- Products
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- Learn
- Local User Groups
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
- Partners
- More
- ABOUT CHECKMATES & FAQ
- Sign In
- Leaderboard
- Events
Call For Papers
Your Expertise, Our Stage
Ink Dragon: A Major Nation-State Campaign
March 11th @ 5pm CET / 12pm EDT
AI Security Masters E4:
Introducing Cyata - Securing the Agenic AI Era
The Great Exposure Reset
AI Security Masters E3:
AI-Generated Malware
CheckMates Go:
CheckMates Fest
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Developers
- :
- API / CLI Discussion
- :
- Sample batch script to deploy MDSM environment for...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
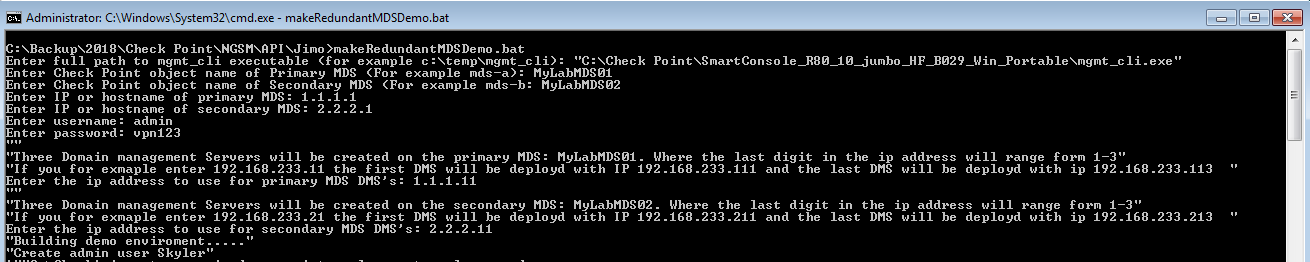
Sample batch script to deploy MDSM environment for lab purposes.
Provisioning Demo using a basic batch script
Using the Security Management API to provisioning domain objects, gateway objects and rules for a single or redundant MDSM environment automatically.Se below for a short around 3 minute video demonstrating the execution of the script.
Description
Attached are two batch files that will allow you to create a single or redundant MDSM environment with gateways, rules and objects to be used for lab and training purposes.
After filling in in some information this script will deploy 4 domains in a single or redundant MDSM environment on one or two MDS servers. The domains are filled with Check Point Gateways, Objects and rules
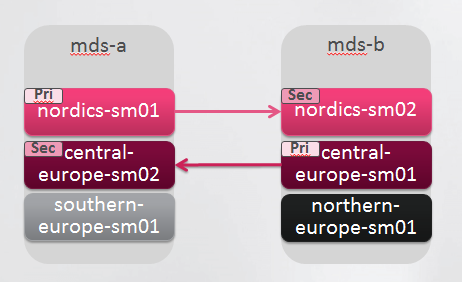
The batch script will build the following topology. In a single deployment all domains will be created on one MDS.
Single Multi-Domain Server Script
@echo off
rem makeSingleMDSDemo.bat create by jimo@checkpoint.com 2017-05-02
rem this batch file will provisioning a MDS demo with domains and rules.
rem Pre-requirements is to have one MDS server installed
goto :comment1
rem ###################### Skip this part and goto comment1#########################
set varMgmt_cli=C:\Backup\2017\Check Point\NGSM\R80.10\Pre-GA\Hugo1_394_T2\SmartConsole_Hugo1_394_T2\PROGRAM\mgmt_cli
set varMdsObject="mds01"
set varMds="172.27.254.20"
set varUid="admin"
set varPwd="vpn123"
set varPrimds_range="172.27.254.2"
:comment1
set /p varMgmt_cli="Enter full path to mgmt_cli executable (for example c:\temp\mgmt_cli): "
set /p varMdsObject="Enter Check Point object name of the MDS (For example mds01): "
set /p varMds="Enter IP or hostname of the MDS: "
set /p varUid="Enter username: "
set /p varPwd="Enter password: "
echo ""
echo "Four Domain management Servers will be created on the MDS server: %varMdsObject%. Where the last digit in the ip address will range form 1-4"
echo "If you for exmaple enter 192.168.233.11 the first DMS will be deployd with IP 192.168.233.111 and the last DMS will be deployed with ip 192.168.233.114 "
set /p varPrimds_range="Enter the ip address to use for primary MDS DMS's: "
echo "Building demo enviroment....."
rem ################ Create Admins and Domains ###########################################
echo "Create admin user Skyler"
"%varMgmt_cli%" --unsafe-auto-accept true -m %varMds% login user "%varUid%" password "%varPwd%" domain "System Data" > id.txt
"%varMgmt_cli%" set session new-name "Create admin Skyler" description "Creating administrator Skyler to be used in the API calls to populate the demo database" -s id.txt
"%varMgmt_cli%" add-administrator name "Skyler" password "1234" must-change-password false multi-domain-profile "Multi-Domain Super User" -s id.txt
"%varMgmt_cli%" publish -s id.txt
"%varMgmt_cli%" logout -s id.txt
echo "Create admin users for Multi Domain using user Skyler"
"%varMgmt_cli%" -m %varMds% login user "Skyler" password "1234" domain "System Data" > id.txt
"%varMgmt_cli%" set session new-name "Create ACME Corp MDS Admins" description "Creating MDS administrators for ACME Corp" -s id.txt
"%varMgmt_cli%" add-administrator name "Walter" password "1234" must-change-password false multi-domain-profile "Multi-Domain Super User" -s id.txt
"%varMgmt_cli%" add-administrator name "Saul" password "1234" must-change-password false multi-domain-profile "Multi-Domain Super User" -s id.txt
"%varMgmt_cli%" add-administrator name "Jesse" password "1234" must-change-password false multi-domain-profile "Domain Level Only" -s id.txt
"%varMgmt_cli%" publish -s id.txt
echo "Build the domains for ACME Corp MDSM start with Nordics domain"
"%varMgmt_cli%" set session new-name "Create Nordics domain" description "Creating domain management server for the Nordics region" -s id.txt
"%varMgmt_cli%" add domain name "Nordics" servers.name "Nordics-sm01" servers.ip-address "%varPrimds_range%1" servers.multi-domain-server "%varMdsObject%" -s id.txt
"%varMgmt_cli%" set trusted-client name "AnyHost" domains-assignment.add "Nordics" -s id.txt
"%varMgmt_cli%" publish -s id.txt
"%varMgmt_cli%" logout -s id.txt
echo "Create Central-Europe domain"
"%varMgmt_cli%" -m %varMds% login user "Walter" password "1234" domain "System Data" > id.txt
"%varMgmt_cli%" set session new-name "Create Central Europe domain" description "Creating domain management server for the Central Europe region" -s id.txt
"%varMgmt_cli%" add domain name "Central-Europe" servers.name "Central-Europe-sm01" servers.ip-address "%varPrimds_range%2" servers.multi-domain-server "%varMdsObject%" -s id.txt
"%varMgmt_cli%" set trusted-client name "AnyHost" domains-assignment.add "Central-Europe" -s id.txt
"%varMgmt_cli%" publish -s id.txt
"%varMgmt_cli%" logout -s id.txt
echo "Create Southern-Europe domain"
"%varMgmt_cli%" -m %varMds% login user "Saul" password "1234" domain "System Data" > id.txt
"%varMgmt_cli%" set session new-name "Create Southern Europe domain" description "Creating domain management server for the Southern Europe region" -s id.txt
"%varMgmt_cli%" add domain name "Southern-Europe" servers.name "Southern-Europe-sm01" servers.ip-address "%varPrimds_range%3" servers.multi-domain-server "%varMdsObject%" -s id.txt
"%varMgmt_cli%" set trusted-client name "AnyHost" domains-assignment.add "Southern-Europe" -s id.txt
"%varMgmt_cli%" publish -s id.txt
"%varMgmt_cli%" logout -s id.txt
echo "Create Northern-Europe domain"
"%varMgmt_cli%" -m %varMds% login user "Saul" password "1234" domain "System Data" > id.txt
"%varMgmt_cli%" set session new-name "Create Northern Europe domain" description "Creating domain management server for the Northern Europe region" -s id.txt
"%varMgmt_cli%" add domain name "Northern-Europe" servers.name "Northern-Europe-sm01" servers.ip-address "%varPrimds_range%4" servers.multi-domain-server "%varMdsObject%" -s id.txt
"%varMgmt_cli%" set trusted-client name "AnyHost" domains-assignment.add "Northern-Europe" -s id.txt
"%varMgmt_cli%" publish -s id.txt
"%varMgmt_cli%" logout -s id.txt
rem ################ Fill Nordics domain ###########################################
echo "Populate Nordics domain with objects and rules"
"%varMgmt_cli%" -m %varMds% login user "Skyler" password "1234" domain "Nordics" > id.txt
"%varMgmt_cli%" set session new-name "Create rule base" description "Populate Nordics domain with objects and rules" -s id.txt
"%varMgmt_cli%" add simple-gateway name "Stockholm-sg01" ip-address 192.0.0.40 version r80.10 one-time-password "vpn123" firewall true ips true vpn true -s id.txt
"%varMgmt_cli%" add simple-gateway name "Oslo-sg01" ip-address 192.0.2.30 version "r80.10" one-time-password "vpn123" firewall true ips true vpn true interfaces.1.name "eth0" interfaces.1.ip-address 192.0.2.30 interfaces.1.mask-length 24 interfaces.1.topology "EXTERNAL" interfaces.2.name "eth1" interfaces.2.ip-address 198.53.100.5 interfaces.2.mask-length 25 interfaces.2.topology "INTERNAL" interfaces.2.topology-settings.ip-address-behind-this-interface "LOCAL_NETWORK" interfaces.3.name "eth2" interfaces.3.ip-address 198.53.100.129 interfaces.3.mask-length 25 interfaces.3.topology "INTERNAL" interfaces.3.topology-settings.ip-address-behind-this-interface "LOCAL_NETWORK" -s id.txt
"%varMgmt_cli%" add simple-gateway name "Helsinki-sg01" ip-address 192.0.2.40 version "r75.40" one-time-password "vpn123" firewall true ips true vpn true interfaces.1.name "eth0" interfaces.1.ip-address 192.0.2.40 interfaces.1.mask-length 24 interfaces.1.topology "EXTERNAL" interfaces.2.name "eth1" interfaces.2.ip-address 198.54.100.5 interfaces.2.mask-length 25 interfaces.2.topology "INTERNAL" interfaces.2.topology-settings.ip-address-behind-this-interface "LOCAL_NETWORK" interfaces.3.name "eth2" interfaces.3.ip-address 198.54.100.129 interfaces.3.mask-length 25 interfaces.3.topology "INTERNAL" interfaces.3.topology-settings.ip-address-behind-this-interface "LOCAL_NETWORK" -s id.txt
"%varMgmt_cli%" add simple-gateway name "Copenhagen-sg01" ip-address 192.0.2.200 firewall true anti-bot true anti-virus true application-control true threat-emulation true ips true url-filtering true vpn true interfaces.1.name "eth0" interfaces.1.ip-address 192.0.2.200 interfaces.1.mask-length 24 interfaces.1.topology "EXTERNAL" interfaces.2.name "eth1" interfaces.2.ip-address 198.51.100.5 interfaces.2.mask-length 25 interfaces.2.topology "INTERNAL" interfaces.2.topology-settings.ip-address-behind-this-interface "LOCAL_NETWORK" interfaces.3.name "eth2" interfaces.3.ip-address 198.51.100.129 interfaces.3.mask-length 25 interfaces.3.topology "INTERNAL" interfaces.3.topology-settings.ip-address-behind-this-interface "LOCAL_NETWORK" -s id.txt
"%varMgmt_cli%" add simple-gateway name "SandBlastDevice" comments "Threat Emulation" ip-address 192.0.2.13 firewall true threat-emulation true interfaces.1.name "eth0" interfaces.1.ip-address 192.0.2.13 interfaces.1.mask-length 24 interfaces.1.topology "EXTERNAL" interfaces.2.name "eth1" interfaces.2.ip-address 198.0.1.113 interfaces.2.mask-length 25 interfaces.2.topology "INTERNAL" interfaces.2.topology-settings.ip-address-behind-this-interface "LOCAL_NETWORK" -s id.txt
echo # Add Hosts
"%varMgmt_cli%" set session description "Add hosts" new-name "creating host objects" -s id.txt
"%varMgmt_cli%" add host name "DNS Server" ip-address 198.53.100.130 color "ORANGE" -s id.txt
"%varMgmt_cli%" add host name "Web Server" ip-address 198.53.100.131 color "ORANGE" -s id.txt
"%varMgmt_cli%" add host name "FTP Server" ip-address 198.53.100.132 color "ORANGE" -s id.txt
"%varMgmt_cli%" add host name "IIS_Host" ip-address 192.168.50.10 color "ORANGE" -s id.txt
"%varMgmt_cli%" add host name "labs-proxy" ip-address 194.29.36.43 color "ORANGE" -s id.txt
"%varMgmt_cli%" add host name "Finance Server" ip-address 192.168.13.101 color "GREEN" -s id.txt
"%varMgmt_cli%" add host name "File Server" ip-address 192.168.33.112 color "GREEN" -s id.txt
"%varMgmt_cli%" add host name "HR Server" ip-address 192.168.33.113 color "GREEN" -s id.txt
"%varMgmt_cli%" add host name "Marketing Server" ip-address 192.168.33.114 color "GREEN" -s id.txt
"%varMgmt_cli%" add host name "Sales Server" ip-address 192.168.33.115 color "GREEN" -s id.txt
"%varMgmt_cli%" add host name "Mail Server" ip-address 192.168.33.117 color "ORANGE" -s id.txt
"%varMgmt_cli%" add host name "Exchange" ip-address 192.168.32.110 color "GREEN" -s id.txt
"%varMgmt_cli%" add host name "COM AntiSPAM" ip-address 192.168.32.111 color "ORANGE" -s id.txt
"%varMgmt_cli%" add host name "proxy 1231" ip-address 192.168.32.214 color "ORANGE" -s id.txt
"%varMgmt_cli%" add host name "BADIP" ip-address 192.67.32.212 color "RED" -s id.txt
"%varMgmt_cli%" add host name "Demo Station" ip-address 198.51.100.80 color "gold" -s id.txt
"%varMgmt_cli%" publish -s id.txt
echo # Add Networks
"%varMgmt_cli%" set session description "Add networks" new-name "creating network objects" -s id.txt
"%varMgmt_cli%" add network name "RnD Network" subnet 91.90.128.0 subnet-mask 255.255.255.0 color "RED" -s id.txt
"%varMgmt_cli%" add network name "Sales Network" subnet 192.168.50.0 subnet-mask 255.255.255.0 color "GREEN" -s id.txt
"%varMgmt_cli%" add network name "Finance Network" subnet 192.168.51.0 subnet-mask 255.255.255.0 color "BLUE" -s id.txt
"%varMgmt_cli%" add network name "HR Network" subnet 172.23.51.0 subnet-mask 255.255.255.0 color "CYAN" -s id.txt
"%varMgmt_cli%" publish -s id.txt
echo # Add Zones
"%varMgmt_cli%" set session description "Add zones" new-name "creating zone objects" -s id.txt
"%varMgmt_cli%" add-security-zone name "Finance" color "BLUE" -s id.txt
"%varMgmt_cli%" add-security-zone name "HRWiFi" color "CYAN" -s id.txt
"%varMgmt_cli%" publish -s id.txt
echo # Add Service-TCP
"%varMgmt_cli%" set session description "Add services" new-name "creating custom servuices objects" -s id.txt
"%varMgmt_cli%" add service-tcp name "Evil-TCP-Service1" port 666 keep-connections-open-after-policy-installation false session-timeout 0 match-for-any true sync-connections-on-cluster true aggressive-aging.enable true -s id.txt
echo # Add Service-UDP
"%varMgmt_cli%" add service-udp name "Evil-UDP-Service1" port 999 keep-connections-open-after-policy-installation false session-timeout 0 match-for-any true sync-connections-on-cluster true aggressive-aging.enable true -s id.txt
"%varMgmt_cli%" publish -s id.txt
echo # Add access roles
"%varMgmt_cli%" set session description "Add access roles" new-name "creating access role objects" -s id.txt
"%varMgmt_cli%" add-access-role name "System Admins" -s id.txt
"%varMgmt_cli%" add-access-role name "Sales Operations" -s id.txt
"%varMgmt_cli%" publish -s id.txt
echo # adding network object group
"%varMgmt_cli%" set session description "Add net groups" new-name "creating network groups" -s id.txt
"%varMgmt_cli%" add group name "SecurityGateways" color "BLACK" members.1 "Oslo-sg01" members.2 "Stockholm-sg01" members.3 "Helsinki-sg01" -s id.txt
rem ###
rem #Not possible to roup zone object right now, will uncommen this once it is possible //jimo 2016-08-19
rem #"%varMgmt_cli%" add group name "InternalZones" color "BLACK" members.1 "Finance" members.2 "HR WiFi" -s id.txt
rem ###
"%varMgmt_cli%" add group name "InternalZones" color "BLACK" members.1 "Finance Network" members.2 "HR Network" -s id.txt
"%varMgmt_cli%" add group name "DMZ Servers" color "ORANGE" members.1 "DNS Server" members.2 "Web Server" members.3 "FTP Server" -s id.txt
"%varMgmt_cli%" publish -s id.txt
echo # adding service object group
"%varMgmt_cli%" set session description "Add services groups" new-name "creating services groups" -s id.txt
"%varMgmt_cli%" add service-group name "Internet Protocols" color "BLACK" members.1 "HTTP_and_HTTPS_proxy" members.2 "http" members.3 "https" -s id.txt
"%varMgmt_cli%" add service-group name "Management Protocols" color "BLACK" members.1 "https" members.2 "ssh" -s id.txt
"%varMgmt_cli%" publish -s id.txt
echo # Create Policy package "SimpleOpenPolicy" with "SimpleOpenPolicy Network" layer
"%varMgmt_cli%" set session description "Create Simple open policy" new-name "Create Policy package SimpleOpenPolicy with SimpleOpenPolicy Network layer" -s id.txt
"%varMgmt_cli%" add package name "SimpleOpenPolicy" access true desktop-security false qos false threat-prevention false installation-targets "Helsinki-sg01" -s id.txt
"%varMgmt_cli%" publish -s id.txt
echo # Fill "SimpleOpenPolicy Network" layer with rules
"%varMgmt_cli%" set session description "Fill SimpleOpenPolicy" new-name "adding rules" -s id.txt
"%varMgmt_cli%" add access-rule layer "SimpleOpenPolicy Network" name "Admin firewall access" action "Accept" position top source "Demo Station" destination any track "none" -s id.txt
"%varMgmt_cli%" publish -s id.txt
echo # Create Policy package AUnifiedPolicy with "AUnifiedPolicy Network" Layer
"%varMgmt_cli%" set session description "Create AUnifiedPolicy" new-name "Create Policy package AUnifiedPolicy with AUnifiedPolicy Network layer" -s id.txt
"%varMgmt_cli%" add package name "AUnifiedPolicy" color gold access "true" desktop-security "false" qos "false" threat-prevention "true" -s id.txt
"%varMgmt_cli%" publish -s id.txt
echo # Create "Sales Operations" Layer activated APPI and Data awareness
"%varMgmt_cli%" set session description "Create sales Operations Layer" new-name "Create sales Operations layer" -s id.txt
"%varMgmt_cli%" add access-layer name "Sales Operations" applications-and-url-filtering "true" data-awareness "true" -s id.txt
"%varMgmt_cli%" publish -s id.txt
echo # Fill "Sales Operations" Layer with rules
"%varMgmt_cli%" set session description "Fill sales Operations Layer" new-name "Fill sales Operations with rules" -s id.txt
"%varMgmt_cli%" set access-rule layer "Sales Operations" rule-number 1 new-name "Cleanup Rule" -s id.txt
"%varMgmt_cli%" add access-rule layer "Sales Operations" name "Allow Sales Operations to access Share Portal" destination "Internet" action "accept" service "Office365" data "Document File" position.top "Sales Operations" -s id.txt
"%varMgmt_cli%" publish -s id.txt
echo # Create "Compliance" layer
"%varMgmt_cli%" set session description "Create Compliance Layer" new-name "Create Compliances layer" -s id.txt
"%varMgmt_cli%" add access-layer name "Compliance" applications-and-url-filtering "true" data-awareness "true" -s id.txt
"%varMgmt_cli%" publish -s id.txt
echo # Fill "Compliance" Layer with rules
"%varMgmt_cli%" set session description "Fill Compliance Layer" new-name "Fill Compliances layer with rules" -s id.txt
"%varMgmt_cli%" set access-rule layer "Compliance" rule-number 1 new-name "Allow all traffic that did not violate compliance" action "Accept" -s id.txt
"%varMgmt_cli%" add access-rule layer "Compliance" name "Uncategorised applications are not allowed for all corporate users - Ask User" action "Ask" position.top "Compliance" destination "Internet" service "Uncategorized" -s id.txt
"%varMgmt_cli%" add access-rule layer "Compliance" name "Source Code is confidential and must not leave the organization" action "Drop" position.top "Compliance" source "InternalZones" destination.1 "Internet" destination.2 "ExternalZone" data.1 "Source Code - Perl" data.2 "Source Code - Python" data.3 "Source Code - C Sharp" -s id.txt
"%varMgmt_cli%" publish -s id.txt
echo # Insert "Compliance" layer as ordered layer in "AUnifiedPolicy" package
"%varMgmt_cli%" set session description "Add compliance layer to AUnifiedPolicy" new-name "Add layer in ordered mode in policy" -s id.txt
"%varMgmt_cli%" set package name "AUnifiedPolicy" access-layers.add.1.name "Compliance" access-layers.add.1.position "2" -s id.txt
"%varMgmt_cli%" publish -s id.txt
echo # Prepare "AUnifiedPolicy Network" Layer in "AUnifiedPolicy" policy package by adding APPI column, DLP column and renaming "cleanup rule"
"%varMgmt_cli%" set session description "Activate APPI and Content blade in AUnifiedPolicy" new-name "Activate blades in layer" -s id.txt
"%varMgmt_cli%" set access-layer name "AUnifiedPolicy Network" applications-and-url-filtering "true" data-awareness "true" -s id.txt
"%varMgmt_cli%" set access-rule name "Cleanup rule" layer "AUnifiedPolicy Network" new-name "delete_me" -s id.txt
"%varMgmt_cli%" publish -s id.txt
echo # Fill "AUnifiedPolicy Network" Layer with rules
echo # add section "MGMT access Single Management Nordics-sm01""
"%varMgmt_cli%" set session description "Fill AUnifiedPolicy" new-name "adding rules" -s id.txt
"%varMgmt_cli%" add access-section name "MGMT access Security Management Nordics-sm01" position.bottom "AUnifiedPolicy Network" layer "AUnifiedPolicy Network" -s id.txt
"%varMgmt_cli%" add access-rule layer "AUnifiedPolicy Network" name "Enable open shell and open webui from management" action "Accept" position.bottom "AUnifiedPolicy Network" source "Nordics-sm01" destination "SecurityGateways" service "Management Protocols" -s id.txt
"%varMgmt_cli%" add access-rule layer "AUnifiedPolicy Network" name "Stealth rule" action "Drop" position.bottom "AUnifiedPolicy Network" destination.1 "Nordics-sm01" destination.2 "SecurityGateways" -s id.txt
"%varMgmt_cli%" publish -s id.txt
echo # add section "Internet Access"
"%varMgmt_cli%" set session description "Fill AUnifiedPolicy" new-name "adding rules" -s id.txt
"%varMgmt_cli%" add access-section name "Internet Access" position.bottom "AUnifiedPolicy Network" layer "AUnifiedPolicy Network" -s id.txt
"%varMgmt_cli%" add access-rule layer "AUnifiedPolicy Network" name "Drop high risk applications" service.1 "High Risk" service.2 "Critical Risk" install-on.1 "Stockholm-sg01" install-on.2 "Oslo-sg01" install-on.3 "Helsinki-sg01" action "Drop" position.bottom "Internet Access" -s id.txt
"%varMgmt_cli%" publish -s id.txt
echo # Insert "Sales Operations" Layer as a inline layer
"%varMgmt_cli%" set session description "Fill AUnifiedPolicy" new-name "adding rules" -s id.txt
"%varMgmt_cli%" add access-rule layer "AUnifiedPolicy Network" name "Sales Operations" source "Sales Operations" action "Apply Layer" inline-layer "Sales Operations" position.bottom "Internet Access" -s id.txt
"%varMgmt_cli%" publish -s id.txt
echo # Continue fill "AUnifiedPolicy Network" layer with rules under "Internet Access" section
"%varMgmt_cli%" set session description "Fill AUnifiedPolicy" new-name "adding rules" -s id.txt
"%varMgmt_cli%" add access-rule layer "AUnifiedPolicy Network" name "File Sharing - user check" destination "Internet" action "ask" service "File Storage and Sharing" position.bottom "Internet Access" -s id.txt
"%varMgmt_cli%" add access-rule layer "AUnifiedPolicy Network" name "limit social applications to off hours" service "Social Networking" action "Ask" position.bottom "Internet Access" destination "Internet" -s id.txt
"%varMgmt_cli%" add access-rule layer "AUnifiedPolicy Network" name "Enable internet access" action "Accept" position.bottom "Internet Access" source "InternalZones" destination "Internet" service "Internet Protocols" -s id.txt
"%varMgmt_cli%" publish -s id.txt
echo # Add section "VPN Site2Site"
"%varMgmt_cli%" set session description "Fill AUnifiedPolicy" new-name "adding rules" -s id.txt
"%varMgmt_cli%" add access-section name "VPN Site2Site" position.bottom "AUnifiedPolicy Network" layer "AUnifiedPolicy Network" -s id.txt
"%varMgmt_cli%" add access-rule layer "AUnifiedPolicy Network" name "allow VPN access to site1 and site2 internal network from all internal zones" action "Accept" position.bottom "VPN Site2Site" source "InternalZones" vpn "All_GwToGw" -s id.txt
"%varMgmt_cli%" publish -s id.txt
echo # Add section "Internal Server access"
"%varMgmt_cli%" set session description "Fill AUnifiedPolicy" new-name "adding rules" -s id.txt
"%varMgmt_cli%" add access-section name "Internal Server access" position.bottom "AUnifiedPolicy Network" layer "AUnifiedPolicy Network" -s id.txt
"%varMgmt_cli%" add access-rule layer "AUnifiedPolicy Network" name "Give full access to system administrators" action "Accept" position.bottom "Internal Server access" source "System Admins" destination "DMZ Servers" -s id.txt
"%varMgmt_cli%" add access-rule layer "AUnifiedPolicy Network" name "Give web access to servers" action "Accept" position.bottom "Internal Server access" destination "DMZ Servers" service "Internet Protocols" -s id.txt
"%varMgmt_cli%" publish -s id.txt
echo # Add section "Cleanup"
"%varMgmt_cli%" set session description "Fill AUnifiedPolicy" new-name "adding rules" -s id.txt
"%varMgmt_cli%" add access-section name "Cleanup" position.bottom "AUnifiedPolicy Network" layer "AUnifiedPolicy Network" -s id.txt
"%varMgmt_cli%" add access-rule layer "AUnifiedPolicy Network" name "Cleanup rule" action "Drop" position.bottom "Cleanup" -s id.txt
"%varMgmt_cli%" publish -s id.txt
echo remove the old renamed cleanup rule
"%varMgmt_cli%" set session description "remove old cleanup from AUnifiedPolicy" new-name "remove old cleanup" -s id.txt
"%varMgmt_cli%" delete access-rule name "delete_me" layer "AUnifiedPolicy Network" -s id.txt
echo #publish and logout
"%varMgmt_cli%" publish -s id.txt
"%varMgmt_cli%" logout -s id.txt
rem ################ Fill Central-Europe domain ###########################################
echo "Populate Central-Europe domain with objects and rules"
"%varMgmt_cli%" -m %varMds% login user "Walter" password "1234" domain "Central-Europe" > id.txt
"%varMgmt_cli%" set session new-name "Create rule base" description "Populate Central-Europe domain with objects and rules" -s id.txt
"%varMgmt_cli%" add simple-gateway name "EuropeBranchGw" comments "Europe Office gateway" ip-address 192.0.2.100 firewall true anti-bot true anti-virus true application-control true threat-emulation true url-filtering true ips true vpn true interfaces.1.name "eth0" interfaces.1.ip-address 192.0.2.100 interfaces.1.mask-length 24 interfaces.1.topology "EXTERNAL" interfaces.2.name "eth1" interfaces.2.ip-address 203.0.113.1 interfaces.2.mask-length 25 interfaces.2.topology "INTERNAL" interfaces.2.topology-settings.ip-address-behind-this-interface "LOCAL_NETWORK" tags '["Europe_gw"]' -s id.txt
"%varMgmt_cli%" add simple-gateway name "HQgw" comments "Main Office gateway" ip-address 192.0.2.200 firewall true anti-bot true anti-virus true application-control true threat-emulation true ips true url-filtering true vpn true interfaces.1.name "eth0" interfaces.1.ip-address 192.0.2.200 interfaces.1.mask-length 24 interfaces.1.topology "EXTERNAL" interfaces.2.name "eth1" interfaces.2.ip-address 198.51.100.5 interfaces.2.mask-length 25 interfaces.2.topology "INTERNAL" interfaces.2.topology-settings.ip-address-behind-this-interface "LOCAL_NETWORK" interfaces.3.name "eth2" interfaces.3.ip-address 198.51.100.129 interfaces.3.mask-length 25 interfaces.3.topology "INTERNAL" interfaces.3.topology-settings.ip-address-behind-this-interface "LOCAL_NETWORK" tags '["Internal_gw"]' -s id.txt
"%varMgmt_cli%" publish -s id.txt
"%varMgmt_cli%" add simple-gateway name "Corporate-GW" comments "First Office gateway" ip-address 198.51.100.4 firewall true application-control true anti-bot true anti-virus true vpn true url-filtering true data-awareness true ips true threat-emulation true version R80 interfaces.1.name "eth0" interfaces.1.ipv4-address "198.51.100.5" interfaces.1.ipv4-network-mask "255.255.255.0" interfaces.1.anti-spoofing false interfaces.1.topology "EXTERNAL" interfaces.2.name "eth1" interfaces.2.ipv4-address "198.51.100.6" interfaces.2.ipv4-network-mask "255.255.255.0" interfaces.2.anti-spoofing false interfaces.2.topology "INTERNAL" interfaces.2.topology-settings.ip-address-behind-this-interface "LOCAL_NETWORK" interfaces.3.name "eth2" interfaces.3.ipv4-address "198.51.100.7" interfaces.3.ipv4-network-mask "255.255.255.0" interfaces.3.anti-spoofing false interfaces.3.topology "INTERNAL" interfaces.3.topology-settings.ip-address-behind-this-interface "LOCAL_NETWORK" interfaces.4.name "eth3" interfaces.4.ipv4-address "198.51.100.8" interfaces.4.ipv4-network-mask "255.255.255.0" interfaces.4.anti-spoofing false interfaces.4.topology "INTERNAL" interfaces.4.topology-settings.ip-address-behind-this-interface "LOCAL_NETWORK" tags '["Internal_gw"]' -s id.txt
"%varMgmt_cli%" add simple-gateway name "BranchOffice" comments "Second office gateway" ip-address 198.51.100.0 firewall true application-control true vpn true version R77.30 interfaces.1.name "eth0" interfaces.1.ipv4-address "198.51.100.1" interfaces.1.ipv4-network-mask "255.255.255.0" interfaces.1.anti-spoofing false interfaces.1.topology "EXTERNAL" interfaces.2.name "eth1" interfaces.2.ipv4-address "198.51.100.2" interfaces.2.ipv4-network-mask "255.255.255.0" interfaces.2.anti-spoofing false interfaces.2.topology "INTERNAL" interfaces.2.topology-settings.ip-address-behind-this-interface "LOCAL_NETWORK" tags '["External_gw"]' -s id.txt
"%varMgmt_cli%" add simple-gateway name "RemoteBranchGw" comments "RemoteBranchGw" ip-address 198.51.100.120 firewall true ips true interfaces.1.name "eth0" interfaces.1.ip-address 98.51.100.120 interfaces.1.mask-length 24 interfaces.1.topology "EXTERNAL" interfaces.2.name "eth1" interfaces.2.ip-address 172.0.113.112 interfaces.2.mask-length 25 interfaces.2.topology "INTERNAL" interfaces.2.topology-settings.ip-address-behind-this-interface "LOCAL_NETWORK" tags '["External_gw"]' -s id.txt
"%varMgmt_cli%" add simple-gateway name "ThreatEmulationDevice" comments "Threat Emulation" ip-address 192.0.111.13 firewall true threat-emulation true interfaces.1.name "eth0" interfaces.1.ip-address 192.0.111.13 interfaces.1.mask-length 24 interfaces.1.topology "EXTERNAL" interfaces.2.name "eth1" interfaces.2.ip-address 172.0.1.113 interfaces.2.mask-length 25 interfaces.2.topology "INTERNAL" interfaces.2.topology-settings.ip-address-behind-this-interface "LOCAL_NETWORK" tags '["ThreatEmulation_gw"]' -s id.txt
"%varMgmt_cli%" set session description "Add R80.10 gateways" new-name "Demo add gateways - Step 2" -s id.txt
"%varMgmt_cli%" publish -s id.txt
"%varMgmt_cli%" add simple-gateway name "Remote-1-gw" version "R75.40" os-name "SecurePlatform" comments "Remote-1-gw" ip-address 192.0.22.1 firewall true ips true vpn true interfaces.1.name "eth0" interfaces.1.ip-address 192.0.22.1 interfaces.1.mask-length 24 interfaces.1.topology "EXTERNAL" interfaces.2.name "eth1" interfaces.2.ip-address 172.0.113.1 interfaces.2.mask-length 25 interfaces.2.topology "INTERNAL" interfaces.2.topology-settings.ip-address-behind-this-interface "LOCAL_NETWORK" tags '["External_gw"]' -s id.txt
"%varMgmt_cli%" add simple-gateway name "Remote-2-gw" version "R75.40" os-name "Windows" comments "Remote-2-gw" ip-address 192.0.23.1 firewall true ips true vpn true interfaces.1.name "eth0" interfaces.1.ip-address 192.0.3.1 interfaces.1.mask-length 24 interfaces.1.topology "EXTERNAL" interfaces.2.name "eth1" interfaces.2.ip-address 172.0.113.1 interfaces.2.mask-length 25 interfaces.2.topology "INTERNAL" interfaces.2.topology-settings.ip-address-behind-this-interface "LOCAL_NETWORK" tags '["External_gw"]' -s id.txt
"%varMgmt_cli%" add simple-gateway name "Remote-3-gw" version "R77.20" comments "Remote-3-gw" ip-address 192.0.24.1 firewall true interfaces.1.name "eth0" interfaces.1.ip-address 192.0.4.1 interfaces.1.mask-length 24 interfaces.1.topology "EXTERNAL" interfaces.2.name "eth1" interfaces.2.ip-address 172.0.1.1 interfaces.2.mask-length 25 interfaces.2.topology "INTERNAL" interfaces.2.topology-settings.ip-address-behind-this-interface "LOCAL_NETWORK" tags '["External_gw"]' -s id.txt
"%varMgmt_cli%" add simple-gateway name "Remote-4-gw" version "R75.40" comments "Remote-4-gw" ip-address 192.0.25.1 firewall true ips true vpn true interfaces.1.name "eth0" interfaces.1.ip-address 192.0.5.1 interfaces.1.mask-length 24 interfaces.1.topology "EXTERNAL" interfaces.2.name "eth1" interfaces.2.ip-address 172.0.2.1 interfaces.2.mask-length 25 interfaces.2.topology "INTERNAL" interfaces.2.topology-settings.ip-address-behind-this-interface "LOCAL_NETWORK" tags '["External_gw"]' -s id.txt
"%varMgmt_cli%" add simple-gateway name "Remote-5-gw" version "R77.20" comments "Remote-5-gw" ip-address 192.0.26.1 firewall true interfaces.1.name "eth0" interfaces.1.ip-address 192.0.6.1 interfaces.1.mask-length 24 interfaces.1.topology "EXTERNAL" interfaces.2.name "eth1" interfaces.2.ip-address 172.0.3.1 interfaces.2.mask-length 25 interfaces.2.topology "INTERNAL" interfaces.2.topology-settings.ip-address-behind-this-interface "LOCAL_NETWORK" tags '["External_gw"]' -s id.txt
"%varMgmt_cli%" set session description "Add remote gateways" new-name "Add Remote gateways" -s id.txt
"%varMgmt_cli%" publish -s id.txt
"%varMgmt_cli%" set session description "Add tags and Security Zone" new-name "Add tags and Security Zone" -s id.txt
"%varMgmt_cli%" add tag name "Internal_gw" color red -s id.txt
"%varMgmt_cli%" add tag name "External_gw" color yellow -s id.txt
"%varMgmt_cli%" add tag name "DMZ_gw" color "dark orange 3" -s id.txt
"%varMgmt_cli%" add tag name "Europe_gw" color "dark orchid" -s id.txt
"%varMgmt_cli%" add tag name "ThreatEmulation_gw" color blue -s id.txt
"%varMgmt_cli%" add-security-zone name "Finance" -s id.txt
"%varMgmt_cli%" publish -s id.txt
"%varMgmt_cli%" set session description "Add Groups" new-name "Add Groups" -s id.txt
"%varMgmt_cli%" add group name "Gateways_Group" color "BLACK" members "[\"HQgw\", \"EuropeBranchGw\"]" -s id.txt
"%varMgmt_cli%" add group name "InternalZones" color "BLACK" members "[]" -s id.txt
"%varMgmt_cli%" add group name "DMZ Servers" color "BLACK" members "[]" -s id.txt
"%varMgmt_cli%" publish -s id.txt
echo "create hosts"
"%varMgmt_cli%" set session description "Add Policy" new-name "New policy package with rules and objects" -s id.txt
"%varMgmt_cli%" add host name "DNS Server" ip-address 198.51.100.9 -s id.txt
"%varMgmt_cli%" add host name "ERP Server" ip-address 198.51.100.10 -s id.txt
"%varMgmt_cli%" add host name "Exchange" ip-address 198.51.100.11 -s id.txt
"%varMgmt_cli%" add host name "FTP_Int" ip-address 198.51.100.12 -s id.txt
"%varMgmt_cli%" add host name "Web Server" ip-address 198.51.100.13 -s id.txt
"%varMgmt_cli%" add host name "MTA" ip-address 198.51.100.14 -s id.txt
echo "create networks"
"%varMgmt_cli%" add network name "HR LAN" subnet 198.51.100.15 subnet-mask 255.255.255.255 -s id.txt
"%varMgmt_cli%" add network name "Sales LAN" subnet 198.51.100.16 subnet-mask 255.255.255.255 -s id.txt
"%varMgmt_cli%" add network name "DMZ LAN" subnet 198.51.100.17 subnet-mask 255.255.255.255 -s id.txt
"%varMgmt_cli%" add network name "Branch Office LAN" subnet 198.51.100.18 subnet-mask 255.255.255.255 -s id.txt
"%varMgmt_cli%" add network name "Data Center LAN" subnet 198.51.100.19 subnet-mask 255.255.255.255 -s id.txt
echo "create services"
"%varMgmt_cli%" add service-tcp name "Http_9090" port 9090 -s id.txt
echo "create time"
"%varMgmt_cli%" add time name "Temp Access" start-now "true" end.date "12-Dec-2015" end.time "21:25" end-never "false" recurrence.pattern "Daily" -s id.txt
echo "create network group"
"%varMgmt_cli%" add group name "Corporate LANs" members "[\"HR LAN\", \"Sales LAN\"]" -s id.txt
echo "create application/site"
"%varMgmt_cli%" add application-site name "Blocked URLs" primary-category "Custom_Application_Site" url-list.1 "www.block*.*" urls-defined-as-regular-expression true -s id.txt
"%varMgmt_cli%" add application-site name "Report Portal" primary-category "Custom_Application_Site" url-list.1 "*.portal" urls-defined-as-regular-expression false -s id.txt
echo "create communities"
"%varMgmt_cli%" add vpn-community-meshed name "Site2Site" gateways "[\"BranchOffice\", \"Corporate-GW\"]" -s id.txt
echo "create application group"
"%varMgmt_cli%" add application-site-group name "Inappropriate Sites" members.1 "Child Abuse" members.2 "High Risk" members.3 "Spyware / Malicious Sites" members.4 "Gambling" -s id.txt
echo "create service group"
"%varMgmt_cli%" add service-group name "Manage Services" members.1 "GoToMyPC" -s id.txt
"%varMgmt_cli%" add service-group name "Internet Services" members.1 "HTTPS_proxy" members.2 "HTTP_proxy" members.3 "IMAP-SSL" members.4 "POP3S" members.5 "http" members.6 "https" -s id.txt
echo "create access roles"
"%varMgmt_cli%" add access-role name "Admins" networks "any" users "any" machines "any" remote-access-clients "any" -s id.txt
"%varMgmt_cli%" add access-role name "Finance User" networks "any" users "any" machines "any" remote-access-clients "any" -s id.txt
"%varMgmt_cli%" add access-role name "HR" networks "any" users "any" machines "any" remote-access-clients "any" -s id.txt
"%varMgmt_cli%" add access-role name "IT Department" networks "any" users "any" machines "any" remote-access-clients "any" -s id.txt
"%varMgmt_cli%" add access-role name "Sales" networks "any" users "any" machines "any" remote-access-clients "any" -s id.txt
"%varMgmt_cli%" add access-role name "Remote Access Users" networks "any" users "any" machines "any" remote-access-clients "any" -s id.txt
rem ################ Create Layers ###########################################
echo "create layers"
"%varMgmt_cli%" add access-layer name "Web Control" applications-and-url-filtering true data-awareness true mobile-access true -s id.txt
"%varMgmt_cli%" add access-layer name "Data Center Layer" applications-and-url-filtering true data-awareness true mobile-access true -s id.txt
"%varMgmt_cli%" add access-layer name "Guest Exception Layer" applications-and-url-filtering true data-awareness true -s id.txt
rem ######################################################################################
rem ################### Add Rules to "Web Control" Layer #################################
echo "add rules to 'Web Control Layer"
"%varMgmt_cli%" add access-rule layer "Web Control" name "DNS server should have access to" action accept position top source "[\"DNS Server\"]" destination "[\"ExternalZone\"]" service.1 "dns" track log -s id.txt
"%varMgmt_cli%" add access-rule layer "Web Control" name "Block abuse/ high risk applications" action drop position bottom source "[\"Corporate LANs\", \"Branch Office LAN\"]" destination "[\"Internet\"]" service.1 "Inappropriate Sites" user-check.interaction "Blocked Message - Access Control" track log -s id.txt
"%varMgmt_cli%" add access-rule layer "Web Control" name "HR can access to social network applications" action inform position bottom source "[\"HR\"]" destination "[\"Internet\"]" service.1 "Facebook" service.2 "Twitter" service.3 "LinkedIn" user-check.interaction "Access Approval" track log -s id.txt
"%varMgmt_cli%" add access-rule layer "Web Control" name "All employees can access YouTube for work purposes" action ask position bottom source "[\"Corporate LANs\", \"Branch Office LAN\"]" destination "[\"Internet\"]" service.1 "YouTube" service.2 "Vimeo" user-check.interaction "Company Policy" track log -s id.txt
"%varMgmt_cli%" add access-rule layer "Web Control" name "Block specific URLs" action drop position bottom destination "[\"Internet\"]" service.1 "Blocked URLs" track log -s id.txt
"%varMgmt_cli%" add access-rule layer "Web Control" name "Block specific categories for all employees" action drop position bottom source "[\"Corporate LANs\", \"Branch Office LAN\"]" destination "[\"Internet\"]" service.1 "Social Networking" service.2 "Streaming Media Protocols" service.3 "P2P File Sharing" user-check.interaction "Blocked Message - Access Control" track log -s id.txt
"%varMgmt_cli%" delete access-rule rule-number 2 layer "Web Control" -s id.txt
rem ##################################################################################
rem ################### Add Rules to "Data Center Layer" Layer #################################
echo "add rules to 'Data Center Layer' layer"
"%varMgmt_cli%" add access-rule layer "Data Center Layer" name "Mobile Access for Internal FS" action accept position top source "[\"Sales\"]" destination "[\"FTP_Int\"]" vpn "RemoteAccess" service.1 "ftp" data "[\"Document File\", \"Archive File\"]" track "detailed log" -s id.txt
"%varMgmt_cli%" add access-rule layer "Data Center Layer" name "Branch office should have VPN access to servers (ERP on ftp_22)" action accept position bottom source "[\"Branch Office LAN\"]" destination "[\"ERP Server\", \"Exchange\", \"FTP_Int\"]" vpn "Site2Site" service.1 "ftp" service.2 "smtp" service.3 "ftp" data "[\"Document File\", \"Media and Images\"]" track "detailed log" -s id.txt
"%varMgmt_cli%" add access-rule layer "Data Center Layer" name "ERP server being accessed on FTP via port 22" action accept position bottom source "[\"Corporate LANs\"]" destination "[\"ERP Server\"]" service.1 "ftp" data "[\"Document File\"]" track "detailed log" -s id.txt
"%varMgmt_cli%" add access-rule layer "Data Center Layer" name "Only Finance department has access to reports" action accept position bottom source "[\"Finance User\"]" destination "[\"ERP Server\"]" service.1 "Report Portal" track "detailed log" -s id.txt
"%varMgmt_cli%" add access-rule layer "Data Center Layer" name "Save DNS requests using our DNS" action accept position bottom source "[\"DMZZone\", \"InternalZone\"]" destination "[\"DNS Server\"]" service.1 "dns" track log -s id.txt
rem #remove default clean up rule
"%varMgmt_cli%" delete access-rule rule-number 2 layer "Data Center Layer" -s id.txt
rem ##################################################################################
rem ################### Add Rules to "Guest Exception Layer" Layer #################################
echo "add rules to 'Guest Exception Layer' layer"
"%varMgmt_cli%" add access-rule layer "Guest Exception Layer" name "Guests from Portal" action accept position top destination "[\"Internet\"]" service.1 "http" service.2 "https" track log action-settings.enable-identity-captive-portal true -s id.txt
rem #remove default clean up rule
"%varMgmt_cli%" delete access-rule rule-number 2 layer "Guest Exception Layer" -s id.txt
rem ##################################################################################
rem ########################### Edit Standard Layer ##################################
echo "edit Network layer blades"
"%varMgmt_cli%" set access-layer name "Network" applications-and-url-filtering true data-awareness true mobile-access true -s id.txt
rem #####################################################################################
rem ########################## Add Rules To Standard Network Layer #############################
echo "add rules to 'Network' layer"
rem #section 'Security Gateways Access'
"%varMgmt_cli%" add access-section name "Security Gateways Access" position.bottom Network layer Network -s id.txt
"%varMgmt_cli%" add access-rule layer Network name "Administrator Access to Gateways" action accept position.top "Security Gateways Access" source "[\"Admins\"]" destination "[\"Corporate-GW\"]" service.1 "Manage Services" -s id.txt
rem #"%varMgmt_cli%" add access-rule layer Network name "Noise rule" action drop position.bottom "Security Gateways Access" source "[\"InternalZone\"]" destination "[\"Corporate-GW\"]" service.1 "NBT" -s id.txt
"%varMgmt_cli%" add access-rule layer Network name "Stealth rule" action drop position.bottom "Security Gateways Access" destination "[\"Corporate-GW\"]" -s id.txt
rem #section 'VPN'
"%varMgmt_cli%" add access-section name "VPN" position.bottom Network layer Network -s id.txt
"%varMgmt_cli%" add access-rule layer Network name "Remote Access of employees to Data Center servers" action accept position.top "VPN" source "[\"Remote Access Users\"]" destination "[\"Data Center LAN\"]" vpn "RemoteAccess" -s id.txt
"%varMgmt_cli%" add access-rule layer Network name "VPN between Internal LANs and Branch office LAN" action accept position.bottom "VPN" source "[\"Corporate LANs\", \"Branch Office LAN\"]" destination "[\"Branch Office LAN\", \"Corporate LANs\"]" vpn "Site2Site" -s id.txt
rem #section 'Access To Internet'
"%varMgmt_cli%" add access-section name "Access To Internet" position.bottom Network layer Network -s id.txt
"%varMgmt_cli%" add access-rule layer "Network" position.top "Access To Internet" name "Access to Internet according to Web control policy" action "Apply Layer" inline-layer "Web Control" source "[\"InternalZone\"]" destination "[\"Internet\"]" -s id.txt
rem #section "DMZ"
"%varMgmt_cli%" add access-section name "DMZ" position.bottom Network layer Network -s id.txt
"%varMgmt_cli%" add access-rule layer Network name "Access to company's web server" action accept position.top "DMZ" source "[\"ExternalZone\"]" destination "[\"Web Server\"]" service.1 "Web Browser" track "detailed log" -s id.txt
"%varMgmt_cli%" add access-rule layer Network name "Allow corporate LANs to DMZ" action accept position.bottom "DMZ" source "[\"Corporate LANs\"]" destination "[\"DMZZone\"]" service.1 "https" service.2 "http" service.3 "ftp" track log -s id.txt
rem #section "Data Center Access"
"%varMgmt_cli%" add access-section name "Data Center Access" position.bottom Network layer Network -s id.txt
"%varMgmt_cli%" add access-rule layer "Network" position.top "Data Center Access" name "Policy for access to Data Center servers" action "Apply Layer" inline-layer "Data Center Layer" destination "[\"Data Center LAN\"]" -s id.txt
rem #section "Data Center Access" - TP blade
"%varMgmt_cli%" set threat-rule rule-number 1 layer "Standard Threat Prevention" new-name "Recommended Protections" -s id.txt
"%varMgmt_cli%" add threat-rule layer "Standard Threat Prevention" position "top" name "Data Center Protection" comments "" protected-scope "Data Center LAN" action "Strict" install-on "Policy Targets" -s id.txt
rem #section "Temporary Access Grant"
"%varMgmt_cli%" add access-section name "Temporary Access Grant" position.bottom Network layer Network -s id.txt
"%varMgmt_cli%" add access-rule layer "Network" position.top "Temporary Access Grant" name "Special policy for temp guest rules using wireless LAN" action "Apply Layer" inline-layer "Guest Exception Layer" source "[\"WirelessZone\"]" -s id.txt
rem #section CleanUp
"%varMgmt_cli%" add access-section name "Clean Up" position.bottom Network layer Network -s id.txt
"%varMgmt_cli%" add access-rule layer Network name "Clean up" action drop position.bottom "Clean Up" track log -s id.txt
rem #remove default clean up rule
"%varMgmt_cli%" delete access-rule rule-number 1 layer Network -s id.txt
rem ############################################################################
rem ####################### Create Branch_Office_Policy policy Package ###########################
echo "create Branch_Office_Policy policy package"
rem #create Branch_Office_Policy policy package
"%varMgmt_cli%" add package name "Branch_Office_Policy" access true threat-prevention true installation-targets "BranchOffice" -s id.txt
"%varMgmt_cli%" set package name "Branch_Office_Policy" access-layers.add.1.name "Web Control" access-layers.add.1.position 2 -s id.txt
rem ############################################################################
rem ################# Add rules to Branch_Office_Policy Network Layer ####################
echo "add rules to 'Branch_Office_Policy Network' layer"
rem #section GW access
"%varMgmt_cli%" add access-section name "GW Access" position.bottom "Branch_Office_Policy Network" layer "Branch_Office_Policy Network" -s id.txt
"%varMgmt_cli%" add access-rule layer "Branch_Office_Policy Network" name "Administrator Access to Gateways" action accept position.top "GW Access" source "[\"Admins\"]" destination "[\"BranchOffice\"]" service.1 "Manage Services" track log -s id.txt
"%varMgmt_cli%" add access-rule layer "Branch_Office_Policy Network" name "DHCP Server for the branch Office" action accept position.bottom "GW Access" destination "[\"BranchOffice\"]" service.1 "dhcp-request" track log -s id.txt
"%varMgmt_cli%" add access-rule layer "Branch_Office_Policy Network" name "Stealth rule" action drop position.bottom "GW Access" destination "[\"BranchOffice\"]" track log -s id.txt
rem #section VPN
"%varMgmt_cli%" add access-section name "VPN" position.bottom "Branch_Office_Policy Network" layer "Branch_Office_Policy Network" -s id.txt
"%varMgmt_cli%" add access-rule layer "Branch_Office_Policy Network" name "VPN between Internal LANs and Branch office LAN" action accept position.top "VPN" source "[\"Corporate LANs\", \"Branch Office LAN\"]" destination "[\"Branch Office LAN\", \"Corporate LANs\"]" vpn "Site2Site" track log -s id.txt
"%varMgmt_cli%" add access-rule layer "Branch_Office_Policy Network" name "Branch office should have VPN access to servers (ERP on ftp_22)" action accept position.bottom "VPN" source "[\"Branch Office LAN\"]" destination "[\"ERP Server\", \"FTP_Int\"]" service.1 "ftp" service.2 "ftp" vpn "Site2Site" track log -s id.txt
"%varMgmt_cli%" add access-rule layer "Branch_Office_Policy Network" name "Branch office should have VPN access to servers" action accept position.bottom "VPN" source "[\"Branch Office LAN\"]" destination "[\"Exchange\", \"DNS Server\"]" vpn "Site2Site" service.1 "http" service.2 "https" service.3 "dns" service.4 "smtp" track log -s id.txt
rem #section Internet Access
"%varMgmt_cli%" add access-section name "Internet Access" position.bottom "Branch_Office_Policy Network" layer "Branch_Office_Policy Network" -s id.txt
"%varMgmt_cli%" add access-rule layer "Branch_Office_Policy Network" name "Access to Internet according to Web control policy (next layer)" action accept position.top "Internet Access" source "[\"Branch Office LAN\"]" service.1 "Internet Services" track log -s id.txt
rem #section Clean Up
"%varMgmt_cli%" add access-section name "Clean Up" position.bottom "Branch_Office_Policy Network" layer "Branch_Office_Policy Network" -s id.txt
"%varMgmt_cli%" add access-rule layer "Branch_Office_Policy Network" name "clean up" action drop position.bottom "Clean Up" -s id.txt
rem #remove default cleanup rule
"%varMgmt_cli%" delete access-rule rule-number 1 layer "Branch_Office_Policy Network" -s id.txt
rem #####################################################################
rem ############# change package names ###########################
echo "change policy package names"
"%varMgmt_cli%" set package name "Standard" new-name "Corporate_Policy" -s id.txt
"%varMgmt_cli%" set package name "Corporate_Policy" installation-targets "Corporate-GW" -s id.txt
rem ###############################################################
"%varMgmt_cli%" set session description "Add Corporate_Policy" new-name "Demo add policy package" -s id.txt
"%varMgmt_cli%" publish -s id.txt
rem #### create host , add new rule and publish( in favour install statuses object)
"%varMgmt_cli%" add host name "FTP_Ext" ip-address 2.3.2.2 -s id.txt
"%varMgmt_cli%" add access-rule layer Network name "Customers to ftp servers" action accept position 8 source "[\"ExternalZone\"]" destination "[\"FTP_Ext\"]" service.1 "ftp" data "[\"Archive File\"]" track "detailed log" -s id.txt
"%varMgmt_cli%" set session description "Add ftp rule to Corporate_Policy" new-name "Demo rule policy package" -s id.txt
"%varMgmt_cli%" publish -s id.txt
rem ##### add new rule and publish( in favour install statuses object)
"%varMgmt_cli%" add access-rule layer "Guest Exception Layer" name "Temp rule: Board Presentation" action accept position bottom destination "[\"FTP_Int\"]" service.1 "ftp" track log time "Temp Access" -s id.txt
"%varMgmt_cli%" set session description "Add ftp guest access" new-name "Demo guest rule" -s id.txt
"%varMgmt_cli%" publish -s id.txt
"%varMgmt_cli%" logout -s id.txt
rem #add rules history
"%varMgmt_cli%" -m %varMds% login user "Saul" password "1234" domain "Central-Europe" > id.txt
"%varMgmt_cli%" set access-rule layer Network name "Administrator Access to Gateways" action Reject source "[\"Sales\"]" destination "[\"Corporate-GW\"]" track log -s id.txt
"%varMgmt_cli%" set access-rule layer Network name "Stealth rule" track log -s id.txt
"%varMgmt_cli%" set access-rule layer Network name "Remote Access of employees to Data Center servers" track log -s id.txt
"%varMgmt_cli%" set access-rule layer Network name "VPN between Internal LANs and Branch office LAN" track log -s id.txt
"%varMgmt_cli%" set session description "Set rule Corporate_Policy" new-name "Demo rule Reject" -s id.txt
"%varMgmt_cli%" publish -s id.txt
"%varMgmt_cli%" set access-rule layer Network name "Administrator Access to Gateways" action "accept" source "[\"Admins\"]" destination "[\"Corporate-GW\"]" -s id.txt
"%varMgmt_cli%" set session description "Set accept rule Corporate_Policy" new-name "Demo rule accept" -s id.txt
"%varMgmt_cli%" publish -s id.txt
"%varMgmt_cli%" logout -s id.txt
goto :end
:end
echo "All done.."
Redundant Multi-Domain Server Script
@echo off
rem makeRedundantMDSDemo.bat create by jimo@checkpoint.com 2017-05-01
rem this batch file will provisioning a MDS demo with redundant domains.
rem Pre-requirements is to have two mds servers installed called mds-a and mds-b
goto :comment1
rem ###################### Skip this part and goto comment1#########################
set varMgmt_cli=C:\Backup\2017\Check Point\NGSM\R80.10\Pre-GA\Hugo1_394_T2\SmartConsole_Hugo1_394_T2\PROGRAM\mgmt_cli
set varMdsPriObject="mds-a"
set varMdsSecObject="mds-b"
set varMds="mds-a.lab.local"
set varMdsB="mds-b.lab.local"
set varUid="admin"
set varPwd="vpn123"
set varPrimds_range="192.168.233.11"
set varSecmds_range="192.168.233.21"
:comment1
set /p varMgmt_cli="Enter full path to mgmt_cli executable (for example c:\temp\mgmt_cli): "
set /p varMdsPriObject="Enter Check Point object name of Primary MDS (For example mds-a): "
set /p varMdsSecObject="Enter Check Point object name of Secondary MDS (For example mds-b: "
set /p varMds="Enter IP or hostname of primary MDS: "
set /p varMdsB="Enter IP or hostname of secondary MDS: "
set /p varUid="Enter username: "
set /p varPwd="Enter password: "
echo ""
echo "Three Domain management Servers will be created on the primary MDS: %varMdsPriObject%. Where the last digit in the ip address will range form 1-3"
echo "If you for exmaple enter 192.168.233.11 the first DMS will be deployd with IP 192.168.233.111 and the last DMS will be deployd with ip 192.168.233.113 "
set /p varPrimds_range="Enter the ip address to use for primary MDS DMS's: "
echo ""
echo "Three Domain management Servers will be created on the secondary MDS: %varMdsSecObject%. Where the last digit in the ip address will range form 1-3"
echo "If you for exmaple enter 192.168.233.21 the first DMS will be deployd with IP 192.168.233.211 and the last DMS will be deployd with ip 192.168.233.213 "
set /p varSecmds_range="Enter the ip address to use for secondary MDS DMS's: "
echo "Building demo enviroment....."
rem ################ Create Admins and Domains ###########################################
echo "Create admin user Skyler"
"%varMgmt_cli%" --unsafe-auto-accept true-m %varMds% login user "%varUid%" password "%varPwd%" domain "System Data" > id.txt
"%varMgmt_cli%" set session new-name "Create admin Skyler" description "Creating administrator Skyler to be used in the API calls to populate the demo database" -s id.txt
"%varMgmt_cli%" add-administrator name "Skyler" password "1234" must-change-password false multi-domain-profile "Multi-Domain Super User" -s id.txt
"%varMgmt_cli%" publish -s id.txt
"%varMgmt_cli%" logout -s id.txt
echo "Create admin users for Multi Domain using user Skyler"
"%varMgmt_cli%" -m %varMds% login user "Skyler" password "1234" domain "System Data" > id.txt
"%varMgmt_cli%" set session new-name "Create ACME Corp MDS Admins" description "Creating MDS administrators for ACME Corp" -s id.txt
"%varMgmt_cli%" add-administrator name "Walter" password "1234" must-change-password false multi-domain-profile "Multi-Domain Super User" -s id.txt
"%varMgmt_cli%" add-administrator name "Saul" password "1234" must-change-password false multi-domain-profile "Multi-Domain Super User" -s id.txt
"%varMgmt_cli%" add-administrator name "Jesse" password "1234" must-change-password false multi-domain-profile "Domain Level Only" -s id.txt
"%varMgmt_cli%" publish -s id.txt
echo "Build the domains for ACME Corp MDSM start with Nordics domain"
"%varMgmt_cli%" set session new-name "Create Nordics domain" description "Creating domain management server for the Nordics region" -s id.txt
"%varMgmt_cli%" add domain name "Nordics" servers.name "Nordics-sm01" servers.ip-address "%varPrimds_range%1" servers.multi-domain-server "%varMdsPriObject%" -s id.txt
"%varMgmt_cli%" publish -s id.txt
pause
"%varMgmt_cli%" set domain name "Nordics" servers.add.name "Nordics-sm02" servers.add.ip-address "%varSecmds_range%1" servers.add.multi-domain-server "%varMdsSecObject%" -s id.txt
"%varMgmt_cli%" set trusted-client name "AnyHost" domains-assignment.add "Nordics" -s id.txt
"%varMgmt_cli%" publish -s id.txt
"%varMgmt_cli%" logout -s id.txt
pause
echo "Create Central-Europe domain"
"%varMgmt_cli%" -m %varMds% login user "Walter" password "1234" domain "System Data" > id.txt
"%varMgmt_cli%" set session new-name "Create Central Europe domain" description "Creating domain management server for the Central Europe region" -s id.txt
"%varMgmt_cli%" add domain name "Central-Europe" servers.name "Central-Europe-sm01" servers.ip-address "%varPrimds_range%2" servers.multi-domain-server "%varMdsSecObject%" -s id.txt
"%varMgmt_cli%" publish -s id.txt
pause
"%varMgmt_cli%" set domain name "Central-Europe" servers.add.name "Central-Europe-sm02" servers.add.ip-address "%varSecmds_range%2" servers.add.multi-domain-server "%varMdsPriObject%" -s id.txt
"%varMgmt_cli%" set trusted-client name "AnyHost" domains-assignment.add "Central-Europe" -s id.txt
"%varMgmt_cli%" publish -s id.txt
"%varMgmt_cli%" logout -s id.txt
pause
echo "Create Southern-Europe domain"
"%varMgmt_cli%" -m %varMds% login user "Saul" password "1234" domain "System Data" > id.txt
"%varMgmt_cli%" set session new-name "Create Southern Europe domain" description "Creating domain management server for the Southern Europe region" -s id.txt
"%varMgmt_cli%" add domain name "Southern-Europe" servers.name "Southern-Europe-sm01" servers.ip-address "%varPrimds_range%3" servers.multi-domain-server "%varMdsPriObject%" -s id.txt
pause
"%varMgmt_cli%" set trusted-client name "AnyHost" domains-assignment.add "Southern-Europe" -s id.txt
"%varMgmt_cli%" publish -s id.txt
"%varMgmt_cli%" logout -s id.txt
echo "Create Northern-Europe domain"
"%varMgmt_cli%" -m %varMds% login user "Saul" password "1234" domain "System Data" > id.txt
"%varMgmt_cli%" set session new-name "Create Northern Europe domain" description "Creating domain management server for the Northern Europe region" -s id.txt
"%varMgmt_cli%" add domain name "Northern-Europe" servers.name "Northern-Europe-sm01" servers.ip-address "%varPrimds_range%4" servers.multi-domain-server "%varMdsSecObject%" -s id.txt
pause
"%varMgmt_cli%" set trusted-client name "AnyHost" domains-assignment.add "Northern-Europe" -s id.txt
"%varMgmt_cli%" publish -s id.txt
"%varMgmt_cli%" logout -s id.txt
pause
rem ################ Fill Nordics domain ###########################################
echo "Populate Nordics domain with objects and rules"
"%varMgmt_cli%" -m %varMds% login user "Skyler" password "1234" domain "Nordics" > id.txt
"%varMgmt_cli%" set session new-name "Create rule base" description "Populate Nordics domain with objects and rules" -s id.txt
"%varMgmt_cli%" add simple-gateway name "Stockholm-sg01" ip-address 192.0.0.40 version r80.10 one-time-password "vpn123" firewall true ips true vpn true -s id.txt
"%varMgmt_cli%" add simple-gateway name "Oslo-sg01" ip-address 192.0.2.30 version "r80.10" one-time-password "vpn123" firewall true ips true vpn true interfaces.1.name "eth0" interfaces.1.ip-address 192.0.2.30 interfaces.1.mask-length 24 interfaces.1.topology "EXTERNAL" interfaces.2.name "eth1" interfaces.2.ip-address 198.53.100.5 interfaces.2.mask-length 25 interfaces.2.topology "INTERNAL" interfaces.2.topology-settings.ip-address-behind-this-interface "LOCAL_NETWORK" interfaces.3.name "eth2" interfaces.3.ip-address 198.53.100.129 interfaces.3.mask-length 25 interfaces.3.topology "INTERNAL" interfaces.3.topology-settings.ip-address-behind-this-interface "LOCAL_NETWORK" -s id.txt
"%varMgmt_cli%" add simple-gateway name "Helsinki-sg01" ip-address 192.0.2.40 version "r75.40" one-time-password "vpn123" firewall true ips true vpn true interfaces.1.name "eth0" interfaces.1.ip-address 192.0.2.40 interfaces.1.mask-length 24 interfaces.1.topology "EXTERNAL" interfaces.2.name "eth1" interfaces.2.ip-address 198.54.100.5 interfaces.2.mask-length 25 interfaces.2.topology "INTERNAL" interfaces.2.topology-settings.ip-address-behind-this-interface "LOCAL_NETWORK" interfaces.3.name "eth2" interfaces.3.ip-address 198.54.100.129 interfaces.3.mask-length 25 interfaces.3.topology "INTERNAL" interfaces.3.topology-settings.ip-address-behind-this-interface "LOCAL_NETWORK" -s id.txt
"%varMgmt_cli%" add simple-gateway name "Copenhagen-sg01" ip-address 192.0.2.200 firewall true anti-bot true anti-virus true application-control true threat-emulation true ips true url-filtering true vpn true interfaces.1.name "eth0" interfaces.1.ip-address 192.0.2.200 interfaces.1.mask-length 24 interfaces.1.topology "EXTERNAL" interfaces.2.name "eth1" interfaces.2.ip-address 198.51.100.5 interfaces.2.mask-length 25 interfaces.2.topology "INTERNAL" interfaces.2.topology-settings.ip-address-behind-this-interface "LOCAL_NETWORK" interfaces.3.name "eth2" interfaces.3.ip-address 198.51.100.129 interfaces.3.mask-length 25 interfaces.3.topology "INTERNAL" interfaces.3.topology-settings.ip-address-behind-this-interface "LOCAL_NETWORK" -s id.txt
"%varMgmt_cli%" add simple-gateway name "SandBlastDevice" comments "Threat Emulation" ip-address 192.0.2.13 firewall true threat-emulation true interfaces.1.name "eth0" interfaces.1.ip-address 192.0.2.13 interfaces.1.mask-length 24 interfaces.1.topology "EXTERNAL" interfaces.2.name "eth1" interfaces.2.ip-address 198.0.1.113 interfaces.2.mask-length 25 interfaces.2.topology "INTERNAL" interfaces.2.topology-settings.ip-address-behind-this-interface "LOCAL_NETWORK" -s id.txt
echo # Add Hosts
"%varMgmt_cli%" set session description "Add hosts" new-name "creating host objects" -s id.txt
"%varMgmt_cli%" add host name "DNS Server" ip-address 198.53.100.130 color "ORANGE" -s id.txt
"%varMgmt_cli%" add host name "Web Server" ip-address 198.53.100.131 color "ORANGE" -s id.txt
"%varMgmt_cli%" add host name "FTP Server" ip-address 198.53.100.132 color "ORANGE" -s id.txt
"%varMgmt_cli%" add host name "IIS_Host" ip-address 192.168.50.10 color "ORANGE" -s id.txt
"%varMgmt_cli%" add host name "labs-proxy" ip-address 194.29.36.43 color "ORANGE" -s id.txt
"%varMgmt_cli%" add host name "Finance Server" ip-address 192.168.13.101 color "GREEN" -s id.txt
"%varMgmt_cli%" add host name "File Server" ip-address 192.168.33.112 color "GREEN" -s id.txt
"%varMgmt_cli%" add host name "HR Server" ip-address 192.168.33.113 color "GREEN" -s id.txt
"%varMgmt_cli%" add host name "Marketing Server" ip-address 192.168.33.114 color "GREEN" -s id.txt
"%varMgmt_cli%" add host name "Sales Server" ip-address 192.168.33.115 color "GREEN" -s id.txt
"%varMgmt_cli%" add host name "Mail Server" ip-address 192.168.33.117 color "ORANGE" -s id.txt
"%varMgmt_cli%" add host name "Exchange" ip-address 192.168.32.110 color "GREEN" -s id.txt
"%varMgmt_cli%" add host name "COM AntiSPAM" ip-address 192.168.32.111 color "ORANGE" -s id.txt
"%varMgmt_cli%" add host name "proxy 1231" ip-address 192.168.32.214 color "ORANGE" -s id.txt
"%varMgmt_cli%" add host name "BADIP" ip-address 192.67.32.212 color "RED" -s id.txt
"%varMgmt_cli%" add host name "Demo Station" ip-address 198.51.100.80 color "gold" -s id.txt
"%varMgmt_cli%" publish -s id.txt
echo # Add Networks
"%varMgmt_cli%" set session description "Add networks" new-name "creating network objects" -s id.txt
"%varMgmt_cli%" add network name "RnD Network" subnet 91.90.128.0 subnet-mask 255.255.255.0 color "RED" -s id.txt
"%varMgmt_cli%" add network name "Sales Network" subnet 192.168.50.0 subnet-mask 255.255.255.0 color "GREEN" -s id.txt
"%varMgmt_cli%" add network name "Finance Network" subnet 192.168.51.0 subnet-mask 255.255.255.0 color "BLUE" -s id.txt
"%varMgmt_cli%" add network name "HR Network" subnet 172.23.51.0 subnet-mask 255.255.255.0 color "CYAN" -s id.txt
"%varMgmt_cli%" publish -s id.txt
echo # Add Zones
"%varMgmt_cli%" set session description "Add zones" new-name "creating zone objects" -s id.txt
"%varMgmt_cli%" add-security-zone name "Finance" color "BLUE" -s id.txt
"%varMgmt_cli%" add-security-zone name "HRWiFi" color "CYAN" -s id.txt
"%varMgmt_cli%" publish -s id.txt
echo # Add Service-TCP
"%varMgmt_cli%" set session description "Add services" new-name "creating custom servuices objects" -s id.txt
"%varMgmt_cli%" add service-tcp name "Evil-TCP-Service1" port 666 keep-connections-open-after-policy-installation false session-timeout 0 match-for-any true sync-connections-on-cluster true aggressive-aging.enable true -s id.txt
echo # Add Service-UDP
"%varMgmt_cli%" add service-udp name "Evil-UDP-Service1" port 999 keep-connections-open-after-policy-installation false session-timeout 0 match-for-any true sync-connections-on-cluster true aggressive-aging.enable true -s id.txt
"%varMgmt_cli%" publish -s id.txt
echo # Add access roles
"%varMgmt_cli%" set session description "Add access roles" new-name "creating access role objects" -s id.txt
"%varMgmt_cli%" add-access-role name "System Admins" -s id.txt
"%varMgmt_cli%" add-access-role name "Sales Operations" -s id.txt
"%varMgmt_cli%" publish -s id.txt
echo # adding network object group
"%varMgmt_cli%" set session description "Add net groups" new-name "creating network groups" -s id.txt
"%varMgmt_cli%" add group name "SecurityGateways" color "BLACK" members.1 "Oslo-sg01" members.2 "Stockholm-sg01" members.3 "Helsinki-sg01" -s id.txt
rem ###
rem #Not possible to roup zone object right now, will uncommen this once it is possible //jimo 2016-08-19
rem #"%varMgmt_cli%" add group name "InternalZones" color "BLACK" members.1 "Finance" members.2 "HR WiFi" -s id.txt
rem ###
"%varMgmt_cli%" add group name "InternalZones" color "BLACK" members.1 "Finance Network" members.2 "HR Network" -s id.txt
"%varMgmt_cli%" add group name "DMZ Servers" color "ORANGE" members.1 "DNS Server" members.2 "Web Server" members.3 "FTP Server" -s id.txt
"%varMgmt_cli%" publish -s id.txt
echo # adding service object group
"%varMgmt_cli%" set session description "Add services groups" new-name "creating services groups" -s id.txt
"%varMgmt_cli%" add service-group name "Internet Protocols" color "BLACK" members.1 "HTTP_and_HTTPS_proxy" members.2 "http" members.3 "https" -s id.txt
"%varMgmt_cli%" add service-group name "Management Protocols" color "BLACK" members.1 "https" members.2 "ssh" -s id.txt
"%varMgmt_cli%" publish -s id.txt
echo # Create Policy package "SimpleOpenPolicy" with "SimpleOpenPolicy Network" layer
"%varMgmt_cli%" set session description "Create Simple open policy" new-name "Create Policy package SimpleOpenPolicy with SimpleOpenPolicy Network layer" -s id.txt
"%varMgmt_cli%" add package name "SimpleOpenPolicy" access true desktop-security false qos false threat-prevention false installation-targets "Helsinki-sg01" -s id.txt
"%varMgmt_cli%" publish -s id.txt
echo # Fill "SimpleOpenPolicy Network" layer with rules
"%varMgmt_cli%" set session description "Fill SimpleOpenPolicy" new-name "adding rules" -s id.txt
"%varMgmt_cli%" add access-rule layer "SimpleOpenPolicy Network" name "Admin firewall access" action "Accept" position top source "Demo Station" destination any track "none" -s id.txt
"%varMgmt_cli%" publish -s id.txt
echo # Create Policy package AUnifiedPolicy with "AUnifiedPolicy Network" Layer
"%varMgmt_cli%" set session description "Create AUnifiedPolicy" new-name "Create Policy package AUnifiedPolicy with AUnifiedPolicy Network layer" -s id.txt
"%varMgmt_cli%" add package name "AUnifiedPolicy" color gold access "true" desktop-security "false" qos "false" threat-prevention "true" -s id.txt
"%varMgmt_cli%" publish -s id.txt
echo # Create "Sales Operations" Layer activated APPI and Data awareness
"%varMgmt_cli%" set session description "Create sales Operations Layer" new-name "Create sales Operations layer" -s id.txt
"%varMgmt_cli%" add access-layer name "Sales Operations" applications-and-url-filtering "true" data-awareness "true" -s id.txt
"%varMgmt_cli%" publish -s id.txt
echo # Fill "Sales Operations" Layer with rules
"%varMgmt_cli%" set session description "Fill sales Operations Layer" new-name "Fill sales Operations with rules" -s id.txt
"%varMgmt_cli%" set access-rule layer "Sales Operations" rule-number 1 new-name "Cleanup Rule" -s id.txt
"%varMgmt_cli%" add access-rule layer "Sales Operations" name "Allow Sales Operations to access Share Portal" destination "Internet" action "accept" service "Office365" data "Document File" position.top "Sales Operations" -s id.txt
"%varMgmt_cli%" publish -s id.txt
echo # Create "Compliance" layer
"%varMgmt_cli%" set session description "Create Compliance Layer" new-name "Create Compliances layer" -s id.txt
"%varMgmt_cli%" add access-layer name "Compliance" applications-and-url-filtering "true" data-awareness "true" -s id.txt
"%varMgmt_cli%" publish -s id.txt
echo # Fill "Compliance" Layer with rules
"%varMgmt_cli%" set session description "Fill Compliance Layer" new-name "Fill Compliances layer with rules" -s id.txt
"%varMgmt_cli%" set access-rule layer "Compliance" rule-number 1 new-name "Allow all traffic that did not violate compliance" action "Accept" -s id.txt
"%varMgmt_cli%" add access-rule layer "Compliance" name "Uncategorised applications are not allowed for all corporate users - Ask User" action "Ask" position.top "Compliance" destination "Internet" service "Uncategorized" -s id.txt
"%varMgmt_cli%" add access-rule layer "Compliance" name "Source Code is confidential and must not leave the organization" action "Drop" position.top "Compliance" source "InternalZones" destination.1 "Internet" destination.2 "ExternalZone" data.1 "Source Code - Perl" data.2 "Source Code - Python" data.3 "Source Code - C Sharp" -s id.txt
"%varMgmt_cli%" publish -s id.txt
echo # Insert "Compliance" layer as ordered layer in "AUnifiedPolicy" package
"%varMgmt_cli%" set session description "Add compliance layer to AUnifiedPolicy" new-name "Add layer in ordered mode in policy" -s id.txt
"%varMgmt_cli%" set package name "AUnifiedPolicy" access-layers.add.1.name "Compliance" access-layers.add.1.position "2" -s id.txt
"%varMgmt_cli%" publish -s id.txt
echo # Prepare "AUnifiedPolicy Network" Layer in "AUnifiedPolicy" policy package by adding APPI column, DLP column and renaming "cleanup rule"
"%varMgmt_cli%" set session description "Activate APPI and Content blade in AUnifiedPolicy" new-name "Activate blades in layer" -s id.txt
"%varMgmt_cli%" set access-layer name "AUnifiedPolicy Network" applications-and-url-filtering "true" data-awareness "true" -s id.txt
"%varMgmt_cli%" set access-rule name "Cleanup rule" layer "AUnifiedPolicy Network" new-name "delete_me" -s id.txt
"%varMgmt_cli%" publish -s id.txt
echo # Fill "AUnifiedPolicy Network" Layer with rules
echo # add section "MGMT access Single Management Nordics-sm01""
"%varMgmt_cli%" set session description "Fill AUnifiedPolicy" new-name "adding rules" -s id.txt
"%varMgmt_cli%" add access-section name "MGMT access Security Management Nordics-sm01" position.bottom "AUnifiedPolicy Network" layer "AUnifiedPolicy Network" -s id.txt
"%varMgmt_cli%" add access-rule layer "AUnifiedPolicy Network" name "Enable open shell and open webui from management" action "Accept" position.bottom "AUnifiedPolicy Network" source "Nordics-sm01" destination "SecurityGateways" service "Management Protocols" -s id.txt
"%varMgmt_cli%" add access-rule layer "AUnifiedPolicy Network" name "Stealth rule" action "Drop" position.bottom "AUnifiedPolicy Network" destination.1 "Nordics-sm01" destination.2 "SecurityGateways" -s id.txt
"%varMgmt_cli%" publish -s id.txt
echo # add section "Internet Access"
"%varMgmt_cli%" set session description "Fill AUnifiedPolicy" new-name "adding rules" -s id.txt
"%varMgmt_cli%" add access-section name "Internet Access" position.bottom "AUnifiedPolicy Network" layer "AUnifiedPolicy Network" -s id.txt
"%varMgmt_cli%" add access-rule layer "AUnifiedPolicy Network" name "Drop high risk applications" service.1 "High Risk" service.2 "Critical Risk" install-on.1 "Stockholm-sg01" install-on.2 "Oslo-sg01" install-on.3 "Helsinki-sg01" action "Drop" position.bottom "Internet Access" -s id.txt
"%varMgmt_cli%" publish -s id.txt
echo # Insert "Sales Operations" Layer as a inline layer
"%varMgmt_cli%" set session description "Fill AUnifiedPolicy" new-name "adding rules" -s id.txt
"%varMgmt_cli%" add access-rule layer "AUnifiedPolicy Network" name "Sales Operations" source "Sales Operations" action "Apply Layer" inline-layer "Sales Operations" position.bottom "Internet Access" -s id.txt
"%varMgmt_cli%" publish -s id.txt
echo # Continue fill "AUnifiedPolicy Network" layer with rules under "Internet Access" section
"%varMgmt_cli%" set session description "Fill AUnifiedPolicy" new-name "adding rules" -s id.txt
"%varMgmt_cli%" add access-rule layer "AUnifiedPolicy Network" name "File Sharing - user check" destination "Internet" action "ask" service "File Storage and Sharing" position.bottom "Internet Access" -s id.txt
"%varMgmt_cli%" add access-rule layer "AUnifiedPolicy Network" name "limit social applications to off hours" service "Social Networking" action "Ask" position.bottom "Internet Access" destination "Internet" -s id.txt
"%varMgmt_cli%" add access-rule layer "AUnifiedPolicy Network" name "Enable internet access" action "Accept" position.bottom "Internet Access" source "InternalZones" destination "Internet" service "Internet Protocols" -s id.txt
"%varMgmt_cli%" publish -s id.txt
echo # Add section "VPN Site2Site"
"%varMgmt_cli%" set session description "Fill AUnifiedPolicy" new-name "adding rules" -s id.txt
"%varMgmt_cli%" add access-section name "VPN Site2Site" position.bottom "AUnifiedPolicy Network" layer "AUnifiedPolicy Network" -s id.txt
"%varMgmt_cli%" add access-rule layer "AUnifiedPolicy Network" name "allow VPN access to site1 and site2 internal network from all internal zones" action "Accept" position.bottom "VPN Site2Site" source "InternalZones" vpn "All_GwToGw" -s id.txt
"%varMgmt_cli%" publish -s id.txt
echo # Add section "Internal Server access"
"%varMgmt_cli%" set session description "Fill AUnifiedPolicy" new-name "adding rules" -s id.txt
"%varMgmt_cli%" add access-section name "Internal Server access" position.bottom "AUnifiedPolicy Network" layer "AUnifiedPolicy Network" -s id.txt
"%varMgmt_cli%" add access-rule layer "AUnifiedPolicy Network" name "Give full access to system administrators" action "Accept" position.bottom "Internal Server access" source "System Admins" destination "DMZ Servers" -s id.txt
"%varMgmt_cli%" add access-rule layer "AUnifiedPolicy Network" name "Give web access to servers" action "Accept" position.bottom "Internal Server access" destination "DMZ Servers" service "Internet Protocols" -s id.txt
"%varMgmt_cli%" publish -s id.txt
echo # Add section "Cleanup"
"%varMgmt_cli%" set session description "Fill AUnifiedPolicy" new-name "adding rules" -s id.txt
"%varMgmt_cli%" add access-section name "Cleanup" position.bottom "AUnifiedPolicy Network" layer "AUnifiedPolicy Network" -s id.txt
"%varMgmt_cli%" add access-rule layer "AUnifiedPolicy Network" name "Cleanup rule" action "Drop" position.bottom "Cleanup" -s id.txt
"%varMgmt_cli%" publish -s id.txt
echo remove the old renamed cleanup rule
"%varMgmt_cli%" set session description "remove old cleanup from AUnifiedPolicy" new-name "remove old cleanup" -s id.txt
"%varMgmt_cli%" delete access-rule name "delete_me" layer "AUnifiedPolicy Network" -s id.txt
echo #publish and logout
"%varMgmt_cli%" publish -s id.txt
"%varMgmt_cli%" logout -s id.txt
rem ################ Fill Central-Europe domain ###########################################
echo "Populate Central-Europe domain with objects and rules"
"%varMgmt_cli%" -m %varMdsB% login user "Walter" password "1234" domain "Central-Europe" > id.txt
"%varMgmt_cli%" set session new-name "Create rule base" description "Populate Central-Europe domain with objects and rules" -s id.txt
"%varMgmt_cli%" add simple-gateway name "EuropeBranchGw" comments "Europe Office gateway" ip-address 192.0.2.100 firewall true anti-bot true anti-virus true application-control true threat-emulation true url-filtering true ips true vpn true interfaces.1.name "eth0" interfaces.1.ip-address 192.0.2.100 interfaces.1.mask-length 24 interfaces.1.topology "EXTERNAL" interfaces.2.name "eth1" interfaces.2.ip-address 203.0.113.1 interfaces.2.mask-length 25 interfaces.2.topology "INTERNAL" interfaces.2.topology-settings.ip-address-behind-this-interface "LOCAL_NETWORK" tags '["Europe_gw"]' -s id.txt
"%varMgmt_cli%" add simple-gateway name "HQgw" comments "Main Office gateway" ip-address 192.0.2.200 firewall true anti-bot true anti-virus true application-control true threat-emulation true ips true url-filtering true vpn true interfaces.1.name "eth0" interfaces.1.ip-address 192.0.2.200 interfaces.1.mask-length 24 interfaces.1.topology "EXTERNAL" interfaces.2.name "eth1" interfaces.2.ip-address 198.51.100.5 interfaces.2.mask-length 25 interfaces.2.topology "INTERNAL" interfaces.2.topology-settings.ip-address-behind-this-interface "LOCAL_NETWORK" interfaces.3.name "eth2" interfaces.3.ip-address 198.51.100.129 interfaces.3.mask-length 25 interfaces.3.topology "INTERNAL" interfaces.3.topology-settings.ip-address-behind-this-interface "LOCAL_NETWORK" tags '["Internal_gw"]' -s id.txt
"%varMgmt_cli%" publish -s id.txt
"%varMgmt_cli%" add simple-gateway name "Corporate-GW" comments "First Office gateway" ip-address 198.51.100.4 firewall true application-control true anti-bot true anti-virus true vpn true url-filtering true data-awareness true ips true threat-emulation true version R80 interfaces.1.name "eth0" interfaces.1.ipv4-address "198.51.100.5" interfaces.1.ipv4-network-mask "255.255.255.0" interfaces.1.anti-spoofing false interfaces.1.topology "EXTERNAL" interfaces.2.name "eth1" interfaces.2.ipv4-address "198.51.100.6" interfaces.2.ipv4-network-mask "255.255.255.0" interfaces.2.anti-spoofing false interfaces.2.topology "INTERNAL" interfaces.2.topology-settings.ip-address-behind-this-interface "LOCAL_NETWORK" interfaces.3.name "eth2" interfaces.3.ipv4-address "198.51.100.7" interfaces.3.ipv4-network-mask "255.255.255.0" interfaces.3.anti-spoofing false interfaces.3.topology "INTERNAL" interfaces.3.topology-settings.ip-address-behind-this-interface "LOCAL_NETWORK" interfaces.4.name "eth3" interfaces.4.ipv4-address "198.51.100.8" interfaces.4.ipv4-network-mask "255.255.255.0" interfaces.4.anti-spoofing false interfaces.4.topology "INTERNAL" interfaces.4.topology-settings.ip-address-behind-this-interface "LOCAL_NETWORK" tags '["Internal_gw"]' -s id.txt
"%varMgmt_cli%" add simple-gateway name "BranchOffice" comments "Second office gateway" ip-address 198.51.100.0 firewall true application-control true vpn true version R77.30 interfaces.1.name "eth0" interfaces.1.ipv4-address "198.51.100.1" interfaces.1.ipv4-network-mask "255.255.255.0" interfaces.1.anti-spoofing false interfaces.1.topology "EXTERNAL" interfaces.2.name "eth1" interfaces.2.ipv4-address "198.51.100.2" interfaces.2.ipv4-network-mask "255.255.255.0" interfaces.2.anti-spoofing false interfaces.2.topology "INTERNAL" interfaces.2.topology-settings.ip-address-behind-this-interface "LOCAL_NETWORK" tags '["External_gw"]' -s id.txt
"%varMgmt_cli%" add simple-gateway name "RemoteBranchGw" comments "RemoteBranchGw" ip-address 198.51.100.120 firewall true ips true interfaces.1.name "eth0" interfaces.1.ip-address 98.51.100.120 interfaces.1.mask-length 24 interfaces.1.topology "EXTERNAL" interfaces.2.name "eth1" interfaces.2.ip-address 172.0.113.112 interfaces.2.mask-length 25 interfaces.2.topology "INTERNAL" interfaces.2.topology-settings.ip-address-behind-this-interface "LOCAL_NETWORK" tags '["External_gw"]' -s id.txt
"%varMgmt_cli%" add simple-gateway name "ThreatEmulationDevice" comments "Threat Emulation" ip-address 192.0.111.13 firewall true threat-emulation true interfaces.1.name "eth0" interfaces.1.ip-address 192.0.111.13 interfaces.1.mask-length 24 interfaces.1.topology "EXTERNAL" interfaces.2.name "eth1" interfaces.2.ip-address 172.0.1.113 interfaces.2.mask-length 25 interfaces.2.topology "INTERNAL" interfaces.2.topology-settings.ip-address-behind-this-interface "LOCAL_NETWORK" tags '["ThreatEmulation_gw"]' -s id.txt
"%varMgmt_cli%" set session description "Add R80.10 gateways" new-name "Demo add gateways - Step 2" -s id.txt
"%varMgmt_cli%" publish -s id.txt
"%varMgmt_cli%" add simple-gateway name "Remote-1-gw" version "R75.40" os-name "SecurePlatform" comments "Remote-1-gw" ip-address 192.0.22.1 firewall true ips true vpn true interfaces.1.name "eth0" interfaces.1.ip-address 192.0.22.1 interfaces.1.mask-length 24 interfaces.1.topology "EXTERNAL" interfaces.2.name "eth1" interfaces.2.ip-address 172.0.113.1 interfaces.2.mask-length 25 interfaces.2.topology "INTERNAL" interfaces.2.topology-settings.ip-address-behind-this-interface "LOCAL_NETWORK" tags '["External_gw"]' -s id.txt
"%varMgmt_cli%" add simple-gateway name "Remote-2-gw" version "R75.40" os-name "Windows" comments "Remote-2-gw" ip-address 192.0.23.1 firewall true ips true vpn true interfaces.1.name "eth0" interfaces.1.ip-address 192.0.3.1 interfaces.1.mask-length 24 interfaces.1.topology "EXTERNAL" interfaces.2.name "eth1" interfaces.2.ip-address 172.0.113.1 interfaces.2.mask-length 25 interfaces.2.topology "INTERNAL" interfaces.2.topology-settings.ip-address-behind-this-interface "LOCAL_NETWORK" tags '["External_gw"]' -s id.txt
"%varMgmt_cli%" add simple-gateway name "Remote-3-gw" version "R77.20" comments "Remote-3-gw" ip-address 192.0.24.1 firewall true interfaces.1.name "eth0" interfaces.1.ip-address 192.0.4.1 interfaces.1.mask-length 24 interfaces.1.topology "EXTERNAL" interfaces.2.name "eth1" interfaces.2.ip-address 172.0.1.1 interfaces.2.mask-length 25 interfaces.2.topology "INTERNAL" interfaces.2.topology-settings.ip-address-behind-this-interface "LOCAL_NETWORK" tags '["External_gw"]' -s id.txt
"%varMgmt_cli%" add simple-gateway name "Remote-4-gw" version "R75.40" comments "Remote-4-gw" ip-address 192.0.25.1 firewall true ips true vpn true interfaces.1.name "eth0" interfaces.1.ip-address 192.0.5.1 interfaces.1.mask-length 24 interfaces.1.topology "EXTERNAL" interfaces.2.name "eth1" interfaces.2.ip-address 172.0.2.1 interfaces.2.mask-length 25 interfaces.2.topology "INTERNAL" interfaces.2.topology-settings.ip-address-behind-this-interface "LOCAL_NETWORK" tags '["External_gw"]' -s id.txt
"%varMgmt_cli%" add simple-gateway name "Remote-5-gw" version "R77.20" comments "Remote-5-gw" ip-address 192.0.26.1 firewall true interfaces.1.name "eth0" interfaces.1.ip-address 192.0.6.1 interfaces.1.mask-length 24 interfaces.1.topology "EXTERNAL" interfaces.2.name "eth1" interfaces.2.ip-address 172.0.3.1 interfaces.2.mask-length 25 interfaces.2.topology "INTERNAL" interfaces.2.topology-settings.ip-address-behind-this-interface "LOCAL_NETWORK" tags '["External_gw"]' -s id.txt
"%varMgmt_cli%" set session description "Add remote gateways" new-name "Add Remote gateways" -s id.txt
"%varMgmt_cli%" publish -s id.txt
"%varMgmt_cli%" set session description "Add tags and Security Zone" new-name "Add tags and Security Zone" -s id.txt
"%varMgmt_cli%" add tag name "Internal_gw" color red -s id.txt
"%varMgmt_cli%" add tag name "External_gw" color yellow -s id.txt
"%varMgmt_cli%" add tag name "DMZ_gw" color "dark orange 3" -s id.txt
"%varMgmt_cli%" add tag name "Europe_gw" color "dark orchid" -s id.txt
"%varMgmt_cli%" add tag name "ThreatEmulation_gw" color blue -s id.txt
"%varMgmt_cli%" add-security-zone name "Finance" -s id.txt
"%varMgmt_cli%" publish -s id.txt
"%varMgmt_cli%" set session description "Add Groups" new-name "Add Groups" -s id.txt
"%varMgmt_cli%" add group name "Gateways_Group" color "BLACK" members "[\"HQgw\", \"EuropeBranchGw\"]" -s id.txt
"%varMgmt_cli%" add group name "InternalZones" color "BLACK" members "[]" -s id.txt
"%varMgmt_cli%" add group name "DMZ Servers" color "BLACK" members "[]" -s id.txt
"%varMgmt_cli%" publish -s id.txt
echo "create hosts"
"%varMgmt_cli%" set session description "Add Policy" new-name "New policy package with rules and objects" -s id.txt
"%varMgmt_cli%" add host name "DNS Server" ip-address 198.51.100.9 -s id.txt
"%varMgmt_cli%" add host name "ERP Server" ip-address 198.51.100.10 -s id.txt
"%varMgmt_cli%" add host name "Exchange" ip-address 198.51.100.11 -s id.txt
"%varMgmt_cli%" add host name "FTP_Int" ip-address 198.51.100.12 -s id.txt
"%varMgmt_cli%" add host name "Web Server" ip-address 198.51.100.13 -s id.txt
"%varMgmt_cli%" add host name "MTA" ip-address 198.51.100.14 -s id.txt
echo "create networks"
"%varMgmt_cli%" add network name "HR LAN" subnet 198.51.100.15 subnet-mask 255.255.255.255 -s id.txt
"%varMgmt_cli%" add network name "Sales LAN" subnet 198.51.100.16 subnet-mask 255.255.255.255 -s id.txt
"%varMgmt_cli%" add network name "DMZ LAN" subnet 198.51.100.17 subnet-mask 255.255.255.255 -s id.txt
"%varMgmt_cli%" add network name "Branch Office LAN" subnet 198.51.100.18 subnet-mask 255.255.255.255 -s id.txt
"%varMgmt_cli%" add network name "Data Center LAN" subnet 198.51.100.19 subnet-mask 255.255.255.255 -s id.txt
echo "create services"
"%varMgmt_cli%" add service-tcp name "Http_9090" port 9090 -s id.txt
echo "create time"
"%varMgmt_cli%" add time name "Temp Access" start-now "true" end.date "12-Dec-2015" end.time "21:25" end-never "false" recurrence.pattern "Daily" -s id.txt
echo "create network group"
"%varMgmt_cli%" add group name "Corporate LANs" members "[\"HR LAN\", \"Sales LAN\"]" -s id.txt
echo "create application/site"
"%varMgmt_cli%" add application-site name "Blocked URLs" primary-category "Custom_Application_Site" url-list.1 "www.block*.*" urls-defined-as-regular-expression true -s id.txt
"%varMgmt_cli%" add application-site name "Report Portal" primary-category "Custom_Application_Site" url-list.1 "*.portal" urls-defined-as-regular-expression false -s id.txt
echo "create communities"
"%varMgmt_cli%" add vpn-community-meshed name "Site2Site" gateways "[\"BranchOffice\", \"Corporate-GW\"]" -s id.txt
echo "create application group"
"%varMgmt_cli%" add application-site-group name "Inappropriate Sites" members.1 "Child Abuse" members.2 "High Risk" members.3 "Spyware / Malicious Sites" members.4 "Gambling" -s id.txt
echo "create service group"
"%varMgmt_cli%" add service-group name "Manage Services" members.1 "GoToMyPC" -s id.txt
"%varMgmt_cli%" add service-group name "Internet Services" members.1 "HTTPS_proxy" members.2 "HTTP_proxy" members.3 "IMAP-SSL" members.4 "POP3S" members.5 "http" members.6 "https" -s id.txt
echo "create access roles"
"%varMgmt_cli%" add access-role name "Admins" networks "any" users "any" machines "any" remote-access-clients "any" -s id.txt
"%varMgmt_cli%" add access-role name "Finance User" networks "any" users "any" machines "any" remote-access-clients "any" -s id.txt
"%varMgmt_cli%" add access-role name "HR" networks "any" users "any" machines "any" remote-access-clients "any" -s id.txt
"%varMgmt_cli%" add access-role name "IT Department" networks "any" users "any" machines "any" remote-access-clients "any" -s id.txt
"%varMgmt_cli%" add access-role name "Sales" networks "any" users "any" machines "any" remote-access-clients "any" -s id.txt
"%varMgmt_cli%" add access-role name "Remote Access Users" networks "any" users "any" machines "any" remote-access-clients "any" -s id.txt
rem ################ Create Layers ###########################################
echo "create layers"
"%varMgmt_cli%" add access-layer name "Web Control" applications-and-url-filtering true data-awareness true mobile-access true -s id.txt
"%varMgmt_cli%" add access-layer name "Data Center Layer" applications-and-url-filtering true data-awareness true mobile-access true -s id.txt
"%varMgmt_cli%" add access-layer name "Guest Exception Layer" applications-and-url-filtering true data-awareness true -s id.txt
rem ######################################################################################
rem ################### Add Rules to "Web Control" Layer #################################
echo "add rules to 'Web Control Layer"
"%varMgmt_cli%" add access-rule layer "Web Control" name "DNS server should have access to" action accept position top source "[\"DNS Server\"]" destination "[\"ExternalZone\"]" service.1 "dns" track log -s id.txt
"%varMgmt_cli%" add access-rule layer "Web Control" name "Block abuse/ high risk applications" action drop position bottom source "[\"Corporate LANs\", \"Branch Office LAN\"]" destination "[\"Internet\"]" service.1 "Inappropriate Sites" user-check.interaction "Blocked Message - Access Control" track log -s id.txt
"%varMgmt_cli%" add access-rule layer "Web Control" name "HR can access to social network applications" action inform position bottom source "[\"HR\"]" destination "[\"Internet\"]" service.1 "Facebook" service.2 "Twitter" service.3 "LinkedIn" user-check.interaction "Access Approval" track log -s id.txt
"%varMgmt_cli%" add access-rule layer "Web Control" name "All employees can access YouTube for work purposes" action ask position bottom source "[\"Corporate LANs\", \"Branch Office LAN\"]" destination "[\"Internet\"]" service.1 "YouTube" service.2 "Vimeo" user-check.interaction "Company Policy" track log -s id.txt
"%varMgmt_cli%" add access-rule layer "Web Control" name "Block specific URLs" action drop position bottom destination "[\"Internet\"]" service.1 "Blocked URLs" track log -s id.txt
"%varMgmt_cli%" add access-rule layer "Web Control" name "Block specific categories for all employees" action drop position bottom source "[\"Corporate LANs\", \"Branch Office LAN\"]" destination "[\"Internet\"]" service.1 "Social Networking" service.2 "Streaming Media Protocols" service.3 "P2P File Sharing" user-check.interaction "Blocked Message - Access Control" track log -s id.txt
"%varMgmt_cli%" delete access-rule rule-number 2 layer "Web Control" -s id.txt
rem ##################################################################################
rem ################### Add Rules to "Data Center Layer" Layer #################################
echo "add rules to 'Data Center Layer' layer"
"%varMgmt_cli%" add access-rule layer "Data Center Layer" name "Mobile Access for Internal FS" action accept position top source "[\"Sales\"]" destination "[\"FTP_Int\"]" vpn "RemoteAccess" service.1 "ftp" data "[\"Document File\", \"Archive File\"]" track "detailed log" -s id.txt
"%varMgmt_cli%" add access-rule layer "Data Center Layer" name "Branch office should have VPN access to servers (ERP on ftp_22)" action accept position bottom source "[\"Branch Office LAN\"]" destination "[\"ERP Server\", \"Exchange\", \"FTP_Int\"]" vpn "Site2Site" service.1 "ftp" service.2 "smtp" service.3 "ftp" data "[\"Document File\", \"Media and Images\"]" track "detailed log" -s id.txt
"%varMgmt_cli%" add access-rule layer "Data Center Layer" name "ERP server being accessed on FTP via port 22" action accept position bottom source "[\"Corporate LANs\"]" destination "[\"ERP Server\"]" service.1 "ftp" data "[\"Document File\"]" track "detailed log" -s id.txt
"%varMgmt_cli%" add access-rule layer "Data Center Layer" name "Only Finance department has access to reports" action accept position bottom source "[\"Finance User\"]" destination "[\"ERP Server\"]" service.1 "Report Portal" track "detailed log" -s id.txt
"%varMgmt_cli%" add access-rule layer "Data Center Layer" name "Save DNS requests using our DNS" action accept position bottom source "[\"DMZZone\", \"InternalZone\"]" destination "[\"DNS Server\"]" service.1 "dns" track log -s id.txt
rem #remove default clean up rule
"%varMgmt_cli%" delete access-rule rule-number 2 layer "Data Center Layer" -s id.txt
rem ##################################################################################
rem ################### Add Rules to "Guest Exception Layer" Layer #################################
echo "add rules to 'Guest Exception Layer' layer"
"%varMgmt_cli%" add access-rule layer "Guest Exception Layer" name "Guests from Portal" action accept position top destination "[\"Internet\"]" service.1 "http" service.2 "https" track log action-settings.enable-identity-captive-portal true -s id.txt
rem #remove default clean up rule
"%varMgmt_cli%" delete access-rule rule-number 2 layer "Guest Exception Layer" -s id.txt
rem ##################################################################################
rem ########################### Edit Standard Layer ##################################
echo "edit Network layer blades"
"%varMgmt_cli%" set access-layer name "Network" applications-and-url-filtering true data-awareness true mobile-access true -s id.txt
rem #####################################################################################
rem ########################## Add Rules To Standard Network Layer #############################
echo "add rules to 'Network' layer"
rem #section 'Security Gateways Access'
"%varMgmt_cli%" add access-section name "Security Gateways Access" position.bottom Network layer Network -s id.txt
"%varMgmt_cli%" add access-rule layer Network name "Administrator Access to Gateways" action accept position.top "Security Gateways Access" source "[\"Admins\"]" destination "[\"Corporate-GW\"]" service.1 "Manage Services" -s id.txt
rem #"%varMgmt_cli%" add access-rule layer Network name "Noise rule" action drop position.bottom "Security Gateways Access" source "[\"InternalZone\"]" destination "[\"Corporate-GW\"]" service.1 "NBT" -s id.txt
"%varMgmt_cli%" add access-rule layer Network name "Stealth rule" action drop position.bottom "Security Gateways Access" destination "[\"Corporate-GW\"]" -s id.txt
rem #section 'VPN'
"%varMgmt_cli%" add access-section name "VPN" position.bottom Network layer Network -s id.txt
"%varMgmt_cli%" add access-rule layer Network name "Remote Access of employees to Data Center servers" action accept position.top "VPN" source "[\"Remote Access Users\"]" destination "[\"Data Center LAN\"]" vpn "RemoteAccess" -s id.txt
"%varMgmt_cli%" add access-rule layer Network name "VPN between Internal LANs and Branch office LAN" action accept position.bottom "VPN" source "[\"Corporate LANs\", \"Branch Office LAN\"]" destination "[\"Branch Office LAN\", \"Corporate LANs\"]" vpn "Site2Site" -s id.txt
rem #section 'Access To Internet'
"%varMgmt_cli%" add access-section name "Access To Internet" position.bottom Network layer Network -s id.txt
"%varMgmt_cli%" add access-rule layer "Network" position.top "Access To Internet" name "Access to Internet according to Web control policy" action "Apply Layer" inline-layer "Web Control" source "[\"InternalZone\"]" destination "[\"Internet\"]" -s id.txt
rem #section "DMZ"
"%varMgmt_cli%" add access-section name "DMZ" position.bottom Network layer Network -s id.txt
"%varMgmt_cli%" add access-rule layer Network name "Access to company's web server" action accept position.top "DMZ" source "[\"ExternalZone\"]" destination "[\"Web Server\"]" service.1 "Web Browser" track "detailed log" -s id.txt
"%varMgmt_cli%" add access-rule layer Network name "Allow corporate LANs to DMZ" action accept position.bottom "DMZ" source "[\"Corporate LANs\"]" destination "[\"DMZZone\"]" service.1 "https" service.2 "http" service.3 "ftp" track log -s id.txt
rem #section "Data Center Access"
"%varMgmt_cli%" add access-section name "Data Center Access" position.bottom Network layer Network -s id.txt
"%varMgmt_cli%" add access-rule layer "Network" position.top "Data Center Access" name "Policy for access to Data Center servers" action "Apply Layer" inline-layer "Data Center Layer" destination "[\"Data Center LAN\"]" -s id.txt
rem #section "Data Center Access" - TP blade
"%varMgmt_cli%" set threat-rule rule-number 1 layer "Standard Threat Prevention" new-name "Recommended Protections" -s id.txt
"%varMgmt_cli%" add threat-rule layer "Standard Threat Prevention" position "top" name "Data Center Protection" comments "" protected-scope "Data Center LAN" action "Strict" install-on "Policy Targets" -s id.txt
rem #section "Temporary Access Grant"
"%varMgmt_cli%" add access-section name "Temporary Access Grant" position.bottom Network layer Network -s id.txt
"%varMgmt_cli%" add access-rule layer "Network" position.top "Temporary Access Grant" name "Special policy for temp guest rules using wireless LAN" action "Apply Layer" inline-layer "Guest Exception Layer" source "[\"WirelessZone\"]" -s id.txt
rem #section CleanUp
"%varMgmt_cli%" add access-section name "Clean Up" position.bottom Network layer Network -s id.txt
"%varMgmt_cli%" add access-rule layer Network name "Clean up" action drop position.bottom "Clean Up" track log -s id.txt
rem #remove default clean up rule
"%varMgmt_cli%" delete access-rule rule-number 1 layer Network -s id.txt
rem ############################################################################
rem ####################### Create Branch_Office_Policy policy Package ###########################
echo "create Branch_Office_Policy policy package"
rem #create Branch_Office_Policy policy package
"%varMgmt_cli%" add package name "Branch_Office_Policy" access true threat-prevention true installation-targets "BranchOffice" -s id.txt
"%varMgmt_cli%" set package name "Branch_Office_Policy" access-layers.add.1.name "Web Control" access-layers.add.1.position 2 -s id.txt
rem ############################################################################
rem ################# Add rules to Branch_Office_Policy Network Layer ####################
echo "add rules to 'Branch_Office_Policy Network' layer"
rem #section GW access
"%varMgmt_cli%" add access-section name "GW Access" position.bottom "Branch_Office_Policy Network" layer "Branch_Office_Policy Network" -s id.txt
"%varMgmt_cli%" add access-rule layer "Branch_Office_Policy Network" name "Administrator Access to Gateways" action accept position.top "GW Access" source "[\"Admins\"]" destination "[\"BranchOffice\"]" service.1 "Manage Services" track log -s id.txt
"%varMgmt_cli%" add access-rule layer "Branch_Office_Policy Network" name "DHCP Server for the branch Office" action accept position.bottom "GW Access" destination "[\"BranchOffice\"]" service.1 "dhcp-request" track log -s id.txt
"%varMgmt_cli%" add access-rule layer "Branch_Office_Policy Network" name "Stealth rule" action drop position.bottom "GW Access" destination "[\"BranchOffice\"]" track log -s id.txt
rem #section VPN
"%varMgmt_cli%" add access-section name "VPN" position.bottom "Branch_Office_Policy Network" layer "Branch_Office_Policy Network" -s id.txt
"%varMgmt_cli%" add access-rule layer "Branch_Office_Policy Network" name "VPN between Internal LANs and Branch office LAN" action accept position.top "VPN" source "[\"Corporate LANs\", \"Branch Office LAN\"]" destination "[\"Branch Office LAN\", \"Corporate LANs\"]" vpn "Site2Site" track log -s id.txt
"%varMgmt_cli%" add access-rule layer "Branch_Office_Policy Network" name "Branch office should have VPN access to servers (ERP on ftp_22)" action accept position.bottom "VPN" source "[\"Branch Office LAN\"]" destination "[\"ERP Server\", \"FTP_Int\"]" service.1 "ftp" service.2 "ftp" vpn "Site2Site" track log -s id.txt
"%varMgmt_cli%" add access-rule layer "Branch_Office_Policy Network" name "Branch office should have VPN access to servers" action accept position.bottom "VPN" source "[\"Branch Office LAN\"]" destination "[\"Exchange\", \"DNS Server\"]" vpn "Site2Site" service.1 "http" service.2 "https" service.3 "dns" service.4 "smtp" track log -s id.txt
rem #section Internet Access
"%varMgmt_cli%" add access-section name "Internet Access" position.bottom "Branch_Office_Policy Network" layer "Branch_Office_Policy Network" -s id.txt
"%varMgmt_cli%" add access-rule layer "Branch_Office_Policy Network" name "Access to Internet according to Web control policy (next layer)" action accept position.top "Internet Access" source "[\"Branch Office LAN\"]" service.1 "Internet Services" track log -s id.txt
rem #section Clean Up
"%varMgmt_cli%" add access-section name "Clean Up" position.bottom "Branch_Office_Policy Network" layer "Branch_Office_Policy Network" -s id.txt
"%varMgmt_cli%" add access-rule layer "Branch_Office_Policy Network" name "clean up" action drop position.bottom "Clean Up" -s id.txt
rem #remove default cleanup rule
"%varMgmt_cli%" delete access-rule rule-number 1 layer "Branch_Office_Policy Network" -s id.txt
rem #####################################################################
rem ############# change package names ###########################
echo "change policy package names"
"%varMgmt_cli%" set package name "Standard" new-name "Corporate_Policy" -s id.txt
"%varMgmt_cli%" set package name "Corporate_Policy" installation-targets "Corporate-GW" -s id.txt
rem ###############################################################
"%varMgmt_cli%" set session description "Add Corporate_Policy" new-name "Demo add policy package" -s id.txt
"%varMgmt_cli%" publish -s id.txt
rem #### create host , add new rule and publish( in favour install statuses object)
"%varMgmt_cli%" add host name "FTP_Ext" ip-address 2.3.2.2 -s id.txt
"%varMgmt_cli%" add access-rule layer Network name "Customers to ftp servers" action accept position 8 source "[\"ExternalZone\"]" destination "[\"FTP_Ext\"]" service.1 "ftp" data "[\"Archive File\"]" track "detailed log" -s id.txt
"%varMgmt_cli%" set session description "Add ftp rule to Corporate_Policy" new-name "Demo rule policy package" -s id.txt
"%varMgmt_cli%" publish -s id.txt
rem ##### add new rule and publish( in favour install statuses object)
"%varMgmt_cli%" add access-rule layer "Guest Exception Layer" name "Temp rule: Board Presentation" action accept position bottom destination "[\"FTP_Int\"]" service.1 "ftp" track log time "Temp Access" -s id.txt
"%varMgmt_cli%" set session description "Add ftp guest access" new-name "Demo guest rule" -s id.txt
"%varMgmt_cli%" publish -s id.txt
"%varMgmt_cli%" logout -s id.txt
rem #add rules history
"%varMgmt_cli%" -m %varMdsB% login user "Saul" password "1234" domain "Central-Europe" > id.txt
"%varMgmt_cli%" set access-rule layer Network name "Administrator Access to Gateways" action Reject source "[\"Sales\"]" destination "[\"Corporate-GW\"]" track log -s id.txt
"%varMgmt_cli%" set access-rule layer Network name "Stealth rule" track log -s id.txt
"%varMgmt_cli%" set access-rule layer Network name "Remote Access of employees to Data Center servers" track log -s id.txt
"%varMgmt_cli%" set access-rule layer Network name "VPN between Internal LANs and Branch office LAN" track log -s id.txt
"%varMgmt_cli%" set session description "Set rule Corporate_Policy" new-name "Demo rule Reject" -s id.txt
"%varMgmt_cli%" publish -s id.txt
"%varMgmt_cli%" set access-rule layer Network name "Administrator Access to Gateways" action "accept" source "[\"Admins\"]" destination "[\"Corporate-GW\"]" -s id.txt
"%varMgmt_cli%" set session description "Set accept rule Corporate_Policy" new-name "Demo rule accept" -s id.txt
"%varMgmt_cli%" publish -s id.txt
"%varMgmt_cli%" logout -s id.txt
goto :end
:end
echo "All done.."
2 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Running the single MDS script, see endless failed to parse errors.
"Create admin user Skyler"
Failed to parse login output file [id.txt]
Failed to parse login output file [id.txt]
Failed to parse login output file [id.txt]
Failed to parse login output file [id.txt]
"Create admin users for Multi Domain using user Skyler"
Failed to parse login output file [id.txt]
Failed to parse login output file [id.txt]
Failed to parse login output file [id.txt]
Failed to parse login output file [id.txt]
Failed to parse login output file [id.txt]
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
id.txt is the file with your auth token. Check if it is there & make sure the relevant creating command was not truncated during copy/paste:
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 2 | |
| 1 | |
| 1 | |
| 1 | |
| 1 | |
| 1 |
Upcoming Events
Tue 03 Mar 2026 @ 04:00 PM (CET)
Maestro Masters EMEA: Introduction to Maestro Hyperscale FirewallsTue 03 Mar 2026 @ 03:00 PM (EST)
Maestro Masters Americas: Introduction to Maestro Hyperscale FirewallsTue 03 Mar 2026 @ 04:00 PM (CET)
Maestro Masters EMEA: Introduction to Maestro Hyperscale FirewallsTue 03 Mar 2026 @ 03:00 PM (EST)
Maestro Masters Americas: Introduction to Maestro Hyperscale FirewallsFri 06 Mar 2026 @ 08:00 AM (COT)
Check Point R82 Hands‑On Bootcamp – Comunidad DOJO PanamáTue 24 Mar 2026 @ 06:00 PM (COT)
San Pedro Sula: Spark Firewall y AI-Powered Security ManagementAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter


