- Products
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- Learn
- Local User Groups
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
- Partners
- More
- ABOUT CHECKMATES & FAQ
- Sign In
- Leaderboard
- Events
Access Control and Threat Prevention Best Practices
5 November @ 5pm CET / 11am ET
Ask Check Point Threat Intelligence Anything!
October 28th, 9am ET / 3pm CET
Check Point Named Leader
2025 Gartner® Magic Quadrant™ for Hybrid Mesh Firewall
HTTPS Inspection
Help us to understand your needs better
CheckMates Go:
Spark Management Portal and More!
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Who rated this post
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
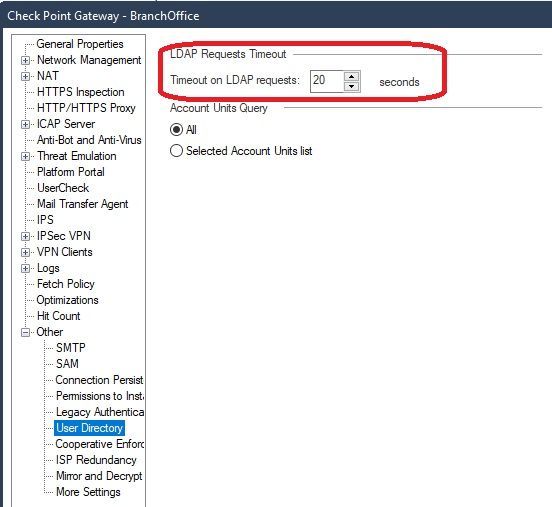
You have something wrong/misconfigured in your LDAP setup. SecurID/RADIUS/TACACS authentication methods are accessed through an External User Profile object (formerly known as the generic* user), which is always checked after the local user database then LDAP, and this order of operations cannot be changed. See this screenshot:
When no match is found for the user login name in the local user database, all defined LDAP Account Units (AUs) are queried simultaneously. They must all respond before the authentication process can move on to External User Profiles and SecurID, or the above timer must be reached. The most common cause of this is an old or invalid AU specifying servers that are unreachable or no longer exist, if you clean up those old AUs the delay should go away. If you only have one AU and it appears to be valid, check the defined servers for that AU object and make sure they are correct and reachable. The delay you are seeing is not normally caused by an LDAP credentials issue since that results in a quick failure; the delay is normally caused by unreachable or invalid LDAP servers defined somewhere in an AU configuration.
If you can't delete the old AUs for some reason, on the above screen you can configure a firewall to query only certain AUs and ignore others (or maybe even shorten the timer), but the best long-term approach is to clean up your AU configuration and/or servers definitions.
Gaia 4.18 (R82) Immersion Tips, Tricks, & Best Practices Video Course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
About CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter