- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity AI Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
CheckMates Fest 2026
Join the Celebration!
AI Security Masters
E1: How AI is Reshaping Our World
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
R82.10 and Rationalizing Multi Vendor Security Policies
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Developers
- :
- API / CLI Discussion
- :
- How to export and import IPS profiles and their ov...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
How to export and import IPS profiles and their overridden protections in R80.10
Prior to R80, there was a closed-source tool by Check Point called export_import_profile.
Starting with R80:
1. The back-end representation of profiles and protections has changed, so the tool is no longer supported.
2. The open API enable any customer to make their own export and import operations.
Step 1: On the source machine, export the specific Threat Prevention Profile
The show threat-profile command returns a structure of the profile's settings.
Example:
show threat-profile name MyOrganization details-level full
uid: "fa1aa324-a8cc-4dbd-bc04-f31fdb8abf61"
name: "MyOrganization "
type: "threat-profile"
domain:
uid: "a0bbbc99-adef-4ef8-bb6d-defdefdefdef"
name: "Check Point Data"
domain-type: "data domain"
active-protections-performance-impact: "medium"
active-protections-severity: "Medium or above"
confidence-level-low: "Inactive"
confidence-level-medium: "Prevent"
confidence-level-high: "Prevent"
ips: true
ips-settings:
newly-updated-protections: "staging"
exclude-protection-with-performance-impact: false
exclude-protection-with-severity: false
threat-emulation: true
anti-virus: true
anti-bot: true
Step 2: On the source machine, export IPS Protections which had their action override for this specific Threat Prevention Profile
This part is a little tricky - you have to go over all protections, and only pick the ones that have a different action for your profile.
The show threat-protections command returns the protections.
There is no way to get all the IPS Protections as one response, since that would make the output so big it will fail to return. Therefore we have to use the "offset" parameter to advance and get 50 protections every time.
In the example below, the first protection just happened to have an override action for the "MyOrganization" profile. The second protection did not have an override action for the "MyOrganization" profile.
Example:
show threat-protections offset 0 details-level full
protections:
- uid: "8027f5c8-1bac-cf49-99a3-59a89a35cdb6"
name: "3Com Network Supervisor Directory Traversal"
type: "threat-protection"
domain:
uid: "41e821a0-3720-11e3-aa6e-0800200c9fde"
name: "SMC User"
domain-type: "domain"
severity: "High"
confidence-level: "Medium"
performance-impact: "Low"
release-date: "20091124"
update-date: "20091124"
profiles:
- name: "Basic"
uid: "eb39a60d-c454-49f5-a28c-a89aa5bd2e09"
default:
action: "Inactive"
track: "log"
capture-packets: false
final:
action: "Inactive"
track: "log"
capture-packets: false
- name: "Strict"
uid: "caf8b711-d762-4c1e-82d5-6af2549b2869"
default:
action: "Prevent"
track: "log"
capture-packets: false
final:
action: "Prevent"
track: "log"
capture-packets: false
- name: "MyOrganization"
uid: "fa1aa324-a8cc-4dbd-bc04-f31fdb8abf61"
default:
track: "log"
capture-packets: false
override:
action: "Prevent"
track: "log"
capture-packets: false
final:
action: "Prevent"
track: "log"
capture-packets: false
comments: ""
follow-up: false
ipsAdditionalProperties:
...
name: "3Com TFTP Server Transporting Mode Remote Buffer Overflow"
type: "threat-protection"
- name: "MyOrganization"
uid: "fa1aa324-a8cc-4dbd-bc04-f31fdb8abf61"
default:
action: "Inactive"
track: "log"
capture-packets: false
final:
action: "Inactive"
track: "log"
capture-packets: false
...
Step 3: On the target machine, create the new profile.
The add threat-profile command creates a new Threat Prevention Profile.
You have to convert the output from step 1 to a command-line with the values.
Example:
add threat-profile name MyOrganization active-protections-performance-impact "medium" active-protections-severity "Medium or above" confidence-level-low "Inactive" confidence-level-medium "Prevent" confidence-level-high "Prevent" ips true ips-settings.newly-updated-protections "staging" ips-settings.exclude-protection-with-performance-impact false ips-settings.exclude-protection-with-severity false threat-emulation true anti-virus true anti-bot true
Step 4: On the target machine, set protection actions for the specific protections that were exported at step 2.
The set threat-protection command lets you change the action of the protection for a given profile.
Example:
set threat-protection name "3Com Network Supervisor Directory Traversal" overrides.1.profile MyOrganization overrides.1.action Prevent
12 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Tomer, I am concerned that CP is beginning to rely too heavily on the programmatic functionality for trivial and common tasks.
Having these capabilities in addition to a two-click action this is supposed to be, is great, as it will empower those capable and in need of a comprehensive scripted operations to do this job, while not alienating already overworked mid-market admins who were sold on the capabilities, simplicity and intuitiveness of the SmartConsole and the Single Pane of Glass idea.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I agree that if this was a standard common thing that most of our customers were doing then we should have provided a 1-click solution.
Importing an exporting IPS settings between different machines is considered a deployment / provisioning scenario, and typically those scenarios could have more steps. So in this particular case - I am in favor of giving building blocks and letting others utilize them.
There are other cases in which we have API and no simple UI, for example - a view of all objects that have the same IP of another object - and to those cases we will work to add the simple UI out of the box.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I suspect that this is more of the operational issue in addition to deployment and migration.
If situation described in sk113748 arises and leads to the need of IPSClean files to replace all the corrupted IPS configuration files, it could be handy to have the import and export capabilities.
Incidentally, are the IPS profiles with overrides a part of the Gaia Backup?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
IPSClean is no longer ![]() We have revision revert for IPS since R80.
We have revision revert for IPS since R80.
Gaia Backup retains all security management configuration.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@Tomer Sole
That API Call is very helpful! Is there a similar API to set the Recommended and Default Inspection profiles under the Inspection Settings?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Might be a better question for Amiad Stern
If I had to guess, it's something that will require using the generic object API, though through a cursory glance, I do not see what property it is.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Please confirm if ips_export_import command was introduced back in R80.20.
Page 38.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I'm not seeing this utility here in my R80.20 standalone installation VM, so unless this is a special package that needs to be installed separately it looks like the answer is no.
Gaia 4.18 (R82) Immersion Tips, Tricks, & Best Practices Video Course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
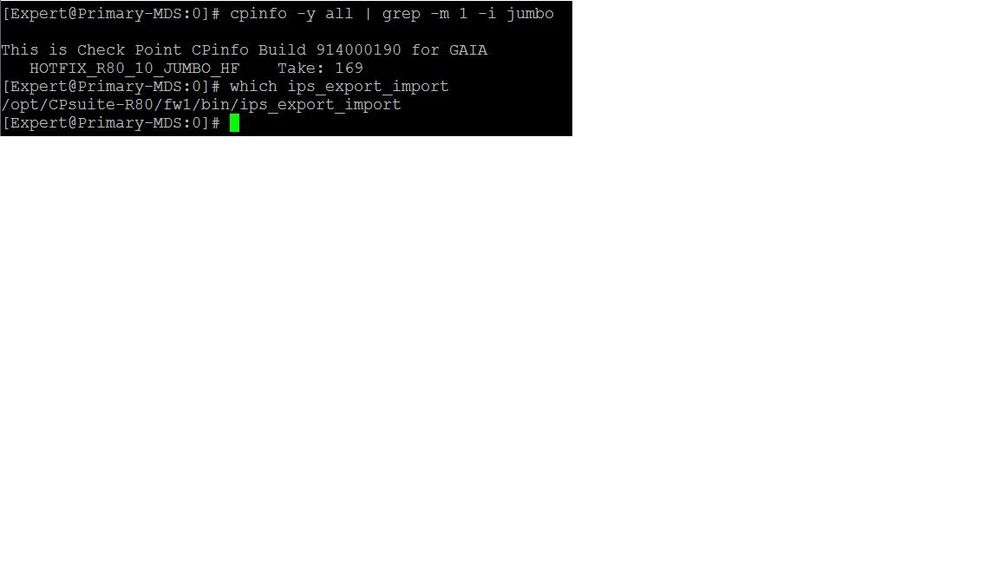
Thank you for looking into it Tim. I have R80.10 with take 169 installed on my machine and binary is located at
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Ramchand and All,
I am also searching for a simple and straight forward way to export / import only IPS configuration.
In the last R80.20 take 47 this ips_export_import utility is not presented (attached screenshot).
I checked the provided Thread Prevention Administration guide for R80.30 version, which is not available for download, at it seems that this utility is removed according to the revision history of the document (attached screenshot).
Ramchand, can you please advise when this IPS configuration export functionality will be available?
Thanks.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
An open API procedure Tomer outlined above would allow similar export & import functionality.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 3 | |
| 1 | |
| 1 |
Upcoming Events
Thu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldFri 09 Jan 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 42: Looking back & forwardThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: Exposing AI Vulnerabilities: CP<R> Latest Security FindingsThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldFri 09 Jan 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 42: Looking back & forwardThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter