the policy. The first match is applied. Notice that the Action of the first rule is Block.
- Double click on the first rule to edit it. Notice that this rule blocks Undesired Applications and that the Action Block is not editable.
- Click on Undesired Applications. Notice that Block other undesired applications is enabled from the first part of the exercise. If you like, click on other undesired applications and you should see that the category Alcohol is still checked. Click Cancel to get back to the base policy.
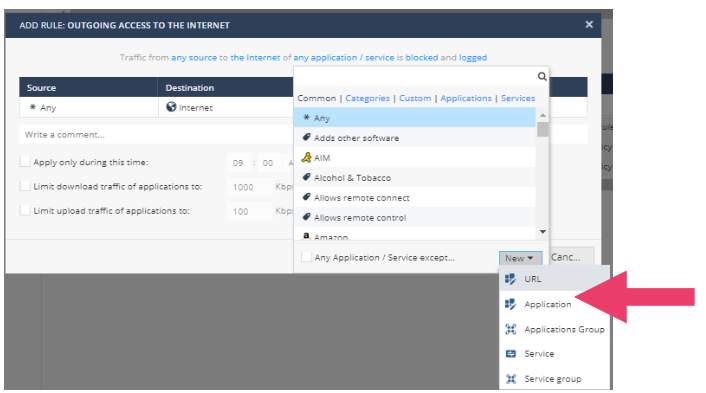
- Let’s modify the outgoing policy. What if we want to allow connections to the www.budweiser.com site, but block connections to other Alcohol related sites? Since inspection is done top-down, we can create a rule that allows this connection at the top of the policy. Click New and select On Top.
- Notice that all of the fields can be edited. Click on any applications -> New and select URL.
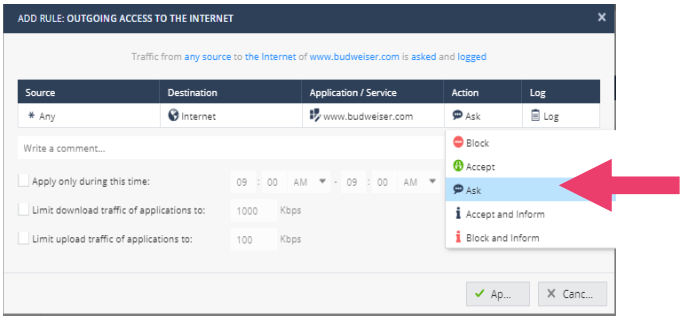
- Enter the URL www.budweiser.com. Click Apply.
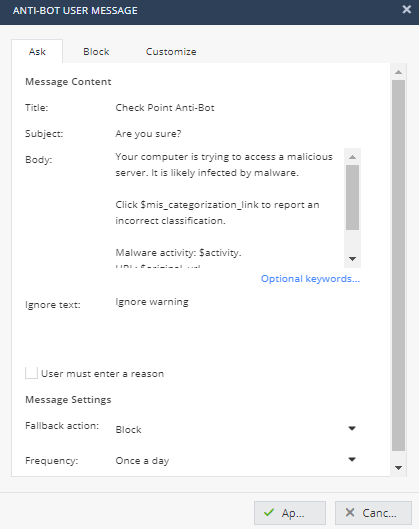
- Notice that the default Action is Block. Click on blocked and select Ask. Click Apply.
- Test the policy by browsing again to www.budweiser.com. This time instead of a Block page you should see the Ask page. Note: The default is doing categorization in the background, which means the first time a site is accessed it may not be blocked, but will be blocked on subsequent page visits. This default behavior can be changed.
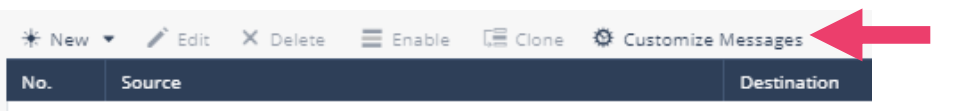
- These messages are customizable. Click on Customize Messages and view the messages that users receive for the actions; Ask, Accept and Inform and Block and Inform.
Modifying Threat Prevention Policy
In addition to Next-Generation Firewall access control the 1500 Appliance protects against the latest threats with IPS, Antivirus, Anti Bot and Anti-Spam technologies.
Update frequency
- Anti-Bot new packages are released twice a week Monday and Wednesday or Tuesday and Thursday
- Application updates are released once a week on Tuesday or Wednesday
- IPS updates are released every day
- Anti-Virus are updated every 2 hours
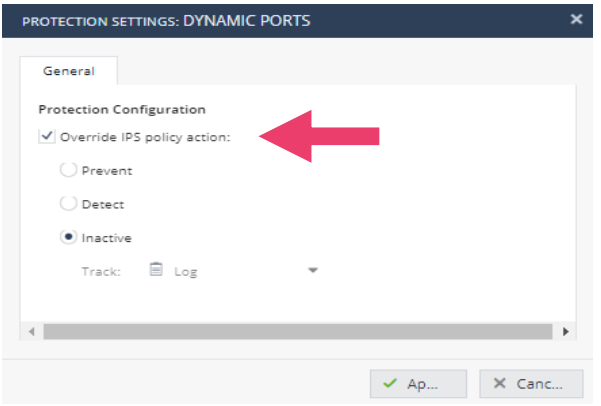
Policy Settings | IPS
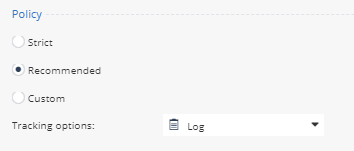
- Click on the Threat Prevention tab. Click Blade Control. The Threat Prevention Blade Control is displayed. Notice there are 3 policy options; Strict, Typical and Custom.
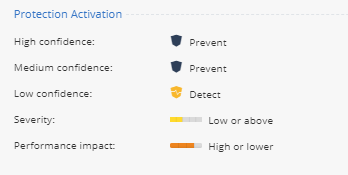
- Click on Custom to enable the configuration and click on configure. With this policy an IPS protection will be activated according to the protection severity, confidence-level, and performance impact. This is an easy way to modify your IPS instance based upon these three parameters. Click Load default settings and select a strict policy to see how the protection levels are set.
- Click Cancel to return to Threat Prevention Blade Control. Select Strict and Click Apply for the setting that provides the best security and good performance.
- Click Threat Prevention, Protections, IPS Protections. A list will be displayed. Double click on a protection. Notice that you can override the default action.
- Click on IPS Engine Settings. Notice that by default IPS inspection is done to protect internal hosts.
Policy settings | Anti-Virus
Anti-Virus allows you to block known malware using signatures and heuristics.
- Click on the Threat Prevention tab. Click Blade Control. Click Edit in the Anti-Virus or Anti-Bot section. Notice the default settings. Click Cancel.
- On the bottom of the Blade Control page, click on Schedule updates to see the automatic update schedule for IPS, Antivirus and Application Control. Click Cancel.
- Click on Engine Settings. In the File Types section, click on Configure. Click on the Action column to sort by Action. Notice that for some file types the default Action is Block. Click Close.
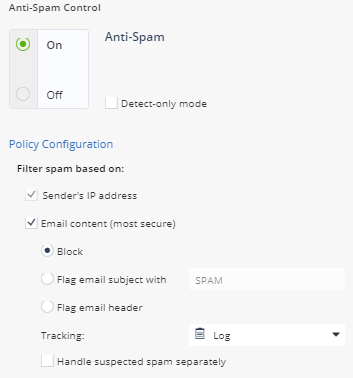
Policy settings | Anti-Spam
- Anti-Spam provides e-mail protection based on IP reputation, block/allow list, content-based and zero-hour outbreak protection.
- Click on Anti-Spam Blade Control. Notice the default settings.
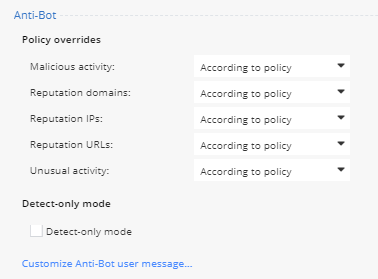
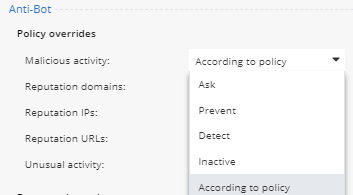
Policy settings | Anti-Bot
Anti-Bot blocks connections to Command & Control Servers. Helping you to identify infected systems.
- Notice the default settings.
- You can configured if needed, Ask.
Policy Settings | Threat Emulation
The 1500 series Appliance supports threat emulation handling for SMP, IMAP/IMAPS and POP3.
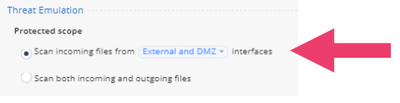
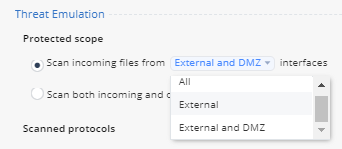
- Click on Threat Emulation Blade Control. Notice the default setting: scan incoming files from External and DMZ interface.
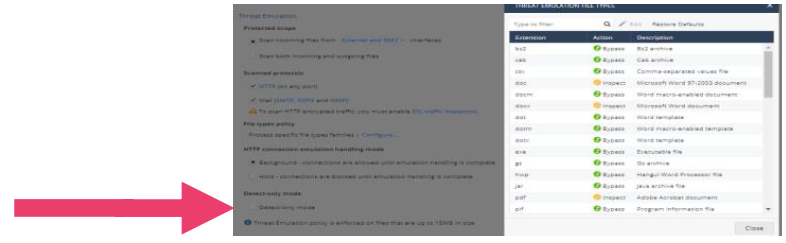
- Click on file types. Select the security that matches the requirements.
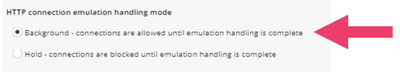
The default HTTP connection emulation handling mode is background.
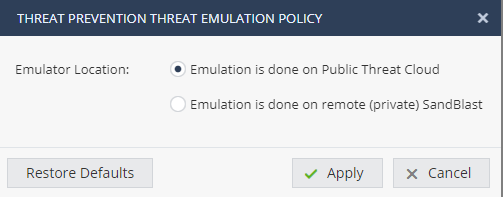
The 1500 Appliance also supports a Private Threat Cloud. With this setup an on-premises SandBlast Threat Emulation, TE appliance will be used for emulation.
The TE Appliance IP address can be configured via the WebUI.
- Click on Device -> Advanced -> Advanced Settings. Search for Threat Emulation.
Note: Default Public Threat Cloud
- The up following TE Appliances need to be configured via CLISH. CLISH is a default shell of the CLI, Command Line Interface.
set threat-prevention threat-emulation policy emulation-location remote primary-emulation-gateway <IP address>
Modifying the VPN Policy
The 1500 Appliance supports Site-to-Site for and Client-to-Site VPNs. The Remote Access options are available in this release.
|
Product |
Version |
Link |
|---|---|---|
|
Check Point VPN Clients |
E80.41, R75.20, E80.50, E80.60, E80.61, E80.62, E80.64, E80.65, E80.70, E80.71, E80.72, E80.80, E80.90, E80.92 |
|
|
Mobile Client |
Android Capsule VPN |
|
|
Mobile Client |
iOS Capsule Connect
|
|
|
SSL VPN |
Supported Endpoint Windows, Mac OS X and Linux platforms Java Availability |
|
|
L2TP VPN |
Windows L2TP VPN client For users who use their Windows VPN client |
- Click on VPN -> Site to Site -> VPN Sites. Click on New. Notice Authentication may be done by using Pre-shared keys or Certificate. The default Encryption Domain is set according to the network topology to facilitate VPN configuration. Click Cancel.
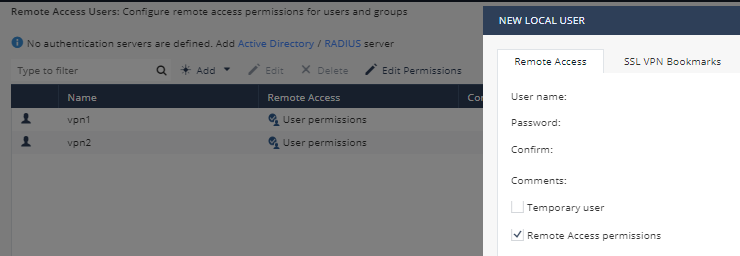
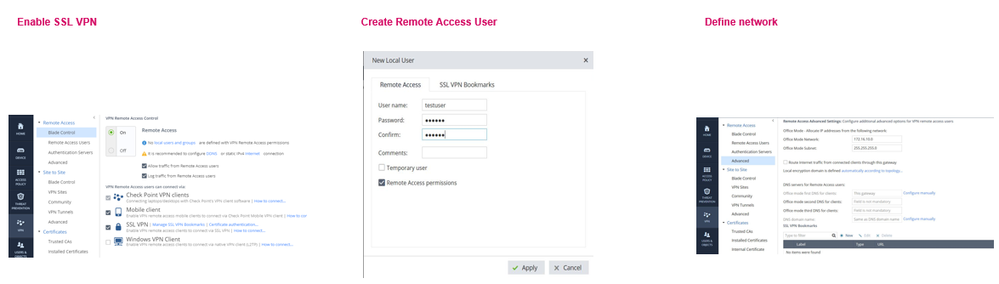
- Click on VPN -> Remote Access -> Blade Control. Notice that there are 4 options for Remote Access.
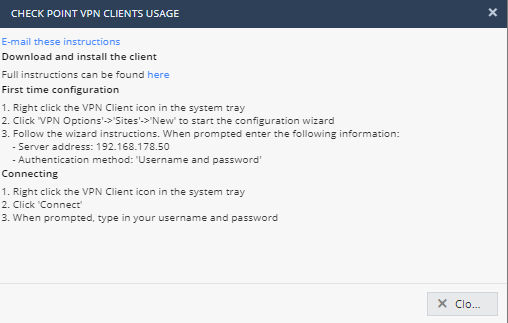
- Click on Check Point VPN clients Usage. Notice the instructions for setting up the Remote Access Client can be emailed to users and a link is provided for downloading the client. No special credentials are needed to download the client or the client documentation. Click Close.
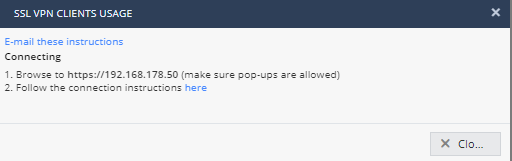
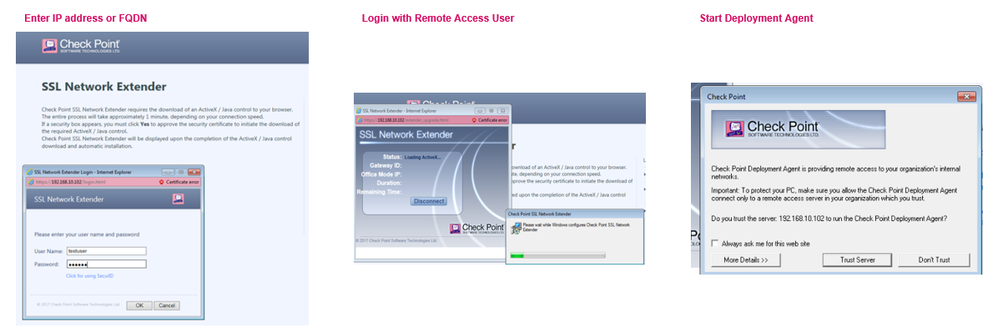
- Enable SSL VPN and Windows VPN client if desired. Click on SSL VPN Usage. Click on the Connection instructions link to see how to connect via SSL (SSL Network Extender). Click Close.
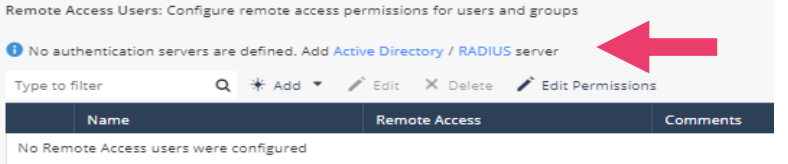
- Click on VPN -> Remote Access -> Remote Access Users. Click Add -> New Local User. Notice that Active Directory and RADIUS authentication is supported.
- Click VPN -> Remote Access -> Advanced. Notice that Office Mode is supported. Office Mode is used by remote clients inside the local network and makes them part of the local network. Notice that it is also possible to Route Internet traffic from connected clients through this gateway. It provides the same protection to remote clients as it does to local internal clients.
Modifying Users & Objects
The 1500 Appliance includes User Awareness. It provides the ability to create security policies based upon users or IP addresses and ports. In the Users & Objects tab local users and remote user solutions like Active Directory and RADIUS can be configured. Same goes for network objects, services, and applications.
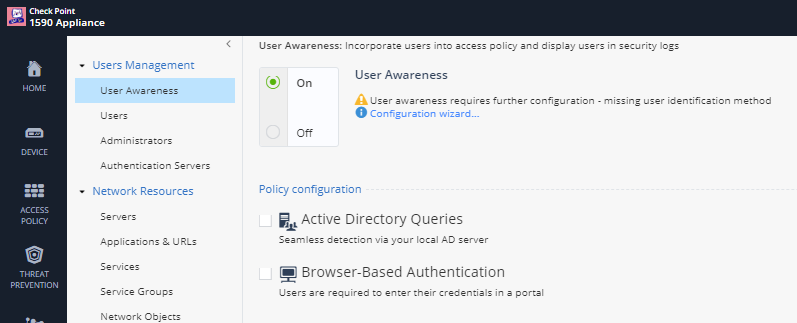
- Click on Users & Objects -> Users Management -> User Awareness. Click on Configuration Wizard.
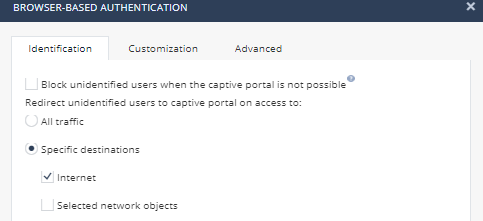
- Notice there are two options; Active Directory Queries and Browser-Based Authentication. Enable BrowserBased Authentication. Notice “Block unidentified users when captive portai is not possible and “Redirect unidentified users to captive portal on access to”
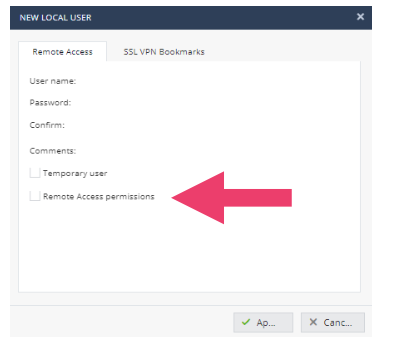
- Click on Users & Objects -> Users Management -> Users. Click New -> Local Users. Notice that users may be given temporary and remote access permission.
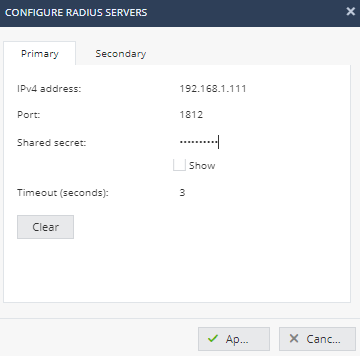
- Click on Users & Objects -> Users Management -> Administrators. Notice that RADIUS authentication is an option.
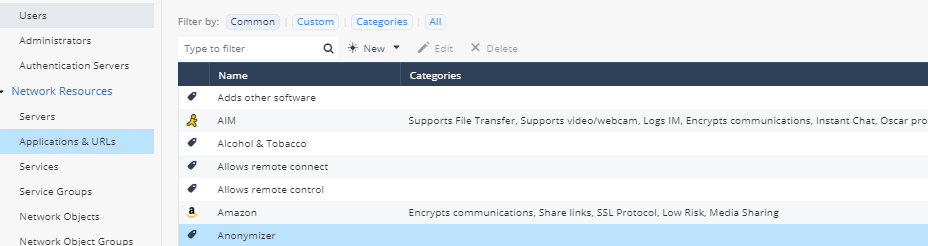
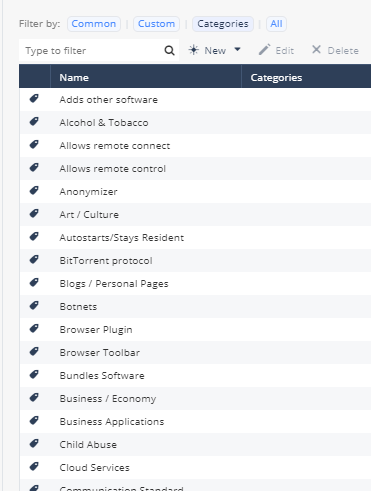
- Click on Users & Objects -> Network Resources -> Applications & URLs. Click All. Notice that there are over 6,000 Applications that are available in the security policy providing granular control.
- Click Categories to show the Application & URL categories. Notice how easily you can create a security policy that is categories.
Logging, Monitoring and Reporting
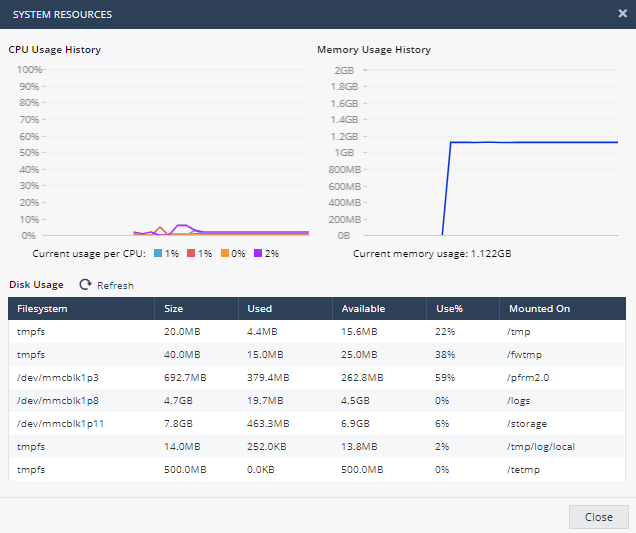
The 1500 Appliance includes a Google-like search through security and system logs. Here you can also view active computers, view high risk security events, high bandwidth users, applications and generate hourly, daily, weekly and monthly reports. In addition you can create a diagnostics file or packet capture.
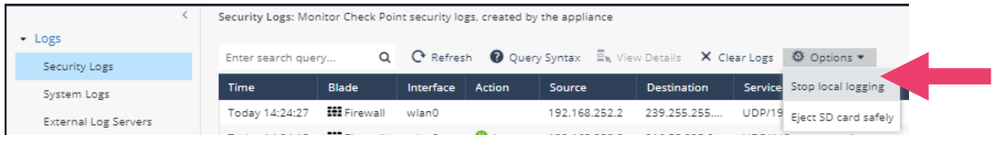
- Click Logs -> Options. Notice that in Security Logs there is an option to safely eject the SD Card. The appliance has the option to save logs to an SD card of up to 32 GB.
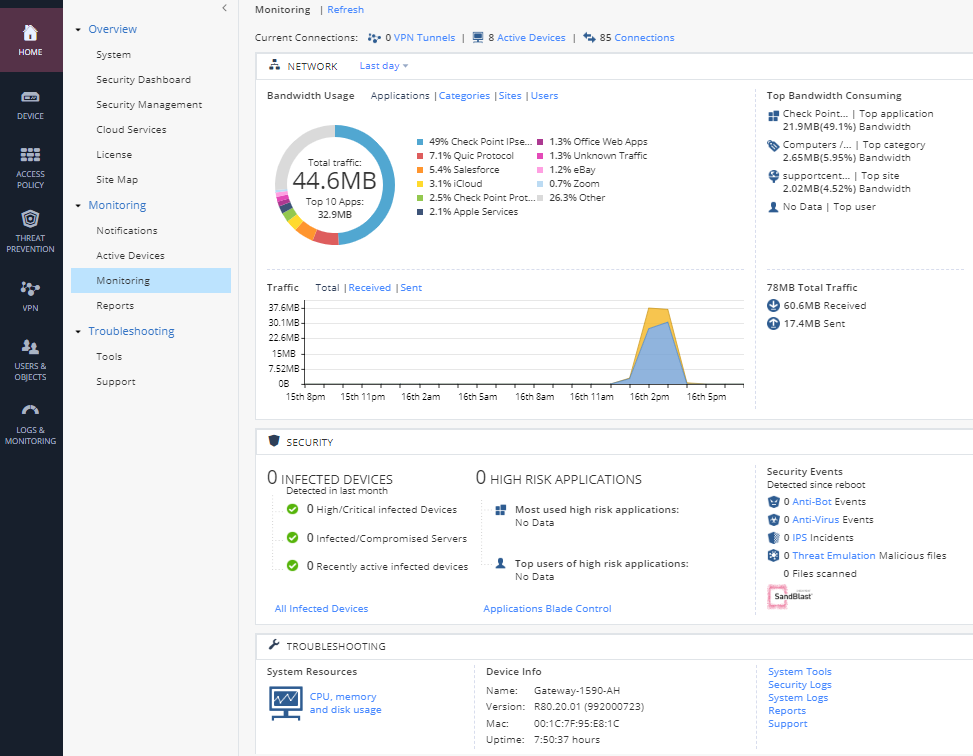
- Click on Monitoring. Scroll through the available graphs.
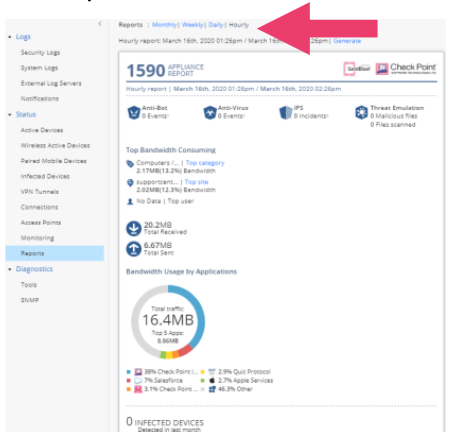
- Click on Security Reports -> Reports Dashboard. Generate an hourly report and then click it to view the result. If you have not generated a lot of traffic, notice that there is a (View demo) report to see what the report might look like when the appliance is in a high use environment. Scroll though the report to see Security Events, Bandwidth Consumption and Number of Sessions reports.
- Notice that in Diagnostics there is a tool to Monitor System Resources, Generate a CPinfo diagnostic file and create a packet capture file for support and the ability test cloud services ports. Click on Monitor System Resources.
Networking Features
- The 1500 Appliance supports a lot of networking features, for example:
- Alias IP | Associate more than one IP address to the same network interface
- Link Aggregation | Aggregating or bonding of multiple network connections. Join two or more interfaces together to improve performance and redundancy by increasing the network throughput and bandwidth
- Supported VLANs | Support for 100 VLANs
- Dynamic Address Assignment (DHCP) | Dynamic IP address assignment from the internet connection to the bridge interface
- Assign hostname from DHCP server | Assign the appliance hostname from a DHCP server with DHCP option 12
- DHCP whitelist | Configure your network so IP addresses are assigned by the internal network DHCP server only for known hosts (defined as network objects and a specific MAC address is assigned to the IP). DHCP requests from other hosts are ignored.
Cloud Services | Security Management Portal, SMP
The Security Management Portal simplifies the deployment and maintenance of Check Point SMB gateways using group-based management tools. Administrators define multiple service plans, each consisting of a template that defines the plan’s expiration date, gateway properties, VPN settings, as well as additional services such as Anti-Virus protection and content filtering. Plans can be associated with an unlimited number of SMB gateways which inherit all of that plan’s properties. Specific aspects can be overridden if required. When the administrator updates the plan, the changes are automatically applied to all associated gateways.
Log, Report, Monitor and Alert
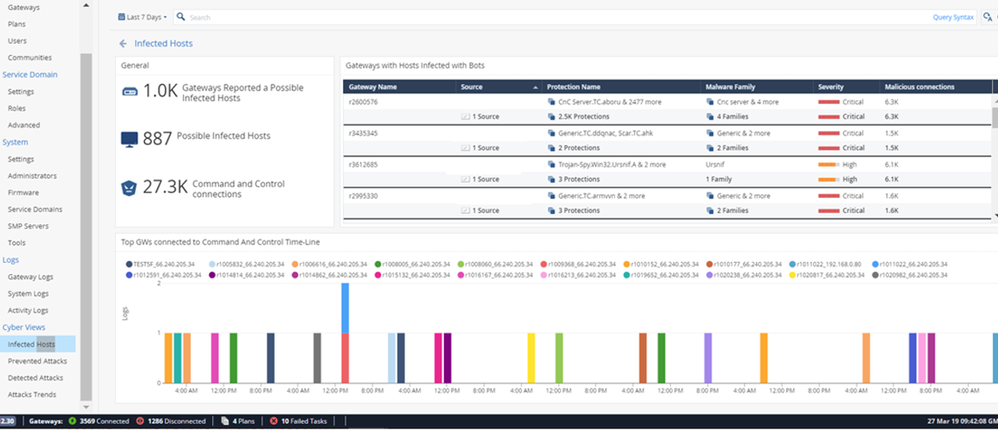
Security reports can be rebranded, automatically generated and emailed to customers at predefined intervals and can also be viewed directly from the SMP management interface. Security reports include information about blocked attacks, detected viruses, filtered web sites and more. In addition, SMP offers powerful real-time monitoring tools, showing the status of connected devices at a single glance. You can use real-time alerts and notifications to proactively support your customers and notify them of connection outages, VPN tunnel drops or attacks, all before the customers become aware of these problems. In network analysis you can find top applications and users consuming the most bandwidth. Security analysis shows users visiting high-risk sites and using high-risk applications. You can also view incidents or infected hosts found during the reporting period.
Automate Firmware Updates
Ensuring that hundreds of gateways all enforce the highest level of security can be a daunting administrative task. To address this problem, Check Point SMB gateways use a “fetch” technology for automatic and scheduled firmware updates: gateways automatically detect and download new firmware whenever it becomes available on the management server, instead of the management server initiating communications with each individual gateway. This reduces the load on the management server. In addition, updates can be scheduled to minimize gateway downtime, and administrators also have the option to override group settings and push unique firmware and settings to specific gateways.
The cloud-managed service, Security Management Portal, SMP you can manage the security policy, firmware upgrades (gradual and remote scheduled), Cyber Views and periodic backups. Key benefits of the SMP:
- Easy initial setup
- Protected with the latest Check Point security
- Detailed security and network usage reports
- Safe and simple device replacement process
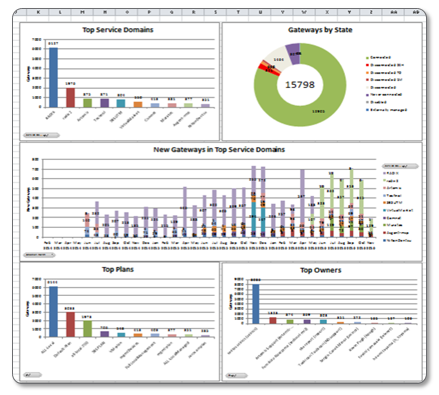
Below is a screenshot that shows the customer view and the features.
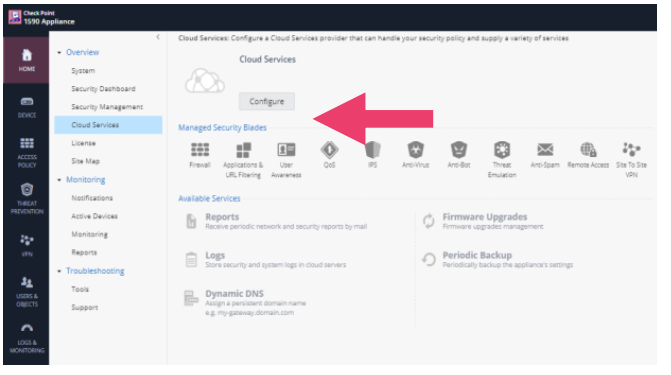
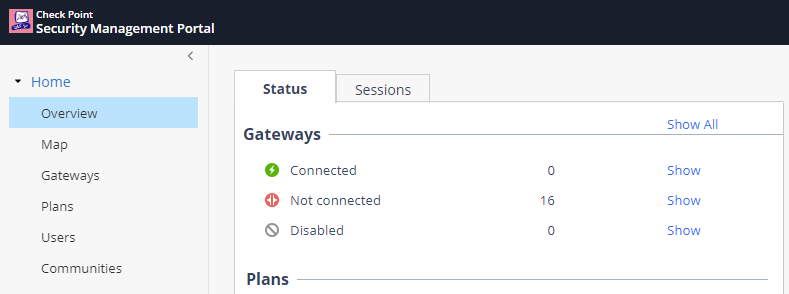
- Click on Home -> Overview -> Cloud Services. Notice the options for managing the 1500 Appliance.
- When a customer is registered an email is sent with instructions how configuring the Cloud Service connection.
- For Internet Service Providers (ISPs) and Managed Service Providers (MSPs) the cloud-managed service offers an interface to manage and support thousands of their customers easily and intuitively. This includes security policy management, firmware upgrades, automatic backups, periodic reports and VPN community support which is essential when using these appliances in the retail sector. Key benefits of the service to ISPs and MSPs are;
- Cloud based, mutli-tenant, central management
- Designed for managed service providers on any scale
- Supports management of 10,000 small business appliances from a single console
- Provides ISPs and MSPs with value-add and upsell opportunities
A demo site of the cloud managed interface is available. Ask your Check Point contact to provide access to the demo. Highlights of the interface are shown below for your convenience.
- When administrators login to the site, they’re presented with an overview of the managed devices.
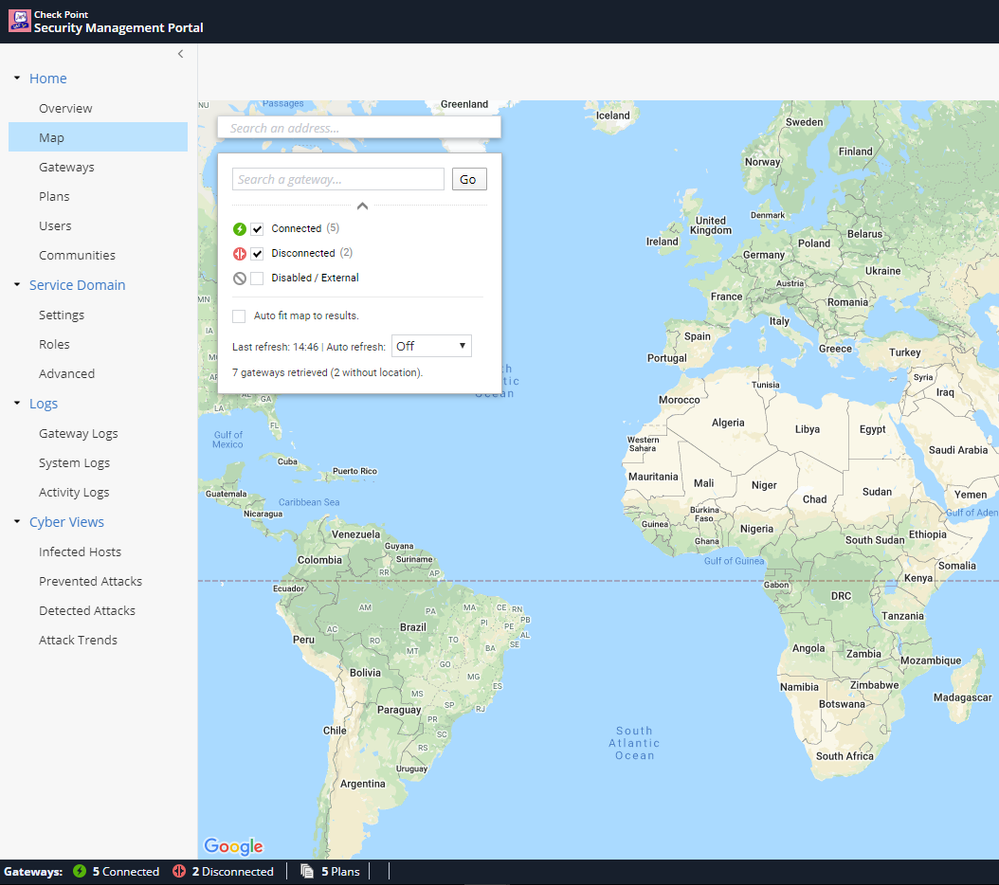
- Click on Home -> Map. A map is displayed of the managed devices. Click on Gateways to see a overview of all managed devices, the device owner and the plan assigned to the device.
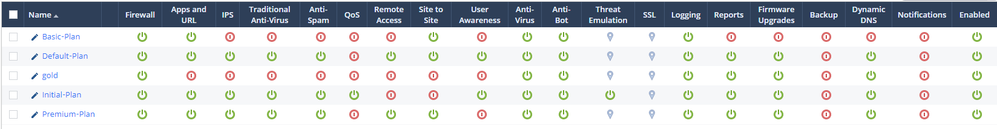
- Click on Home -> Plans to see what services are covered in the different plans.
- Click on Home -> Communities. Notice that it’s possible to set up VPNs for managed appliances.
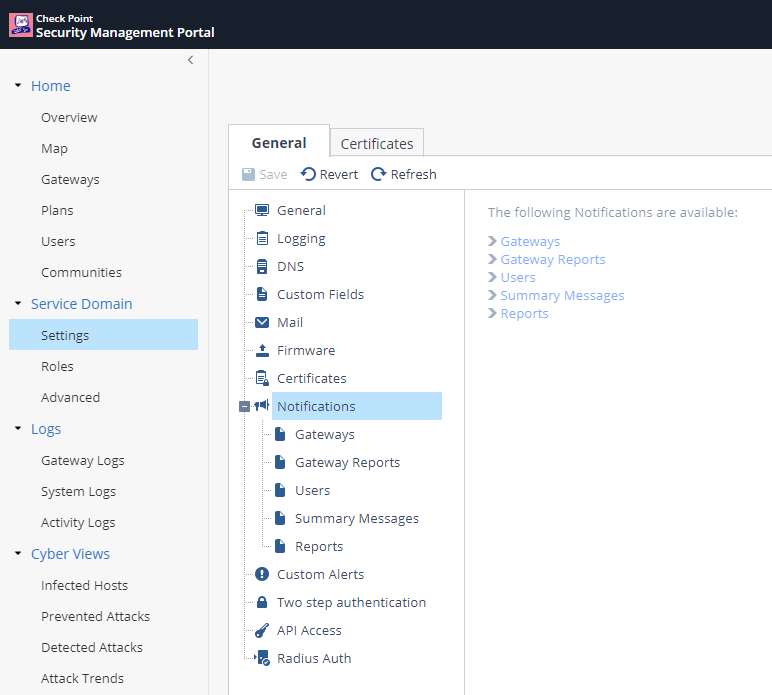
- Click on Service Domain -> Settings. Here you can set notifications, logging options and DNS settings.
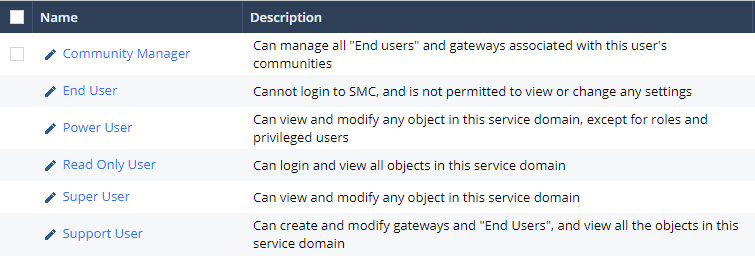
- Click on Service Domain -> Roles. Notice that different roles.
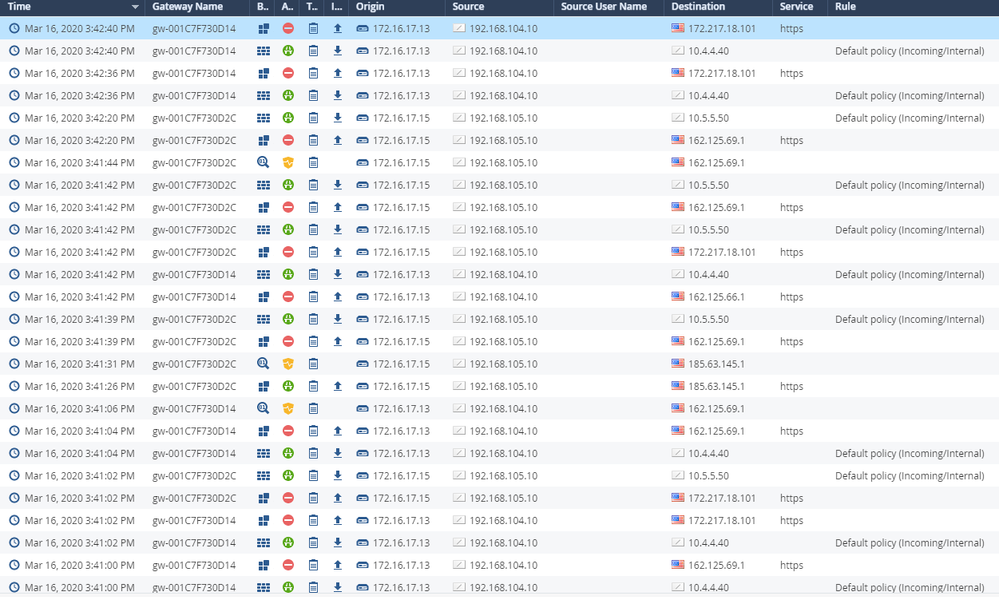
- Click on Gateway Logs -> Logs. Here admins can monitor and investigate incidents. The search bar is a “Google-like” search engine that help sort the logs.
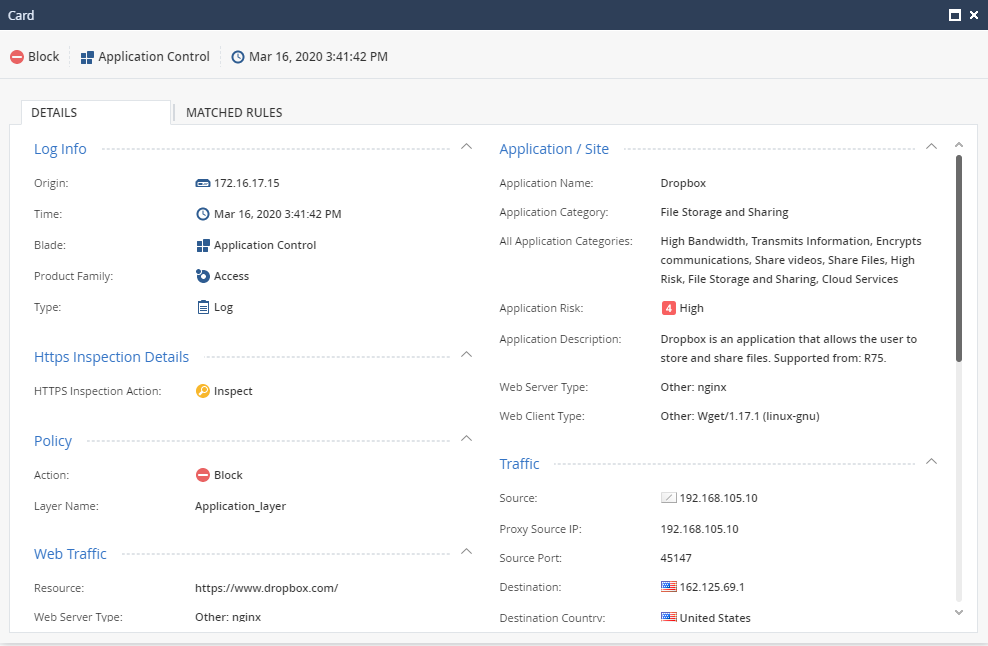
- Double click on the log. The log card shows useful information on that specific transaction.
- CyberViews provides detailed and realtime insight. All widgets are intuitive and clickable.
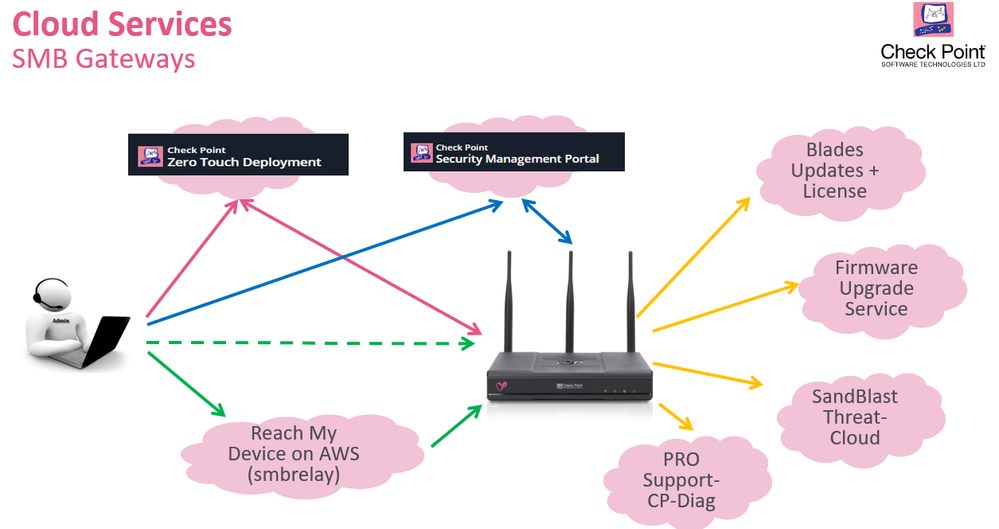
Cloud Services | Zero Touch
- The Zero Touch Cloud service allows users to manage easily the initial deployment of Security Gateways. The administrator applies the initial deployment configuration for the gateways in the Zero Touch portal (or API service). When a gateway is connected to the internet for the first time, it fetches the settings automatically. The settings from the Zero Touch server replace the First Time Configuration Wizard. Zero Touch Cloud service is based REST API, all actions are available through API calls.
|
Guide |
Link |
|---|---|
|
Zero Touch Administration |
|
|
Zero Touch API |
MaaS | Management as a Service
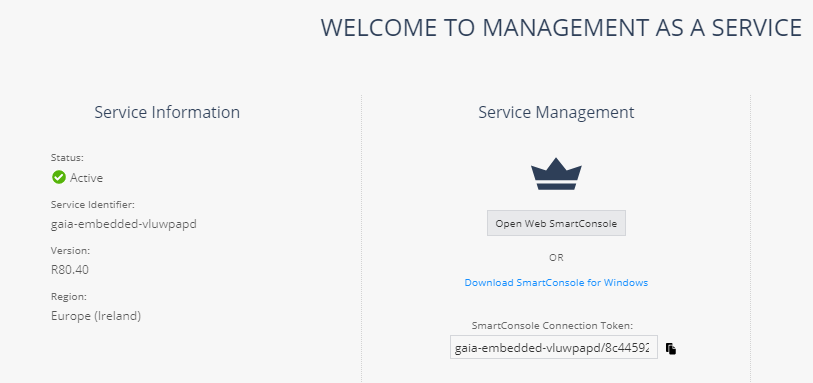
- The 1500 Appliance supports MaaS for central managed appliances. Management as a Service is a new Software as a Service solution for Security Management. Instead of deploying and maintaining a Management server, customers can connect to our new service and manage their on-premises gateways. Setup is very easy and can be done by registering to portal.checkpoint.com. With no start up efforts, no installation, no deployment and no upkeep.
Key benefits:
- Elastic growth
- Infinite logging
- Always up-to date
- Zero maintenance
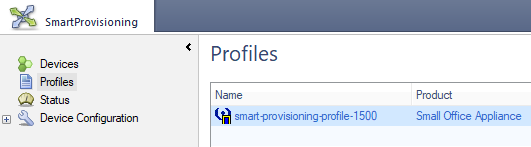
LSM | Large Scale Management
LSM and SmartProvisioning lets you manage multiple gateways from one Security Management Server, SMS or MDS. SmartProvisioning defines, manages, and provisions meaning, remotely configures large-scale deployments. In Central Management environments with SMB domain and updatable objects are supported.
SmartProvisioning helps you manage the load on the Appliances.
The policy is not installed on all Appliances simultaneously, but the Appliances fetch the policy at different time intervals. The SmartProvisioning management concept is based on profiles, which help you manage your gateways more efficiently. With these profiles, you can define the gateway settings once and then assign each profile to multiple gateways, as needed. For example, when you select which blades to enable in the LSM Profile, the selected blades are enabled on all gateways which are assigned to the Profile.
SmartProvisioning supports two types of profiles: Security Profiles, which define the security settings, and Provisioning Profiles, which define the device settings. SmartProvisioning is efficient for use in large enterprises with many branch offices, where the branch offices have identical or similar characteristics. You can use a relatively small number of Security Profiles or Provisioning Profiles to manage a huge amount of Appliances.
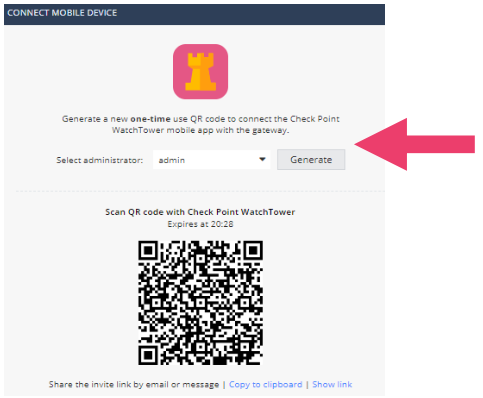
WatchTower
Enhance your Check Point network security with the ability to monitor your network and quickly mitigate security threats on the go with your mobile phone. The intuitive app provides real-time monitoring of network events, alerts you when your network is at risk, enables you to quickly block security threats, and configure the security policy for multiple gateways. The main features include: security alerts, on-the-spot threats, security policy configuration, customized push notifications and prioritized event notifications.
- Install the WatchTower app on your mobile phone
- Click on pair your mobile device. Select the relevant administrator and generate the QR code. The QR code can be shared with an invitation link via email or message.
- Notice the management of administrators, security updates and assign contacts.
For detailed information see WatchTower User Guide
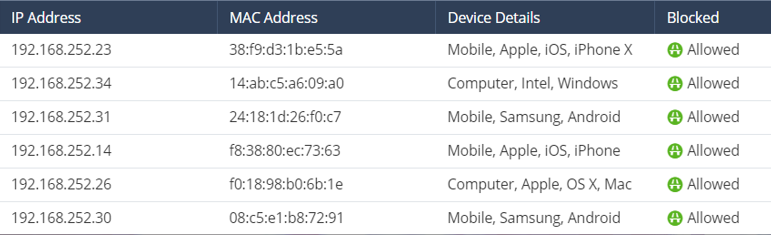
IoT Device recognition and discovery
The 1500 Appliance offers Device Recognition and Discovery. Find all connected devices in your network.
Wi-Fi
In our walk-through of the 1500 Appliance management, we skipped over the Device tab. In the Device tab the network configuration defined in the First-Time Configuration can be further defined. And other administrative and maintenance can be done. Monitor and track your Wi-Fi environment to identify congested channels, frequency used and signal strength.
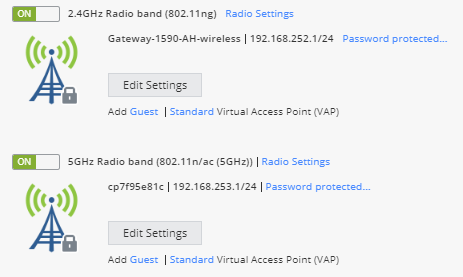
- Click on Device -> Network -> Wireless.
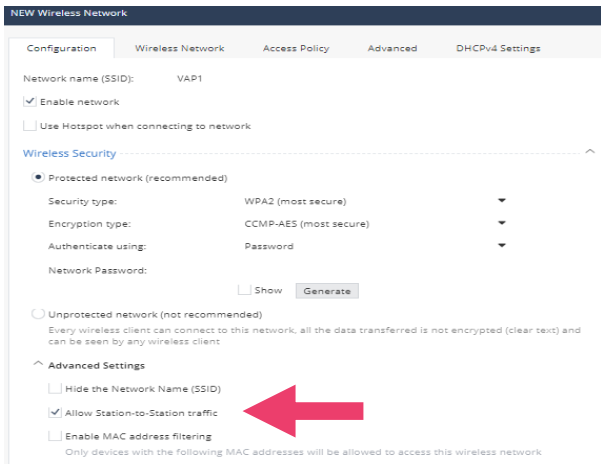
- Notice that this option provides the ability to have multiple wireless networks. This may be useful if you want to have one wireless networks for employees and one wireless network for guest access. Click Add a Standard Virtual Access Point (VAP).
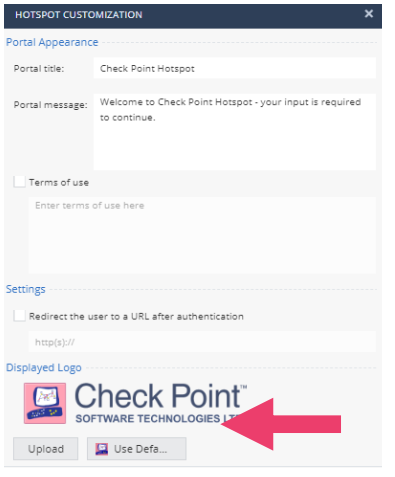
- Notice there is an optioin to enable a Hotspot. When enabled this option redirects users to the Hotspot portal. You can configure the Hotspot portal with your own company logo.
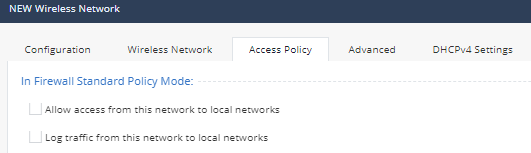
- Click on the Access Policy tab. Notice that Allow access from this network to local networks is checked. For a guest wireless network you may want to disable this. Click Cancel.
- Click Device -> Network -> Hotspot. This is where you would complete the hot spot configuration.
- Finally click on Device -> System -> System Operation. You can reboot the appliance, manage images, back up and restore from a backup. Now that appliance configuration has been completed, it is a good time to create a backup. Click on Backup. To understand the backup options, Click on Help.
If you wish to replace an existing appliance with another one (for example, upon hardware failure) you can simply restore the settings saved on your previous appliance and re-activate your license (through License Page > Activate License).
If you want to duplicate an existing configuration you can restore the settings of the original appliance on the new one. Make sure to change the IP address of the duplicated appliance (Device > Internet page) and generate a new license.
Click on Backup. When the backup file is ready, click on Download Backup. The backup file is downloaded to your computer.
SSL/HTTPS Inspection
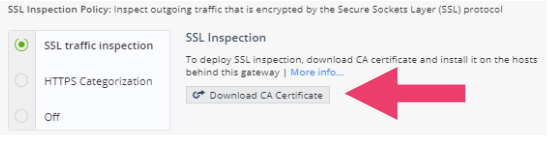
- Click on Access Policy -> SSL Inspection -> Policy. Notice the default HTTPS Categorization. This functionality allows URL filtering for HTTPS sites and applications based on server’s certificate, without activating SSL traffic inspection.
- Click Access Policy -> SSL Inspection -> Policy -> SSL traffic inspection. Notice the CA certificate needs to be downloaded for deployment of SSL inspection.
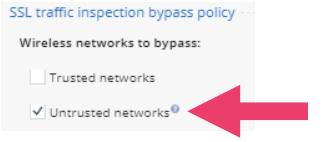
- Default untrusted networks are excluded.
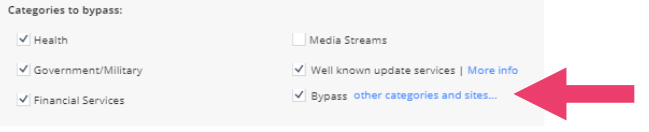
- Notice the bypass categories and click bypass other categories and sites
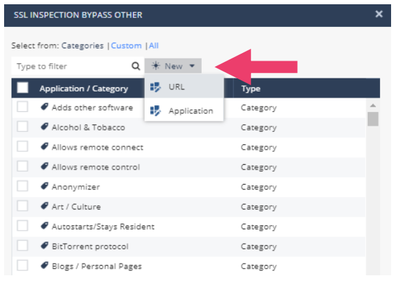
- Click bypass other categories and sites, if you wish you can add new URL’s or applications
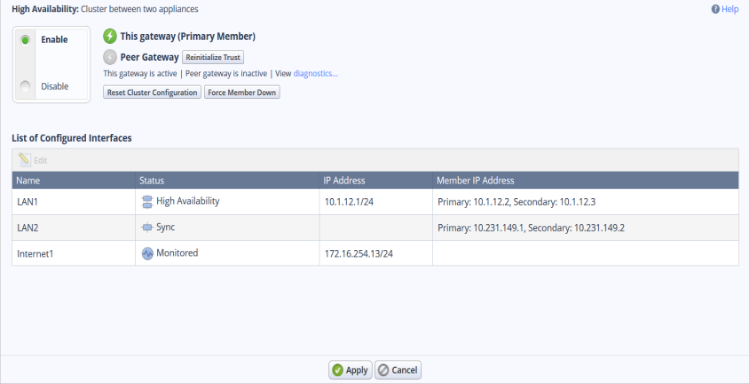
Clustering/High Availability
You can configure two appliances in a cluster configuration for High Availability. High Availability maintains connections in the organization's network when there is a failure in a cluster member.
Only one gateway is active. When there is a failover, the standby member becomes active, providing 100% availability.
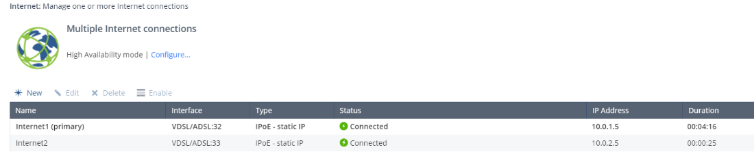
ISP Redundancy
We all become dependent on internet connectivity. Uninterrupted internet access is mission critical. Check Point Supports two types of traffic distribution: Load Sharing and High Availability. Connection monitoring can be done on recovery time, maximum latency allowed, probing frequecy, pings and failover pings.
Advanced options
The advanced Settings allows you to manage and configure very advanced settings. Changing these Advanced Settings can be harmful to the stability, security and performance. They should only be used in special configurations and when advised by Check Point
To become familiar with the Advanced Settings follow this quick walk through.
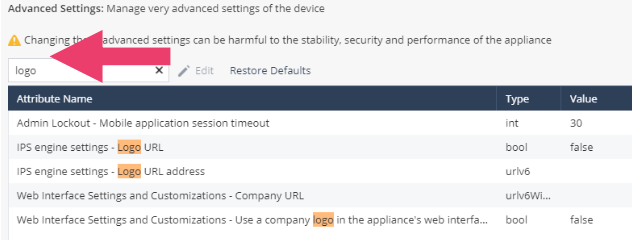
- Click on the Device -> Advanced -> Advanced Settings.
- The search bar takes you quickly to the desired configuration option. Search for logo.
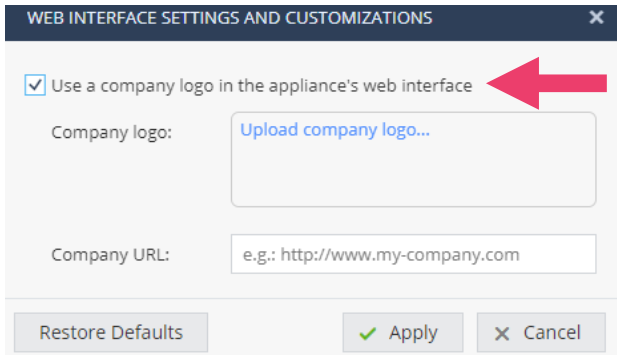
- Notice you can upload your own Company logo quite easy.
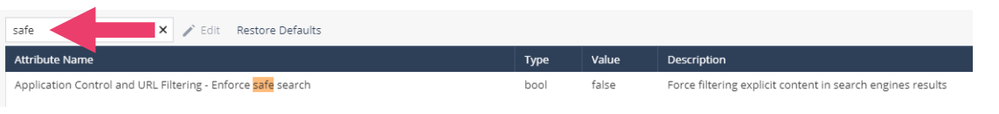
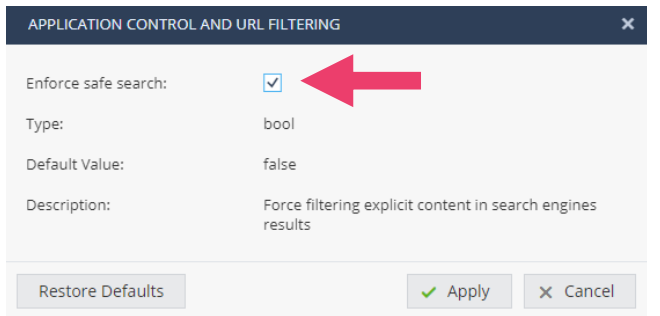
- You might want to enable Safe Search to enforce filtering of explicit content in search engines.
- Enable this functionality by clicking the checkbox.
The 1500 Appliance also supports the SNI, Server Name Indications functionality with Next Generation Bypass, TLS inspection is based on Verified Subject Name. And offers an improved TLS implementation for TLS Inspection and Categorization.
Conclusion
This completes the tour of the 1500 Appliance. We hope that you enjoy the new local management interface. If you have questions about the appliance please don’t hesitate to ask here in the comments.
Labels
About this guide
The 1500 Appliance includes the same enterprise-grade Software Blade security that is deployed on Check Point security appliances. Unique to the 1500 Appliance is the simplified web-based management and pre-defined security policies providing out-of-the-box security. This guide describes the Check Point 1500 Appliance management, focusing on the Next Generation security policy pre-defined on the 1500 Appliance. The policies are explained, followed by a general explanation of how to modify the default policies.
Authors and contributors
This document is
- created by Antoinette Hodes a.k.a. @AntoinetteHodes
- edited by @Aviv_Abramovich
- adapted for CP4B by @_Val_
Documentation
The 1500 Appliance includes a Quick Start Guide and Getting Started Guide. Context sensitive on-line help is available in the Web User Interface.
The platform
Check Point 1500 Appliances
Check Po
...You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
About CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter