- Products
- Learn
- Local User Groups
- Partners
- More
Call For Papers
Your Expertise, Our Stage
Ink Dragon: A Major Nation-State Campaign
March 11th @ 5pm CET / 12pm EDT
AI Security Masters E4:
Introducing Cyata - Securing the Agenic AI Era
The Great Exposure Reset
AI Security Masters E3:
AI-Generated Malware
CheckMates Go:
CheckMates Fest
📕 Referenced in the book: Max Power 2020
▶️ Featured in How to use fw monitor
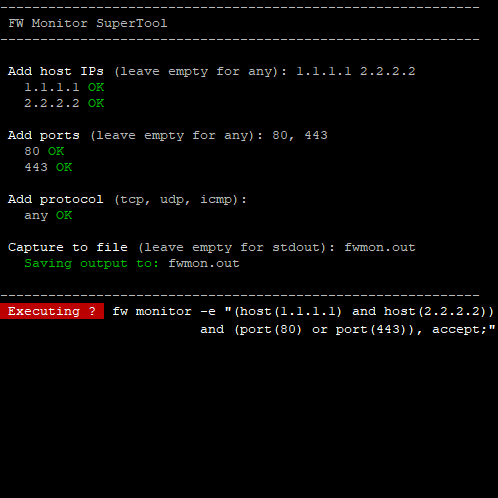
One-liner (Bash) to assist running fw monitor on Check Point firewall gateways.
In expert mode run:
if [[ `$CPDIR/bin/cpprod_util FwIsFirewallModule 2>/dev/null` != *'1'* ]]; then echo; tput bold; echo ' Not a firewall gateway!'; tput sgr0; echo; else echo; printf '%.s-' {1..60}; echo; echo ' FW Monitor SuperTool'; printf '%.s-' {1..60}; echo; echo; tput bold; echo -n ' Add host IPs '; tput sgr0; echo -n '(leave empty for any): '; read _hosts; b='0'; case $_hosts in '') echo -n ' any '; tput setaf 2; echo 'OK'; tput sgr0;; *) _hosts=($(echo $_hosts | tr ',;:|()#<>' ' ' | tr -s ' ')); for a in ${_hosts[@]}; do if [[ `ipcalc -ms $a` == *'='* ]] && [[ $a == *'.'* ]]; then echo -n ' '$a' '; tput setaf 2; echo 'OK'; b='1'; tput sgr0; else echo -n ' '$a' '; tput setaf 1; echo 'Bad syntax!'; tput sgr0; fi; done; esac; echo; tput bold; echo -n ' Add ports '; tput sgr0; echo -n '(leave empty for any): '; read _ports; d='0'; case $_ports in '') echo -n ' any '; tput setaf 2; echo 'OK'; tput sgr0;; *) _ports=($(echo $_ports | tr ',;:|()#<>' ' ' | tr -s ' ')); for a in ${_ports[@]}; do if [[ $a != *[^0-9]* ]]; then echo -n ' '$a' '; tput setaf 2; echo 'OK'; d='1'; tput sgr0; else echo -n ' '$a' '; tput setaf 1; echo 'Bad syntax!'; tput sgr0; fi; done; esac; echo; tput bold; echo -n ' Add protocol '; tput sgr0; echo -n '(tcp, udp, icmp): '; read _prot; c='0'; case $_prot in '') echo -n ' any '; tput setaf 2; echo 'OK'; tput sgr0;; *) _prot=($(echo $_prot | tr ',;:|()#<>' ' ' | tr -s ' ')); for a in ${_prot[@]}; do case $a in tcp|udp|icmp) echo -n ' '$a' '; tput setaf 2; echo 'OK'; c='1'; tput sgr0;; *) echo -n ' '$a' '; tput setaf 1; echo 'Unknown protocol!'; tput sgr0; esac; done; esac; echo; tput bold; echo -n ' Capture to file '; tput sgr0; read -p '(leave empty for stdout): ' _file; if [[ -n $_file ]]; then tput setaf 2; echo -n ' Saving output to: '; tput sgr0; echo $_file; else tput setaf 2; echo ' Output to CLI'; tput sgr0; fi; echo; printf '%.s-' {1..60}; echo; _sxl='0'; tput setab 1; tput setaf 7; tput bold; echo -n ' Executing ? '; tput sgr0; echo -n ' '; if [[ `fw monitor -h 2>&1` != *'-F'* ]]; then case `fwaccel stat | grep 'Accelerator Status :' | cut -c 22-` in on) _sxl='1'; esac; fi; if [[ $_sxl == '1' ]]; then _run='fwaccel off; fw monitor'; else _run='fw monitor'; fi; if [[ -z $_file ]]; then _run+=' -T'; if [[ `fw monitor -h 2>&1` != *'-F'* ]]; then _run+=' -e "'; if [[ $b == '1' && $d == '1' ]]; then _run+='('; elif [[ $b == '1' && $c == '1' ]]; then _run+='('; fi; for a in ${_hosts[@]}; do if [[ `ipcalc -ms $a` == *'='* ]] && [[ $a == *'.'* ]]; then _run+='host('$a') and '; fi; done; if [[ $b == '1' && $d == '1' ]]; then _run=${_run%?????}; _run+=')'; elif [[ $b == '1' && $c == '1' ]]; then _run=${_run%?????}; _run+=')'; fi; if [[ $b == '1' && $d == '1' ]]; then _run+=' and ('; elif [[ $d == '1' && $c == '1' ]]; then _run+='('; elif [[ $b == '1' && $c == '1' ]]; then _run+=' and ('; fi; for a in ${_ports[@]}; do if [[ $a != *[^0-9]* ]]; then _run+='port('$a') or '; fi; done; if [[ $b == '1' && $d == '1' ]]; then _run=${_run%????}; _run+=')'; elif [[ $d == '1' && $c == '1' ]]; then _run=${_run%????}; _run+=')'; elif [[ $b == '0' && $d == '1' ]]; then _run=${_run%????}; elif [[ $b == '1' && $d == '0' ]]; then _run=${_run%?????}; fi; if [[ $b == '1' || $d == '1' ]]; then if [[ $c == '1' ]]; then _run+=' and ('; fi; fi; for a in ${_prot[@]}; do case $a in tcp) _run+='ip_p=6 or ';; udp) _run+='ip_p=11 or ';; icmp) _run+='ip_p=1 or '; esac; done; if [[ $b == '1' || $d == '1' ]]; then if [[ $c == '1' ]]; then _run=${_run%????}; _run+=')'; fi; elif [[ $b == '1' && $d == '0' && $c == '0' ]]; then _run=${_run%?????}; elif [[ $b == '0' && $d == '1' && $c == '0' ]]; then _run=${_run%?????}; elif [[ $b == '0' && $d == '0' && $c == '1' ]]; then _run=${_run%????}; fi; if [[ $b == '1' || $d == '1' || $c == '1' ]]; then _run+=', '; fi; _run+='accept;"'; else _run+=' -F "0,0,0,0,0"'; fi; if [[ -n $_file ]]; then _run+=' -o /var/log/'$_file; fi; if [[ $_sxl == '1' ]]; then _run+='; fwaccel on'; fi; tput bold; echo -n $_run; tput sgr0; read -sn1; echo; case $REPLY in '') eval $_run;; *) echo 'Abort!'; esac; echo; unset _hosts _ports _prot _file _sxl _run a b c d; fi; fiSuperTool interactively asks for all data to build up the correct syntax to run fw monitor.
SuperTool adjusts the resulting fw monitor syntax according to the requirements of the gateway it is run.
It identifies if:
It also checks and deactivates SecureXL during fw monitor execution if necessary.
SuperTool is also integrated within our ccc script.
Attention! *Work in progress*
SuperTool will be further improved to support:
FW Monitor developers: @Coby_Schmidt (LinkedIn), ...
FW Monitor documentation: @Uri_Lewitus (LinkedIn)
FW Monitor memory usage: sk160954
📕 Referenced in the book: Max Power 2020
▶️ Featured in How to use fw monitor
One-liner (Bash) to assist running fw monitor on Check Point firewall gateways.
In expert mode run:
if [[ `$CPDIR/bin/cpprod_util FwIsFirewallModule 2>/dev/null` != *'1'* ]]; then echo; tput bold; echo ' Not a firewall gateway!'; tput sgr0; echo; else echo; printf '%.s-' {1..60}; echo; echo ' FW Monitor SuperTool'; printf '%.s-' {1..60}; echo; echo; tput bold; echo -n ' Add host IPs ';
@Danny , this is awesome! Happy to see CCC evolution over the past year! I hope that CP will decide one day to officially support or endorse it.
Danny,
thanks a lot for this, simplifies the daily work.
I used https://tcpdump101.com to built complex fw monitor filter but your tool make this easy.
applause, applause
Wolfgang
Danny,
thanks a lot for this, simplifies the daily work.
I used https://tcpdump101.com to built complex fw monitor filter but your tool make this easy.
applause, applause
Wolfgang
;Very nice Danny
but isnt fw monitor changed in r80.20 take 87?
fw monitor -e is changed with filter function isnt?
From me 100 points. 👍
I'll add the one-liner to my one-liner list:
Hi @Danny
I'm having issues with this working? Paste it straight into the CLI or do I need to enter this into a script?
Hi @Tom_Cripps ,
just paste it straight into your Expert mode CLI.
Hi @Tom_Cripps ,
just paste it straight into your Expert mode CLI.
;Hi Danny,
nice script! Well done!
I would highly recommend to add a friendly reminder at the end of the script that performing "fwaccel off" can increase the load of the gateway or could lead to outages if the gateways is already well loaded.
Cheers
Sven
Hi Danny,
nice script! Well done!
I would highly recommend to add a friendly reminder at the end of the script that performing "fwaccel off" can increase the load of the gateway or could lead to outages if the gateways is already well loaded.
Cheers
Sven
;
that‘s why this SuperTool checks if SecureXL is enabled on versions prior to R80.20 and only disables it while running fw monitor. I checked if disabling SecureXL just for the specified IP addresses (sk194468) would be an option, unluckily this requires adjustments on the SmartCenter, so I had to stay with fwaccel off/on.
that‘s why this SuperTool checks if SecureXL is enabled on versions prior to R80.20 and only disables it while running fw monitor. I checked if disabling SecureXL just for the specified IP addresses (sk194468) would be an option, unluckily this requires adjustments on the SmartCenter, so I had to stay with fwaccel off/on.
;This doesn't work at all. No matter what values I give it it only generates the following command:
Executing ? fw monitor -F "0,0,0,0,0"
I'm using R80.20 - Build 128 in expert mode. I hate this new syntax for fw monitor. Can someone tell me how to translate the following from the old fw monitor syntax to the new style?
fw monitor -e "accept (host (1.2.3.4) and net(13.104.0.0,14));"
This doesn't work at all. No matter what values I give it it only generates the following command:
Executing ? fw monitor -F "0,0,0,0,0"
I'm using R80.20 - Build 128 in expert mode. I hate this new syntax for fw monitor. Can someone tell me how to translate the following from the old fw monitor syntax to the new style?
fw monitor -e "accept (host (1.2.3.4) and net(13.104.0.0,14));"
;This is the expected behaviour as -F is currently not supported (see my initial post).
So the tool is working as it should and correctly informs you to use fw monitor with simple filters instead of inspect code.
Outstanding work Danny.
My issue with fw monitor has always been its complexity to run a command. Granted, once you have a command written out, its just a case of changing variables - however in the middle of a change, or whilst troubleshooting a situation, getting the syntax completely correct is just a pain for someone like me.
Ill start using fw monitor more proficiently now!
Thank you
Outstanding work Danny.
My issue with fw monitor has always been its complexity to run a command. Granted, once you have a command written out, its just a case of changing variables - however in the middle of a change, or whilst troubleshooting a situation, getting the syntax completely correct is just a pain for someone like me.
Ill start using fw monitor more proficiently now!
Thank you
;I tried running the script but it doesn't work. Below is my gateway version.
This is Check Point's software version R80.30 - Build 484
kernel: R80.30 - Build 478
This tool used to work great for me every time. I am running R80.30 - Build 217 and no matter what I enter into the tool what shows up to be executed is "fw monitor -T -F "0,0,0,0,0"". This is true when simply entering a single ip address into the tool and nothing else.
This tool used to work great for me every time. I am running R80.30 - Build 217 and no matter what I enter into the tool what shows up to be executed is "fw monitor -T -F "0,0,0,0,0"". This is true when simply entering a single ip address into the tool and nothing else.
;I have version R80.40 running, but each IP address is ingored in the filer, result is always :
fw monitor -T- F "0,0,0,0,0"
What is going wrong, and how can I solve this ?
Known limitation. Quoted from above:
Attention! *Work in progress*
SuperTool will be further improved to support:
The -F syntax isn't too tough to come up with on your own (-F srcIP,srcPort,dstIP,dstPort,IPProto), but just keep in mind some points mentioned in my Max Capture series:
Known limitation. Quoted from above:
Attention! *Work in progress*
SuperTool will be further improved to support:
The -F syntax isn't too tough to come up with on your own (-F srcIP,srcPort,dstIP,dstPort,IPProto), but just keep in mind some points mentioned in my Max Capture series:
About CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
