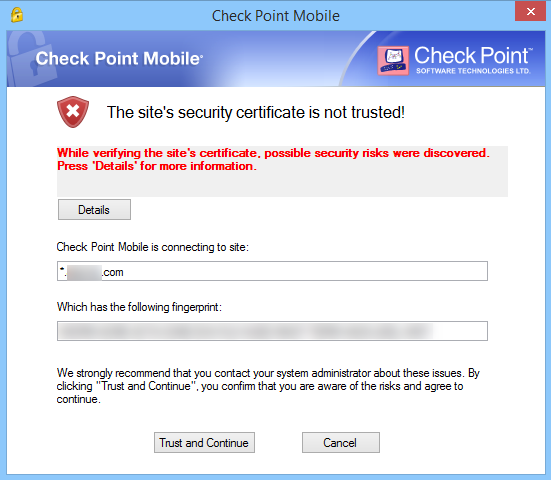
Hi David,
I have gotten it to work, and I will have a write-up posted on another thread here which shows the most direct and efficient way to do it as far as I have found.
TAC pointed me toward this SK.
How to generate Server Certificate Signing Request (CSR) and import the new 3rd Party certificate to...
There are two command line examples there in stage one, they are not two steps. That bit me because I did the steps without reading ahead. You want to use the second example, as nobody is supporting 1024bit signing anymore
====================================
To Generate the 2048 bit CSR please use below command:
[Expert@GW]# cpopenssl req -new -newkey rsa:2048 -out <CERT.CSR> -keyout <KEYFILE.KEY> -config $CPDIR/conf/openssl.cnf
====================================
Bottom line, when you use the cpopenssl command to generate the CSR and the KEY files, it will prompt you for a few attributes; put the FQDN of the host in as the CN when it asks you for it.
When you go to your CA they usually have a field where you can add SANs when you request a duplicate, put that FQDN hostname in as one of them, and that is half the battle.
My write up will cover the whole generation and import process, stay tuned.
Note, there is a significant delay after importing the finished cert, publishing the changes, and installing the policy.
I am not sure if the gateway waits for a window before the new cert becomes internet facing, but in my case it was more than 10 minutes. I did not restart any services to get it to happen, either.