Just to compare, attached below typical output of R8x show-package tool. As you can see, information completely replaces the same functionality of R7x Web Visualization Tool.
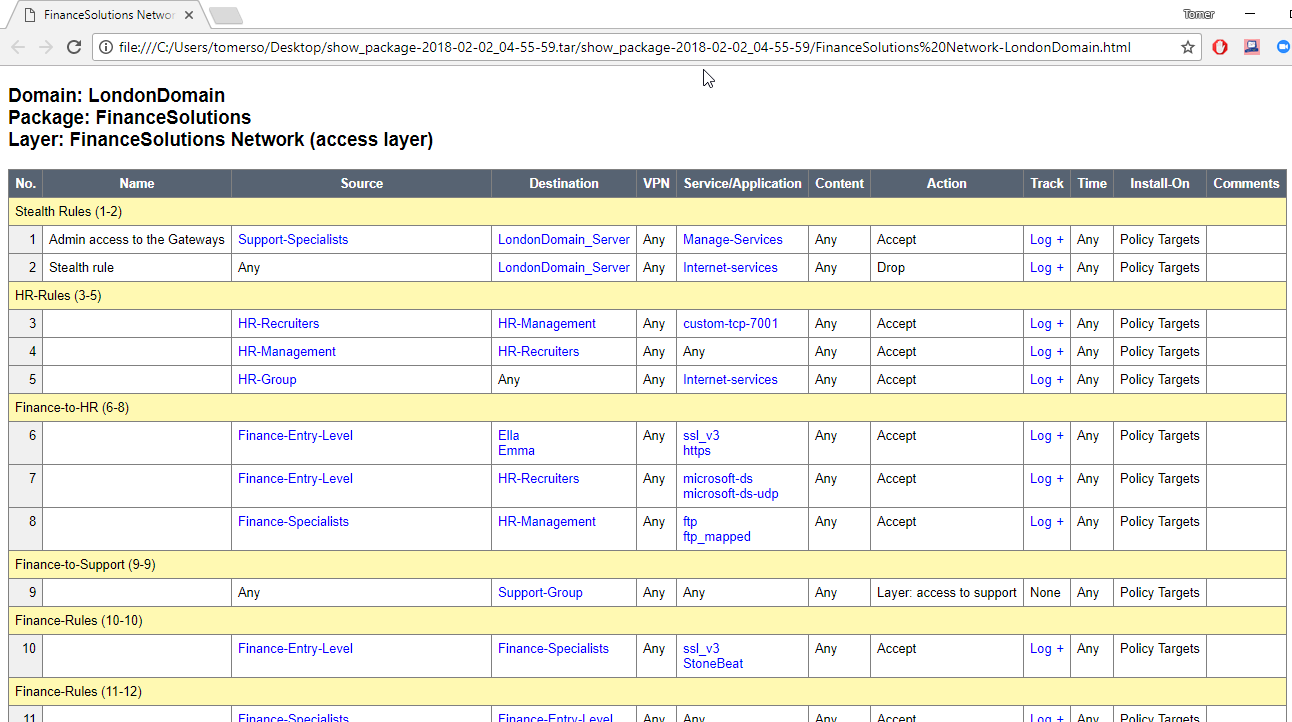
This thread however discusses how to get full rule information when searching for usages of objects.
Option 1: run "where used", collect the UID's of the rules, then run "show access-rule" for each rule UID.
Option 2: run "where used" with "details-level full". This will show the full objects that use the given object. However, it will show a lot of other information and may result with a slow response.
Option 3: run "where used", collect the rule positions, then look at the show-package HTML output (see image above) and locate the rule.
Let's demonstrate option 1:
Step 1: where used for host "Marco". We want to see its indirect usages, because Marco belongs to a network group which appears in some rules. From the output we would like to isolate the rule UID and the layer UID because both parameters are required for the next step. So we will use JQ to parse the output and select only the things that we care about.
mgmt_cli where-used name Marco indirect true -s id.txt --format json | jq -r '."used-indirectly"."access-control-rules"[] | (.rule.name // "no rule name", .rule.uid, .layer.name, .layer.uid)'
no rule name
97ed7f41-f56d-4ef5-99e9-9f698ad55902
FinanceSolutions Network
19942103-1419-4e71-b655-e1aad4c82535
no rule name
86f56fc4-7652-4518-8d94-3f9ec6ced892
FinanceSolutions Network
19942103-1419-4e71-b655-e1aad4c82535
no rule name
1030a2d1-7663-462f-b43b-8825abf39e21
FinanceSolutions Network
19942103-1419-4e71-b655-e1aad4c82535
no rule name
c0d19b8f-10d7-4ea2-8684-61968c7e94d7
FinanceSolutions Network
19942103-1419-4e71-b655-e1aad4c82535
no rule name
69ea551c-ad13-4a5f-8b68-897928119da8
FinanceSolutions Network
19942103-1419-4e71-b655-e1aad4c82535
no rule name
5f0d2800-1e9d-44f6-9f39-7953a33b82a2
FinanceSolutions Network
19942103-1419-4e71-b655-e1aad4c82535
no rule name
0fb52774-487a-4e3c-afcc-65d1ccbaffb7
FinanceSolutions Network
19942103-1419-4e71-b655-e1aad4c82535
We got groups of 4 - rule name (which shows "no rule name" in case it has no name), rule UID, layer name, layer UID.
Now we can run show access-rule on each result to see the full rule. For example, for the first result:
mgmt_cli show access-rule uid 69ea551c-ad13-4a5f-8b68-897928119da8 layer 19942103-1419-4e71-b655-e1aad4c82535 -s id.txt




