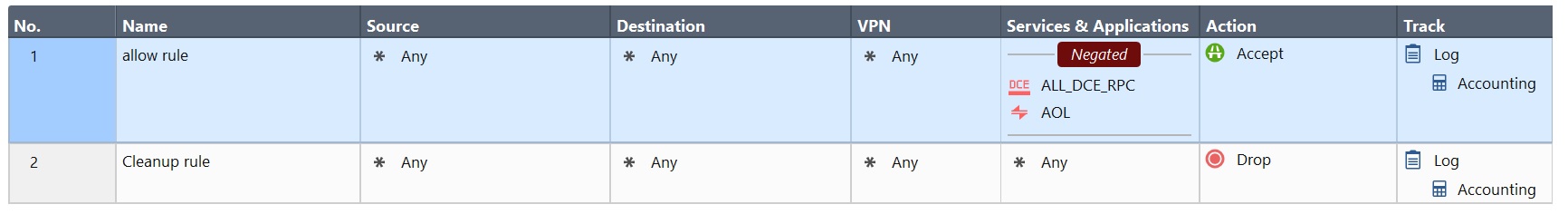
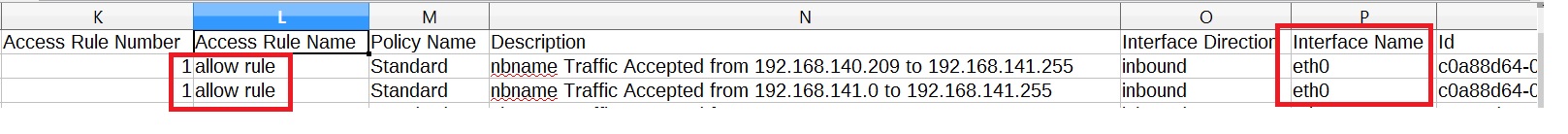
Oh, I see the problem--your rule does not list any zones as source or destinations.
As such, querying the rulebase will not give you this information.
Your best bet is to query the gateway that accepted the connection (by name or UID) using show simple-gateway.
One potential issue I see is that you won't see the interface zone if you use the "default" zone for that interface (i.e. "According to topology"):
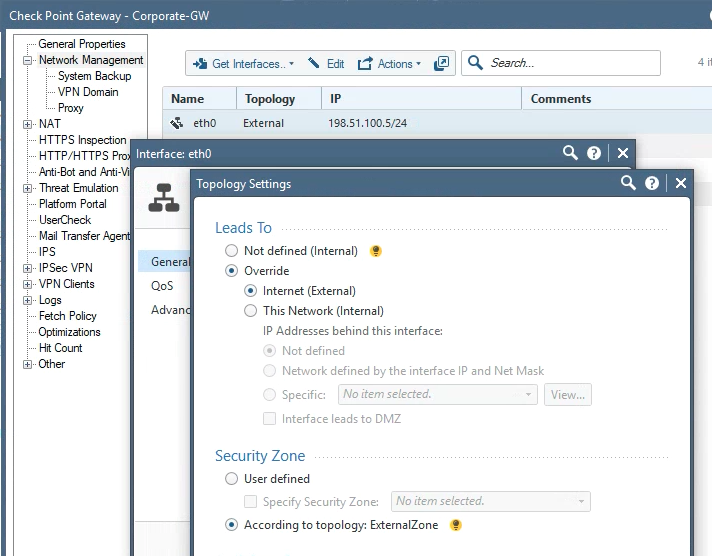
In this case, you'll have to work it out from the interface topology which interfaces are InternalZone or ExternalZone.
In this case, it's eth0.
For others not marked as topology external, you can assume they are in the InternalZone if one is not listed.
In the case of eth2, I set an explicit zone for that interface.
> show simple-gateway name Corporate-GW
uid: "8c134e6d-7b92-4f6a-b572-a819905c1918"
name: "Corporate-GW"
type: "simple-gateway"
domain:
uid: "41e821a0-3720-11e3-aa6e-0800200c9fde"
name: "SMC User"
domain-type: "domain"
interfaces:
- name: "eth3"
ipv4-address: "198.51.100.8"
ipv4-network-mask: "255.255.255.0"
ipv4-mask-length: 24
ipv6-address: ""
topology: "internal"
topology-settings:
ip-address-behind-this-interface: "network defined by the interface ip and net mask"
interface-leads-to-dmz: false
anti-spoofing: false
security-zone: false
- name: "eth0"
ipv4-address: "198.51.100.5"
ipv4-network-mask: "255.255.255.0"
ipv4-mask-length: 24
ipv6-address: ""
topology: "external"
anti-spoofing: false
security-zone: false
- name: "eth1"
ipv4-address: "198.51.100.6"
ipv4-network-mask: "255.255.255.0"
ipv4-mask-length: 24
ipv6-address: ""
topology: "internal"
topology-settings:
ip-address-behind-this-interface: "network defined by the interface ip and net mask"
interface-leads-to-dmz: false
anti-spoofing: false
security-zone: false
- name: "eth2"
ipv4-address: "198.51.100.7"
ipv4-network-mask: "255.255.255.0"
ipv4-mask-length: 24
ipv6-address: ""
topology: "internal"
topology-settings:
ip-address-behind-this-interface: "network defined by the interface ip and net mask"
interface-leads-to-dmz: false
anti-spoofing: false
security-zone: true
security-zone-settings:
auto-calculated: false
specific-zone: "DMZZone"
ipv4-address: "198.51.100.4"
dynamic-ip: false
version: "R80"
os-name: "Gaia"
hardware: "21000 Appliances"
sic-name: ""
sic-state: "uninitialized"
firewall: true
firewall-settings:
auto-maximum-limit-for-concurrent-connections: true
maximum-limit-for-concurrent-connections: 25000
auto-calculate-connections-hash-table-size-and-memory-pool: true
connections-hash-size: 131072
memory-pool-size: 6
maximum-memory-pool-size: 30
vpn: true
vpn-settings:
maximum-concurrent-ike-negotiations: 1000
maximum-concurrent-tunnels: 10000
application-control: true
url-filtering: true
ips: true
content-awareness: true
anti-bot: true
anti-virus: true
threat-emulation: true
save-logs-locally: false
send-alerts-to-server:
- "mgmt"
send-logs-to-server:
- "mgmt"
send-logs-to-backup-server: []
logs-settings:
rotate-log-by-file-size: false
rotate-log-file-size-threshold: 1000
rotate-log-on-schedule: false
alert-when-free-disk-space-below-metrics: "mbytes"
alert-when-free-disk-space-below: true
alert-when-free-disk-space-below-threshold: 20
alert-when-free-disk-space-below-type: "popup alert"
delete-when-free-disk-space-below-metrics: "mbytes"
delete-when-free-disk-space-below: true
delete-when-free-disk-space-below-threshold: 5000
before-delete-keep-logs-from-the-last-days: false
before-delete-keep-logs-from-the-last-days-threshold: 0
before-delete-run-script: false
before-delete-run-script-command: ""
stop-logging-when-free-disk-space-below-metrics: "mbytes"
stop-logging-when-free-disk-space-below: true
stop-logging-when-free-disk-space-below-threshold: 100
reject-connections-when-free-disk-space-below-threshold: false
reserve-for-packet-capture-metrics: "mbytes"
reserve-for-packet-capture-threshold: 500
delete-index-files-when-index-size-above-metrics: "mbytes"
delete-index-files-when-index-size-above: false
delete-index-files-when-index-size-above-threshold: 100000
delete-index-files-older-than-days: false
delete-index-files-older-than-days-threshold: 14
forward-logs-to-log-server: false
perform-log-rotate-before-log-forwarding: false
update-account-log-every: 3600
detect-new-citrix-ica-application-names: false
turn-on-qos-logging: true
groups: []
comments: ""
color: "black"
icon: "NetworkObjects/gateway"
tags: []
meta-info:
lock: "unlocked"
validation-state: "ok"
last-modify-time:
posix: 1542390183151
iso-8601: "2018-11-16T19:43+0200"
last-modifier: "admin"
creation-time:
posix: 1460464877124
iso-8601: "2016-04-12T15:41+0300"
creator: "admin"
read-only: false