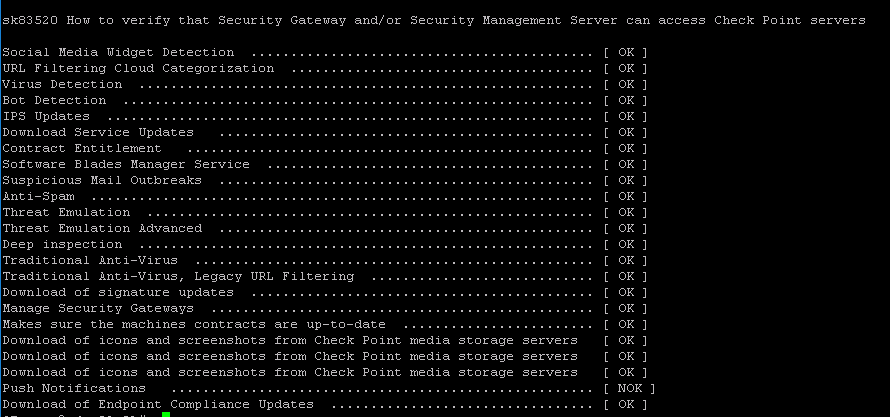
Hi,
how do you know 200 OK is necessarily means the service is ok ?
I mean what if http is 200 but XML returns service error or something ?
also, using grep on 'Found' prints OK also for 404 Not Found so you need to change your if statement to something like this:
if [ `curl_cli -Lisk $1 | head -1 | egrep "OK|Found|Moved" | egrep -c -v "Not Found"` -gt 0 ]; then result=" [ OK ]"; fi
echo $result
but i still found some FP using this script, see TE response for example which the script returns OK for it.
[Expert@Kings_Landing:0]# curl_cli -Lisk 'http://te.checkpoint.com'
HTTP/1.1 302 Found
Location: https://te.checkpoint.com/
Connection: close
HTTP/1.1 403 Forbidden
Date: Mon, 23 Apr 2018 08:37:07 GMT
Server: CPWS
Vary: accept-language,accept-charset
Accept-Ranges: bytes
Transfer-Encoding: chunked
Content-Type: text/html; charset=iso-8859-1
Content-Language: en
Set-Cookie: te_cookie=ANPHKIMA; Domain=te.checkpoint.com; Expires=Thu, 20-Apr-2028 08:51:56 GMT; Path=/
<?xml version="1.0" encoding="ISO-8859-1"?>
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Strict//EN"
"http://www.w3.org/TR/xhtml1/DTD/xhtml1-strict.dtd">
<html xmlns="http://www.w3.org/1999/xhtml" lang="en" xml:lang="en">
<head>
<title>Access forbidden!</title>
<link rev="made" href="mailto:systems@us.checkpoint.com" />
<style type="text/css"><!--/*--><![CDATA[/*><!--*/
body { color: #000000; background-color: #FFFFFF; }
a:link { color: #0000CC; }
p, address {margin-left: 3em;}
span {font-size: smaller;}
/*]]>*/--></style>
</head>
<body>
<h1>Access forbidden!</h1>
<p>
You don't have permission to access the requested directory.
There is either no index document or the directory is read-protected.
</p>
<p>
If you think this is a server error, please contact
the <a href="mailto:systems@us.checkpoint.com">webmaster</a>.
</p>
<h2>Error 403</h2>
<address>
<a href="https://community.checkpoint.com/">te.checkpoint.com</a><br />
<span>Mon Apr 23 10:37:07 2018<br />
Apache</span>
</address>
</body>
</html>