- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity AI Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
CheckMates Fest 2026
Join the Celebration!
AI Security Masters
E1: How AI is Reshaping Our World
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
R82.10 and Rationalizing Multi Vendor Security Policies
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Developers
- :
- API / CLI Discussion
- :
- How to export firewall policies and NAT.csv in exp...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
How to export firewall policies and NAT.csv in expert mode
This section describes how to export the firewall policy and nat rule policy to csv through the command line, or enter the policy in json format through the command.
14 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I would start with "mgmt_cli show packages"
From there you can get/parse all policy names and run the following for every policy you like. If you have a unified policy package, the layer name is probably "network".
mgmt_cli show access-rulebase name Network package <policy_name>
mgmt_cli show nat-rulebase package <policy_name>
Kind regards, Amir Senn
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
That would show it, but is there a flag to export it?
Hope you are staying safe!
Andy
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I usually echo the response into a file and then it's easier for me. I haven't tried the tool from the sk @Zolocofxp mentioned, if it works well it will be more presentable and worth a shot.
Trying to stay safe, thank you very much for your concern.
Kind regards, Amir Senn
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
True, that tool is good, agree! I pray for peace man no matter who it is or what nation. I lived in war myself (Hell, probably better word to use), so I know exactly how it is...sadly, ALWAYS innocent people pay the price.
Andy
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello, Amir_Senn, using mgmt_cli export has bar code restrictions, the policy can only display 20 items at a time, can you specify the main information such as source address, destination address, and port in a table?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Sorry, I don't understand which 20 items you're talking about, can you elaborate?
BTW, I made a one-liner that goes over the DB and takes all the policy packages and export access control RB + NAT RB for each and saves them as text file in json format. Still needs work but maybe you can use it. Not suitable for MDS at the moment.
mgmt_cli show packages -r true | grep "name" > Senn_temp.txt ; cat Senn_temp.txt | cut -d':' -f2- > Senn_temp0.txt ; Lines=$(cat Senn_temp0.txt | wc -l) ; for (( N=0; $N<$Lines; N=(($N+2)))); { current=$(head -1 Senn_temp$N.txt); current=${current::-2}; current=${current:2}; echo $current >> policies0.txt; cat Senn_temp0.txt | tail -$(($Lines-$N-2)) > Senn_temp$(($N+2)).txt; } ; rm Senn_temp* ; Lines=$(cat policies0.txt | wc -l) ; for (( N=0; $N<$Lines; N=(($N+1)))); { current_policy=$(head -1 policies$N.txt); current_layer=$(mgmt_cli show package -r true name $current_policy | grep -A2 access-layers: | grep name* | cut -c8-); current_layer=${current_layer::-2}; current_layer=${current_layer:2}; current_name="${current_layer// /_}"; mgmt_cli show access-rulebase name "$current_layer" limit 500 -r true --format json > $current_name.txt; mgmt_cli show nat-rulebase package "$current_policy" limit 500 -r true --format json > NAT_$current_name.txt; cat policies$N.txt | tail -$(($Lines-$N-1)) > policies$(($N+1)).txt; } ; rm policies* ;
Kind regards, Amir Senn
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hey Amir,
Just tested this in my lab and got below. PLEASE keep staying safe.
Andy
[Expert@CP-management:0]# mgmt_cli show packages -r true | grep "LAB-POLICY" > Senn_temp.txt ; cat Senn_temp.txt | cut -d':' -f2- > Senn_temp0.txt ; Lines=$(cat Senn_temp0.txt | wc -l) ; for (( N=0; $N<$Lines; N=(($N+2)))); { current=$(head -1 Senn_temp$N.txt); current=${current::-2}; current=${current:2}; echo $current >> policies0.txt; cat Senn_temp0.txt | tail -$(($Lines-$N-2)) > Senn_temp$(($N+2)).txt; } ; rm Senn_temp* ; Lines=$(cat policies0.txt | wc -l) ; for (( N=0; $N<$Lines; N=(($N+1)))); { current_policy=$(head -1 policies$N.txt); current_layer=$(mgmt_cli show package -r true name $current_policy | grep -A2 access-layers: | grep name* | cut -c8-); current_layer=${current_layer::-2}; current_layer=${current_layer:2}; current_name="${current_layer// /_}"; mgmt_cli show access-rulebase name "$current_layer" limit 500 -r true --format json > $current_name.txt; mgmt_cli show nat-rulebase package "$current_policy" limit 500 -r true --format json > NAT_$current_name.txt; cat policies$N.txt | tail -$(($Lines-$N-1)) > policies$(($N+1)).txt; } ; rm policies* ;
tail: unrecognized option '--1'
Try 'tail --help' for more information.
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Nm, disregard my last command, layer 8 issue lol
Just ran same command without changing anything and it did produce 2 files, one for network, one for nat...looks good!
Kind regards,
Andy
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
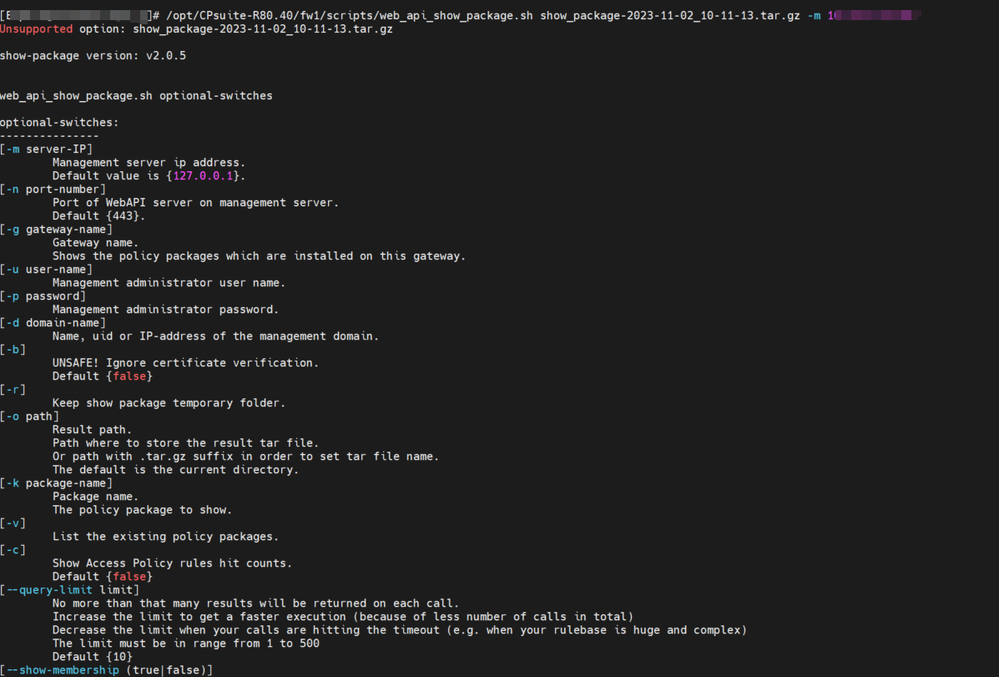
I think web_api_show_package.sh under sk120342 is what you are looking for. Give it a shot, it has been really helpful in my case.
https://support.checkpoint.com/results/sk/sk120342
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
That is true, BUT, I dont think it exports it into csv format, at least not that I can recall.
Andy
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
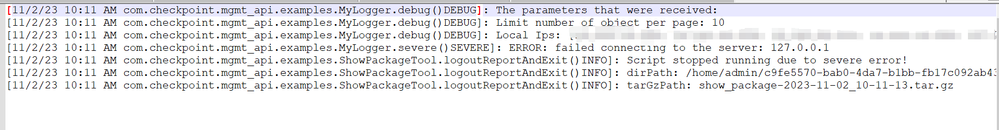
Hi,@Zolocofxp,this sk has seen, is it necessary to export the policy file through python? I performed the configuration according to the requirements of sk, but the log content was empty and the path of the exported file was not found.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
In general, you'd use the output of a series of mgmt_cli commands piped through jq, which can output in CSV.
Note that NAT rules will not include "automatic NAT" rules that are created as these are configured in the relevant object.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi PhoneBoy,mgmt_cli Export policy The bar code has a maximum of 500 lines. What are the exported commands? What additional parameters do I need to add? I saw a python export policy on github, is this reliable? And you can export it in any format you want? For example, only the source IP address, destination IP address, vpn, port, action, and log parameters are exported. Other Uids do not need to be displayed.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
To be clear, there is no single command that will dump a large rulebase and/or object database.
The API limits the number of results returned by design to keep the service performant.
This means you will have to make multiple API calls with the offset parameter (offset 500, offset 1000, etc) to get the next set of results.
You can pipe the output of mgmt_cli to jq in order to get exactly the fields you want in the exact format you want.
This tool, although not formally supported, is produced by Check Point R&D: https://community.checkpoint.com/t5/API-CLI-Discussion/Python-tool-for-exporting-importing-a-policy-...
Another tool, produced by one of our SEs, exports to/imports from CSV: https://community.checkpoint.com/t5/API-CLI-Discussion/CLI-API-Example-for-exporting-importing-and-d...
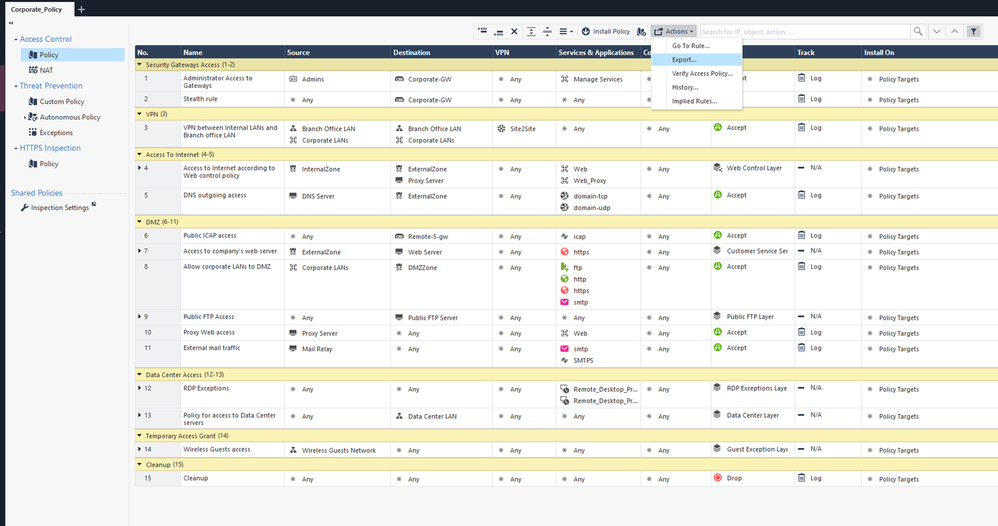
Having said all of that, SmartConsole can export the current rulebase in CSV from here:
The NAT rulebase can be exported similarly.
Note that you can not import rules directly from CSV.
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 3 | |
| 1 | |
| 1 |
Upcoming Events
Thu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldFri 09 Jan 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 42: Looking back & forwardThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: Exposing AI Vulnerabilities: CP<R> Latest Security FindingsThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldFri 09 Jan 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 42: Looking back & forwardThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter