- Products
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- Learn
- Local User Groups
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
- Partners
- More
- ABOUT CHECKMATES & FAQ
- Sign In
- Leaderboard
- Events
Access Control and Threat Prevention Best Practices
5 November @ 5pm CET / 11am ET
Ask Check Point Threat Intelligence Anything!
October 28th, 9am ET / 3pm CET
Check Point Named Leader
2025 Gartner® Magic Quadrant™ for Hybrid Mesh Firewall
HTTPS Inspection
Help us to understand your needs better
CheckMates Go:
Spark Management Portal and More!
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Who rated this post
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Redundant VPN over BGP
Hi community,
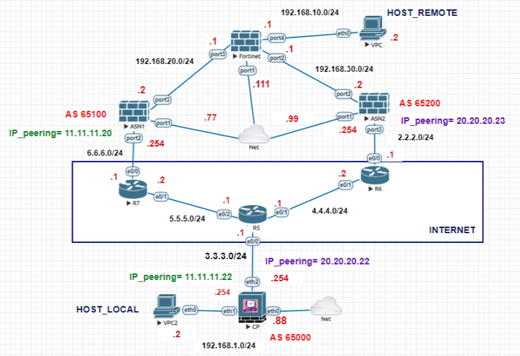
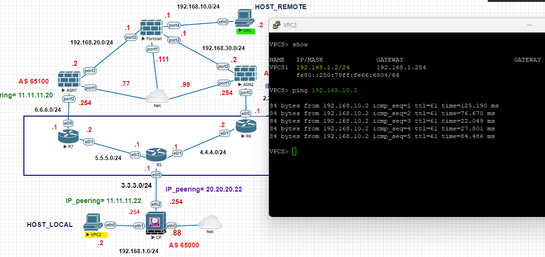
I have carried out a laboratory to test redundant VPNs over BGP, I share with you the topology of my environment and the configurations on the checkpoint side, I hope it helps you.
LAB.
ASN1 and ASN2 are the remote gateways with which I will set up the VPNs.
OBJECTIVE: The "HOST_LOCAL" connects with the "HOST_REMOTE" through a VPN over BGP with ASN1, if this VPN goes down, there will be a VPN over BGP with ASN2 to reach the "HOST_REMOTE" again, guaranteeing that connectivity is not lost between both hosts using VPNs.
Configuration at the checkpoint.
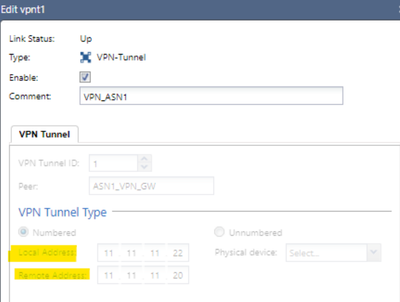
At the GAIA level, we create a VPN-tunnel interface, where we define the tunnel ID, in this case 1, and we will place the peering IPs that we have defined in the topology, in this case for ASN1 they are those highlighted in green (local 11.11 .11.22 and remote 11.11.11.20)
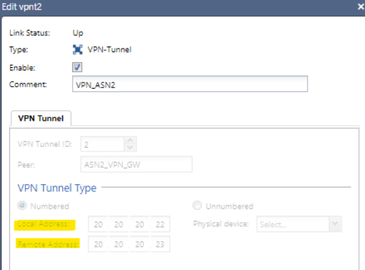
We repeat the same step for the VPN against ASN2, we will change the peering IPs, as shown in the topology the IPs to use would be the purple ones (local 20.20.20.22 and remote 20.20.20.23), we choose the ID = 2 for this VPN.
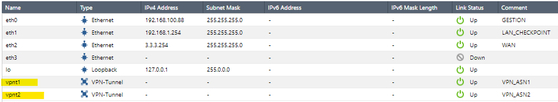
Once the VPN-tunnel interfaces have been created, it would look like this.
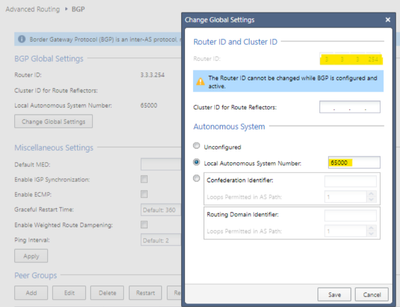
In the Advanced Routing > BGP > Change Global Settings option, configure your Router ID (in my case I assigned the IP of my external interface 3.3.3.254) and your AS number, which in my case I set 65000.
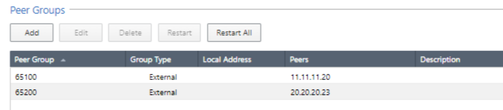
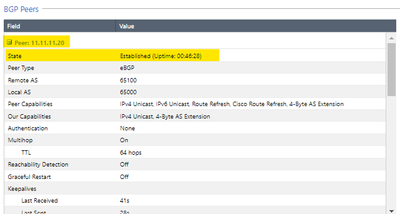
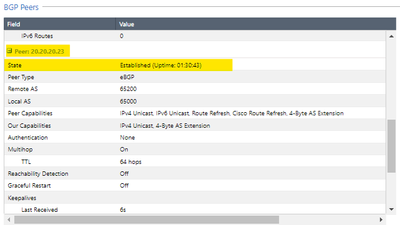
In the same section of Advanced Routing > BGP, we will add the BGP peers for both VPNS.
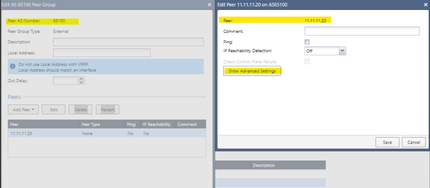
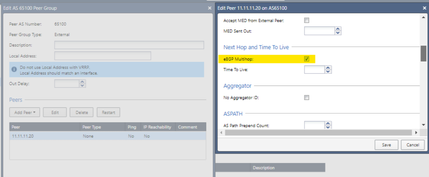
In the BGP Peer, we must place the remote AS as well as the remote peer with which we create the VPN-tunnel interfaces. Don't forget that we must enable the eBGP Multihop option. We repeat the same for the ASN2 peer
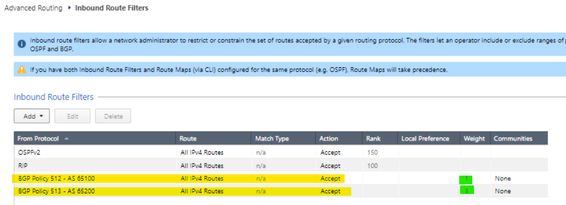
We will allow all the networks that the remote peer with AS 65100 and 65200 publish to us in the "inbound route filters" option. I am setting the VPN with ASN1 (AS 65100) to be the primary one using the weights (green underline)
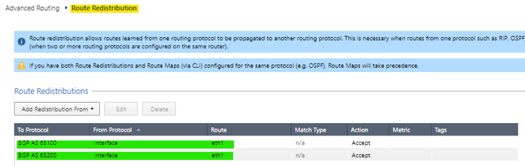
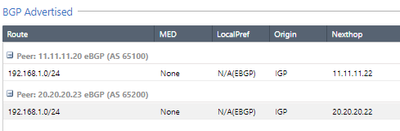
In the "Route Redistribution" section I am publishing my network from eth1 to peers AS65100 and AS65200.
Once configured at the GAIA level, we configure at the SMC level.
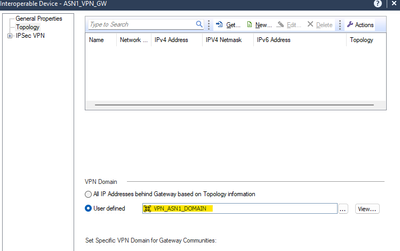
We created the 2 domains for both VPNs without anything.
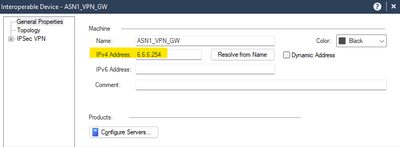
We create the "Interoperable Device" with the public IP of the other end, and with the respective domain that we just created. We follow the same sequence for ASN2.
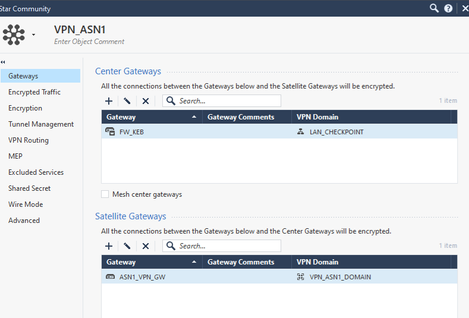
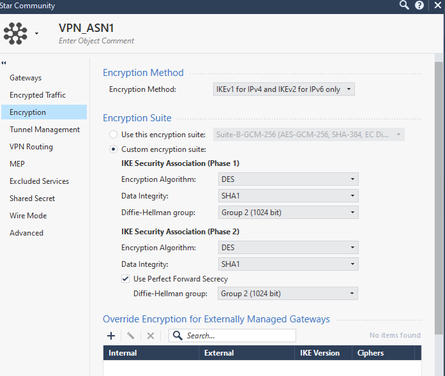
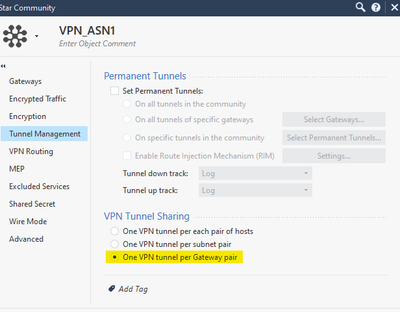
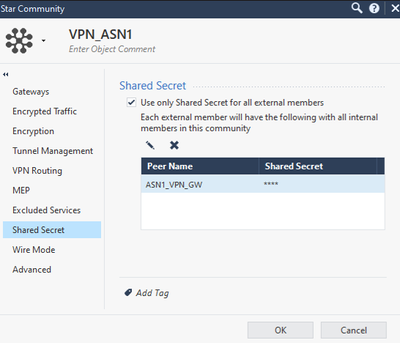
We create a star community with the following steps, repeat the same process for ASN2
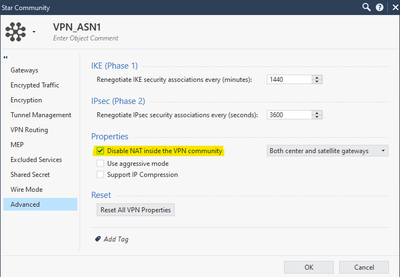
In this case, I am not using nateo, but if you want to use it, do not enable that option.
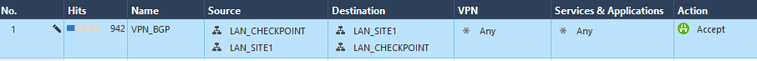
RULE.
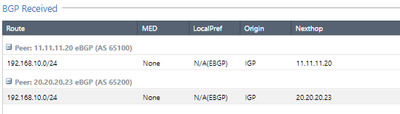
After the configurations on the checkpoint side and the configurations of the remote devices, the BGP neighborhood is established with both peers (ASN1 and ASN2), in this case I have configured that both ASN2 and ASN2 publish the HOST network. REMOTE towards the checkpoint.
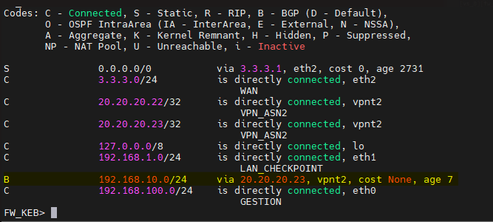
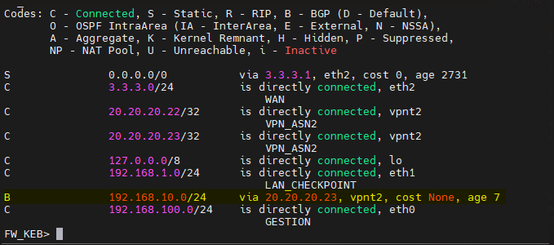
Networks received and published using BGP.
Routes at the checkpoint.
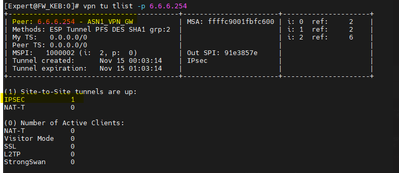
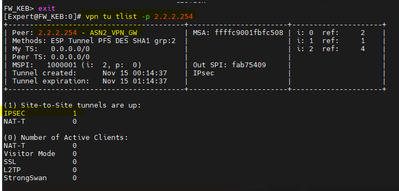
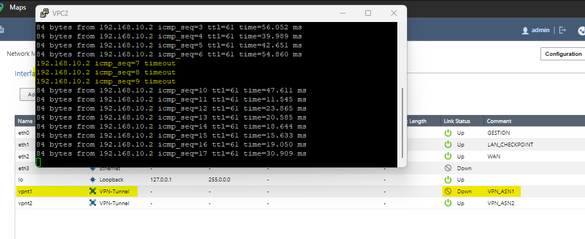
VPNs UP.
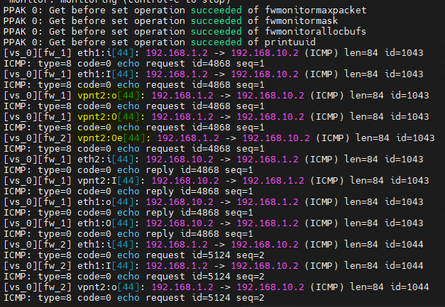
Connectivity test through VPN_ASN1
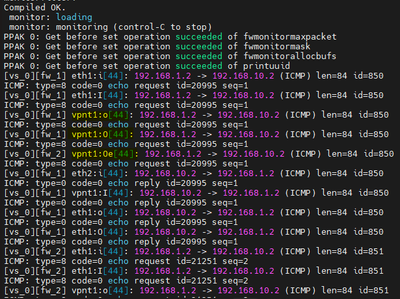
Failover test
In the simulated environment, I observed that during the failover 3 ping packets were lost, after which the connection was kept constant by the backup VPN that is with ASN2, the test was performed in reverse and 2 ICMP packets were obtained, and then The connection remained constant. As far as I can tell the setup is functional.
Regards
About CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter