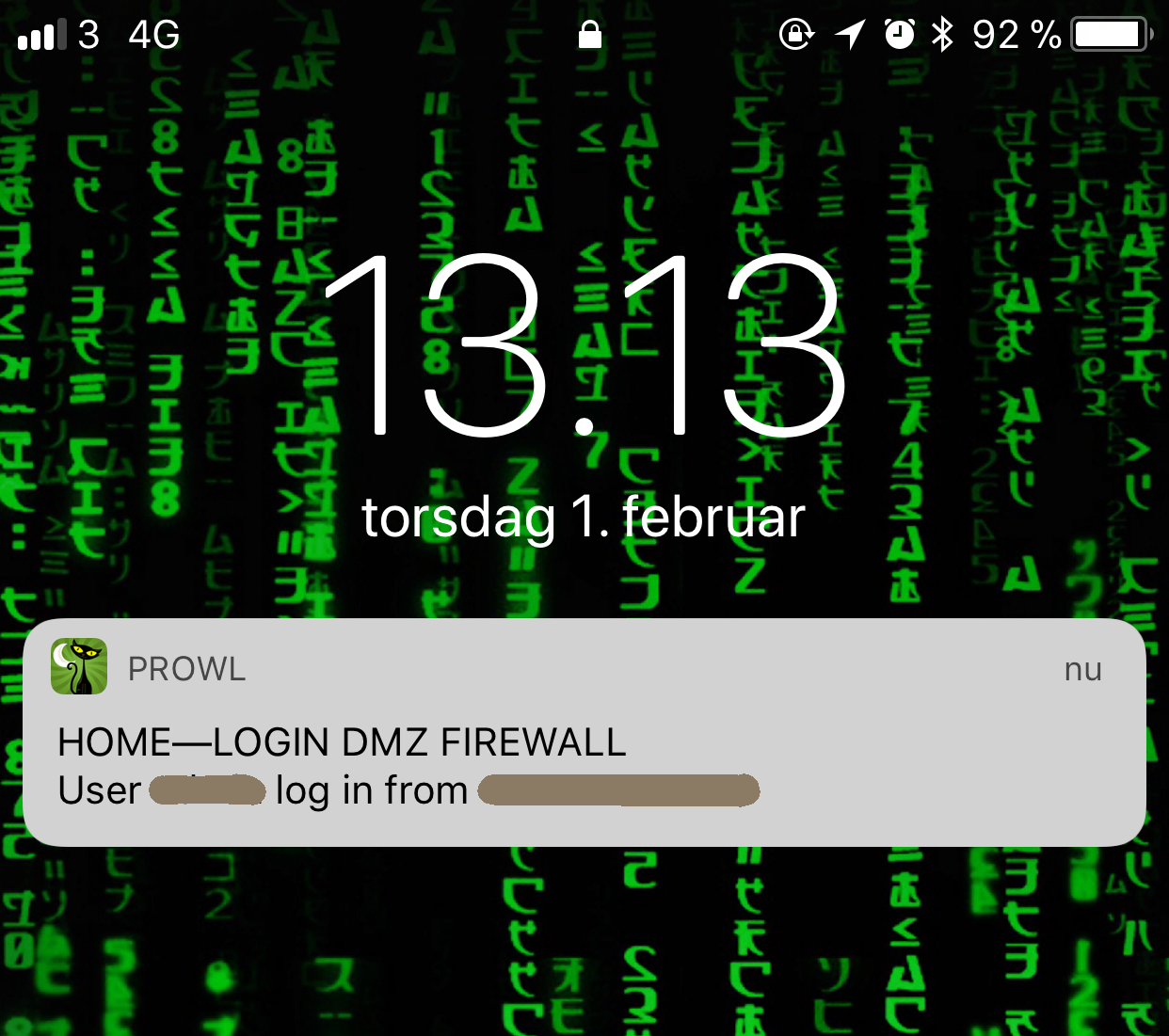
This is what I see on my iPhone in real-time when there is a SSH login on firewalls or firewall manager.
(It is a push message send via the service called #Prowl)
I also gets real-time notifications whenever a port scan is detected from the intranet (see the prowl message at the bottom of this page).
Below is a quick guide on how to setup this type of real-time alerting - it takes less the 20 min to do.
1. Download the Prowl App from the Apple App Store.
2. Register at www.prowlapp.com and generate an API key.
3. Place a bash script on your firewall that uses curl to send an alarm (using the API key).
4. Configure Smart Event to use the prowl as a generic alarm.
5. Select the events you want to have realtime alerts on.
1. Download the Prowl App from Apple's App Store..
First you must download the prowl app (it is an iPhone app).
An alternative exist, it is called PushOver for Android based phones (also works on iPhones) but my script and description here is made for iPhones - feel free to rewrite another version with a more generic app 
The app looks like this:
A link to the appstore: https://itunes.apple.com/us/app/prowl-easy-push-notifications/id320876271?mt=8
2. Register at www.prowlapp.com and create an API key
To generate an API key you must register at the webpage https://www.prowlapp.com.
You can generate as many keys there as you like for free - they will be linked to your prowl account and can be used to differentiate different types of alarms.
They also come with a unique email address you can send a mail to and get the same function ( a push message on your iPhone).
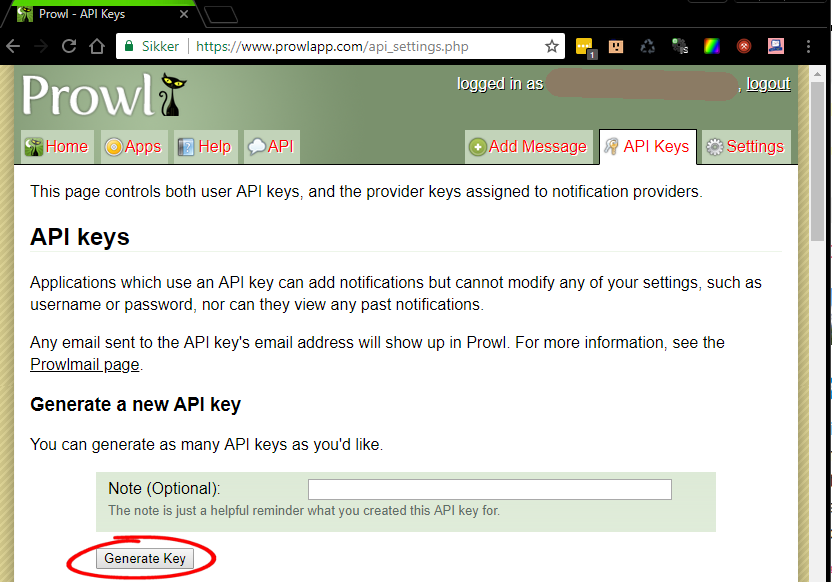
It is really as easy as seen below - after registering on the prowlapp.com page just press the "API Keys" tab and then the top right corner and then the "generate key" button on the page (then copy the key to be used later below).
You can give it a note/name if you like like "firewall alarms", "firewall login" etc..
3. Place a bash script on your firewall
I have two scripts placed on all my Check Point appliances - no matter if they are acting as firewalls or managers etc.
They are for logging all SSH logins and for logging Reboots.
To get a notification every time some one logges in via Secure Shell..
To get a notification every time some one logges in via SSH you can place a file in the directory /etc/ssh/ called sshrc
(this file will, per design of sshd, be executed by the system whenever any SSH login occours)
In that file you place the following code - but remember to replace the "your-prowl-api-key-here" with your own prowl API key (The API key consists of a 40 char/digit long string).
In the file /etc/ssh/sshrc place the following code (Notice the blue text is a hardcoded directory - it can be replaced with a variable)
/etc/ssh/sshrc:
if [ -e /etc/profile.d/CP.sh ]; then
. /etc/profile.d/CP.sh
fi
if [ -x ${CPMDIR}/bin/curl_cli ]; then
I=$(echo ${SSH_CONNECTION:-Unknown}|/bin/cut -d " " -f 1)
${CPMDIR}/bin/curl_cli \
--insecure https://prowl.weks.net/publicapi/add \
-F apikey=your-prowl-api-key-here \
-F priority=2 \
-F application="DMZ01" \
-F event="LOGIN FIREWALL #2" \
-F description="User ${USER:-[Unknown]} log in from ${I:-[Unknown IP]}" > /dev/null 2>&1 &
fi
Feel free to alter the green text to variables or other descriptions
* Note: Perhaps the firewall is blocked from sending a https request via curl to the address https://prowl.weks.net/publicapi/add
To get alerts when the firewall boots..
To get an alert when the firewall or manager boots place the following in the file called /etc/rc.local:
Edit this file: /etc/rc.local
REBOOT_TIME="$(last reboot|head -1|cut -d ' ' -f13-17)"
${CPMDIR}/bin/curl_cli \
--insecure https://prowl.weks.net/publicapi/add \
-F apikey=your-prowl-api-key-here \
-F priority=2 \
-F application="LAN" \
-F event="REBOOT FIREWALL #XXX" \
-F description="Reboot: ${REBOOT_TIME:-Unknown} : $(date)" > /dev/null 2>&1 &
Again feel free to alter the green text to variables or other descriptions
* Note: Perhaps the firewall is blocked from sending a https request via curl to the address https://prowl.weks.net/publicapi/add
IMPORTANT: Ensure curl is present on the firewall/manager you install this on
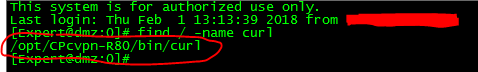
In my 80.20 it is located here: ${CPMDIR}/bin/curl_cli
If you also wants to enable push messages / alarms from Smart Events then read on..
4. Configure Smart Event to use the prowl as a generic alarm.
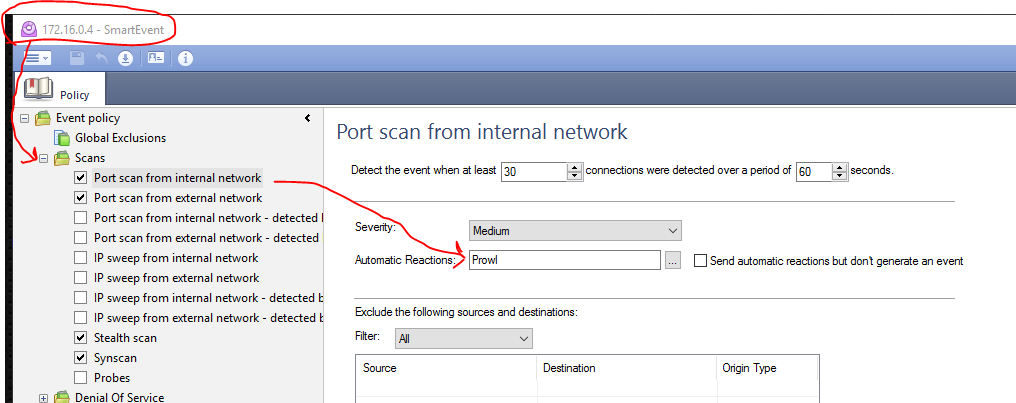
If you also want to get alarms from Smart Event's like an internal port scan, virus attacks, IDS/IPS trigger etc, you can simply create a new smart event alarm in the Smart Event Policy pane under:
-> Generic Settings -> Objects view called "Automatic Reactions" like this:
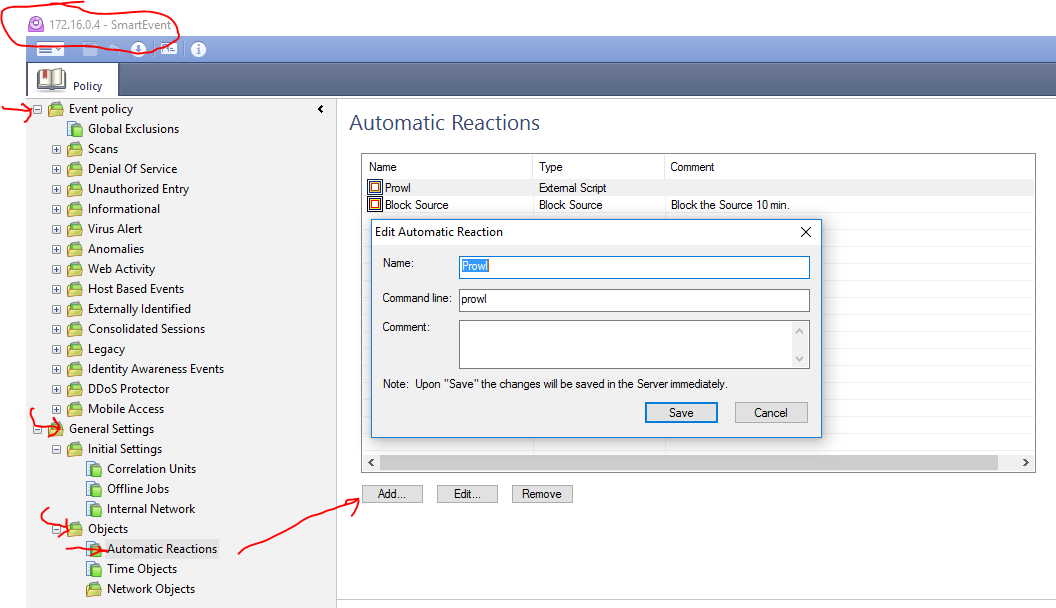
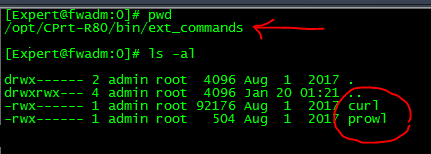
to get the prowl activated you must place curl and the prowl script shown #below in the special directory on the firewall manager / smart event server called: $RTDIR/bin/ext_commands
It might not exist - if that is the case then just create it :
mkdir -m 700 $RTDIR/bin/ext_commands
Now place the program curl in the same directory (one way to get curl is to run "find / -name curl" and copy it to the directory)
And add the following to the prowl script:
vi $RTDIR/bin/ext_commands/prowl
#!/bin/bash
source /etc/profile.d/CP.sh
EVENT=$(cat)
CURL="${CPMDIR}/bin/curl_cli"
if [ ! -x ${CURL} ]; then
echo ""
echo "Missing ${CURL} - exiting!"
echo ""
exit 1
fi
OUT=$(echo ${EVENT:-error}|awk 'NR > 1 {print $1}' RS='(' FS=')'|tr ';' '\n')
${CURL} --silent \
--insecure https://prowl.weks.net/publicapi/add \
-F apikey=your_prowl_api_key_here \
-F priority=2 \
-F application="Firewall Alert" \
-F event="Notification" \
-F description=" Info: ${OUT:-Error}" > /dev/null
return 0
Set the script and curl to be executable and owned by the user admin:
chown admin:root $RTDIR/bin/ext_commands/prowl
chmod 700 $RTDIR/bin/ext_commands/prowl
NB: I have also set the ext_commands directory to chmod 700
chmod 700 $RTDIR/bin/ext_commands
5. Select the events you want to have real-time alerts on.
Now you just need to select the events you want to have the prowl real-time alarm on like this:
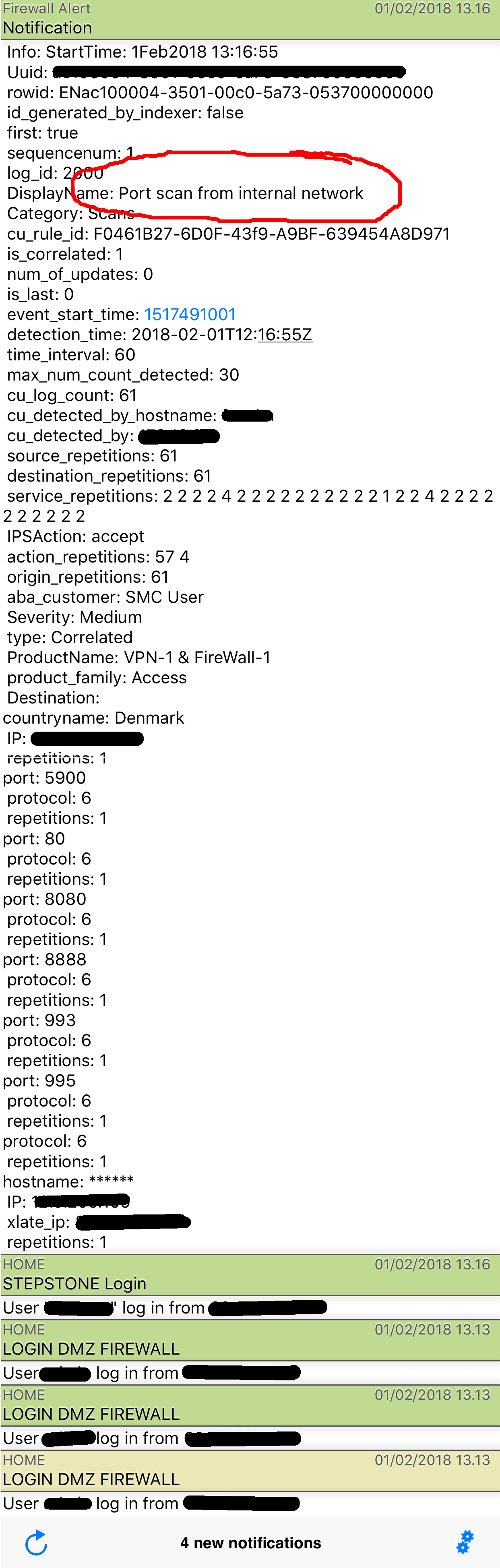
Here is how a portscan is reported - notice i can also see what ports they scanned for:
To test if the trigger and alarm works, just try a nmap -Pn -p0-65535 www.nsa.gov from your internal net # *just kidding* 
---------------------------------------- END OF MESSAGE --------------------------
Best regards
Keld Norman @ #Dubex A/S - Denmark.