ICAP integration for R77.30 and R80.10
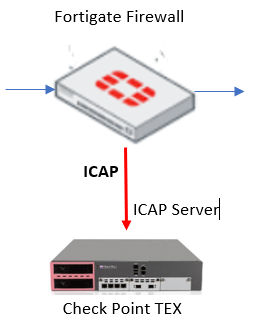
Configuring ICAP Server on Check Point Sandblast Appliance (TEX) or Gateway:
Enable ICAP-Server on TEX Appliance see SK111306 and configure Thread rules in DashBoard.
Use Hotfix 286 or higher for R77.30.
Enable ICAP Server
Start ICAP server on TEX appliance or gateway:
# icap_server start
Enable ICAP Logs
# tecli advanced remote emulator logs enable <<< Hotfix 286 or higher automatically activates logging.
Enable firewall rule to connect ICAP Server (TEX Appliance)
Source: Fortigate
Destination: "ip-address of sandblast appliance"
Port: 1344
Configure Thread Rules
Configure Thread rules in SmartDashboard
.
Configuring ICAP on Fortigate:
ICAP Servers
- Go to Security Profiles > ICAP Servers and click on Create New.
- Enter a Name "sandblast_server" for the server.
- Enter the server's IP Address “ip-address of sandblast appliance”
- Set the Port; 1344 is default TCP port used for the ICAP traffic.
Maximum Connections
config icap server
edit sandblast_server
set max-connection 100 <<< You can configure this on sandblast appliance in config files. Set the same value. If you overstay the value you become an ICAP error!
end
Profile
- Go to Security Profiles > ICAP and click on Create New.
- Enter a Name "Sandblast_Profile" for the server.
- Enable settings as required.
- Enable Request Processing allows the ICAP server to process request messages. If enabled this setting will also require:
- Server - This is the name of the ICAP server >>> sandblast_server
- Path - This is the path on the server to the processing content “icap://<ip-address of sandblast appliance>:1344/sandblast”.
- On Failure Error or Bypass.
- Enable Response Processing allows the ICAP server to process response messages. If enabled this setting will also require:
- Server - This is the name of the ICAP server >>> sandblast_server
- Path - This is the path on the server to the processing compent "icap://<ip-address of sandblast appliance>:1344/sandblast”.
- On Failure Error or Bypass.
- Enable Streaming Media Bypass allows streaming media to ignore offloading to the ICAP server.
- Select Apply.
Enable firewall rule to connect ICAP Server (TEX Appliance)
Source: Fortigate
Destination: "ip-address of sandblast appliance"
Port: 1344
Enable firewall rule to use ICAP Profile
Source: xyz-ip
Destination: xyz-ip
Port: http
Profile: "Sandblast_Profile"
---
Better:
Use a Check Point Firewall! 
Regards,
Heiko
➜ CCSM Elite, CCME, CCTE ➜ www.checkpoint.tips



