- Products
Quantum
Secure the Network IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloudGuard CloudMates
Secure the Cloud CNAPP Cloud Network Security CloudGuard - WAF CloudMates General Talking Cloud Podcast - Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- Quantum (Secure the Network)
- CloudGuard CloudMates
- Harmony (Secure Users and Access)
- Infinity Core Services (Collaborative Security Operations & Services)
- Developers
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Infinity Portal
- Products Announcements
- Threat Prevention Blog
- CheckMates for Startups
- Learn
- Local User Groups
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- APAC
- Partners
- More
- ABOUT CHECKMATES & FAQ
- Sign In
- Leaderboard
- Events
CheckMates Toolbox Contest 2024
Submit a Tool for a Chance to WIN a $300 or $50 Gift Card!
May the 4th (+4)
Roadmap Session and Use Cases for
Cloud Security, SASE, and Email Security
Harmony Endpoint:
Packing a Punch in 2024
CPX 2024 Content
is Here!
Harmony SaaS
The most advanced prevention
for SaaS-based threats
CheckMates Go:
The Difference Is In The Details
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Quantum
- :
- Remote Access VPN
- :
- How to get better grades @ SSL Labs Certificate sc...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
How to get better grades @ SSL Labs Certificate scan
Can any one here guide me on how to get a better score when I scan my firewall with the SSL Server Test (Powered by Qualys SSL Labs) ?
Is there a quick guide on how to enable forward secrecy, disable tls v1.0, 1.1 and weak ciphers etc. ?
![]() Best regards Keld Norman
Best regards Keld Norman
Thanks for the anwsers so far - I have collected them all - testet and gotten better scores - here is what i did:
#######################################################################
# HOW TO GET BETTER GRADES IN THE SSLLABS.COM SSL TEST #
#######################################################################
To get from the B to A I did the following:
Alter the portal to only support TLS 1.2
In my 80.10 SmartConsole:
Global Properties -> AdvancedConfiguration -> Portal Properties: Altered minimum version to TLS 1.2
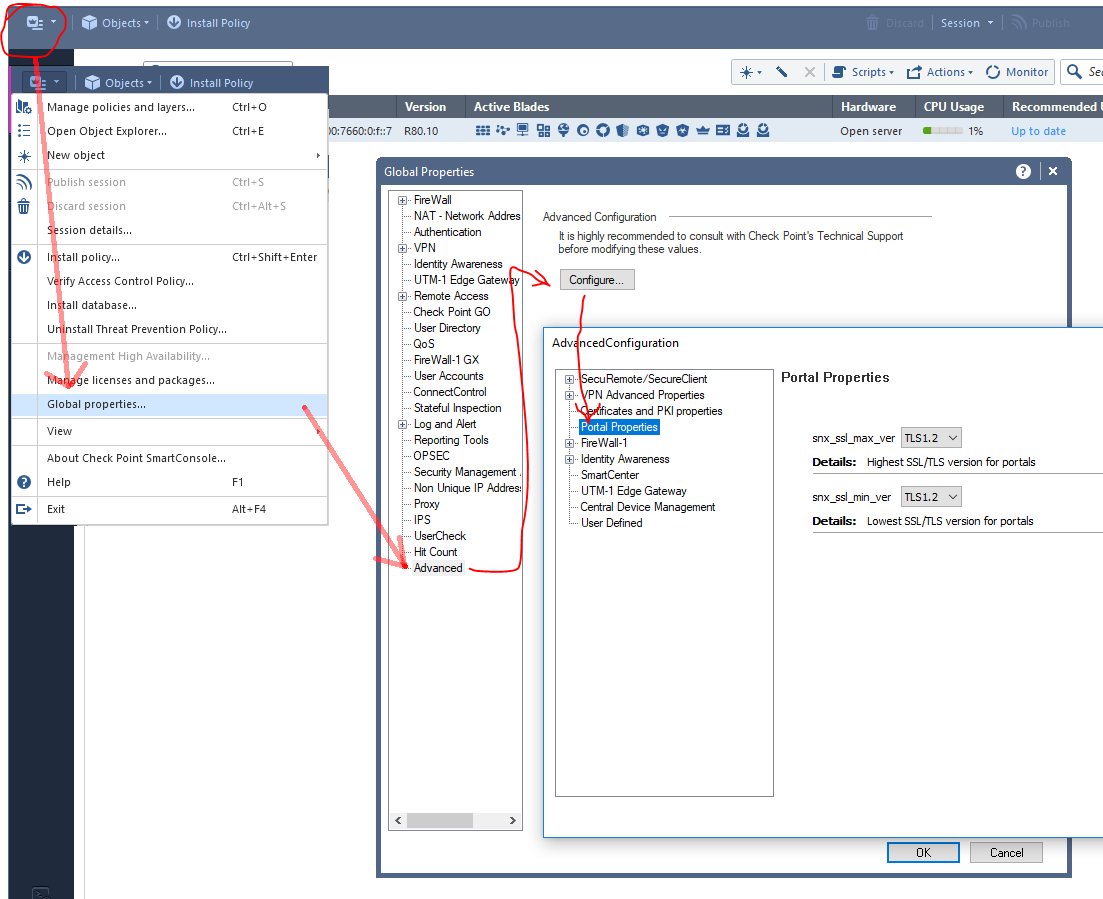
NB: Thanks to Claus Kjær for reminding me of this GUI way of doing things - I were trying to do achieve this by altering conf files with vim in expert shell..
Now to enable perfect forward support:
REF: Specific HTTPS sites that use ECDHE ciphers are not accessible when HTTPS Inspection is enabled (sk110883)
| A note about the above sk110883 |
|---|
ECDHE is quite widely used and recommend. It works with elliptical keys and provides forward secrecy. It's used for the key exchange. ECDSA is not widely used though, but it does also use elliptical keys. It it used for authentication |
I logged on to the firewall via secure shell (I have a standalone installation with the manager and firewall running in a VM) and in expert mode pasted the following 3 lines in:
[Expert@firewall:0]#
ckp_regedit -a SOFTWARE//CheckPoint//FW1 CPTLS_ACCEPT_ECDHE 1
ckp_regedit -a SOFTWARE//CheckPoint//FW1 CPTLS_PROPOSE_ECDHE 1
ckp_regedit -a SOFTWARE//CheckPoint//FW1 CPTLS_EC_P384 1
Then a reboot or just a cpstop/start is needed:
[Expert@firewall:0]# nohup $(cpstop ; cpstart) &
Now the grade went from B to A :
Now to look at the suggested link from Dameon Welch Abernathy
![]()
Remove the weak ciphers related to TLS 1.2
(ref: https://supportcenter.checkpoint.com/supportcenter/portal?eventSubmit_doGoviewsolutiondetails=&solut...)
So basically I just need to alter this in the file: /web/templates/httpd-ssl.conf.templ
ALTER: SSLCipherSuite HIGH:!RC4:!LOW:!EXP:!aNULL:!SSLv2:!MD5
TO SSLCipherSuite ECDH:!aNULL:!ECDSA:!aECDH:!eNULL:!MD5:!SHA1
Again secure shell to the system - and in export mode paste the lines in purple below:
# Backup the file you want to alter first
[Expert@firewall:0]#
cp /web/templates/httpd-ssl.conf.templ /web/templates/httpd-ssl.conf.templ.backup
# Oneliner to replace the old line with the new using the SED util.
sed -i 's/SSLCipherSuite HIGH:!RC4:!LOW:!EXP:!aNULL:!SSLv2:!MD5/SSLCipherSuite ECDH:!aNULL:!ECDSA:!aECDH:!eNULL:!MD5:!SHA1/' /web/templates/httpd-ssl.conf.templ
# Test if the line was altered:
grep -i ^SSLCipherSuite /web/templates/httpd-ssl.conf.templ
( it should return: SSLCipherSuite ECDH:!aNULL:!ECDSA:!aECDH:!eNULL:!MD5:!SHA1)
Then reboot the firewall..
[Expert@firewall:0]# reboot
The Qualys SSL scan still only shows an A - I still have some weak ciphers 😕
To be continued..
9 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
It was a good tip - I'll just need to investigate what impact disabling the last 4 weak ciphers would have if i turn them off:
| Cipher Suites | ||
# TLS 1.2 (suites in server-preferred order) | ||
TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256 (0xc02f) ECDH secp256r1 (eq. 3072 bits RSA) FS | 128 | |
TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA (0xc014) ECDH secp256r1 (eq. 3072 bits RSA) FS | 256 | |
TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA (0xc013) ECDH secp256r1 (eq. 3072 bits RSA) FS | 128 | |
TLS_RSA_WITH_AES_128_GCM_SHA256 (0x9c) WEAK | 128 | |
TLS_RSA_WITH_AES_128_CBC_SHA (0x2f) WEAK | 128 | |
TLS_RSA_WITH_AES_256_CBC_SHA (0x35) WEAK | 256 | |
TLS_RSA_WITH_3DES_EDE_CBC_SHA (0xa) WEAK | 112 | |
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You should probably add !3DES to the list of modifications as well.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
One vulnerability scan shows we have weak dh groups. We don't use those groups...but it doesn't like the fact that we even have them available...? How would one go about fixing that.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello everyone,
Just to revive this old post, this SK is relevant for versions R80.10, R80.20 and R80.30
Cipher configuration tool for R80.x Gateways
sk126613
Just used this on a customer and works as advertised.
Have fun,
Pedro Madeira
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The SSLLABS scan still show the weak ciphers.
Can we remove all the ciphers except one that is shown ok?
How about preferring PFS ciphers?
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
First of all thanks for sharing your investigation, i used some of your findings in my own lab for testing purposes. Could you explain to me if you're trying to get a better grade for your "Multiportal" (Gaia Web Interface) or are you trying to get a better grade for a website that is terminated via HTTPS inspection on your gateway?
I am in a situation where i need to enhance the ciphers proposed when using inbound HTTPS inscpection on R80.10. What i discovered so far is that on R80.10 you can only alter the server preferred cipher order (The server is your Security Gateway), and it is not possible to disable some of the weak ciphers completely.
You are saying that you successfully disabled the weak ciphers if i understand correctly right? If so, does your customer run R80.20 or R80.30?
Because the SK (sk126613) describes the following under the section R80.10:
Important Information:
- If a cipher exists in the file but the Security Gateway doesn't support it, the cipher will be ignored.
- If there are ciphers on the Security Gateway that are not in the file, the Security Gateway will still use them but give preference to the ciphers in the file.
- If there is a syntax error in the file, the changes will not take effect, and the Security Gateway will use the old behavior.
- This procedure is not relevant for SSL Inspection.
I am still investigating so if i discover a way to disable the weak ciphers on R80.10 completely i will share this info with you 🙂
Regards,
Jelle
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi I am also facing similar issues on R80.10, specifically to disable
: (TLS_RSA_WITH_AES_128_GCM_SHA256)
: (TLS_RSA_WITH_AES_128_CBC_SHA)
: (TLS_RSA_WITH_AES_256_CBC_SHA)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Nice tutorial!
Waiting for part 2.
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 3 | |
| 3 | |
| 3 | |
| 2 | |
| 2 | |
| 2 | |
| 1 | |
| 1 | |
| 1 | |
| 1 |
Upcoming Events
Thu 16 May 2024 @ 10:00 AM (CEST)
EMEA: Playblocks & MS Defender – Security Automation DeepDive into New Endpoint IntegrationThu 16 May 2024 @ 04:00 PM (CEST)
CheckMates Live DACH - ACHTUNG, Sie werden gehackt! So schützen Sie sich!Thu 16 May 2024 @ 05:00 PM (CEST)
Americas: Playblocks & MS Defender – Security Automation DeepDive into New Endpoint IntegrationFri 17 May 2024 @ 10:00 AM (CEST)
CheckMates Live Netherlands - Sessie 26: ElasticXL & VSNext DescriptionTue 21 May 2024 @ 10:00 AM (CEST)
CheckMates Live DACH - Einführung in Check Points Hyperscalinglösung - Quantum MaestroThu 16 May 2024 @ 04:00 PM (CEST)
CheckMates Live DACH - ACHTUNG, Sie werden gehackt! So schützen Sie sich!Fri 17 May 2024 @ 10:00 AM (CEST)
CheckMates Live Netherlands - Sessie 26: ElasticXL & VSNext DescriptionTue 21 May 2024 @ 10:00 AM (CEST)
CheckMates Live DACH - Einführung in Check Points Hyperscalinglösung - Quantum MaestroWed 22 May 2024 @ 10:00 AM (BRT)
Brazil: Desafios e melhores práticas na gestão de CibersegurançaAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2024 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
Facts at a Glance
User Center


