As of February 3, 2019, Administrators of SandBlast Mobile can now set Granular Policies. These policies can be assigned to specific users, specific groups, or all users.
Granular Policies will allow you to configure policies for different groups of users, such as enforcing stricter security control for executives.
When this capability is released, the current policies you have configured for Device, Application, Network Protection, Wi-Fi Network Protection, and Cellular Network Protection will be moved to the Global rulebase so that you and your users will not have policy enforcement interruptions during the roll-out.
New Policy tab
Navigating to the Policy tab, you are presented with a rulebase list that has the default Global policy profile already listed.

Rulebase
When you first navigate to the Policy tab, you are presented with a rulebase list that has the default Global policy profile already listed.
As you add new policy profiles for different groups/users, you will add them to the rulebase to assign them to the appropriate groups/users.
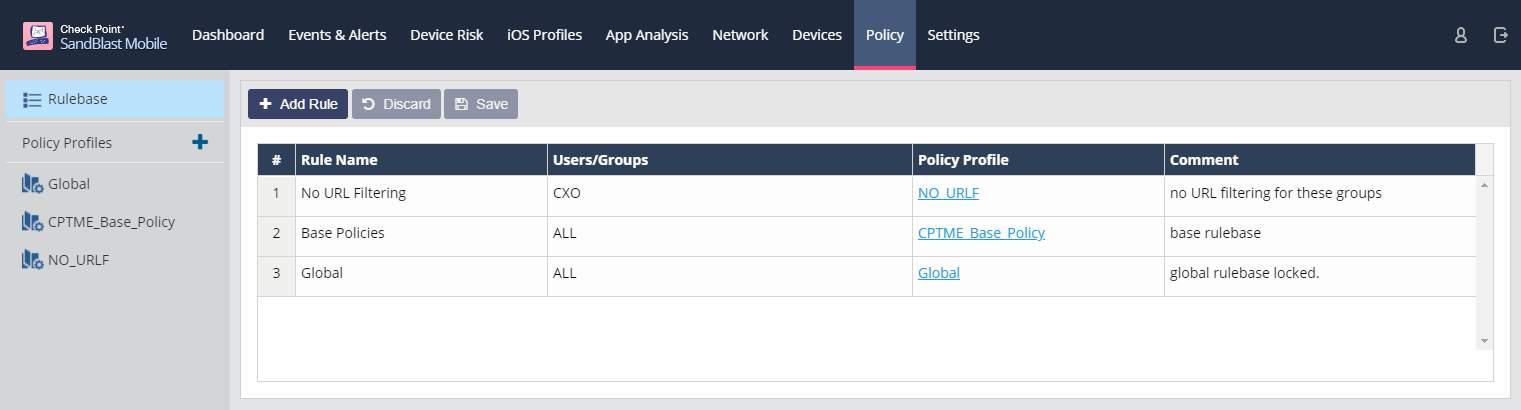
This list is processed in order from 1, 2, 3, etc. until a user or group match for the user is made, then that policy is applied to the user.
So the more granular the policy, the higher in the list it should be listed with the Global policy being at the bottom of the list.
To add a policy to the rulebase, click "Add Rule".

A line will be added to the top of the rulebase list.
Enter in a Rule Name, select the users or groups from the drop-down list, select the policy profile from the drop-down list, and enter in a comment.
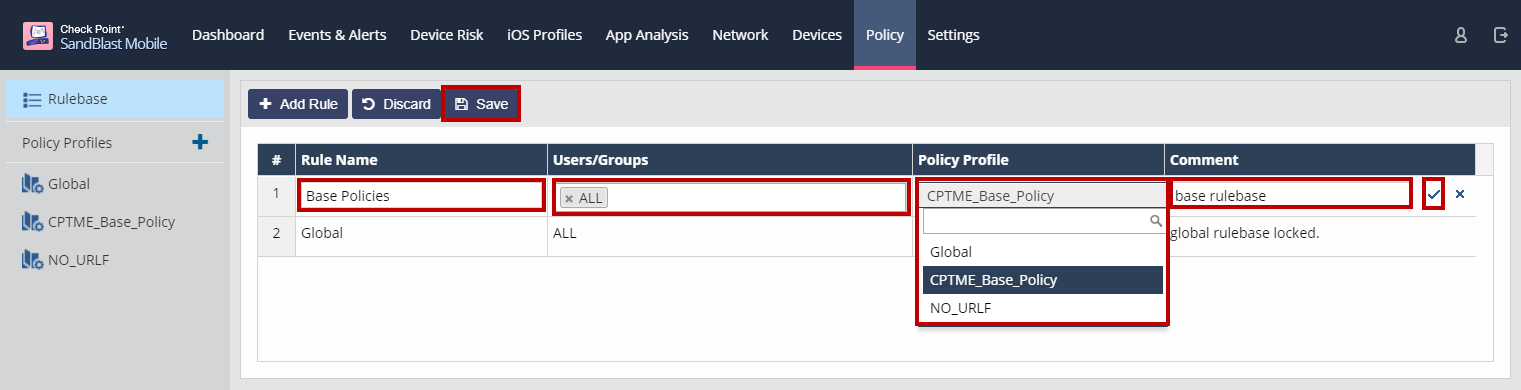
Click the checkmark at the end of the rule.
When you are done adding all of policies to the rulebase, click "Save".
Policy Profiles
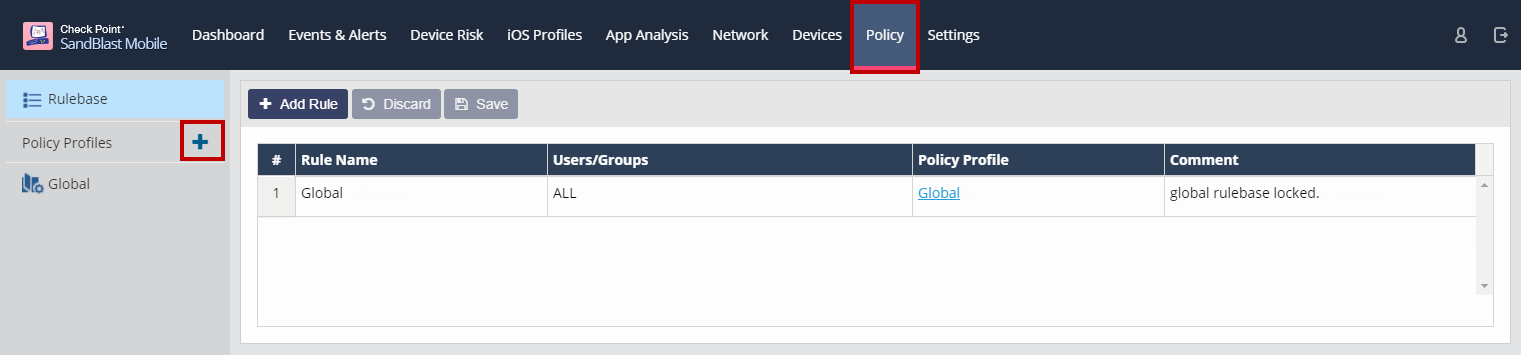
You can edit the Global policy profile as this is the default policy for all devices.
You create a new policy profile by clicking on the "+".
Give the policy a unique name and a description.
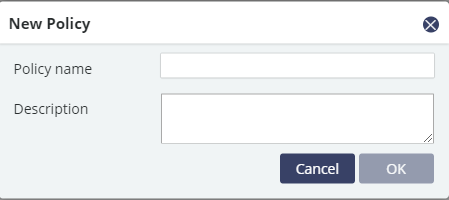
Click "OK".
After you click OK, you are taken to the profile editing view. You can always edit a profile by selecting it from the Policy Profiles list.
Device Policies
On the Device tab, you can configure general, Android, and iOS specific policies, such as when a device is marked "inactive" if it hasn't communicated with the SandBlast Mobile Dashboard for a set number of days, or raising the risk level of a device running an OS version below Android 6.0.
This is also the place to whitelist proxy server IP addresses.
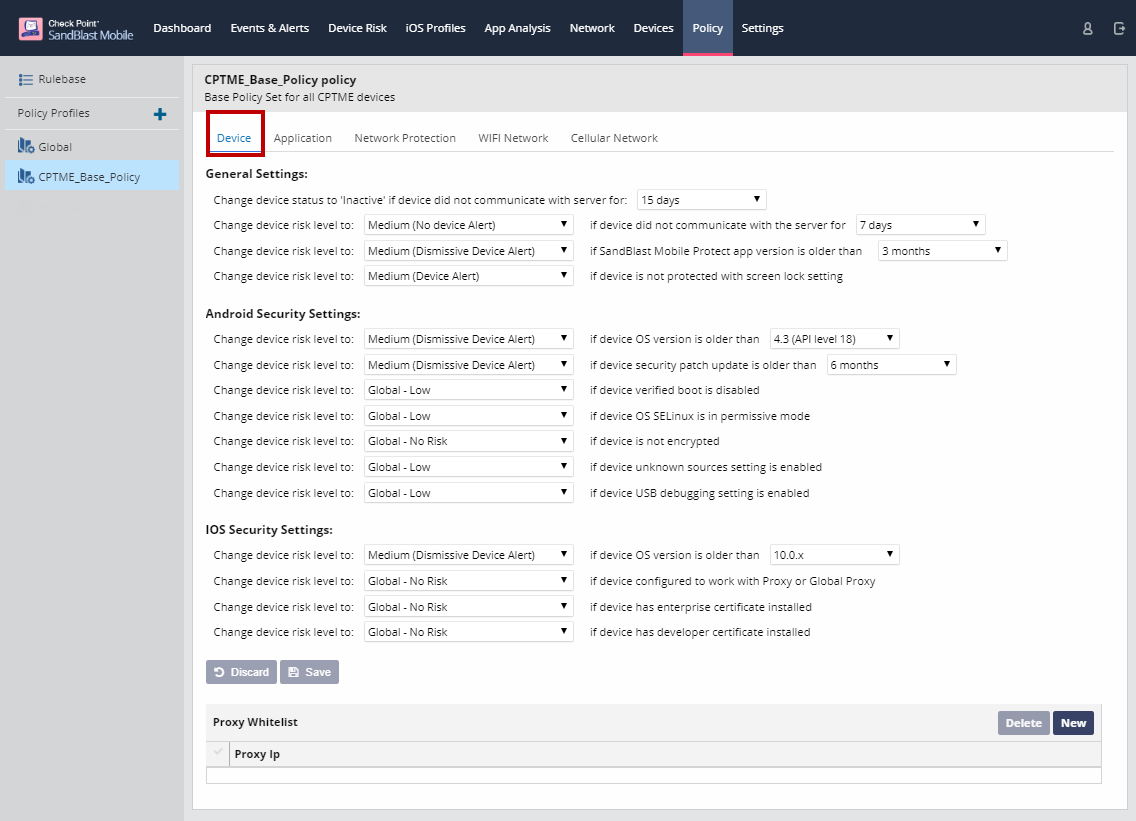
Click "Save" to save policy changes.
Application Policies
On the Application tab, you can configure the risk level associated with different application classifications.
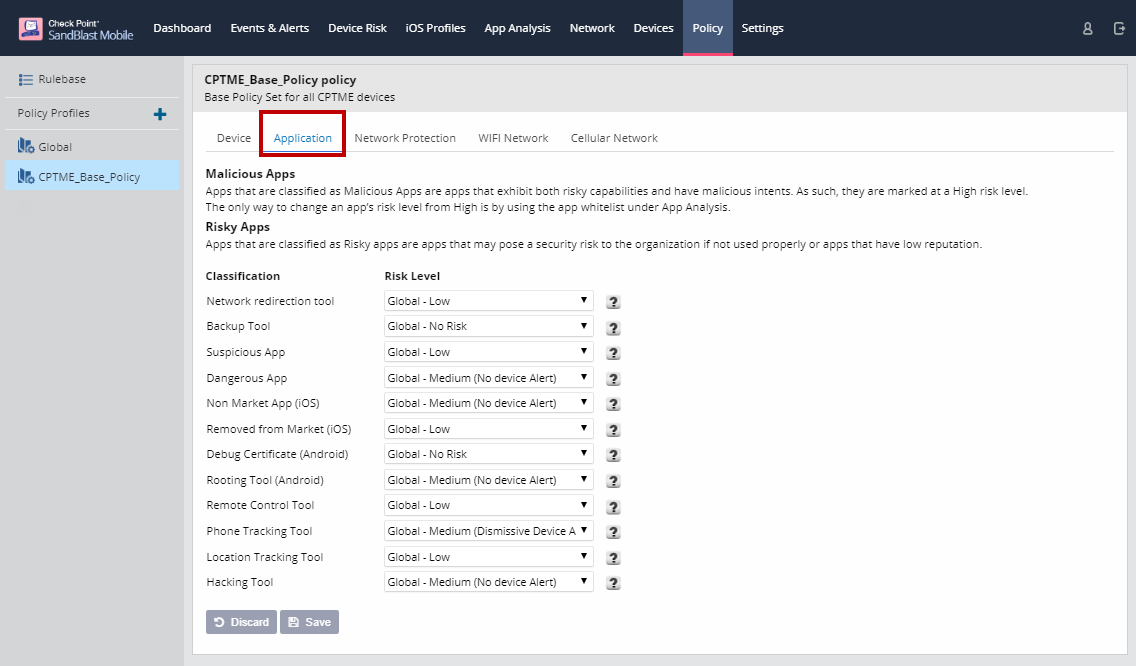
Click "Save" to save policy changes.
On-device Network Protection Policies
On-device Network Protection enhances SandBlast Mobile's advanced mobile threat protection and establishes a new mobile security paradigm to prevent emerging Gen V network attacks.
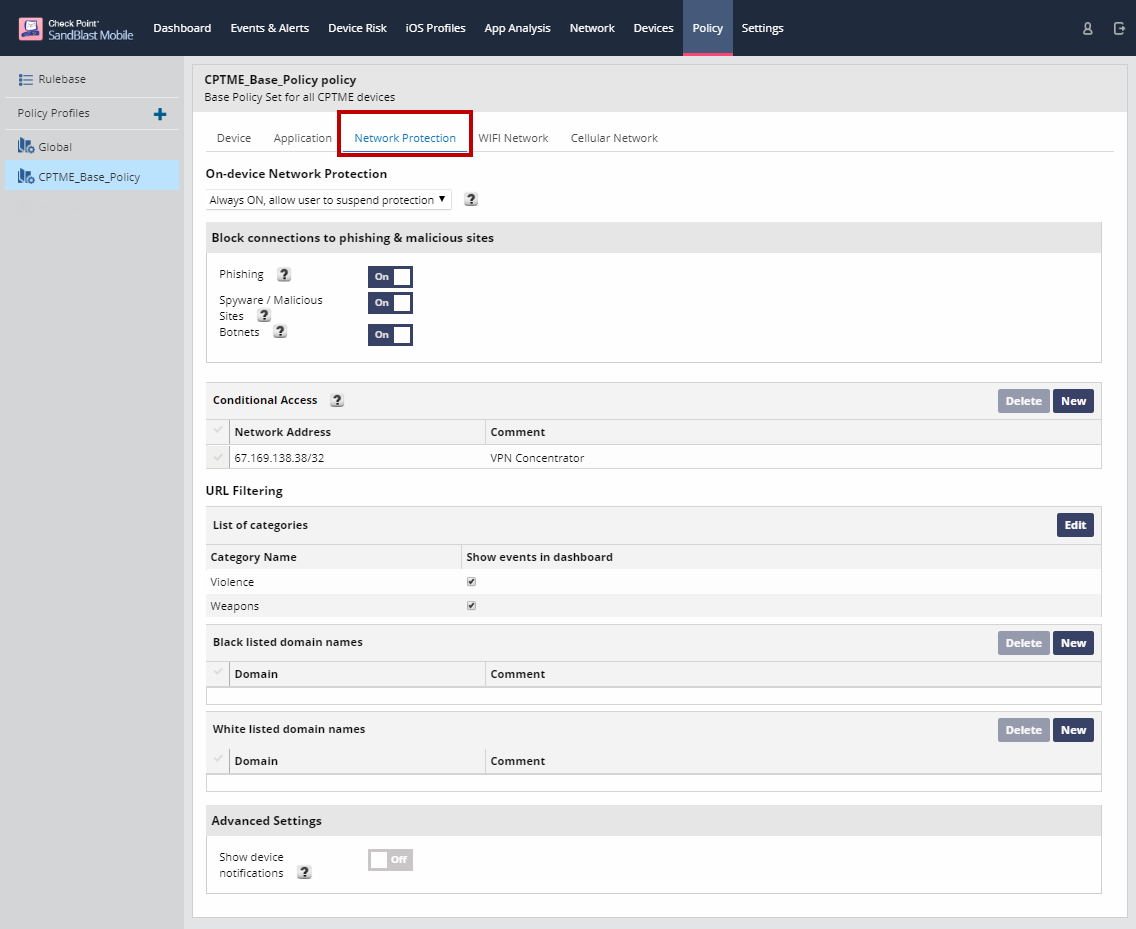
The configuration of Network Protection policies is the same as covered in these articles:
Wi-Fi Network Policies
On the WiFi Network tab, you can set the risk level for Wi-Fi Network Protection settings, add additional servers to be used for MitM detection, enable Geolocation collection, and upload SSL certificates you wish to whitelist.
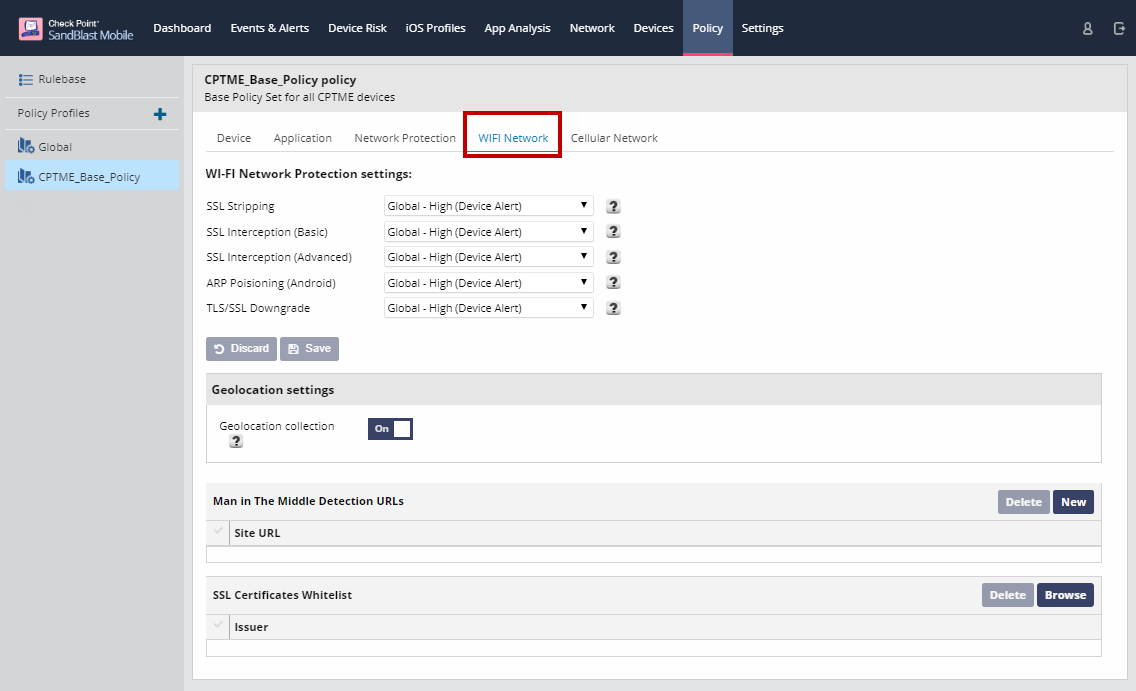
Enable Geo Location
This only enables it from the Dashboard side; the user must still enable the SandBlast Mobile Protect app to use Location on their device in order for Geo Location information to be gathered.
This information is used to provide map detail on the Network tab.
Whitelisting Corporate Certificates
When checking for SSL interception attacks (SSL Bumping), the Solution checks if the destination site’s SSL certificate is the one expected. If it is not, the Solution alerts that there may be an attack, even if the received certificate is in the root CA list of the device.
However, many organizations inspect employee traffic and to the Solution it appears that this is indeed an advanced SSL interception attack because:
The organization requires the organization’s certificate be installed on the device as a root CA
The SSL interception of the traffic in an organizational proxy
In order to avoid alerting on the organization’s own certificate, the organization can whitelist its own certificates through this screen. This way the Solution will not alert an "attack" involving these certificates.
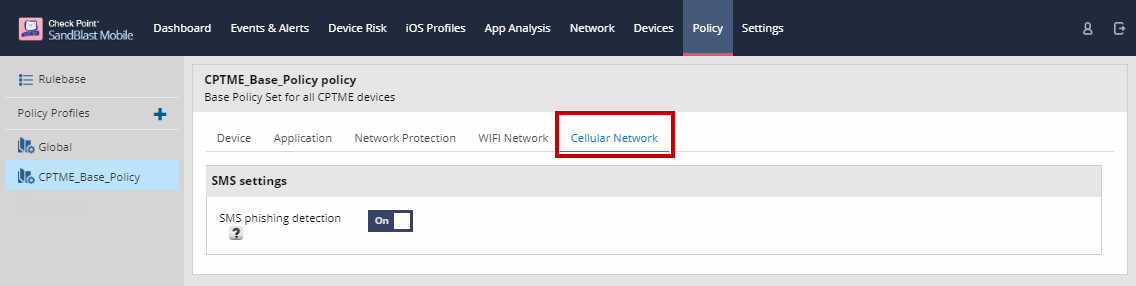
Cellular Network Policies
On the Cellular Network tab, you can enable/disable SMS phishing detection/protection.
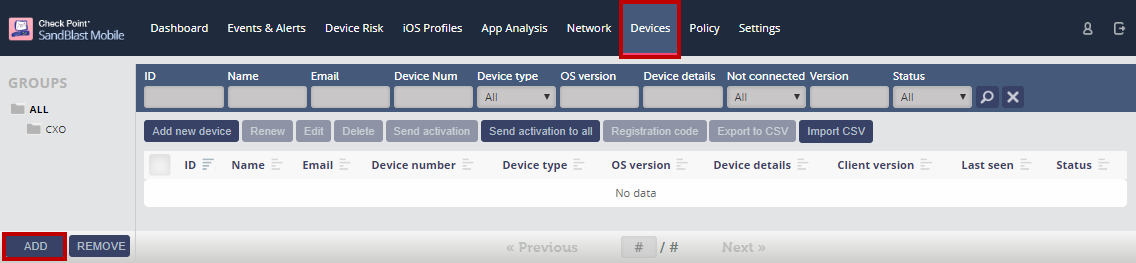
Adding a Device Group
Navigating to Devices, click "ADD" at the bottom of the Groups list.
In the pop-up window, enter in a group name.
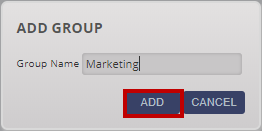
Click "ADD".
When adding devices, you can assign them to their appropriate groups.
NOTE: When integrating with a Device Management platform, the devices and device groups are imported from that platform. And "Add new device" and "Add" groups are disabled.















