- Products
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- Learn
- Local User Groups
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
- Partners
- More
- ABOUT CHECKMATES & FAQ
- Sign In
- Leaderboard
- Events
Firewall Uptime, Reimagined
How AIOps Simplifies Operations and Prevents Outages
Introduction to Lakera:
Securing the AI Frontier!
Check Point Named Leader
2025 Gartner® Magic Quadrant™ for Hybrid Mesh Firewall
HTTPS Inspection
Help us to understand your needs better
CheckMates Go:
SharePoint CVEs and More!
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Who rated this post
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
ID Sharing on AutoScaling
Use case; since the VMSS setup on Azure allow to customers connect the On-Prem to cloud with Native VPN GW or Express Route and redirect the traffic to the VMSS members (Check Point Gateways), like the next diagram.

Now let's work on the need to use Identities on the rules and since this comes from the On-Prem, the identities will be based on AD, there is a good way to achieve this, in Check Point exist the ID-Sharing feature, where an On-Prem Check Point Gateway with connectivity to the AD can grab the Login events on the AD and create the list based on AD groups and share this to another GW, so the other GW don't need to reach the AD.
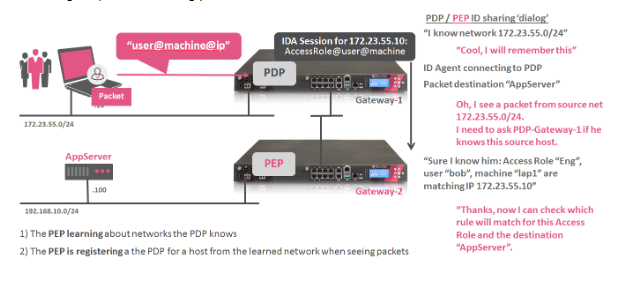
But this needs to be configured per GW basis, this in autoscaling scenarios need automation, the CME tool that handles the automation of the CG IaaS deployment also have the capability to customize based on scripts that can run on Management side or GW side.
So I created a bash script that allows to enable the identity sharing on each VMSS new deployed GW.
First we need to enable the capability to share identities on the On-Prem GW, this is done on the Gateway object under Identity Awareness menu.
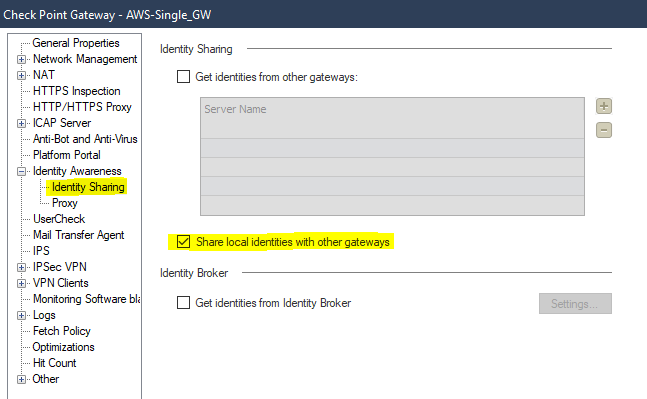
Once we prepare this, we need to set up the CME based on CloudGuard Network for Azure VMSS R80.10 and Higher Administration Guide (This link was edited by Check Point on 19 Dec 2021)
Once all is done, we need to download the bash script and pass it to the management, the script is here Github, you can use curl_cli to do it.
curl_cli -k 'https://raw.githubusercontent.com/christiancastilloporras/Indentity-Sharing-with-CME----Check-Point/master/cme_identitysharing.bash' -O
and give it execution permissions.
Then on the CME need to add this file to the Management, make sure to put the correct path;
autoprov-cfg set management -cs 'path/to/script'
Then on the template need to call the Custom Parameter feature, this feature call the management script and pass params to the script, the script uses 5 parameters, the 1 and 2 are passed by the CME by default each time you call this feature ('add' or 'delete' as $1 and newly deployed GW Name as $2), then the script needs an action this should be "IDSHARING", needs the rulebase to install; this needs to be exactly the name of the Policy Package of the deployed Gateways and exactly the GW name where the VMSS will grab identities; all this will setup the next addition to the CME;
autoprov-cfg set template -tn "name-of-template" -cp 'IDSHARING rulebase gwname'
And now every newly deployed GW will have the identities and we can set up rules for the VMSS based on AD Groups.
About CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter


